Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking. Luckily for those o ...more
Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing u ...more
In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodolo ...more
We're almost there to completing the setup of your Mac for hacking! Now that we have Git and Homebrew under our belts, it's time to take on something fairly easy, but very important for our hacking needs. Ruby is an object-oriented scripting language used to write powerful pr ...more
As an avid coffee drinker, I used to be a big fan of single-serve coffee machines. One day, the machine decided to stop working—which does happen from time to time—so I decided to go old school and use my automatic drip. Then, I realized that all I had were pods of single-serv ...more
Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on b ...more
In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the ...more
It's no secret that Google is all about AI. In their eyes, machine learning is the future of software development, and you can see evidence of this all over the last couple Android updates. They've used it to power all sorts of features in their Pixel phones, and they've even ...more
With the growing list of products Apple offers, the number of devices connected to your Apple ID can get quite extensive. Having all those devices connected to your Apple ID helps you keep track of them, but when it comes time to part ways with an Apple TV or Apple Watch, thos ...more
Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scann ...more
Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side sy ...more
Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, ...more
While seltzer water is commonly consumed as a beverage (and a healthier alternative to carbonated soda), it is less known as a fantastic addition to many familiar recipes. The bubbles in seltzer water expand when heated, and when added to certain foods, it instantly allows the ...more
Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensiv ...more
A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fort ...more
The battle between the Pixels and the iPhones has been heating up over the last few years, and this year's bout is the best one yet, with Google's Pixel 3 taking on Apple's iPhone XS. Why is 2018's lineup the best competition between the two flagships? Because Google and Appl ...more
Former Google employee Tristan Harris claims there's an easy way to combat phone addiction without installing any new software. By enabling grayscale on your phone, checking your apps and notifications will be less appealing and thus stop you from obsessively checking your pho ...more
The rumors have been confirmed by Samsung themselves: Samsung has developed a virtual assistant of their own, named Bixby. Bixby will makes its debut with the Galaxy S8 on March 29, with a "Bixby dedicated button" on the side of the new phone. Samsung senior vice president I ...more
In the first part of my containers series, we learned how to install Docker on our local machine, pull down "hello-world" and Ubuntu containers, SSH into containers, and install software when in a container. Now, we're going to work on building, customizing, and storing our re ...more
Since Ive started to learn about nmap and metasploit and other tools I was learning well but I had one problem, I had nothing to practice it on. As a result I asked someone about my problem and they told me about Vulnhub. It's a great way to practice. Its good beginners and pe ...more
I hate wasting money. To be fair: I doubt there are many people out there who relish the idea, but I especially hate it. And I also dislike spending in excess of what I need. This happens all too often, I feel, when it comes to recipes that involve using sausage. Don't Miss: ...more
INTRODUCTION Hello dear null_byters here we go again with our third part of this serie. in this third part of our series I'd like to do a demonstration or continuation on fuzzing, but I think I should leave for later because the next tutorials about fuzzing will require from ...more
This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the ser ...more
As you're probably well aware by now, the Apple Watch isn't just for sending text messages and checking Instagram—you can also use it as your wallet. With Apple Pay compatibility, you can use your Watch to make purchases at any retailer that accepts the payment service. Lucki ...more
Automated tattoos are now a reality, with 3D printers being hacked into tattoo machines. Multiple people have posted videos of their 3D printer that can "print" tattoos, with one of the more impressive ones shown in the two videos below. Video: . Video: . While many machines ...more
For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swi ...more
Kali Linux is known as being the de facto penetration-testing Linux distribution but can be a pain to use as an everyday OS — even more of a pain if that means carrying around a second laptop or the constant frustration of using the finicky Wi-Fi on virtual machines. But there ...more
At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher. Previously: How to Create a ...more
Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, a ...more
Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of ...more
Normally, office supplies and food don't mix, but you can use a paper shredder to make fresh pasta in your very own home (...or office). In other words, you don't have to buy a bulky and expensive piece of equipment to make fresh pasta. If you already have a paper shredder, yo ...more
Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to c ...more
In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as ...more
After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking t ...more
When alcohol tastes bad, there's little you can do to save it—or so you think. While it might seem easier to toss your entire bottle of old, opened wine, or to give up and drink crappy vodka anyway, there are creative ways to turn a spoiled or just plain bad boozy beverage int ...more
Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes ...more
Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on. In a previous post, I had provided you a cheat sheet of meterpreter commands. These commands are ess ...more
Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, ...more
First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell). We will be using Kali version 1 as the attacker machine and Windows 8 ...more
Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input ...more
Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills. Wh ...more
Replacing your iPhone fingerprint sensor has been one of Apple's most cruel tortures. It's a slow and painful process made worse last year when Error 53 messages started appearing on the phones of users who had tried to repair their sensors outside of Apple. The error rendered ...more
Running diagnostics on your Android phone can be a very tedious process. More often than not, you need to key in dialer codes to see if your device's hardware is functioning properly, though you can also download apps — but these are often hard to understand for a layperson. W ...more
Google, the company that rules the internet, is now testing a method to leverage its machine learning with its ubiquitous presence on mobile devices. The new model they're employing is called Federated Learning, and it hopes to apply artificial intelligence to Google's service ...more
Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help ...more
We're nearly done getting our Mac set up for hacking. If you haven't checked out previous tutorials, I'd recommend you do so first before diving right into this one. While macOS is a powerful POSIX-compliant operating system, some of our Linux tools do not work out of the box ...more
Halloween is this weekend, so if you're looking for a last-minute big batch cocktail that will keep your guests properly hydrated—and might turn them into mutants—look no further! (Note: This will not actually hydrate anyone, just so we're clear. Priorities, people!) Meet Zom ...more
In the past, creative chefs and bakers have been rewarded for their daring in the kitchen with viral attention from the internet—like the rainbow bagel or cronut. These sensations weren't crafted for the sake of going viral, but ended up generating an insane amount of buzz any ...more
If I were to write a snickerdoodle FAQ list, the top question would undoubtedly be "Do I really need to use cream of tartar in my snickerdoodle cookies?" Don't Miss: 5 Baking Substitutions Every Home Cook Should Know I dug deep into the baking science world to find out why ...more
Onion scrubs, salt and olive oil blends, a baking soda slurry... despite the many methods already out there to clean your (old or brand-new) cast iron cookware, there's one you may not have considered: using a potato. Don't Miss: The Ultimate Potato Cheat Sheet According to ...more
Many recipes call for self-rising flour as a staple ingredient. Oftentimes, we find ourselves passing these recipes by because we don't have it on hand, or because we don't use it enough to actually want to buy it. Don't Miss: Cook Like a Chef: Use Ratios, Not Recipes Lucki ...more
We already know that Samsung's Galaxy S7 is one of the most versatile smartphones ever made, complete with edge-to-edge displays, water resistance, and a huge battery. But what's versatility without durability? How much punishment can the Galaxy S7 take? Let's play a game of S ...more
Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam wi ...more
Apple Pay has been available to use in stores, as well as in select apps and websites, ever since its first appearance in iOS 8.1. Now, with iOS 12, there are currently 13 different iPhone models that support Apple Pay functionality without the use of an Apple Watch, and the l ...more
One of the more annoying parts about cooking or baking at home is dealing with sticky ingredients. You scrape the peanut butter out of the jar and into a measuring cup to make sure you have the right amount for your recipe, then scrape the correct amount into the bowl you're c ...more
Parties are a great way to celebrate and have fun with your good friends, so to make sure your next party rocks, I've assembled some of the biggest life-hackers on YouTube to bring you 10 outrageous party tricks your guests will not forget. Video: . All these YouTubers posted ...more
Most of us are used to just grabbing a bag and throwing it in the microwave when we want popcorn. It's easy, convenient, and requires little to no cleanup. But what about those times when you're away from home and don't have access to a microwave? You can buy a popcorn popper ...more
QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into ...more
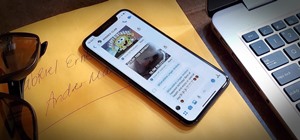
There are a lot of songs out there, so it's tough to remember all of the words to every song you like. If you're like me and have a less-than-perfect memory, visual aids will ensure your Apple Music jams aren't interrupted with incorrect or forgotten lyrics. That's why Apple's ...more
It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to ...more