In this tutorial, we learn how to use salty hashes to keep passwords secure. A hash is stored in a database that is hashed with an algorithm, so not everyone can see exactly what your password is. When you type your password into a website, it doesn't actually register as word ...more
General Electric isn't known for their Christmas lights, but maybe they should be, because their GE Color Effects are pretty awesome. Especially the LED Color Effects G-35 String sets. And especially when someone named Darco hacks them. Darco, whose real name is Robert Sun Qu ...more
WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling. First, U.S. Senator Joe Lieberman swayed Amazon's decision to stop hosting WikiLeaks. Then, Tableau Software removed graphs from th ...more
Update: If you're running iOS 7 or higher, you'll want to check out the new way to fully close your background applications. With the newest version of iPhone firmware, you will be able to multitask. Finally, Apple has given us the ability to access more than one program at o ...more
According to Amazon.com, Kindle was their best-selling item this year, which means many, if not all of you are playing with a brand new Kindle on Christmas Day. Of all of Amazon's Kindle models, the Kindle 3 (6") will be the most common eReader in everyone's hands, either the ...more
It's 1976. The hottest arcade game on the market is Blockade (or Blokade), an 8-bit maze game for 2 players. You and your opponent must move your characters around the screen in 90-degree angles, leaving a solid line behind them. Whoever runs into one of the solid lines first, ...more
In this episode of Full Disclosure we are explaining the website attack known as Cross-Site Scripting (XSS). Cross-Site Scripting is a type of security vulnerability that affects web applications that do not sanitize user input properly. This kind of vulnerability allows an "a ...more
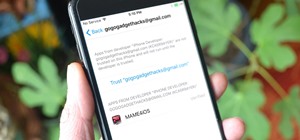
Like the recent XSS 0day exploit found in the Mac and Windows versions of Skype, a similar one has been found in the Skype app for iPhone. The vulnerability allows an attacker to send a message that contains malicious JavaScript code in the "Name" parameter. This code can stea ...more
World of Warcraft is a super fun game, but as anyone who's ruling the game at level 80 (the level cap at the moment) will tell you, getting to 80 is a long and sometimes tedious journey. So why drudge along fighting bosses and other supernatural phenomenon for eighty levels w ...more
Hacking a bike lock is something that you may need to do sometime if you forget your combination or maybe just didn't bring the key for the lock with you. You should never hack a bike lock to steal anything and should know that this tutorial is for informational purposes only. ...more
As the image above suggests, it takes expertise (and perhaps sleuth) to actually hack into somebody's facebook account. But to steal a friend's password? If you're lucky, a simple mind game will do the trick. Read and learn: Image credit.
In this article, I'll show you how to easily "hack" Facebook, Twitter, YouTube, and any number of similar account types with an Android app called FaceNiff. FaceNiff allows you to sniff and intercept web session profiles over the Wi-Fi that your mobile device is connected to. ...more
There's an easy time hack available for Candy Crush Saga that let's you bypass the time restrictions to you can play more games faster, and this video guide from KiboshGaming will walk you through it on both Android and iOS devices. Video: . There is no real "hacking" involved ...more
Worried about not being able to get Cydia on the 3.0 firmware? Never fear! Hackers are here! Check out this video to learn how to jailbreak your iPhone using redsnow to get Cydia. With Cydia, a whole world of iPhone and iTouch hacks and cracks are at your fingertips! iPhone 3 ...more
This is a nifty tutorial guide on how to tether your hacked iPhone or iPhone 3G to a windows computer for use as a high speed modem. Just Jailbreak your iPhone using one of the many tutorials on WonderHowTo, and install 3proxy. This video explains the rest of the configuration ...more
Want to use the iPhone Video Recorder 1.2 without restrictions? Then check out this video tutorial to see how to install the hacked free version of it on your Apple iPhone for never-ending video recording. Make your own movies with this cool little application.
This video clip shows you how you cannot fool any candy machine and debunks the mythical paper hacks in detail. Some say it works, some say it doesn't. Well, check out this video tutorial and decide for yourself what believe. It might just be easier to steal candy from a baby.
This is a terrible prank to pull on a friend. Destroy their iPhone software with a couple of quick hacks.
If you are having trouble getting your hotmail on your iTouch, check out this video. It's safe and easy, without giving somebody your personal info. This is the 32GB version, but it should work for all iTouches as well as the iPhone.
Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills. Submit your best shot to our weekly competition for a chance to win an awes ...more
Hey iPhone jailbreakers! Did you jailbreak your 2G/3G iPhone and then update to firmware 4.1? Yeaah. Now you've got a shiny little brick, don't you. Well, this video will help you get free (again) from the clutches of those clever guys in Cupertino. Apple doesn't like people m ...more
In this video, we learn how to find your IP address. First, start up your computer and open up your web browser. Next, you will type in the site: WhatIsMyIPAddress. Once you do this, you will be led to a new site which will load up your IP information at the top of the page. O ...more
Check out this amazing use of AR via Wired http://theleakinyourhometown.wordpress.com/ “the leak in your home town” is an iPhone app that lets users see the BP Deepwater Horizon oil spill whenever they see a BP logo. A user simply launches the app and aims their iPhone’s cam ...more
When Apple first released the iPad, they only offered a WiFi enabled version. This would make your iPad similar to an iPod Touch. If you are one of the impatient Apple fans who couldn't wait til 3G, check out this tutorial. All hope is not lost for using iPad on the go! In th ...more
If you've ever heard software piracy terminology being discussed, I'm sure the term KeyGens came up. KeyGens is short for key generator, which is a program that exploits algorithmic faults in software by generating software license keys that appear to be genuine. Normally used ...more
You may have asked yourself, "How do hackers take my password, if the website owner can't?" The answer is simple. When a website stores your login password for the site, it is run through a cryptographic hash function before it enters the database (if the website isn't Sony). ...more
Anybody who spends most of their day on the internet should know all about lulz. Lulz are most often jokes made at the expense of web users, as popularized on 4Chan. Today, a consortium of hackers called LulzSec is attempting (and in some cases succeeding) in efforts to shut d ...more
We'd like this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with (anyone want to donate one?), we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a ser ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. This week: A phoneography challenge on silh ...more
Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills. Submit your best shot to our weekly competition for a chance to win an awes ...more
The passcode, or the four-digit code you enter in order to access an iPhone or iPod touch, was created to ensure security and prevent hacking. But what if you haven't touched your iPhone in a month and you simply don't remember what your passcode is anymore? Don't fret; just ...more
Let's be honest. Who actually pays for their music these days? Take your internet piracy to the next level and become a certified bucaneer by watching this video on how to get free applications on your iPhone and iPod Touch. There are two ways to get these free apps: 1. Downl ...more
The Internet is full of crooks just waiting and waiting for the chance to steal your information. One way that people are getting into your system these days is with fake or rogue applications. These viruses sneak themselves onto your PC either through hacked websites or when ...more
Hacking into computer systems to steal passwords could be a bit complicated for the average everyday joe, but for all of your tech illiterate folks out there, there's any easy way to get that password, and all it takes is a camera. Check out this con video tutorial to learn h ...more
The holidays are here and all of us here at Phone Snap hope you're spending them under a nice warm roof with some yummy food and great company! For this week's Phone Snap challenge, we want you to utilize your cell phone to capture some holiday spirit. Whether it be the gifts ...more
It is always a bittersweet moment to find yourself looking back on the fond memories that seem to have taken place in the distant past. When your favorite song from 10 years ago comes onto the radio, or when a sudden scent reminds you of the summers you spent as a child—these ...more
Using an analog camera to create multiple exposures is a technique that has long been in practice throughout the history of photography. Pressing the shutter button twice will superimpose the exposure of two different images onto the same piece of film. Sometimes done in an ar ...more
Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills. Submit your best shot to our weekly competition for a chance to win an awes ...more
Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills. Submit your best shot to our weekly competition for a chance to win an awes ...more
Security awareness seems to be a hot topic these days on the web, with developers making apps and devices that can hack networks and machines with just a few clicks. But these applications aren't only exploiting security flaws in systems and networks, they're being used by ama ...more
Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills. Submit your best shot to our weekly competition for a chance to win an awes ...more
Ever had your car broken into? Or worse, your apartment? Ever been pickpocketed? Handheld electronics—iPods, iPhones, iPads, GPS devices, digital cameras—are easy to snatch, light to carry, and useful to most. And when they're gone, they're gone. Until now. Thanks to develope ...more
Looptaggr is an ingenious drive-by tagging device by Ariel Schlesinger and Aram Bartholl. It's cheap, quick and easy to make, and even speedier to use. Cities and small towns across the world may be littered with graffiti mayhem in no time at all... From Looptaggr, how to make ...more
From Lifehacker's Tips Box, four short-cuts to life's small problems, urawaza-style: No Iron? If you're out an iron and you happen to have a hair straightener hanging around, it will do the trick (quite nicely). Also, works well as a dually useful traveling item, ladies. Warn ...more
This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last fo ...more
I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to rememb ...more
WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most ...more
Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information y ...more
When was the last time you took some time out of your day to play with your favorite action figure? Or build an entire town of Legos? Well, it’s time for you to dust off that old toy chest for this week’s Phone Snap challenge! To kick off Phone Snap’s very first weekly photo ...more
Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills. Submit your best shot to our weekly competition for a chance to win an awes ...more
Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills. Submit your best shot to our weekly competition for a chance to win an awes ...more
What's cuter than a puppy? Not much, especially when you omit all the peeing, barking and furniture chewing, as Remedie Studio did with this sweet time-lapse homage to their beloved pup. Below, watch Dunder the German Shepherd grow from 8 weeks old to 1 year in 40 seconds. Ins ...more
Understandably, the tragedy in Japan has substantially risen the level of worldwide radiation-related hysteria. So much so, as an alternative to stampeding health food stores for iodine tablets, crafty individuals and organizations are hacking together personal radiation detec ...more
Have you ever seen one of those Snapple machines with the lever coin return? I will show you how to get free drinks or snacks out of this type of machine. Don't Miss: 9 Vending Machine Hacks for Free Drinks, Snacks, & More Take your dollar and put it in the machine. Have a f ...more
Cheating ruins everything. Cheating makes game play unfair for others who may be truly competitive and strategic. Cheating makes others disrespect and un-friend you. There can be unforeseen consequences, like getting viruses, trojans or your account hacked from downloading a c ...more
Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. A ...more
Have you ever noticed that whenever you setup your voicemail account after getting a new cell phone number, it asks you to create a security pin to access your voicemail from other phone lines? When you call your home or cell number from another phone, after a few rings your ...more
Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their c ...more
Hello readers again! Sorry about the long wait (scary computer problems). Today I am going to talk to you about security problems on Wizard101. I have recently encountered many security flaws on Wizard101, including hacking, frauding and other crazy things. Wizard101 is the ta ...more
Oh, LifeHacker, we love you. You've brought us so many handy HowTo's: Hack Wireless Internet, Bypass Blocked Websites, Convert a Laptop Into a Projector, Watch TV & Movies on the Web For Free, 10 Must-Know Google Privacy Settings, and more. And now, another great one: LifeHac ...more