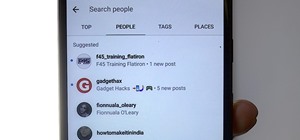
There are a few ways to do this, but I'm going to share with you the easiest way that I know how to share an image on Instagram Stories that isn't currently in your Stories queue. At the moment, Instagram only lets you post photos from the last 24 hours to your Stories. If yo ...more
WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the commu ...more
In an ongoing effort to improve its services and become more accessible to users from all regions, Facebook has released a streamlined version of its social media app. Though the leaner Facebook Lite is only officially available in Turkey for now, there's a simple workaround y ...more
If you're running iOS 10 or lower, there is no built-in way to make a screen recording on an iPad, iPhone, or iPod touch directly from the device, but that doesn't mean there isn't a way to record your screen at all. Occasionally, there will be an app in the iOS App Store tha ...more
In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your i ...more
Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private ...more
It's a given that if you're driving, you or someone you know has Waze as a go-to on their smartphone. The Google-owned crowdsourced navigation app is one of the best for avoiding traffic, roadblocks, and even cops. But a new academic study and report from Fusion suggest that ...more
You don't need an obsessive ex stalking you to benefit from the ability to record calls on your iPhone in a pinch. Besides protecting yourself from nefarious intent, recording important conversations like verbal contracts and agreements can help you cover all your bases and en ...more
As you all journey along with me on my challenge to become some sort of Instagram expert, let me share with you one hack that is currently helping me out a lot. If you've ever wanted to put a line break in your posts, then keep on reading. If you are in Android user, then you ...more
Real Racing 3 is by far one of the best racing simulators available on Google Play, and best of all—it's free! If you're playing this game on your Nexus 7, you've probably noticed that the graphics just don't look anywhere near as good as the in-game screenshots floating aroun ...more
There's not much you can do to customize the look and feel of your iPhone's home screen, at least when it comes to official options provided by Apple. But thanks to a new bug discovered by YouTuber iDeviceHelp, you can now hide text labels for app icons and folders on your iPh ...more
Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in secur ...more
If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs ...more
It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or ...more
It used to be easy to hack tethering—root your device and install a third-party or modded tethering app. But snuck in amongst the changes in Android 4.3, a new data-monitoring service of sorts made its debut. There used to be a time when your data connection was yours. You pai ...more
Bitmoji has experienced explosive success this year thanks to Snapchat. The app allows users to create their own personal emoji and send responses to other friends, and even though it's only two and a half years old, this customizable emoji app is growing at an impressive pace ...more
Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associa ...more
This week, at its developer's conference, Samsung took the wraps off a new tool from Wacom that bestows the S-Pen with AR powers, as well as its own entry to the AR cloud market called Project Whare. But while Samsung is just starting to float its AR cloud to developers, Nian ...more
You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay sec ...more
Thanks to a couple of photoshopped images that made rounds across Twitter last year, iPhone users were duped into thinking that iOS 8 included a security feature that would lock individual apps. Of course, none of it ended up being true, but we covered other features and apps ...more
If you're sick of seeing some of your contacts' faces in the sharing menu every time you share photos, apps, webpages, or other content on your iPhone, or if you want to keep nearby eyes from sneaking a peek at the people you frequently share things with, you can make some or ...more
When typing an email or website address in a compatible input field on an iPhone, most people will manually type in the domain extension. But there's a much faster way to enter domain suffixes for email addresses and website URLs that you should be using on your keyboard. Even ...more
Signal is one of the best end-to-end encrypted messengers on the market. It offers robust security, keeps minimal information about its users, and is free to use. Switching to it as your main messenger can be a bit daunting, so to help, we created a guide to walk you through t ...more
Privacy and security go hand in hand, especially for smartphones. When it comes to privacy, you decide what personal information about yourself is out there to discover. Security, on the other hand, is all about enforcing those privacy decisions. Sometimes privacy and securit ...more
Apple includes a lot of helpful features for iCloud email addresses, but one of its best-kept secrets will give you total control over organizing your inbox like a pro. So, what's the big secret? Subaddressing, also known as plus addressing, tagged addressing, email address ...more
Ingress, the godfather of location based-AR games developed by Pokémon GO creator Niantic Labs, is getting a new lease on life via Ingress Prime, a reboot of the game built on the Niantic Real World Platform. After teasing the reboot late last year, Niantic launched the new g ...more
The OnePlus 5T was just released, and it's packing several new useful features. While many OnePlus 5 buyers are feeling frustrated with the quick release cycle, lots of fans are still clamoring to buy the new device. Aside from the larger screen, most of the buzz around the 5T ...more
Hello My Fellow Hackerzz.. This is my first How-to and i'll be updating the “Hacking Android Using Kali” to msfvenom and some FAQ about known problems from comments. So Here we GO!! For Anything With a *, Please See The FAQ for More Info.. MSFVenom msfvenom -p android/meter ...more
There are a number of reasons you'd want to delete your Skype account. You may have decided to move away from the app in favor of another service like WhatsApp or FaceTime, or perhaps you want to erase your account due to an online hack. Regardless of why you might want to del ...more
I hate folder names, especially the one Apple shoves down our digital throats. On a computer, they make total sense, but on my iPhone, it's just more clutter on the home screen. You can tell what folder is what just by looking at the app icons within it, so why are we forced t ...more
Sense 6 came with a ton of new features for the HTC One, but for some reason, HTC decided to keep one of them hidden to all non-Harman Kardon editions. Music Channel is a music visualizer that can also link into the GraceNote music catalog and display lyrics for any compatibl ...more
Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works ...more
AT&T and Verizon customers, it's finally happened. After many long months of waiting, and a fairly significant bounty up for grabs, your Galaxy Note 3s can finally be rooted! Best of all, it may be the simplest method for achieving root we've ever encountered. Towelroot is th ...more
There's a little-known secret in the world of microwave ovens that even the manufacturers don't care to tell you in their manuals. And once you know it, you'll never go back to using your microwave as you used to. Some microwave owners have figured this "hack" out on their ow ...more
From Farmville to selling a company to Google, Amitt Mahajan has been through the startup ringer. Now, as managing partner with Presence Capital, he's funding the future of augmented and mixed reality. With interest in 3D graphics, Mahajan started his career working on game e ...more
Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about. Sometimes, if yo ...more
A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists righ ...more
You were the chosen one, Snapchat! The new download numbers for the social media app show just how hard it will be to bring them back to the light after the rise of the Instagram empire. Last month we reported that Snapchat's Download numbers had fallen 16%, bringing the num ...more
Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS. Related to the Pegasus hack that recently affected iPhones, Chrysaor is malware that baits the user into insta ...more
When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you ...more
People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people ar ...more
These days, everyone's snapping selfies, taking pics of their latest meals, or sharing pet trick videos on Instagram for the whole world to see. It's not only fun to shoot photos and videos for Instagram, it's inspiring to look at everyone else's creativeness in your feed. On ...more
Stories are everywhere in social media today, but that wasn't always the case. In 2013, Snapchat introduced the world to these temporary windows into our daily lives. Since then, stories have infiltrated other popular apps. However, to stand out, you can't solely rely on the a ...more
Great ideas often strike at random times, but messaging friends and loved ones at an inopportune hour not only risks their wrath, but also increases the chances of your message not being paid proper attention to. Thankfully, there's an app that lets you create and post WhatsAp ...more
As with any new releases, full updates that completely revamp the look and feel of your iPhone's operating system will have teething problems that eventually get ironed out with incremental updates. iOS 11, with its issue of not being able to connect to the App Store on some i ...more
Before many games make it to the US-based iOS App Store, they get "soft launched" in a smaller country to get real-world testing for bugs. It's a pilot program, so to speak, as countries like Vietnam or the Philippines have far fewer iPhone users than the US, thus offer a more ...more
Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history. Using a type of malware dubbed “KeyRaider,” hackers hav ...more
Netflix is more popular now than ever, but it still has a ways to go before satisfying everyone. Whether it's a lack of availability, buggy or unattractive apps, or just not being able to find anything to watch, lots of people have their complaints. But there is a way to make ...more
Don't look now, but stock photo mega-site Shutterstock may have the most extensive library of augmented reality content available. The company recently added the "View in Room" augmented reality tool to its iOS app, enabling users to preview approximately 250 million images o ...more
The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized ...more
Near Field Communication, or NFC for short, is a feature that allows our smartphones to wirelessly communicate with other devices over a short distance while using almost no power at all. Think of it like a slimmed-down version of Wi-Fi or Bluetooth that can send a small burst ...more
Despite numerous reports announcing its stateside arrival, "Final Fantasy Awakening" has yet to show up in the iOS App Store, much to the chagrin of millions of fans in the U.S. Unfortunately, the game seems to be stuck in soft-launch limbo, with no word as to when it'll land ...more
There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your comput ...more
With the introduction of Vine and the subsequent Instagram update, abbreviated video sharing has come to the masses, to be experimented with in an unprecedented way. While both video-sharing apps have their own set of restrictions (length, size), it's never suffocating and ac ...more
When you have minor software issues like an app crashing, restarting your iPhone would usually fix it. But Apple doesn't provide an official "Restart" or "Reboot" option (unless you count this bold text hack), so we typically have to power our devices off and on in these scena ...more
If you have a Barnes & Noble Nook, you may be surprised to find that your eReader can do a lot more than just display ebooks, which makes it a great alternative to those more expensive all-in-one tablets that do everything (seriously, everything). If you want to get more bang ...more
File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target. To demonstrate these vulnerabilities, we'll be practicing PHP file inclusion using the Damn Vulnerable Web App. We'll ...more
Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account ...more
I spent just about my entire weekend trying to break the 800, 900, and 1,000 levels of Instagram — because it's a game, y'all — by playing around with my follower count. I shamelessly manipulated my IG account in such a way that was extremely time consuming and left many of my ...more
Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers w ...more