It's nice having a dark theme on Android 10 and One UI 2, but setting it on a schedule takes it a step further. Imagine the light theme turning on every morning, and the dark theme taking over after sunset — all automatically. It sounds pretty simple, but it's one of those thi ...more
Recovery mode and download mode are useful for modding and they can come in handy in a pinch. Booting into recovery mode to do a factory reset or wipe cache fan save your Galaxy S20 from a soft brick, and entering download mode lets you install firmware with utilities like Odi ...more
Thanks to backups, Signal conversations can span over multiple years and multiple phones. These archives can get rather large as you share photos, videos, and other files with friends. But between the other apps and large files on your phone, you might not be able to afford to ...more
Back in the earlier days of Android, you were able to connect your phone to a computer, and it would mount automatically. This meant once the USB connection was made, your internal storage would pop up on the computer and you could go about your business. But recent versions o ...more
In iOS 13, Apple finally took the built in Files app from an extremely rudimentary file browser to a full featured app that can serve the needs of most any user. Among the new features is the ability to compress a file or series of files into a standard ZIP archive right from ...more
There have been hundreds of reports of Google Calendar users receiving notifications for events they didn't create. These "events" are actually spam ads and potential phishing threats. If this has happened to you, you're not alone — but luckily, there's a way to put an end to ...more
While browsing the web on a computer, most of us are familiar with using Ctrl + F (or Command + F) to search for a specific word on a page — but what if you want to do that on mobile? If you're using Google Chrome, there's a simple way to search for specific words on iPhone or ...more
Pandora has a simple rating system that works by hitting either the thumbs-up or thumbs-down icon on a track that's playing on your station. If you choose the former, the song you like along with others similar to it will play with more frequency, while selecting the latter wi ...more
Ingress, the godfather of location based-AR games developed by Pokémon GO creator Niantic Labs, is getting a new lease on life via Ingress Prime, a reboot of the game built on the Niantic Real World Platform. After teasing the reboot late last year, Niantic launched the new g ...more
The iPhone XR has touched down alongside the XS and XS Max, and it utilizes tried and tested materials found on the iPhone 8, while being molded in the same vein as the iPhone X. The budget-friendlier flagship comes with its own set of design elements to set it apart from its ...more
Apple's successor to the iPhone X is a beautifully made smartphone with much of the same characteristics, including a 5.8-inch OLED screen, two storage choices, and Face ID. But many features set the iPhone XS apart from its predecessor, as well as the other 2018 lineup of iPh ...more
Think back to when you last wanted to transfer some music or videos to your friend's smartphone and how difficult and slow it was. As powerful as our phones are, the default file sharing options are limited. There are, fortunately, some better options which make moving files e ...more
Whether you're in high school or college, you no doubt will have your iPhone in your pocket all day long. To make your iPhone last the whole time and even help you out with your studies, these are the accessories you'll want to get your hands on. You might not think you need ...more
In the tech world, upgrades are normally a good thing. On iOS, it means bug fixes and security patches that protect your iPhone and keep it up with the times. In the jailbreak world, however, upgrades can mean certain death, as we are reminded today when Apple stopped signing ...more
While certainly faster than writing by hand, manually typing passages from a book or document can be slow and frustrating. But thanks to Google Assistant, this is no longer the case. Whether you need to quote text for an essay or need to win an online argument, all you need to ...more
The fourth beta for iOS 11.3 was released by Apple to developers and public beta testers on Monday, March 5. The update comes just under two weeks after the company released beta 3 on Feb. 20, which mostly added bug and stability patches. It appears that beta 4 is much of the ...more
When first released, Snap Map made a lot of users uneasy. Beaming their location to the world at all times isn't necessarily the definition of privacy, but Snapchat's map is nonetheless intriguing, offering users a view into the lives of people across the globe. Now, you don't ...more
Whether you're watching Netflix on your Android tablet, smart TV, or computer, the process for changing how subtitles and closed captioning appear is the same. Plus, when you customize the font, size, color, and the background, all devices connected to your Netflix profile wil ...more
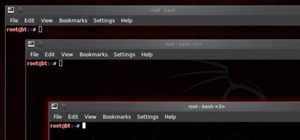
A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack ...more
So, your grandmother finally wants to ditch her flip phone for a shiny new smartphone? Congratulations. But helping her get used to her new device, even when it's an iPhone, is no small task. Grandma mastered checking her email in late-2012 and just recently learned there's a ...more
Cruise Automation, General Motors' (GM) driverless car arm, has hired two hackers who were once seen by many as a safety threat to help find vulnerabilities in its self-drive car network. Cruise CEO Kyle Vogt confirmed the hires of security consultants Charlie Miller and Chri ...more
By default, when you receive a FaceTime video call on your iPhone, the speakerphone kicks in immediately after answering unless you're wearing headphones. It's the exact opposite when it comes to FaceTime audio calls, but it's pretty easy to remedy if you'd rather have the spe ...more
China's Baidu, the Chinese equivalent of Google, live streamed a video yesterday of CEO Robin Li riding a self-drive vehicle along the streets and highways of Beijing. Since it's illegal to even test driverless cars on public roads and streets in China, the stunt culminated i ...more
Volvo Cars' claims it will offer Level 4 models by 2021 means the premium carmaker will likely have to finalize the driverless design to meet the aggressive timeline by next year at the latest. But in consideration of the Swedish carmaker's aggressive goals, the extent to whi ...more
Amidst reports of the newspaper industry struggling to survive, it's becoming more and more clear that people are increasingly turning to their smartphones for the news. In fact, a new study by the Pew Research Center has found that 85% of US adults check the news on mobile de ...more
A fairly hidden feature in iOS 10 let you turn websites and documents into PDFs, but thanks to the new Markup function in iOS 11, this process has become a lot more streamlined. Not only can you save webpages, notes, and other files as PDFs for easy sharing, but iOS 11 even l ...more
Though its necessity is less frequent compared to Android devices, iPhones still need to be shut down from time to time. Whether it's to help correct a buggy app, prevent overheating on a hot day, or conserve battery life in a pinch, the power button on any device is an indisp ...more
If you ever get asked to update your WhatsApp to your favorite color, don't. It's probably spam. According to Reddit user Yuexist, a new WhatsApp adware is going around disguised as an update. The spammer used non-ASCII characters rather than ASCII to look identical to its " ...more
The Google Chrome browser does mostly everything well and integrates nicely with other Google services, but it's not exactly renowned for speed. With a rooted device and the aid of an app called Kernel Adiutor, however, you can make Chrome as nimble as some of the fastest brow ...more
Despite a round of updates to Pokémon GO that patched and eliminated location spoofing, the game still has a difficult time dealing with the most hardcore cheaters. Like weeds on a grassy lawn, third-party bot makers still remain the biggest thorn in Niantic's side and continu ...more
The popular RPG Death Road to Canada has finally arrived for the iPhone and iPad, and its impact is immediate. It's fast becoming a top contender for mobile video game of 2017, and it's very easy to see why. The game blends decision making and good old zombie bashing to create ...more
Dreaded are the days when you're working on a masterpiece, then all of a sudden, your Windows computer crashes, loses power, or an app just gets up and quits. Well, now there's an app for that. According to MakeUseOf, with an app called AutoSaver, you can automatically save t ...more
Augmented reality seems to be the talk of the town lately, with everything from glasses to furniture stores prepping to implement exciting, new AR technology. Well now, it looks like even our food is getting a makeover for the augmented reality future. Dr. Katsunori Okajima, ...more
YouTube is so famous it needs no introduction, but its mischievous clone, YouTube++, sure does. The latter's been tweaked to include hacks not found in the regular version, including background playback, ad blocking, and the ability to download videos directly onto your iPhone ...more
Thanks to live-streaming video and social media apps like Facebook, Instagram, and Snapchat, we're all on camera nowadays. Unfortunately, though, we don't have a script to work with when we're shooting selfie videos, so it's hard to come off as perfectly eloquent when you're j ...more
Skype is one of the most popular messaging and video chat services for a good reason—it's packed to the brim with tons of cool features. But one bit of functionality that Microsoft left out is the ability to block friend requests from people that aren't in your contacts, which ...more
All across the country, retailers like Best Buy, Target, and Walmart are gearing up for their Black Friday sales. Brick and mortar stores are already packed to the brim with inventory in anticipation of the craziness that will strike as soon as the doors open the day after Tha ...more
Apple released Portrait mode for the iPhone 7 Plus in the iOS 10.1 update, which creates a simulated bokeh effect that blurs out the background and makes the subject pop out in the scene. It's still technically a beta feature since Apple does have some kinks to iron out, but i ...more
Several Samsung phones have a feature that turns the screen black and white when the battery is getting low. This takes advantage of the AMOLED display in these devices, because unlike red, green, and blue pixels, no battery power is used to display black pixels on this type o ...more
iPhone and iPad users are getting a huge update with iOS 10, and one of the biggest (and most sought after) redesigns is to the Music app, as shown at Apple's WWDC '16. The redesign essentially makes the user interface easier to navigate, which was something that was fairly cl ...more
Verizon customers who use the Samsung Galaxy S7, beware: a recent update installs new bloatware over your existing bloatware that installs new bloatware. Confused or pissed off? You should be, as this app can install new apps onto your phone without you knowing. Verizon Galax ...more
Researchers at MIT's Computer Science and Artificial Intelligence Laboratory have created Wi-Fi technology that identifies where you are, which may eliminate the need for passwords. Video: . The system, called Chronos, can determine where a user is with an accuracy of "tens of ...more
Hi, I am Robel, I am here to let you know about how to hack windows admin password with out Sam files, this requires physical access and any boot operating system...I used Kali 1.8 , if it doesn't work make sure you have shuted it down properlyor use backtrack. I have tested ...more
If you already have speakers that you love, you don't need to ditch them for an expensive wireless set for convenience's sake. With products like Chromecast Audio, you can turn any set of wired headphones or speakers into wireless versions for much less, and stream music or au ...more
For the past three or four months, Microsoft has been pushing advertisements onto the lock screens of some Windows 10 users as part of its "Windows Spotlight" feature. This feature normally shows you scenic photographs and gives you the option to learn more about them by launc ...more
Using a fingerprint scanner to keep intruders out of your phone might not be as secure as you think. Two researchers from Michigan State University, Kai Cao and Anil K. Jain, developed a relatively cheap and effective way to beat fingerprint readers, and successfully tested th ...more
The Google Cast feature that serves as the primary interface for the Chromecast and comes bundled with Android TV devices like the Nexus Player is a marvel of modern technology. But as these things go, troubleshooting issues can be difficult with something so groundbreaking, e ...more
Five Phases of Hacking:- The five phases of Hacking are as follow: Reconnaissance Scanning Gaining Access Maintaining Access Covering Tracks The Five Phases of Hacking Reconnaissance:- This is the primary phase where the Hacker tries to collect as much information as possib ...more
Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic An exploit is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability in order to cause unintended or unanticipated behavior to occur ...more
Windows 10 universal apps are actually pretty awesome—regardless of if you're using a desktop, laptop, tablet, or convertible, the same app automatically scales up or down to suit your device. Definitely cool, but the Windows Store is pretty bare-bones as it stands, so the dow ...more
This is a little c++ program that I thought would be handy in the future. Although, I apologize in advance for any errors in the code since I haven't had the chance to compile it yet. Anyway, please if you are a script kiddie please do me a favor and at least read this article ...more
I found this article a while back and I found it underneath a bunch of junk. Anyway, it's a article on 9 notorious hacker including Walter O'Brien (You know the T.V. show Scorpion? Well that's him). Not to mention the weird names: 'Susan Headley fell in with a gang and helped ...more
The Fire TV Stick, as well as the Fire TV, may be limited by Amazon's fight on piracy, but after a quick sideloading of Kodi, the floodgates are back open with the freedom to stream just about any video or song you want. This is a great new feature to have, but with the locke ...more
How to do an NMAP scan on Armitage to find IPs within a certain range. Armitage is a gui interface of Metasploit, and advanced hacking/exploiting program. It can be downloaded from http://metasploit.com/ and http://fastandeasyhacking.com/ and you will need NMAP. http://www.nm ...more
Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids to ...more
After a few months, I get so fed up with hearing the same ringtone go off alongside each new notification that I'm forced to switch things up—only to end up repeating this whole process when the new one gets played out. And I'm sure people around me are equally sick of listeni ...more
While it seemed like jailbreaking methods were always one update behind the current build, the team over at Pangu have already released a jailbreak tool for iOS 9, and it works up to iOS 9.0.2. It is not available for iOS 9.1 through 9.2 yet, but we will update this guide when ...more
If you want to watch a movie on Netflix with a friend, family member, or significant other, but can't meet up in the same living room, the next best thing is doing it remotely from the comfort of your own homes. Xbox LIVE used to have a feature called Party mode that made it ...more
Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity! Social Eng ...more
Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial. THC Hydra is very prominent online brute-force tool and ...more