Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills. Submit your best shot to our weekly competition for a chance to win an awes ...more
One of the biggest advantages iOS has over Android as a mobile platform is how readily and fully it has embraced mobile gaming. There are over 200,000 games available in the Apple store, compared to approximately 100,000 in the Android Marketplace. As an Android-using gamer, t ...more
What's cuter than a puppy? Not much, especially when you omit all the peeing, barking and furniture chewing, as Remedie Studio did with this sweet time-lapse homage to their beloved pup. Below, watch Dunder the German Shepherd grow from 8 weeks old to 1 year in 40 seconds. Ins ...more
At Google I/O this morning, Google finally announced the launch of its much awaited Google Music service. It's currently in invite-only beta mode, but they claim it will open up to the masses soon enough. To start syncing your music library with Google's Cloud now, you need ma ...more
Understandably, the tragedy in Japan has substantially risen the level of worldwide radiation-related hysteria. So much so, as an alternative to stampeding health food stores for iodine tablets, crafty individuals and organizations are hacking together personal radiation detec ...more
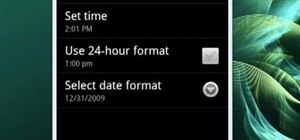
When the iPad 2 was released earlier this month, as to be expected there was a whole lotta buzz. And for good reason—while the the newest version shares the same price tag as the old, it boasts some significant new features. In case you missed it, here's a quick overview: Bet ...more
Your best friend's on Yahoo!, your daughter's on AIM, and now your co-worker wants to connect with you over Windows Live. Before you know it, your desktop is overflowing with buddy lists and message windows. Mismatched alert sounds are dinging and buzzing incessantly. Your com ...more
The Fake Adult Website Prank is an incredible trick if you happen to have the necessary access and work in the internet industry. Luckily, I had both. The objective of this prank is to fool your boss or co-workers into thinking you've accidentally sold out the site to a adult ...more
Want to get started playing FarmVille? Signing up is easy! And this gamer's guide will show you precisely how it's done. FarmVille is the hottest application on Facebook which lets members manage a virtual farm by planting, growing, and harvesting crops, trees, and livestock. ...more
Microsoft Ribbon hero is an application that turns the office into game. It is designed to boost skill and knowledge in Microsoft Office’s latest version. It is released with office 2007 as a social game for increases productivity in office applications. It is compatible with ...more
Flash video. It's what all smartphone users have been waiting for. Why has it taken sooo long? And why is Apple still resistant? Here's the scoop, via Wired: "Adobe is releasing Flash Player 10.1 for mobile phones and desktops today. And it is piggy-backing on Google’s fast ...more
Lifehacker posts an article on the art of cracking weak passwords, courtesy of Internet standards expert, CEO of web company iFusion Labs, and blogger John Pozadzides. Pozadzides certainly knows a thing or two about password logic. (Note: this information is not intended to ha ...more
Dating sites are getting more and more culture specific, and this week's brand new girl + guy site offers a very specific service. Cute girls are paid to play video games. Gamer dudes pay to play with them. GameCrush is already so popular, the server is currently down due to ...more
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a f ...more
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to edit Supe ...more
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a m ...more
I hate waiting to play, and I hate bugging my Facebook friends even more. But that's what Candy Crush Saga makes you do if you want to get new lives and levels faster. Luckily, you don't have follow King's rules—you can use a simple time hack to get new lives and play locked ...more
As many of you know Windows is not the most secure Operating System in the world, but then again no OS is really secure if the user doesn't know how to protect themselves. Later I will show you how to lower the risk even more on your (the user's) end. Well onto the real stuff ...more
Although +Google Chrome has been getting many deserved kudos for its innovations and speed, many people still prefer to use +Mozilla Firefox as their primary browser. If you’re a dedicated Google+ user, you know that there are many Google+ Chrome browser extensions available t ...more
Here's something fun for the Null Byte community to do—a coding competition! This week, I wanted to get everyone involved by offering you all a nice library of possible program types to choose from and try to code. At the end of this competition, all of the submitted programs ...more
I'm sure we've all heard about MSN and Yahoo! Messenger, right? They can be useful, but the setup can be quite time consuming for those who need to use it just once or twice—and the privacy statements are a real bother. For example, we must provide our real details. You could ...more
We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no ne ...more
As per Alex's request, I am posting about generating word-lists in Python. However, this is my FIRST attempt with Python, so please provide me with critiques and any and all comments. I really want to know what you think as there was a little bump here and there seeing as I a ...more
Welcome to the eighth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to asp ...more
Welcome to the seventh Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to as ...more
Welcome to the sixth Community Byte for coding in Python and beating the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and essentially grow together. Everyone is welcome, from novice programmer ...more
Welcome to the fifth Community Byte for coding in Python and beating the challenges given to us from HackThisSite. These sessions are created to bring our community together, to learn from each other, and essentially grow together. Everyone is welcome, from novice programmers ...more
Welcome to the closing of the second HackThisSite and programming Community Byte. First and foremost, I would like to ask that people start showing up on time to the Community Bytes. If you need help converting your time zone to PST, go to Time Zone Converter. When users do no ...more
Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their c ...more
Friday's Community Byte was weird. The intent was to do a HackThisSite mission, but upon time to begin, everyone in there was programming without my assistance, with the help of Sol Gates. This is great! It's really awesome that everyone enjoys programming that much and will m ...more
Our mission for this week's Community Byte was to create a Python program to crack web-based passwords, like the ones you would see on an email or router login. I wanted it to be universal in the sense that it could be easily modified and adapted to another website just by cha ...more
Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it. I'm sure at one time or another you've heard that hack ...more
Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills. Submit your best shot to our weekly competition for a chance to win an awes ...more
The lack of a search function within Google+ is driving me crazy. It takes me way too much time to find the posts I want to save and refer back to, and it's counter-productive for Google to launch their social networking product without an integrated search. Although Google h ...more
Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills. Submit your best shot to our weekly competition for a chance to win an awes ...more
As Google+ became available to more people, it started running into issues of accounts being suspended due to names that did not sound "real". According to Google+'s community standards, names that users "commonly go by" were encouraged, but not pseudonyms. Those who were usin ...more
Although circles are Google+'s answer to the problem of social network relationship management, that's not the only thing it's good for. People on Google+ are using circles for all sorts of creative activities, some of which aren't obvious as first glance. 1. Take Advantage o ...more
Making a video game requires an incredible amount of work. It requires people skilled in many disciplines to work together for thousands of hours merging visual art, computer programming, game design, sound design, and music composition into a fun game. The Indie Stone is a Sc ...more
There are over 425,000 apps in the iTunes App Store and the Android Market has over 300,000 available, which makes it really hard to tell which ones you want and which ones you don't. One of the best ways to find new mobile apps is from your family, friends and colleagues—thos ...more
Do you know how you are perceived by your peers? In real life and online? In the physical world, you could be seen as intelligent, thoughtful and hard-working, but on the Web you could be looked at as irrational, selfish and slothful. There's just something about the Internet ...more
At first, it seemed like a clever art installation housed on the web, but now we're not so sure... the Newstweek hack may indeed be legit. Earlier this year, Newstweek claimed to have developed a way to hack into webpages on a local Wi-Fi network using a homemade device that ...more
Do you ever wonder if the files you're trashing on your Mac are actually trash? Let's say there are 80 million computer owners running Mac OS. If each user trashes at least 10 files each day, that's 800 million deleted files that cease to exist every 24 hours. If that doesn't ...more
There are a few different types of Apple iPhone and iPad users: general household users who largely consume media—e.g. surfing the web, watching movies, listening to music. Other iPhone and iPad owners use their device(s) to produce stuff—written documents, edited movies, blog ...more
With so many wireless iOS networking apps for the iPhone, iPad, and iPod touch available, there’s very little reason to connect any of these devices to iTunes, except to update the software. Besides, importing and exporting photos using iTunes has never been one of the best fe ...more
Our hacked Kinect series has demonstrated amply how the Kinect is changing the worlds of business, art, medicine and robotics. But where does it go from here? That will be determined by the thousands of dedicated DIYers out there doing work like you've seen here over the last ...more
Are you one of countless Facebook users who find the classic Thumbs Up symbol tiresomely sycophantic? You're not alone. Back in August of 2010, the widespread addition of an "official" Thumbs Down symbol to Facebook pages quickly revealed itself to be a scam, but only after co ...more
Thanks Anonymous User For This Article, Not Bad Ok SoftzZz...!.!.!.: Step 1 Antivirus The best freeware antivirus is AVG Anti-Virus Free Edition 2011, and you can get him from this site. Step 2 Optimizing tool For me CCleaner is the easiest way to do some things, like: 1. ...more
Hello readers again! Sorry about the long wait (scary computer problems). Today I am going to talk to you about security problems on Wizard101. I have recently encountered many security flaws on Wizard101, including hacking, frauding and other crazy things. Wizard101 is the ta ...more
Good news. Facebook has finally listened. After severe criticism for ignoring the world's privacy norms, Facebook will finally release simplistic, user-friendly privacy settings soon. Wired reports: “'Now we’ve heard from our users that we have gotten a little bit complex,' ...more
Oh, LifeHacker, we love you. You've brought us so many handy HowTo's: Hack Wireless Internet, Bypass Blocked Websites, Convert a Laptop Into a Projector, Watch TV & Movies on the Web For Free, 10 Must-Know Google Privacy Settings, and more. And now, another great one: LifeHac ...more
Get a little perspective on FarmVille hysteria, via FarmVille World, written by tenebrism: Did you know it only took five weeks to make FarmVille? That it currently has over 80,000,000 users? That FarmVille farmers outnumber real farmers in the United States by a ration of ...more
Did you know it only took five weeks to make FarmVille? That it currently has over 80,000,000 users? That FarmVille farmers outnumber real farmers in the United States by a ration of 80 to 1? Crazy, right? And that's just the tip of the iceberg. There's plenty of other od ...more
Hey, hackers! Now that you've hacked/owned your first "box" in my last article, let's look a little closer at another great feature of Metasploit, the Meterpreter, and then let’s move on to hacking a Linux system and using the Meterpreter to control and own it. Why Meterprete ...more
Dreams are like an internal human holodeck. Inside your mind, anything is possible, from your grandest wishes to your worst nightmares. This is all well and good, but what if you could control your dreams and become the omniscient god of a handpicked reality whenever you go to ...more
This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing p ...more
There are so many hackers around these days, and they are becoming very smart. So smart that they have successfully taken down many government websites. The most recent attack was on the Department of Justice (DOJ). To read about the history of these hackers, check out Wikiped ...more
Hello and welcome to another InfoSecurity World tutorial. The intent of this article is to teach one how to encrypt sensitive files. When set up correctly with a strong password, it would be almost impossible to hack. Even the FBI have had issues decrypting this software. I'm ...more
Google+ has managed to double their user count from three months ago, now standing at over 90 million Google+ accounts created. But how did it get so many so quick? By tricking people who are signing up for Gmail or a regular Google account into setting up a Google+ account, t ...more
The dreaded moment you hope never happens—someone has stolen your laptop. You could have private information, pictures, or even private information belonging to the company you work for, all lost forever. It can cause you pain, money, or even a job. There are paid services th ...more
At GDC 2011 this past March, three of the world's best game designers participated in a contest called Game Design Challenge. Each presented their vision for a game that fit the prompt "Bigger than Jesus: games as religion" before an audience, with applause to determine the wi ...more