View our webcast to learn about the advantages of using a comprehensive Active Directory recovery solution -- and view a product demo. With Quest Recovery Manager for Active Directory, recovery time can be reduced from hours to minutes!
Wouldn't it be awesome if your glasses could detect when it's bright outside and automatically darken? Well, the technology has been around for a while, but it'll set you back a few hundred bucks. Dean Segovis over on Hack A Week decided to make his own by hacking a pair of a ...more
Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. ...more
Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what appli ...more
Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this t ...more
Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester. On the other hand, there are many here who come to Nu ...more
Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even ...more
Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, ...more
Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. ...more
Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will. Torrent clients like uTorre ...more
The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data. Apple introduced so ...more
When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you ...more
Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT se ...more
Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, onlin ...more
Want to share Internet connectivity between two computers without a wireless network but have an extra CAT5 ethernet cable? You're in luck. This home networking how-to will show you what to do to get your machines talking not only to one another but the web at large. Internet ...more
The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an ent ...more
Few Bluetooth users realize that Bluetooth headsets can be hacked or otherwise exploited to a remote attacker the ability to record and inject audio through the headset while the device is not in an active call. SANS Institute author and senior instructor Joshua Wright demonst ...more
Interested in using the Active Directory Administrative Center on a machine running Windows Server 2008 R2? This clip will show you how it's done. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in j ...more
Interested in installing Active Directory Domain Services (ADDS) on a machine running Windows Server 2008 R2? This clip will show you how it's done. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in ...more
This Null Byte is a doozey. On Sunday, September 19th, an exploit for the latest Mac OS X 10.7 "Lion" was discovered by Patrick Dunstan. This exploit allows for an attacker, even remotely, to request to have the root user's password changed without knowing the password to the ...more
To the displeasure of many loyal Firefox users, Mozilla has been deploying what seems like a new marketing strategy to "catch up" to Google Chrome. I have no idea if this is because the version number is higher than theirs, but it is downright annoying. It's not all complaints ...more
Null Byte is looking for forum moderators! Last Friday's mission was to accomplish solving HackThisSite, basic mission 9. This mission delves a little further into Unix commands and remote directory traversal (which is just a fancy term for going through folders blindly). Th ...more
Welcome to the 10th Community Byte session for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers ...more
Warnings i cant be held responsible for any illegal act done by anyone but myself and there are copyrights so notise that taken the trademarks or copyrights are strigtly prohibeted by law and will be punshied by law and i or my partners cant be held responsible for sudo camma ...more
In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, c ...more
Microsoft has informed HoloLens users that the company will begin rolling out a mandatory update for HoloLens as part of its Windows 10 October 2018 release that brings a number of new features and quality-of-life improvements to the headset. The update's new features are hea ...more
On Monday, at its annual Build developer conference, Microsoft revealed two new apps for the HoloLens apps. The apps, Microsoft Remote Assist and Microsoft Layout, will be available to HoloLens customers as a free preview for a limited time starting on May 22. Remote Assist ...more
Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal. This ...more
When Microsoft unveiled Mesh a couple of weeks ago, the move revealed a major part of Microsoft's next steps toward dominating the augmented reality space, particularly with regard to enterprise customers. But aside from the general details contained in the announcement, what ...more
With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Pyth ...more
While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers di ...more
Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire. Those packets can be examined for ...more
Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associa ...more
The peaceful, pastel and doily-filled world of Pinterest is my oasis. My account conveys who I want to be and what I want to accomplish, so the idea of someone hacking it and ruining my favorite escape for me is heartbreaking. Fortunately, Pinterest has updated its security, i ...more
Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often ...more
Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, ...more
A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge. The goal in this article is to acquire a target's .plist file which contains the ...more
Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on. ...more
Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, a ...more
Cheap deals, great games, and a stable, easy-to-use environment are just a few of the reasons why Valve's online game distributor Steam is so popular. That and it's a great place to interact and play with other gamers, which is why it recently broke records with over 6 million ...more
Transparent status bars and new lock screens weren't the only new additions that came with the Galaxy S3 KitKat update. Along with better battery life and a smoother user experience, we got a new toggles design and recent apps menu. Of course, Samsung's infinite wisdom left th ...more
Welcome back, my neophyte hackers! Several of you have written me asking how to crack passwords. The answer, in part, depends upon whether you have physical access to the computer, what operating system you are running, and how strong the passwords are. In this first install ...more
Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial. THC Hydra is very prominent online brute-force tool and ...more
Welcome back, my tenderfoot hackers! This is the third installment of my series on basic Linux skills that every hacker should know. Although some hacking tools are available for Windows and Mac, every real hacker uses Linux—for good reason. Make sure to check out Part 1 and ...more
Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective. In addition, by knowing what files ...more
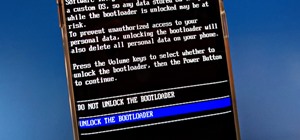
For modders, there are few tools more important than TWRP. TeamWin's custom recovery makes flashing mods like Magisk, Xposed, and custom ROMs incredibly easy, and it lets you root your phone at the press of a button. On top of that, it can make complete backups of your phone i ...more
It's been little over a month since the official release of LG's latest flagship phone, the LG V20. Despite a few minor hiccups, the V20 has been attracting attention from all over for being an amazing phone. But like with most Android phones, there's no better feeling than ro ...more
Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, ...more
Welcome back, my newbie hackers! We've already saved the world from nuclear annihilation and covered our tracks afterwards, but the world is still threatened by a malicious, megalomaniacal dictator with missiles and nuclear weapons. We need to keep a close eye on him, so in ...more
Today, Facebook Messenger is rolling out Discover, a feature that helps you chat with companies and locate nearby businesses of interest to you. First discussed in April at Facebook's developer conference F8, Discover is finally available for public use. During a speech at F8 ...more
Thanks in large part to our phones, many of us don't get the recommended eight hours of sleep. In Android Pie, Google introduced a feature called "Wind Down" that aims to help combat this. However, thanks to a creative app developer, we don't need to wait for Android 9.0 to en ...more
Putting your Galaxy S9 in Immersive Mode lets you truly enjoy the gorgeous display that Samsung is so famous for. You can't have it set on at all times, however, so you'll still have to deal with the status and navigation bars that cut the phone's aspect ratio down to that of ...more
When Google added new security measures to Android Marshmallow, it had a lasting impact on the entire process of rooting. These measures prevent the the Superuser daemon (the process that handles requests for root access) from getting the permissions it needs to do its job at ...more
Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as ...more
The Samsung Galaxy S8's almost bezel-less display is truly a sight to behold, especially when set to Immersive Mode. While transparent when on the home screen, the navigation and status bars on the S8 will often turn opaque depending on what app you're using at the moment. Thi ...more
Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requi ...more
Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array o ...more
With all of the top-notch specs that the Galaxy S5 sports, the only minor quibble users have had with its hardware is the speaker situation. A front-facing earpiece is used for phone calls, but all other media is restricted to a single rear-firing speaker. Developer langeveld ...more
Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians acro ...more
PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's comput ...more