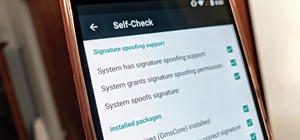
Since its inception in 2007, the Pwn2Own computer hacking contest has been challenging the vulnerability of mobile phones and web-related software. In 2010, the fruit of two full days of hacking came down to the exploitation of the following web browsers: Safari 4 on Mac OS X, ...more
In this video tutorial, viewers learn how to use the on-screen keyboard on a Mac OS X computer. To turn on the keyboard viewer, go to Apple and select System Preferences. Under Personal, click on Language & Text. Click on the Input Sources tab and check Keyboard & Character Vi ...more
This video is a quick guide on how to turn your computer screen up side down. If you have Windows Vista, right click on mouse and go to graphics properties. Go to display settings. On the rotation box, choose the desired angle of rotation. Click apply and hit OK to confirm set ...more
In this tutorial, find out how to easily connect a PS 3 controller to your PC. You can controll the mouse, keyboard with just this one controller. It's easy to do and makes it a whole lot better for your hands and for your sanity. The controller can even be configured to play ...more
VNC stands for Virtual Network Computing. It is remote control software which allows you to view and fully interact with one computer desktop (the "VNC server") using a simple program (the "VNC viewer") on another computer desktop anywhere on the Internet. The two computers do ...more
In this video, Gary from MacMost demonstrates how to select items on a Mac computer. He explains that there are different ways of selecting items, both with the mouse and with the keyboard. Click to select a single item, and click an empty space to clear the selection. Hold Co ...more
Lots of people are going to be getting the latest iOS devices this holiday season. But what good is a portable device if you don't hack it? Jailbreaking on the latest stock iOS, version 4.3.5, is a bit of a trivial endeavor. Not many people know how to downgrade from this firm ...more
Accidentally leave your Gmail open on a public computer terminal? Don't fret. You can have Gmail sign out any unwanted sessions with a click of the mouse. This free video tutorial from the folks at CNET TV will show exactly what to do. Protect your Gmail email account and log ...more
In this video tutorial, viewers learn how to hack the prestige mode in the game Call of Duty: Modern Warfare 2. Prestige Mode is an option that a player can choose after they progress to Level 55 (Commander) and gain a little more experience. With this hack, viewers will be ab ...more
There are a lot of things on your computer that can reveal information about you when you are surfing the Internet. If you are like me, then you will do anything to maintain your privacy and prevent those little leaks of information from happening. Here's a list of a few of th ...more
In this video, we learn how to hack your iPhone 3G. To do this, you will need: iPhone 3G, Firmware 3.0 or 3.1 file, charger cable, and the Redsn0w program. First, connect your phone to the computer and then start up the Redsn0w program on your computer. Turn the phone off, the ...more
Why type everything twice? If you don't know how to copy and paste you are missing out on an incredible time saver. Check out this tutorial and learn how to speed up your work. You Will Need • Computer • Word processing program Step 1: Position cursor Position your cursor n ...more
The tutorial focuses on using Cheat Engine 5.5 to cheat (or hack) Epic Battle Fantasy 2, an online RPG game. The user will need to choose the "Epic Mode" under difficulty setting. The tutorial maker's mouse also shows where the user is clicking for the menu to come up. This tu ...more
If you have an iPad, you can hack a Kinect and connect them together so you can redefine the Kinect's planes of interest. You can even used the accelerometer in the iPad to transfer data to your Kinect and display the results on a computer screen.
Here's a way to hack Ninja Saga to increase all your skills to be precisely where you want them to be! You'll need to be running the game in Firefox, and have the latest version of Cheat Engine downloaded on your computer.
Sparky is a wireless, web-based video-chat robot from the Gomi Style crew. You can learn how to make your own Autonomous Telepresence robot using spare computer parts, some old toys and a bit of custom software (that we provide at gomistyle.com). This robot is operated with a ...more
A 2.0 baseball bat that contains an accelerometer, a gyroscope and a wireless transmitter synched up to a computer was created to track a baseball batter's swing and test how fast Ryan Howard's swing is. Watch this video tutorial to learn how this baseball bat was assembled.
Connecting your new smartphone gadget to your desktop isn't just connecting these products with a USB cord. It is important to sync them to allow the transfer of data from your smartphone to your computer and vice-versa. This is desired if you wish to transfer information incl ...more
This video teaches how to change Windows 7 accessibility options. Choose Start, Control panel. This opens the Control Panel window. Choose Ease of Access in the control panel window. This opens Ease of Access window. Inside the Ease of Access window, there are various links th ...more
Record desktops with RecordItNow! on Ubuntu Linux Ever wanted to record your desktop screen? Well, it's entirely possible on Ubuntu Linux. This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to r ...more
If you can't get access to a wifi hotspot or an Internet connection with your PSP, you can use this method to get online. You will need access to a computer that is online, and a USB cord that can connect the computer to your PSP. Then, open up the command prompt on your compu ...more
Hard drive space is one of the cheapest things you can add to your computer. But people take it for granted, thus game developers have given up any efforts in keeping games compact. With all of its expansion packs, World of Warcraft takes up more than 60 GB of hard drive space ...more
In this tutorial, we learn how to use the notepad to get by school internet blocks. First, open up Notepad on your computer, then type in "<html>" "<body>", "iframe src=http://www.youtube.com", then "height=100%", then "width =100%". To finishe, type in "<iframe>>/body><html>" ...more
You can draw almost anything in Photoshop. Check out this video for information on how to draw an envelope that you can use as an icon for other programs. This step by step tutorial takes you through the entire process of creating a realistic looking envelope on your computer. ...more
This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to rea ...more
Don't be too disappointed if you don't have the spiffy new Kindle Touch, there is an up side. The benefit to owning the older (duller) models is that the firmware remains the same throughought generations, so the hacks retain their usefulness. This has given the modding commun ...more
Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service ...more
Haven't you ever wanted to live in a futuristic home? I think that homes are headed towards an era where they will be controlled by our computers and smartphones. No longer will you have to find your keys to unlock your door, or wait until you get home to monitor your security ...more
I don't know what I'd do without my computer. I can't do my job without the internet. I communicate with employers, friends, and family through emails, video chat and Twitter. I schedule meetings and plan deadlines. I bank. I shop. I read the news. I play games. I watch my fav ...more
Take a look around the next time you open up the File menu and slowly scroll through your editing options. Are your coworkers quietly cringing? Your kids running for the other room? Sounds like you need a few good keyboard shortcuts up your sleeve. Memorizing the right combos ...more
Tired of touch-tone hell? Get human with our cool phone hacks and cheats with the tips from this how-to video. Become a life hacker - we'll show you how to find phone numbers, cheat the computer and hack the call center system with our hacking tools. Watch this video tutorial ...more
Tutorial showing the basic netbios commands in Windows to access or hack a remote, unprotected computer. Use basic netbios commands. Click through to watch this video on tricklife.com
Learn how to draw a Mickey mouse on your computer using MS Paint in simple steps. Use the oval tool and draw two medium size circles leaving some space between the other. Now draw a bigger circle by making its top ends meeting the other two circles. Draw two little circle insi ...more
This is a super easy hack that you can use to get as much money as you want when you're playing the hit indie game Plants vs Zombies. All you'll need for this hack to work is to make sure your computer has both the game and Cheat Engine installed.
Not sure what to do with that old 2G iPhone now that there have been three newer versions since then? Don't toss it or let it collect dust! Jump on the Droid bandwagon and turn your old Apple device into an Android just like the EVO. This hack will require a little fancy compu ...more
See how you can make your mouse cursor leave a trail behind it. First, go to "Start" and then "Control Panel". Then go to "Printers" and "Other Hardware" and then "Mouse". A new window should pop up and you should go click on the "Pointer Options" and then select the length of ...more
This tutorial will work for any version of Cheat Engine that you have currently running on your computer. You can use the program to hack Plants vs Zombies to give yourself unlimited sun, unlimited money, no recharge time and a speed hack as well.
Farm Town hacks, cheats, glitches. How to hack Farm Town. Watch this video tutorial to learn how to plant a Farm Town field with Mouse Tractor (09/27/09). See how to use Mouse Tractor for a super fast way to plant a field on Farm Town. Description of the app on Facebook: In ...more
You can't get this hack without using Cheat Engine to get it. If you do have the most current version of Cheat Engine on your computer, use this method to not only give yourself unlimited sunshine, you can also get instant seed refills.
Download Cheat Engine You can get Cheat Engine here. After downloading, install it on your computer. Log Into Christmas Crunch Log into your Facebook account and go to MindJolt's Christmas Crunch game. Open Cheat Engine / Play Game Open the Cheat Engine and start the game ...more
With all of the advancements in the smartphone world, we can virtually use them for anything. You can use your smartphone as a mobile hotspot, an Xbox controller, a car locator, and a security camera. Heck, you can even turn it into a Swiss Army knife. And now you can even use ...more
Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can l ...more
Google Play continues to grow faster than the iOS App Store and may even hit the million app mark before Apple does. In the Android market, you'll find apps for everything, ranging from augmented reality multiplayer games like Ingress to wireless computer mouse apps like WiFi ...more
Kogoro Kurata, master ironsmith, known for his massive, impressive metalworking. His creations are awe-inspiring. Any blacksmith or engineer would agree. Kurata: "Being an artisan means you need skills first. However in my case, I want to make something first and then learn ...more
There's nothing worse than holding an ice cold brewski on a hot summer day and having no way to open it. If you're a Bud fan, you'll have no problem opening the bottle because most mass-market beers have twist-off caps. But if you have a taste for finer, more expensive brews, ...more
When it comes to getting your computer and smartphone to work well together, there's no service more robust and capable than AirDroid. For years, it's been the go-to tool for users looking to transfer files between their devices or access contact lists and call logs from their ...more
Since picking up your first crayon, chances are you've had a favorite, or dominant, hand. That hand gets you through the day, taking care of everything from writing to eating. If you've ever been forced to rely on your "wrong hand", you know how uncomfortable and unwieldy it f ...more
Like the buttons on your computer's mouse and keyboard, the Home key on your Samsung Galaxy S4 serves a vital function in navigating through your device. It can get pressed dozens of times a day, going through hours of use and abuse. If the GS4's Home button is anything like ...more
I'm still amazed by all the things some people just don't know. Script-kiddies often refer to Metasploit if someone asks them how to hack a computer because they think there's simply no other way. Well here I am today trying to increase your set of tools and -of course- skills ...more
Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us. In this episode, Elliot is being blackmailed by the ru ...more
Welcome back, my greenhorn hackers! Congratulations on your successful hack that saved the world from nuclear annihilation from our little, bellicose, Twinkie-eating dictator. The rest of world may not know what you did, but I do. Good job! Now that we hacked into the malevol ...more
On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated ...more
In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' compu ...more
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started. OVERVIEW: As you'll get further into the hacking community, and learn more about how it's all put together, you'll also realize very quick ...more
Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc. Maybe you forgot or lost the password to your Windows Admin account, this guide wi ...more
Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc. Any time someone's computer seems to act ...more
Every step in the evolution of computing brings an in-kind leap forward in user input technology. The personal computer had the mouse, touchscreens made smartphones mainstream consumer devices, and AR headsets like the HoloLens and the Magic Leap One have leveraged gesture rec ...more
It feels like just yesterday Apple unveiled iOS 13 to the world, introducing game-changing features like system-wide dark mode and enhanced editing tools in Photos. But WWDC 2020 is rapidly approaching, which means iOS 14 is as well. As it turns out, we don't need to wait for ...more
Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you ...more
Want proof that user experiences matter? Look no further than the HTC Vive and Omnipudding's particle generator, GPU Cubes VR, which lets you interact with thousands of colorful, cubic particles in a black void. If this was a simulator for your computer only, controlled with a ...more