Cycling accidents are more common than you think. In the past month, two men have been hit and killed while cycling in New York City. I even saw a cycling accident occur yesterday morning here in NYC. It's dangerous enough to be cycling in populated areas, it's made worse by p ...more
Netflix added the ability to download TV shows and movies on Android and iOS for offline binging back in Nov. 2016, and the process is the same as it is today. So if you anticipate having some downtime to catch up on Narcos or give Bright a try when you'll be away from a secur ...more
The latest video game developer to hit the scene is a hotel chain, and they're offering big prizes for high-scorers. That's right, the W Hotels released a free game that can be played on your desktop, tablet, or smartphone called Belle the Bear. A Frogger-style game, Belle th ...more
The company that brought us a BB-8 droid controlled with the Force — okay, just a high-tech wristband — is releasing its take on Spider-Man. Toymaker Sphero collaborated with Marvel to release an app-enabled Spider-Man toy equipped with numerous features, as well as games for ...more
Update 6/15: Netflix responded to our request for comment: This [download limit] may vary depending on the title and licensing agreement. There may be limits to the number of titles from the same licensing agreement that you can download at the same time. We will only enforce ...more
We all know the internet isn't exactly a safe place. While plenty of its users are innocent and kind, you won't last long unless you treat every new screen name like a criminal (we're all this cynical while surfing the web, right?). Well, that cynicism is proven correct today, ...more
There's never an Apple announcement without some good ol' anger and backlash. To be fair, Apple received some really positive feedback from parts of the iOS 11 presentation at WWDC back in June. Fans had been waiting for years to customize the Control Center, as well as for n ...more
WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still! The messaging giant added an encryption to iCloud backups to prevent a data privacy breaches loophole. This coul ...more
Even though your phone has a built-in media player, it's got nothing on VLC. The popular third-party video player supports virtually every codec and file format, and even better, you can use it to stream movies, shows, and other video files from your computer to your phone. I ...more
Once upon a time, Flash games reigned as some of the best entertainment the internet had to offer. But then came the smartphone, which quickly overtook this genre with similar games that you could play no matter where you were. If you yearn for the good old days, though, you'l ...more
We all know Google's Image Search to be our trusty little companion when it comes to browsing through ideas on the web. Now, Google is adding on "style ideas" to its search feature to help you boost your "style IQ" every time Google catches you snooping through new handbags on ...more
Pinterest, a worldwide catalog of ideas shared by over 175 million users every month, is dominated by Android users, who are now the app's fastest growing group. Pinterest has since taken notice, and has started to incorporate handy home screen shortcuts for users with Android ...more
No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks. Most iPhone and Android phones run on a Broadcom Wi- ...more
Samsung's new Galaxy S8 can turn into a PC with its DeX dock, but while that may sound like the future of mobile computing on the surface, there are definitely a few issues with the entire setup. The Samsung Desktop Experience (DeX) dock was debuted alongside the Galaxy S8 on ...more
One of the biggest things that differentiates Android from iOS is the app drawer. Instead of the operating system just tossing all of your app icons into a cluttered heap on your home screen, most can be tucked away neatly in the app drawer, which, in essence, is very similar ...more
Let's say you gave your Wi-Fi password to your neighbor a while back, under the assumption that they'd only use it while they were at your house sharing stuff via Chromecast. But now, your connection is slower than it normally should be, and you have this sneaking suspicion th ...more
There's no question about it—Skype is one useful program, but has always been lacking in the mobile department. On your desktop, Skype works just fine and all of its options are available for usage. However, the same cannot be said for Android. On Android, you can't even chang ...more
Bluetooth 5 was announced and made officially available on December 7, 2016. It comes with a handful of improvements to speed, range, maximum device connectivity, and anti-interference from other nearby devices. While this might be great for those special few who use Bluetooth ...more
All across the country, retailers like Best Buy, Target, and Walmart are gearing up for their Black Friday sales. Brick and mortar stores are already packed to the brim with inventory in anticipation of the craziness that will strike as soon as the doors open the day after Tha ...more
Kryptowire, a company specializing in mobile security solutions, released a report on Tuesday, November 15 that exposed firmware in a number of Android devices that was collecting personally identifying information (PII) and uploading it to third-party servers without users' k ...more
A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists righ ...more
Google Assistant just got a lot more powerful thanks to IFTTT. The automation platform, whose name stands for If This, Then That, connects your favorite online services and smart devices to one another, allowing for a seamless experience with many different gadgets—and Google ...more
There may be no other crustacean with as many names as the crawfish: crayfish, crawdad, crawdaddy, mudbug, Florida lobster, spiny lobster, rock lobster, and freshwater lobster (to name a few). But no matter what you call it, there's no denying that it's a popular delicacy in t ...more
When you're browsing the internet on a computer, you just need to hit Ctrl F (or Command F) and type something out to find all instances of that word in the webpage. It's a handy feature baked into most browsers (nearly all mobile browsers have a "find" feature, too), but unfo ...more
Logan's Run is one of my favorite movies of all time. The dialog is cheesy, the set design and special effects are wonky, and the main villain looks like he was conceived and built by an eighth grader in shop class—oh, and his name is Box. But there are plenty of things to li ...more
If you're looking to customize your Android beyond its stock options, things can get confusing quickly. One of the best places to get into developer mode is the XDA forums. XDA is home to hundreds of independent Android developers, all eager to showcase their wares. Everythin ...more
No doubt you internet-savvy folks have seen the incredibly beautiful rainbow bagel going viral all over the country—and if not, let me educate you on its multicolored brilliance. Crafted by the brilliant bakers at The Bagel Store in Brooklyn, this cheery creation has actually ...more
Whether you're ready to admit it or not, we've all got our alter egos—especially when it comes to the internet. Perhaps you have one Facebook account that you use publicly, while maintaining a second account for more private interactions. But this isn't exactly the easiest th ...more
Android 6.0 Marshmallow added a new permissions system that can make your digital life much more secure. Unlike previous versions, apps now have to ask for your consent before they can access certain data, which puts you firmly in the driver's seat. As if that weren't enough, ...more
Before you sell or give away an old iPhone, Find My iPhone, which works in conjunction with Activation Lock (Apple's anti-theft system) needs to be deactivated from your iCloud account. This also applies if you've lost your passcode and are locked out of the device, if you're ...more
Android has a built-in browser called WebView that any app can use, which makes it easy for developers to display webpages without actually having to build an internet browser into their apps. But WebView is a stripped-down, bare bones browser with no ties to Android's default ...more
Microsoft's Windows 10 has proven to be a solid release by Microsoft, with faster adoption rates than its predecessor builds. The seamless integration of cloud services and tweaks both major and minor make using Windows easier than ever now. And it's almost enough to forget yo ...more
Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels. "Why would I do that?" One might ask. Good question m ...more
Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series. At this point many of you may be asking, "What the heck does it mean to hug the web?" Don't be discouraged, as this is not a hacking ...more
My French press is one of the most important tools in my kitchen. It's indispensable, and it's no small exaggeration when I say that I use it on a daily basis thanks to my coffee addiction. However, it gets used for a lot more than just my morning cuppa (and my second morning ...more
Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin. If you have not yet read previous posts pl ...more
Piracy, it can be argued, is the scourge of the internet. But when it comes to music, sometimes it's best to give a listen to a track or album before deciding to spend your hard-earned money on fully supporting it. Unfortunately, there are few good ways to do this without exp ...more
I've recently been on holiday in Europe, staying in a hotel that was part of a big chain that included many in the local area. A quick review of the wi-fi within range of my room showed that there was another in the chain that was in range of my Yagi Turbotenna, which naturall ...more
Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record. OTR does all the right things to make your instant messa ...more
Windows 10 marks a new era for Microsoft with the return of the Start menu, the demise of Internet Explorer, and the introduction of the remodeled Windows Store. While the new Windows Store is meant to bridge the gap between every device running Windows 10, many apps have yet ...more
If you've been watching the latest USA TV Series Mr Robot, you will have seen the Raspberry Pi used by Fsoeciety to control the HVAC system. OTW covers this very well here with his take on setup they may of used. However I had a very different take. A netcat bind shell is gre ...more
Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes. But while Tor is great for desktop users, since they can simply install a Tor browser or plugin, it's a bit more c ...more
Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity! Social Eng ...more
Baking a cake is relatively easy... if you happen to have a cookbook or some boxed cake mix nearby. And though you can use the internet or your favorite cooking app, it can be nice to just cook without a recipe. That seems impossible with baking, which is such an exact science ...more
When I was in college, I invited a girl over for a date. It was a glorious spring day, and I thought it would be the perfect time to fire up the unused barbecue that had been sitting on my patio all school year. I prepped all the food, chilled all the beer, and then I realized ...more
With our internet-connected devices growing in number by the year, it would be nice if they could somehow all be interconnected. This is becoming commonplace for our tablets, smartphones, and laptops, but our media streaming boxes still seem to be isolated in their own little ...more
Ever feel like you're receiving notifications way too late on your Android device? Many Android apps use Google's Cloud Messaging service to send and receive notifications, including Hangouts, Gmail, Pushbullet, Facebook, and even WhatsApp to an extent. To ensure that your ph ...more
Resources for finding new music are at our disposal in all corners of the internet; the only problem is deciding which one is the best for you. Spotify, Pandora, and Rdio all have options to discover new music on your smartphone, but they tend to expose mostly established arti ...more
Netflix was my proverbial gateway drug to cord-cutting, as I'm sure it was for many others. Yet as much as I truly love Netflix and its service, there are some annoyances I have with the interface of the desktop web version. Yes, finding movies and TV shows is easy, but my ma ...more
When going out to eat with friends, it's inevitable that one person takes charge at the end of the meal to split the bill. They whip out a pen and begin asking everyone what they ordered, carefully dividing, adding, and subtracting on the back of the receipt for everyone to us ...more
Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities. One of the cardinal rules of hacking is: "If I ca ...more
In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new us ...more
This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging ...more
Anytime you surf the web on your iPad or iPhone, Safari saves which webpages you visit, the information you enter into them, and other types of data. This not only make your internet experience quicker, but it'll also keep track of everything you're doing. Safari does have an ...more
The Play Store is loaded with just about any app you can imagine. While many are free or have a "lite" version of a paid app for download, often enough, these freebies have intrusive ads cluttering up your screen. The internet is already riddled with ads on every webpage, so ...more
International, T-Mobile, and Verizon customers all share something in common—their carriers provide unlocked Wi-Fi tethering for free. Of course, you still pay for the data used, but they don't charge you extra simply for using your Samsung Galaxy S4 as a wireless hotspot. Ho ...more
With the explosion of food blogs in the last couple of years, there are more recipes available at the tip of your fingers than ever before. Craving chocolate chip cookies or Sriracha-flavored anything? You're guaranteed to have several thousand versions to choose from. So that ...more
Craigslist is probably the greatest site ever created, and I'm just talking about it's classified section, both awesome and amazingly creepy. Seriously, spend 20 minutes scrolling through the personals and you'll never want to take your eyes off the screen. But I digress—Craig ...more
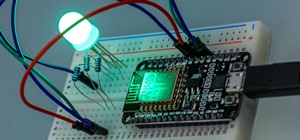
With just two microcontrollers soldered together, you can inject keystrokes into a computer from a smartphone. After building and programming the device, you plug it into a desktop or laptop, access it over a smartphone, and inject keystrokes as you would with a USB Rubber Duc ...more
2020 has been a rollercoaster of a year for all of us, the type of year that makes you feel like you're not sure if you're upside down or right side up. But as the holidays arrive, it's time to get your bearings back and find the good in the world — the type of good that we co ...more