Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack Mybrute for 6 fights on day of registration (08/16/09). Go to DT22. Visit mybrute.com to play the game. In the words of mybrute: Mybrute is a flash based arena ...more
Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack a bear and whip MyBrute (08/12/09). This hack works only on MYMcurse. After you create a character and fight with this brute, you'll receive the besdt weapon in ...more
Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack MyBrute for a bear and level cheat (07/16/09). You can get to level 3 on any new brute! Go to Ace Rima and follow the video's instructions. Visit mybrute.com t ...more
Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack MyBrute for EXP and higher levels (07/15/09). You can get to level 5 instantly! Go to Ace Rima and follow the video's instructions. Visit mybrute.com to play t ...more
Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack MyBrute for double EXP (08/03/09). Go to thevins1232 and follow the video's instructions. Visit mybrute.com to play the game. In the words of mybrute: Mybrute ...more
This video tutorial shows how to hack FarmVille (05/06/10). At this point, it seems like people are more interested in hacking FarmVille than they are in actually playing the thing. This video will teach you how to use Cheat Engine 5.6 to get unlimited tractor fuel, improving ...more
Want unlimited Tiki power on Island Paradise? Just use Cheat Engine to hack your way to more power. This is only for 1 use only. Watch this Island Paradise Facebook video to see how to hack unlimited Tiki power in Island Paradise (11/26/09). Use Cheat Engine 5.5. 1. Open Che ...more
Cheat your way up the ladder, higher and higher, with more levels than anyone on Fish World. Using Cheat Engine, this Facebook Fish World cheat will outperform your expectations on leveling up. In this Fish World video tutorial, see the steps on how to hack levels Fish World ...more
Cheat your way to success by using Cheat Engine on Fish World. Nobody makes it in life without a little cheating! Facebook Fish World cheat! In this Fish World video tutorial, see the steps on how to cheat Fish World: Coin and EXP hack (10/29/09). Download Cheat Engine 5.5 ma ...more
Get tons of free money, unlimited items and instant levels with this hack for Fish World using Cheat Engine. CE will get you whatever you want in Fishworld. In this Fish World video tutorial, see the steps on how to use Cheat Engine to hack Fish World (10/29/09). Download Che ...more
Want some easy to follow instructions on how to hack Icy Tower? They're right here. Hacking Icy Tower 1.4 has never been easier. This wintery video tutorial teaches you how to cheat on Icy Tower (12/14/09). Download Cheat Engine 5.5 and just follow along with the video. There ...more
Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack your way to level 14 on MyBrute (08/18/09). Go to Emmanualson's brute. Enter a Username Click 'Validate' Enter a second verification code if prompted. Fight ...more
Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to get a pet dog, wolf or bear in MyBrute (06/02/09). So how do you get a pet dog, a pet wolf or a pet bear in MyBrute? 1. First, create a new MyBrute character but ma ...more
If you're on the hunt for a profitable side-gig, or even a completely new way to to make money, you'll want to take a look at Upwork, a leading freelancing platform that connects skilled freelancers with clients from all over the world. Upwork allows you to build your own onl ...more
Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and ...more
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
With the same starting price as its predecessor and a nice list of improvements, the OnePlus 6T is a great buy for a number of reasons. But for many Android users, the main selling point for the latest OnePlus flagship is how easy it will be to root and mod the device. We jus ...more
It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time. Both Facebook and Gmail ...more
A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge. The goal in this article is to acquire a target's .plist file which contains the ...more
Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that ru ...more
As we first reported here on Gadget Hacks, Google's new Pixel and Pixel XL smartphones come with an unlockable bootloader, with the exception of models sold by Verizon. This means that by sending a simple fastboot command, you can flash third-party firmware images like TWRP c ...more
Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands. RapidScan does an excellent job of automating the deployment of vulnerabili ...more
Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly d ...more
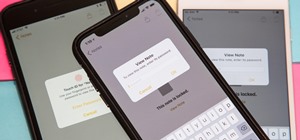
Apple's latest iPhone operating system is notorious for its frequent bugs and glitches. The latest iteration, iOS 11.3, is no exception, as users are experiencing not only 3D Touch issues but missing screenshot previews as well. Normally, when a screenshot is taken in iOS 11 ...more
Hi, I am Robel, I am here to let you know about how to hack windows admin password with out Sam files, this requires physical access and any boot operating system...I used Kali 1.8 , if it doesn't work make sure you have shuted it down properlyor use backtrack. I have tested ...more
Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just ...more
As the developer behind the most popular root methods for hundreds of Android devices, Chainfire knows the ins and outs of Android root procedures. But this doesn't mean he's infallible—occasionally, some of his root utilities can cause minor bugs. Many users have reported th ...more
Apple may have made Mavericks more accessible to Mac users everywhere at the fair price of zero dollars, but unfortunately, they made it trickier to create a bootable install drive of the Mac OS X 10.9 operating system. Don't Miss: How to Create a Bootable Install Drive of 10 ...more
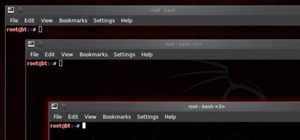
There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distributi ...more
Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and ...more
Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers w ...more
There's been a lot of fanfare as iOS 12 rolls out, and as an Android owner, you might be feeling left out. There's no need to feel that way, though. You don't have to choose between running out to get a new iPhone or being stuck with only your Android's features — at least whe ...more
Arguably the most impressive aspect of the iPhone 7 Plus is its dual-lens camera, or better yet, the Portrait mode that comes with it. This mode creates a dramatically shallow depth of field behind a subject, and was pretty impressive as is. Now, in iOS 11, Apple is making it ...more
TrueCaller is sharing your phone activity by revealing the last time your phone was used to contacts. The application used to identify unknown callers launched in 2009 and has faced a wealth of privacy concerns before. In addition to making your contacts public, TrueCaller no ...more
Anyone who's ever flashed factory images to manually update an Android phone knows how tedious the process can be. Unlocking the bootloader and flashing Android firmware requires the use of ADB and Fastboot—but, like getting a whole pizza pie when all you wanted was a slice, u ...more
Facebook released a new app in November 2016 that aimed to compete directly with Snapchat, but it was only officially available in Brazil—and still is. The app, called "Flash," is so much like Snapchat that it's not even the slightest bit of a stretch to call it a clone. Even ...more
Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or datab ...more
Believe it or not, not every Apple lover is willing to make the commitment and fork over $350+ for the Apple Watch. Like many others, I'm not willing to put that much faith into Apple's first attempt at wearable tech. Thankfully, if you or a buddy have a Moto 360 (which costs ...more
Creating a digital spreadsheet by hand can certainly be tedious, especially if you're copying a printed paper table word for word, number for number. Instead of typing information that's already there, however, use Microsoft Excel on Android or iOS to snap a photo of that prin ...more
Depending on your region, you may not be offered the same call recording option other OnePlus users have. But, as with most things Android, where there's a developer with a will, there's a way regardless. And the method we are about to describe is one of the easiest, most stab ...more
If you've ever rooted an Android device in the past or installed a custom recovery, you're surely familiar with the term "unlocked bootloader." But if all of this sounds like gibberish to you, some major changes in Android have made it to where you should definitely get famili ...more
Apple just sent out a new update to their iPhones, and while that normally wouldn't have any impact on Android users, the fact that they included 184 new emojis means that the text messages you receive from friends and family members with iOS devices might come across with bla ...more
Everyone's favorite Android modding tool is finally available for the Galaxy S6 and S6 Edge. Thanks to some hard work by Wanam and a few other developers, we can now install the Xposed Framework on Samsung's latest mid-sized flagship phones. But there are a few stipulations—m ...more
The Galaxy S6 already has one of the best cameras on the market, but a few minor annoyances still linger. Full-sized photos are stored with heavy compression that can cause artifacting, burst mode shots aren't taken at 100% quality, and the camera flash cannot be used when you ...more
There are several reasons that you might want to restore the factory firmware on your device—maybe you need to send your phone back for warranty purposes, or perhaps you're getting ready to accept an over-the-air update and need to unroot first. In some cases, reverting to the ...more
Your Apple Watch is a fantastic tool that can help you perform daily tasks on your iPhone. Notifications get filtered through it, you can respond to messages on it, and you can even use Apple Pay to purchase goods and services. Your Apple Watch is also a valuable asset when it ...more
Without a comprehensive root method for all Android phones and tablets, a device-specific approach is needed. And since we always cover new rooting methods for all the popular phones here at Gadget Hacks, we've built this always-updated guide to rooting many mainstream Android ...more
The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in r ...more
Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by d ...more
Welcome back, my greenhorn hackers! This tutorial will be the fourtenth in the Linux for hackers series and will focus on the MySQL database. Although this is not strictly a Linux tutorial, MySQL is the database of choice on most Linux distributions. In addition, it is the mo ...more
The OnePlus 5 doesn't have too many weak spots, at least not when you consider the price. But you might feel that the company with the slogan, "Never Settle," might have actually settled a bit with its camera. The OnePlus 5 and 5T don't have bad imaging specs, but they could u ...more
Ever-shrinking bezels and disappearing hardware buttons make for good looking phones, but they also increase the need for gesture controls. Android Pie comes with seven new swipe gestures, but if you don't have the update yet (or find its default gesture options to be lacking) ...more
With a 13 megapixel camera that can record in full 4K, there's a lot to love about the Samsung Galaxy Note 3 from a photographer's perspective. The image quality in my photos and videos are top-notch and nothing to complain about, but as with all things tech, things could alwa ...more
Until recently, brainwave-reading devices have pretty much only existed in science fiction. Sure, electroencephalography (EEG), the technology that powers these devices, has been used in medicine and psychiatry since the late 1800s, but diagnosing people's brains and reading t ...more
According to a study done by Kaspersky, 7.6% of Android users root their phones. That may not sound like a lot, but with over 2 billion Android devices out there, the math works out to over 150 million rooted phones — more than the total population of Russia, Mexico, or Japan ...more
When it comes to customizing Android, there's no better way to make it your own than by installing a custom ROM. You gain new features that were not accessible on the stock firmware that came with the phone, and you get complete control over how your system looks and feels. Bu ...more
Twitter's official iOS app is adequate if you're not much of a tweeter, but if you are, there's a lot of useful features that are missing. Luckily, there are plenty of free Twitter clients available that you can use on your iPhone. These third-party apps have features such as ...more
Imagine this: you have your finger poised to take the perfect picture — a once in a lifetime opportunity, like a solar eclipse — and you are suddenly caught off guard by a buzz, then "ding!" You look down at your phone to find your perfect pic ruined by distortion from the vib ...more
After you unlock the bootloader, install TWRP custom recovery, and flash Magisk to gain root access, what might be the next step of your modding adventure? A custom kernel, of course! Flashing a custom kernel onto your device gives you a whole new level of tweaks and customiza ...more
With the recent launch of the OnePlus 6T, the company continues to impress us with some of the best phones when it comes to the rooting and modding. OnePlus has made it easy enough to get up and running with the rooting process as fast as possible. The OnePlus devices follow t ...more