You can't get this hack without using Cheat Engine to get it. If you do have the most current version of Cheat Engine on your computer, use this method to not only give yourself unlimited sunshine, you can also get instant seed refills.
Earning more money in YoVille doesn't have to be hard and take forever. You can make more cash simply by hacking your way to success with the notorious Cheat Engine program. How to hack YoVille! from Zynga! This video tutorial teaches you how to hack YoVille coins with Cheat ...more
Download Cheat Engine You can get Cheat Engine here. After downloading, install it on your computer. Log Into Christmas Crunch Log into your Facebook account and go to MindJolt's Christmas Crunch game. Open Cheat Engine / Play Game Open the Cheat Engine and start the game ...more
One you understand how a subnetwork works on an Internet Protocol (IP) network, creating one becomes very easy. In this five-part video, you'll learn about IP address and subnets, along with creating an IPv4 (IP version 4) address using Class C, which leaves each network with ...more
How to hack Click Challenge! v3. Master your clicking skills. For this clicking flash game, all that you need is your computer mouse and your hand. Just don't overdo it though or you may experience arthritis at an early age! Watch this video tutorial to learn how to cheat Cli ...more
Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can l ...more
Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa d ...more
Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all co ...more
Firewall is necessary to protect a computer network from hostile intrusions. You can easily setup your Firewall setting. This video helps you to do it. Video: .
Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it. Even if you aren't a Windows user, it's good to know how command prompt works b ...more
As a multitasker, I've embraced the hustle and bustle that has filled my life. I'm constantly doing several things at a time, while looking for shortcuts to finish all of these things quicker than before. I brush my teeth with my cell phone in hand and drive to work with break ...more
For the most part, transferring files from your computer to your Nexus 7 (and vice versa) is a simple process. Just hook up your tablet to your computer with the USB cable and transfer. However, most of the time you'll need additional software on your computer to do this, and ...more
Tesla CEO and founder Elon Musk has repeatedly said this year all Tesla models made since October 2016 have the requisite hardware for "full self-driving" capabilities, yet the company has reportedly begun to add a second graphics processor (GPU) to its computer platform for A ...more
With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years h ...more
In my last article, I discussed: How to install xampp How to install wordpress on xampp The following article describes how to access that wordpress site both remotely and from a different computer on the same network Step 1: Edit Httpd-vhosts.conf File Assuming you're using ...more
Since Ive started to learn about nmap and metasploit and other tools I was learning well but I had one problem, I had nothing to practice it on. As a result I asked someone about my problem and they told me about Vulnhub. It's a great way to practice. Its good beginners and pe ...more
There was big news today from Google, Apple, Volvo, and Nvidia regarding their self-driving efforts. Avis Will Service Waymo's Driveless Fleet Google parent Alphabet's Waymo has selected Avis to service its growing fleet of driverless cars. It now seems Waymo has all of the ...more
As the protectors of all things good, the Federal Communications Commission is usually busy behind the scenes pissing off Slim Shady, giving out fines for indecent nipple exposure at certain halftime events, and warning the NSA about losing any "confidential" phone information ...more
Tesla's Autopilot self-drive interface in its new Model 3 signals the carmaker is already prepping its cars for Level 4 driving years ahead of the competition. The incremental-yet-revealing modification consists of the Model 3's Autopilot gearshift option. Unlike the cruise c ...more
The large, dome-shaped LiDARs that have become a fixture on driverless car prototypes are expensive and notably ugly. And yet, these unsightly devices should remain planted on driverless cars, even when they become available in commercial fleet services across the country in a ...more
Like insurance, it's always better to have a computer mouse and not need it than to need it and not have it. Honestly, I don't want to carry around a clunky mouse with my laptop, so I don't. I do something else, something more convenient. I use my Nexus 7. If you want to give ...more
Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/ne ...more
Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an a ...more
I'm still amazed by all the things some people just don't know. Script-kiddies often refer to Metasploit if someone asks them how to hack a computer because they think there's simply no other way. Well here I am today trying to increase your set of tools and -of course- skills ...more
Hello y'all! I apologize if this question has been solved somewhere else, but I have looked around on Google, Yahoo, and Null Byte and have not been able to find any working solutions. I've been trying to set up my first ever virtualbox guest (Kali Linux 2.0), but I'm having ...more
Welcome back, my greenhorn hackers! Congratulations on your successful hack that saved the world from nuclear annihilation from our little, bellicose, Twinkie-eating dictator. The rest of world may not know what you did, but I do. Good job! Now that we hacked into the malevol ...more
Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post. Let me introduce myself first ! I am from Greece, I am working as a network engineer and I am into system and network administration but definitely ...more
Cruise Automation, the driverless car startup General Motors (GM) bought for $1 billion in 2016, is readying a formidable fleet of robo-taxis for rollout in cities throughout the US. But when it comes to details about how the company plans to realize these lofty goals, it's be ...more
There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely s ...more
Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard. So in the last tutorial we did what we did without the use of our default gateway. To be honest, in really ...more
With Google's recent release of the Software Developers Kit for Chromecast, Android gurus now have a roadmap of sorts to guide them in adding Chromecast functionality to their apps. The results are beginning to pour in. Koushik Dutta, of CyanogenMod and AllCast fame, has just ...more
On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated ...more
"Unfortunately, no one can be told what the matrix is, you have to see it for yourself." That's the line just before Morpheus gives Thomas Anderson (aka Neo) the red pill, finally opening his eyes to the tapestry of code that has veiled his eyes for his entire life. It's a se ...more
Tesla hopes high-level personnel changes will help it gain an edge in neural network knowhow for its models' self-drive features, following the replacement of its Autopilot chief and the appointment of a recent Stanford grad to head its AI and Autopilot vision research. To th ...more
Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc. Maybe you forgot or lost the password to your Windows Admin account, this guide wi ...more
I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started... Your router is blocking outside traffic from coming inside the network for security reasons (Kind of, like, a firewall level), ...more
Most newer computers come with a webcam, but if you're using an older system, you may not have one. If you only need to use a webcam occasionally, it may not be worth putting the money into, so why not just use your smartphone? There are a few apps out there that can help you ...more
SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network ...more
With the the general computer users understanding of Information security rising (at least to the point of not clicking on unknown links), and operating system security getting better by default. We need to look for new and creative ways to gain a foothold in a system. Luckil ...more
Hello my fellow hackers, Welcome to my republished revision of the ruby programming language, Part 1. Today, we will try to build an ftp cracker in ruby: This is going to be a quick one since OTW has already made one in python and we are gonna look upon that to create a simil ...more
Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to se ...more
Android Debug Bridge, or ADB for short, is a very powerful utility that can remotely execute commands on your Android device. This remote terminal interface, however, is not very "remote" at all. You have to be tied down to your computer to use it, since a USB cable is normall ...more
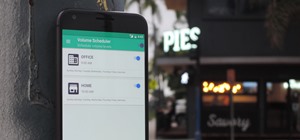
Hi there, Elites Welcome to my 6th post, This tutorial will explain how to hack windows, using a program (No-IP) and windows's inbuilt Task Scheduler. Meanings... Task Scheduler: It is a program, inbuilt in windows, which allows us to create some tasks and execute them at s ...more
Microsoft's HoloLens comes with helpful features for capturing video and photos, but sharing whatever you record isn't as straightforward as you might expect. So here are the many ways to get your media off the device to share with the world. Step 1: Take a Picture or Record ...more
This is a how to to change any user password on a windows 7 computer. If you forgot your password you can change any account password even if you are locked out of your account. Warning I am not responsible for any damage done to any computer in the process of this hack or an ...more
This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartblee ...more
If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed. Spooky Action at a Distance If you need to prove you've got remote ...more
Most of the time, if you're actually using your computer, it won't just go to sleep on you. But when you're reading a long article or watching a video and don't move the mouse or use the keyboard for a while, the screen automatically dims or goes into sleep mode. It may not b ...more
In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffi ...more
You can easily lock any folder on your Windows computer with a simple Notepad hack. By creating a batch file, you can hide a folder and require a password be entered before it becomes visible and accessible. This is a great tool for locking sensitive information, like pictures ...more
Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely. Left an important document on your work computer? Want to run a legacy x86 desktop app from your Surface? You can use Remote Desktop ...more
Want to search through your Samsung Galaxy S III or other Android smartphone using only a web browser? Thanks to XDA-Developers member Metal Droid, you can now access and download anything from your phone through any browser on your computer using DroidXPlorer. With DroidXPlo ...more
While obvious, it's a lot more difficult to hack into a locked computer than an unlocked computer. As a white-hat hacker, pentester, cybersecurity specialist, or someone working in digital forensics, there's an easy solution — make it so that the computer won't fall asleep and ...more
Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities. One of the cardinal rules of hacking is: "If I ca ...more
This is finding some of your vulnerability using Lynis. This tool Lynis is used on Unix and Linux type operating systems (sorry windows). So lets get started What Is Lynis and How to Install Lynis is a security checking tool which can help you harden your security defenses. ...more
UPDATE: Entries are now closed. Thank you for participating! Next Reality is where we help you literally 'see' into the future of augmented reality, and to help with that mission we're offering three free pairs of Snap Spectacles 3 to three lucky readers who sign up for the N ...more
Just recently, I was experimenting with a dual-boot Windows setup, and somehow managed to wipe my primary Windows installation in the process. "Why," I asked myself, "Why didn't I make a backup before I started this?" Still to this day, I'm going through the painstaking proces ...more
Keyboard shortcuts are super useful for multitasking and saving time on the computer. But if you're like me, you might only know a few of the million of keyboard shortcuts that are out there. I pretty much know the most basic of basic shortcuts: copy, cut, paste, save, select ...more
You probably use your smartphone to mostly surf the web, play games, and communicate with others, but there's so much more it can do. Thanks to integrated features and third-party apps, you can seamlessly control things around your home, including your TV, tablet, Bluetooth sp ...more
Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries. And while those films hav ...more