This is a great tutorial on cracking the iphone to record more than 30 seconds on the iPhone 3G's video camera. This is a hack of the previously still camera that comes stock with all of Apple's phones. Enable your iPhone to shoot video instantly and free! Download the iPhone ...more
This video will teach you the basics of payphone phreaking. Pay phone phraking involves doing various pranks and hacks to pay phones.
A mobile phone is capable of all kinds of hacks. You can use your cell for more than just photos, texts, and phone calls. Here are some great ways for messing about with your mobile handset, whether it be using a phone to unlock a car, or entering the mobile phone throwing cha ...more
In this article, I'll show you how to send SMS messages with Python. You'll need Python 2.7 or later, urllib and urllib2. The code basically uses an online text messaging service to "POST" html data, as if a person was entering the data themselves. The uses for something like ...more
Lost the product key for your game? If you have to reinstall the game and don't have that key anymore, you're out of luck, especially if you didn't "buy" the game. But never be in fear of losing product keys again with today's Null Byte, where we'll be practicing a little bit ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. This week: A phoneography challenge on silh ...more
Too lazy to take your phone out of your pocket? If so, then here's a must-have: a customizable inPulse wristwatch that can check into Facebook Places. Created by inPulse designer Eric Migicovsky, the hacked watch uses Bluetooth to pull Facebook Places from a connected Android ...more
The iPhone and iPod touch are nearly identical devices, especially now that Apple has added a front-facing camera to the iPod touch. All that's missing is the phone part. With the help of Lifehacker and apps like Skype and Line2, you can save some money by turning your iPod To ...more
It seemed like an impossible task. No one could figure it out. Only God himself knew the answer. But the impossible has become possibly after only a week of trying. The Droid X has been rooted. Yes, it's true. Everybody who owns Verizon Wireless's Droid X from Motorola can no ...more
Via WonderHowTo World, Cinematography: Lozzless demonstrates how to make a diy cheap macro lens with working aperture for his Canon 5D Mark II, coined the "SuperMacro". According to Hack a Day, "The process involves fashioning a connector ring from a lens cap, modifying an ...more
Got a seriously large number of business cards stashed in your basement due to ordering several boxes full only to have the company mess up on your phone number? Make use of these otherwise extraneous and superfluous cards by watching this video. Whip out those nameplates and ...more
In this clip, learn how to set up the HTC EVO's Hot Spot app. This app is very useful and by using it you can connect up to 8 other devices to your 4G internet via tethering and use your phone as a wireless modem. This app will cost you an additional 29.99 a month but if you a ...more
In this video tutorial, viewers learn how to create free custom ringtones for an iPhone 3G. Begin by opening iTunes and select the song that you want as a ringtone. Right-click on the song and select Get Info. Go to the Options tab and make the song last only 40 seconds. Then ...more
Take a look at this video if you've ever been curious on how people send video messages via the iPhone. This is the source you need to get in Cydia iphonevideorecorder.com/3 This is the Unlock code for the app: xumiqdikni Here is a list of some Cellphone email address forma ...more
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to program a ...more
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to defend yo ...more
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to session h ...more
An iPhone-controlled drone unveiled at the recently held CES is expected to revolutionize the world of video gaming. Called the AR.Drone (AR stands for augmented reality), this new product will literally bring video games to the streets. Via Daily Mail, "The flying saucer-li ...more
Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information y ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. More amazing community contributions this w ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. This week has been an exciting one. The com ...more
In this article, I'll show you how to easily "hack" Facebook, Twitter, YouTube, and any number of similar account types with an Android app called FaceNiff. FaceNiff allows you to sniff and intercept web session profiles over the Wi-Fi that your mobile device is connected to. ...more
Remember the good ol' days when you actually had to swipe your credit or debit card to make a payment at the store? Now all it takes is a flick of the wrist to purchase goods with your card, thanks to RFID (radio-frequency identification) technology from Chase (blink), Visa (p ...more
HoloDecon Tecnology directly afects our perceptive capacity, influencing the construction of the oniric sourronding , built in the alternate hyperrealist narratives The objects and the surroundings are experimented trough their properties and our perception of their substanc ...more
Flash video. It's what all smartphone users have been waiting for. Why has it taken sooo long? And why is Apple still resistant? Here's the scoop, via Wired: "Adobe is releasing Flash Player 10.1 for mobile phones and desktops today. And it is piggy-backing on Google’s fast ...more
There's an easy time hack available for Candy Crush Saga that let's you bypass the time restrictions to you can play more games faster, and this video guide from KiboshGaming will walk you through it on both Android and iOS devices. Video: . There is no real "hacking" involved ...more
Understandably, the tragedy in Japan has substantially risen the level of worldwide radiation-related hysteria. So much so, as an alternative to stampeding health food stores for iodine tablets, crafty individuals and organizations are hacking together personal radiation detec ...more
Since its inception in 2007, the Pwn2Own computer hacking contest has been challenging the vulnerability of mobile phones and web-related software. In 2010, the fruit of two full days of hacking came down to the exploitation of the following web browsers: Safari 4 on Mac OS X, ...more
iPodTouchedMaster shows how one can easily SSH into their iPod Touch with all firmware! To SSH is the ability to hack into your iPod Touch's file system. First, your iPod Touch must be jailbroken. Next, you'll have to open Cydia. Click "Featured Packages" or search for the ter ...more
Impress dinner companions with your flawless manners—it’s as simple as observing a few key rules. You Will Need * A crash course in dining etiquette Step 1. Know the basics As soon as you take your seat at the table, place your napkin in your lap and obey the basic rules: ...more
There is a vast amount of knowledge out there on computers! In fact, it is so vast that no single person could ever possibly ever learn everything there is to learn about hacking or computers in general. People usually specialize in a certain field: cryptography, computer secu ...more
Grab your thinking caps and get your hack on. Null Byte is officially seeking contributors on a weekly basis who are willing to take the time to educate the Null Byte community on anything, from hardware hacks to life hacks. Contributors that write tutorials will be featured o ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. This week: A New Year's Eve cell phone phot ...more
Del The Funky Homosapien ft. Khaos Unique "Proto Culture" Chorus:] Let me tell you about the Proto Culture If you don't know the culture, here's the whole structure We've had enough of the lackluster-trust us We get the kind of games you can't rent at Blockbuster [KU:] Ga ...more
This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last fo ...more
This Null Byte is the first part in a mini-series on the art of Social Engineering. I will be teaching you how to effectively defend yourself against it. What is Social Engineering? Social Engineering is the art of hacking humans. It's when a person is manipulated into doing ...more
Final Fantasy 14 the MMO is now live. The special edition priced at $75 enables people to play eight days earlier than people getting the regular edition, which comes out on September 30th. Mine arrived yesterday and here are some pictures of what's inside the special edition ...more
Please share this info with all your facebook friends. It's not just Farmville players that are affected by scams and spam! This post will help you keep your facebook account clean and safe. We start by showing you a scam and discussing what is real, then we show you how to re ...more
Hallelujah, a miracle tool has been released to the world. This Windows/Mac tool is called Spirit and it enables you to jailbreak any iPhone, iPod Touch or iPad quite easily. And Gizmodo is all over it, with an in-depth guide on exactly how to do it. Some of you may be hackin ...more
If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! mo ...more
Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. A ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. Thanks to all of our active moderators and ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. Thanks to all of our active moderators and ...more
Welcome to the Google+ Insider's Guide to all things Google+. We're dedicated to keeping you updated with all the latest news, tips and tricks on Google+, and this official index will serve as a one-stop catalog of all our How-To articles, as well as all the news & updates we' ...more
Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called ...more
Ok first thing first, you need to download the HackPack. In there is necessary things I use in the video. If you are on XP you must install .net frame work. ( the dotnxfx file) vista users don't have too. Link include: http://www.mediafire.com/?mddzxxf12nl http://www.sendspa ...more
In November 2016, the RCS Universal Profile (Rich Communications Services) was introduced. The technology takes text messaging to the 21st century, emulating many of the features found in IM apps like WhatsApp and iMessage, but working through your phone number like regular SM ...more
Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or ...more
As the COVID-19 virus continues to spread, counties, cities, and states are closing down businesses, events, and schools that aren't absolutely necessary. Some companies around the US are recommending or requiring employees to work from home during the coronavirus pandemic. If ...more
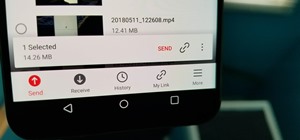
Many apps, including Facebook, Twitter, and Facebook, do not let you download videos, even if they are living on your own account. Saving these videos usually requires a third-party app or screen recorder, which is inconvenient and can result in loss of quality. However, TikTo ...more
With the same starting price as its predecessor and a nice list of improvements, the OnePlus 6T is a great buy for a number of reasons. But for many Android users, the main selling point for the latest OnePlus flagship is how easy it will be to root and mod the device. We jus ...more
The Nokia 6 has been out since January, releasing in China before having a slow trickle of releases throughout the year. Despite announcing a global release, the United States never received a street date for the smartphone, and for all this time, Nokia has left us out to dry. ...more
Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali. I can't see any tutorials explaining this Hack/Exploit, so, I made one. (Still ,you may already know about this) Step 1: Fire-Up Kali: Open a terminal, and make a Troja ...more
With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassin ...more
There's something about alcohol that compels you to contact people. Most of the time, the drunken calls or messages you send out will have you cringing hard tomorrow morning. But if you have a jailbroken iPhone, you can help prevent this potential embarrassment with a free twe ...more
You can mod every aspect of your phone's software with root, but if you want to make changes at the hardware level, you'll need a custom kernel. If you've looked into custom kernels before, one name undoubtedly kept coming up: ElementalX. It's easily the best custom kernel out ...more
More details about Google's latest Taimen device have been revealed all thanks to Geekbench. We already know that Google has been working on a tablet-like third device next to its original Pixel 2 lineup. Though, Taimen is not confirmed to be part of the Pixel 2 lineup. Taime ...more
Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, w ...more
One of the coolest things about Android is the massive development community behind it. These developers keep on cooking up new things even after official support has stopped for an older device. It breathes new life into somewhat forgotten devices, which is always great news. ...more
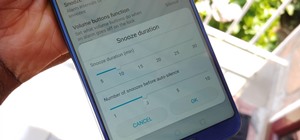
While the Galaxy S10+ is a fantastic device, the biggest gripe I have with it is the curved display. Yes, it adds to the aesthetics of the phone, but it makes the phone prone to accidental touches. Thanks to a recent update, however, this is a problem of the past. Edge Touch ...more