Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educate ...more
It's gigantic! It can handle over 100 simultaneous touch points! It has a curvature of 135 degrees! And best of all, it is not the newest, insanely expensive gadget to hit the market. Instead, this touchscreen was hacked together with a bunch of PCs, video cameras, projectors ...more
Movies like to show hackers breaking passwords with fancy software and ludicrous gadgets. The reality of busting passwords open is much more mundane. Simple as it may sound, most passwords are broken purely by guesswork. Check out this infographic from ZoneAlarm, as well as th ...more
Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information y ...more
Many times throughout history companies have been hacked by so-called "grey-hatters": hackers who do ambiguously ethical things with their computer skills. Often enough, after being hacked the companies actually offer to hire the hacker, but not always (as you see in this case ...more
The days of entering left, right, left, right, up, down, up, down, a, b to cheat your way through a video game are long gone. With achievements and trophies in existence, game developers have, for the most part, removed cheats from video games. But cheats aren't entirely gone ...more
I am looking to learn how to hack. I have basic knowledge to computers so any help will be appreciated. Thx
i am stone taker and currently pursing b.sc computer science. i am from Africa.i want to to master become know programming very well especially c++; i hope you can help me with hacking too, for educational purpose only.
This tutorial shows you how to get started hacking your Xbox Kinect. You will need a high quality USB analyzer between the Kinect and the Xbox for this to work, and then you can start streaming data from your Kinect onto your computer.
The XBox 360 Connectivity Kit is a great tool for connecting your XBox 360 hard drive to your computer, allowing you to manipulate your saves easily. This handy video for beginners will show you how to hook up the CK3 to you XBox drive. Once that's done, you'll be well on your ...more
In this clip, learn how to use PDA Net to tether your rooted Droid 3G smartphone to a WiFi network. By tethering your device, you will be able to use it as a portable, wireless modem for anything from other phones to computers to hand held gaming systems. Anything that is WiFi ...more
Being able to pick a lock is considered to be a rite of passage for boys, especially those with aspirations of becoming a professional pirate/ninja, also known as a computer engineer. Pick your way to manhood with this tutorial on hacking a lock. Learning the method will only ...more
Computers are vulnerable to all kinds of viruses, hacks and other attacks that can do serious damage and cost you money. Make sure your version of Windows is the real deal and protect it from counterfeiters by making it genuine. This video will show you how to make Windows XP ...more
This is a really simple video guide on how to install Hackintosh OSx86 (Mac OS X) on a PC. OSx86 is a portmanteau of OS X and x86, a so-called collaborative hacking project to run Mac OS X computer operating system on a non-Apple brand personal computer, with x86 architecture ...more
This is a nifty tutorial guide on how to tether your hacked iPhone or iPhone 3G to a windows computer for use as a high speed modem. Just Jailbreak your iPhone using one of the many tutorials on WonderHowTo, and install 3proxy. This video explains the rest of the configuration ...more
Computer viruses are terrifying. They are undetectable, dangerous, and operate constantly right under your nose. For the average computer user, there are only a few repair options. You could buy expensive antivirus software that causes more problems than it fixes, you can wipe ...more
Last week's Community Byte we got off to a great start! We had a few people build our IRC bot, and all went well. We had some great contributers, ideas, and people willing to learn. So, needless to say, we will be having another. Let's try to get a few more people involved thi ...more
If you’re having trouble getting games on your memory stick, this video will walk you through the steps of just what you will need to do to compress files onto a thumb drive. There are a variety of steps you will have to follow and you’ll have to have a little bit of time to w ...more
There are so many hackers around these days, and they are becoming very smart. So smart that they have successfully taken down many government websites. The most recent attack was on the Department of Justice (DOJ). To read about the history of these hackers, check out Wikiped ...more
WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. Hacking, crafting, mining & more… just another ...more
Work it without breaking the bank—with a couple of household items and a little ingenuity, you can transform your old junk into effective gym equipment for both cardiovascular workouts and strength training within the comforts of your own home. The best part: if you go throug ...more
Screw gaming, let's get to the serious stuff! Here's an amazing video of a Kinect hack that lets one see what its camera sees - in 3D. Instead of 2D images of motion capture, we get the full spatial view. Think of the "bullet time" effect in The Matrix (freeze, rotate, conti ...more
Earn the secret "Eaten by a Grue" achievement in the single-player campaign mode of Call of Duty: Black Ops with this gamer's guide! In order to unlock this achievement, you will need to break free from your chair and play Zork on the nearby computer terminal. Call of Duty 7 ...more
This is a video tutorial in the Computers & Programming category where you are going to learn how to find and ping your IP address. Go to start > run and type in "cmd" to get the DOS window. Here type in "ipconfig" and hit enter. If you are online, your IP address will be disp ...more
Making the magic memory stick is one of the vital first steps involved in hacking a PSP. This video will walk you through the on-computer part of the process, creating the magic memory stick itself. The steps are very easy to follow, and should have you playing all of the home ...more
Bored and feel like customizing your Windows XP? Check out this tutorial and learn how to hack Windows and change the text on your "Start" menu button. With this video, you will learn how to change this icon, step by step. You can then turn the menu button into anything you'd ...more
In this Computers & Programming video tutorial you will learn how to change the default Windows Remote Desktop port. It is actually a registry hack. You can check the IP address of our machine by typing ipconfig into the cmd prompt. For hacking into a machine, you should have ...more
In this video tutorial, viewers learn how to hack the Flash game "Defend Your Honor" using Cheat Engine. Users will need Cheat Engine version 5.5. Begin by starting the first level of the game. Open Cheat Engine, click on the computer icon and select the internet icon. In the ...more
Hack N Mod offers an incredibly simple cell phone camera mod that delivers striking results. All you need is a lens from an old DVD player and you can magnify your zoom by five times. "You’ll find the lens directly under the disk tray. If you’ve just upgraded to Blu-Ray, now ...more
Do you own a hacked XBox 360? Do you want to burn some games for it? Well, in this video, the viewers will first be taught how to download games using peer-to-peer software, such as uTorrent. Then, with a combination of software, such as IMGBurn and abgx360, the viewers will l ...more
Computer forensics expert Steve Burgess gives a highly informative tutorial on how to recover deleted emails in Outlook and Eudora. The most critical factor affecting the recoverability of deleted web-based emails, according to Steve, is whether the PST file, which stores all ...more
Hacking into computer systems to steal passwords could be a bit complicated for the average everyday joe, but for all of your tech illiterate folks out there, there's any easy way to get that password, and all it takes is a camera. Check out this con video tutorial to learn h ...more
Notice: This is probably not new to many people. This *IS* new for some people however, and meant for them! Post interesting cameras you find. Website at http://householdhacker.com Today we'll show you how to look through various security cameras using search engines. For t ...more
For Infinity Exists Full Disclosure's first Website Hacking episode, we demonstrate how to exploit a security vulnerability occurring in a website's database to extract password hashes. Sql (Structured Query Language) is a computer language designed for the retrieval and manag ...more
Are you serious about becoming a bonafide hacker? Then you simply must learn how to hack SSL passwords using ARP poisoning. ARP poisoning, also known as ARP spoofing, involves attacking an ethernet wireless network by looking at the data frames on a LAN (local area network). R ...more
Kip "Kipkay" Kedersha is known for his intriguing and clever how-to and prank videos, even when he teams up with MAKE Magazine. He will show you how to tweak, hack, mod, and bend any technology to your hacking needs. No electronic device, gadget, or household item can stand th ...more
As advanced gaming systems continue to evolve, older classics like the Nintendo Entertainment System (NES) are one step closer to extinction. They're rotting in the basements of gamers. They're gathering dust at the local pawn shop. Or worse... being thrown out in the trash li ...more
Isn't it annoying when you want to check your Facebook or MySpace but you are at school and hit a big giant Websense blocker? Well, if you are stuck in a library or somewhere else where there are filters on your surf-ability, check out this tutorial for a useful hack. In this ...more
Social engineering is described as the clever manipulation of the natural tendency of human trust. All of the passwords, locks, and encryption in the entire world are useless against a good social engineer who can charm or trick you into giving it up. But what once started as ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. This week has been an exciting one. The com ...more
I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to rememb ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. Thanks to all of our active moderators and ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. Thanks to all of our active moderators and ...more
Have you ever been away from home or on holiday and noticed an open network connection? FREE INTERNET! But then you find out that every search or page redirects you to an "enter password" or "signup here" page. Well, there are ways around this. In this article, I'll show you ...more
In this article, I'll be showing you how to make a cool visual representation of sound using an old cathode ray tube (CRT) television, a stereo, and a sound source. You'll also need a pair of wire cutters, and a few screwdrivers. To properly understand this project, it's a goo ...more
Thanks to Yifan Lu, it's been discovered that the operating system running on the Kindle Touch is written mostly in HTML5 and JavaScript, unlike the previous models which used Java. This is exciting, because when a device is hacked or rooted, that means homebrew programs can b ...more
Hello and welcome to yet another InfoSecurity World tutorial. This post is based on the Windows 7 'GodMode' panel. Windows 7 comes with many hacks, cheats and tweaks. This bonus lesson will teach you how to create Windows 7 GodMode. GodMode works a lot like the Windows Contro ...more
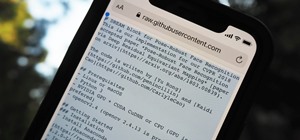
With a lot of Null Byters playing around with Linux because of its excessive use in the hacking world, some of you are bound to run into some trouble with the installation at some point or another. If you make a mistake, or you're intimidated by the wonky-looking installation ...more
SSH is what is referred to as the Secure SHell protocol. SSH allows you to do a plethora of great things over a network, all while being heavily encrypted. You can make a remote accessible shell on your home computer that gives you access to all your files at home, and you can ...more
Warning Don't torrent things that you do not have the rights to torrent. Everything I torrent, I have a physical copy of, and just want a copy on my computer without causing wear-and-tear on my DVD drive's laser. Piracy is naughty. I used to get extremely frustrated with Bit ...more
Hacking can't be that hard, can it? At least, that's what it seems like thanks to movies like Hackers, The Net and that last Die Hard flick. Even the Jurassic Park girl's got some game. They all look like they're typing 20wpm, yet can generate a screen full of code in the blin ...more
It's remarkable that a gaming device (from Microsoft, no less) designed for geeky gamers has incited broad innovation in medicine and robotics. But that Kinect has captured the imagination of hackers-with-MBAs-in-mind is downright amazing. Below, six videos demonstrating a va ...more
For travelers on-the-go, or penny pinchers who like to surf the web for free in public places, there are necessary precautions one must take when accessing sensitive information over a public WiFi connection. For advice on doing this safely, check out Glenn Fleishmann'sguide t ...more
Have an old-school tabula recta lying around? No? Then just print out the chart below. Nothing ensures better password security than this centuries-old cipher technique. Here's how it works, via Wikipedia: "Using a tabula recta, each alphabet is shifted one letter to the left ...more
When Sony released the new versions of the PSP Slim and 3000 in 2009, it thought that it had solved the PSP's rampant hacking problem. They hadn't. This video will show you how to load the popular exploit / CFW installer ChickHEN R2 onto a slim or 3000 PSP, leaving it ready an ...more
Cheating ruins everything. Cheating makes game play unfair for others who may be truly competitive and strategic. Cheating makes others disrespect and un-friend you. There can be unforeseen consequences, like getting viruses, trojans or your account hacked from downloading a c ...more
iPodTouchedMaster shows how one can easily SSH into their iPod Touch with all firmware! To SSH is the ability to hack into your iPod Touch's file system. First, your iPod Touch must be jailbroken. Next, you'll have to open Cydia. Click "Featured Packages" or search for the ter ...more
Nowadays many schools and colleges have blocked the social community sites from accessing them through school computers. The video shows how one can access to these sites using a command prompt. Follow these steps and access the blocked sites: 1. Go to the start menu and ope ...more
There are tons of hacks for Windows computers, so it was only about time that a hack for Bloons TD came out for a Mac. If you're using a Windows, you can still hack with Cheat Engine, but with Mac, you're going to want to use iHaxGamez. This video tutorial teaches how to hack ...more
Are your fish starving? If they are, you need to do something about it, and quick. Well, there's no quicker solution to feeding your fish than hacking Happy Aquarium with Cheat Engine. Watch this video tutorial to learn how to hack unlimited food in Happy Aquarium (10/29/09). ...more