Google is known for merging older products into a new one's ecosystem for ease of use. The transition can take time, and that's the case with the old Google Wifi system now that Nest Wifi is out. Google is working on phasing out the dedicated Google Wifi app in favor of using ...more
You've probably connected your Android device to dozens of Wi-Fi networks since you've had it, and your phone or tablet remembers each of them. Whether it's a hotspot at home, school, work, the gym, a coffee shop, a relative's apartment — or even from a friend's phone — each t ...more
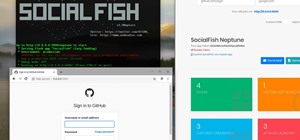
A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwa ...more
Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a smal ...more
These days, if you're having friends over, they'll probably ask to log into your Wi-Fi network before asking for a drink. But if you've forgotten your password, it can be quite hard to find, since most devices obscure the characters with asterisks. But it honestly doesn't tak ...more
While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show y ...more
RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices. I initially covered RouterSploit on Kali Linux and macOS (OS X), but this tuto ...more
It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement. Whether you are a journalist, a protestor, or a hi ...more
If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment. Using a directional Wi-Fi antenna and Wireshark, we can create a display filter to target any device in range to plot the signal strength on a gra ...more
The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac ...more
Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily act ...more
While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one ...more
Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the ...more
With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardri ...more
When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular p ...more
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up ...more
A surefire way to delight this holiday season is with the latest tech. Gadgets today aren't cheap, but we've got you covered with some useful gear that's perfect for practically everyone — at a price that won't break the bank. If you need a last-minute present, check out the b ...more
The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from eve ...more
Apple has a few exciting surprises for you in its latest iOS 16 and iPadOS 16 software updates. Released on Thursday, May 18, version 16.5 includes new features, bug fixes, and security patches, and there are even hints of some big things coming in future software updates for ...more
With the release of iOS 15.4, iPadOS 15.4, and macOS 12.3, Apple unleashed a ton of new features. We saw a preview of one of the most anticipated new features way back in June 2021 when it was announced at WWDC, and now it's finally available for everyone with an iPad and Mac. ...more
Not all weather sources are equal. When you're looking at the forecast, you hope that it's at least semi-accurate so you can plan the week and days ahead, but many sources are unreliable. And with the famous Dark Sky API shutting down on March 31, 2023, you'll need an alternat ...more
Apple released the latest version of its iPhone OS, iOS 14.6, today, Monday, May 24. This latest update (build number 18F72) introduces new features like unlocking your iPhone with Voice Control after a restart, Apple Card Family support for up to five people, and subscription ...more
Thanks to online music services like eMusic and iTunes, compact discs are becoming a far distant memory, turning local music shops around the country into desolate wastelands. The once mighty movie rental store Blockbuster is now bankrupt because of online streaming services l ...more
Many FarmVille farmers want money fast, or experience fast, or want to level up, or want to speed things up— make and earn things faster. No matter how long they play, they're not getting what they want, and that is to outshine everybody else. But you can't reach the top by si ...more
Whether it's the new iPad Killer or not, one thing's for sure—the Motorola XOOM is hackable. Just hours after its release last week, Verizon's new Android-based tablet (running Honeycomb) was rooted by hacker Koushik Dutta, which seems easy enough. "Since it’s another Google ...more
Kip "Kipkay" Kedersha is known for his intriguing and clever how-to and prank videos, even when he teams up with MAKE Magazine. He will show you how to tweak, hack, mod, and bend any technology to your hacking needs. No electronic device, gadget, or household item can stand th ...more
In this installment from the Unorthodox Hacking series of computer security videos, you will explore a few of the areas in Windows that most Sysadmins don’t even know exist. See how to become Local System through the Task Scheduler and abuse long filenames. Take a look at some ...more
WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling. First, U.S. Senator Joe Lieberman swayed Amazon's decision to stop hosting WikiLeaks. Then, Tableau Software removed graphs from th ...more
So, a lot of people seem to be having trouble rooting their Motorola Droid X smartphone from Verizon Wireless using ADB (Android Debug Bridge). Well, there is an alternative for those having problems with the ADB version. You will need to have a Wi-Fi or Bluetooth widget handy ...more
In this tutorial, learn how to access your phone's data network to enable free tethering on your new HTC EVO 4G. By tethering with your EVO you can connect up to eight other devices to your phone and use it as a wireless modem. This hack works with any EVO and will allow you t ...more
Find which airlines Google is providing free Wi-Fi on this holiday season, fix shutter lag on digital cameras, wipe your hard drive for free, improve your Wi-Fi router performance, adjust your television and monitor for accuracy, choose the best 1080p projector, use a single s ...more
Interested in tethering a WiFi device to your Google Nexus One phone? This guide will show you how it's done. Whether you're the owner of a Google Nexus One Android smartphone or just covet one, you're sure to enjoy this Nexus One owner's guide from Nexus One Hacks, which pres ...more
Want to play the original Super Mario Bros. on your HTC Evo 4G phone? Whether you're the owner of an HTC Evo 4G Android smartphone or just covet one, you're sure to enjoy this Evo owner's guide from HTC Evo Hacks, which presents a complete, step-by-step walkthrough of how to i ...more
ChickHen R2 is the most popular PSP hacking software out there, but getting it to work on the many different version of the system is tricky. This easy-to-follow video will show you how to install ChickHen R2 on any PSP with firmware version 5.03. This will allow you to play b ...more
Nintendo 64. It's the classic video game console and probably houses a bunch of your fond childhood memories. Well, now you can relive those tender moments AND play Super Mario Brothers on the go by hacking your Nintendo 64 just a wee bit. Check out this video to learn how to ...more
Looking to make use—if not necessarily good use—of your old hard drives? This how-to presents instructions for creating a hard drive speaker system to use in conjunction with an MP3 player. To follow along, you'll need an MP3 player (e.g., the Samsung YP-S3), at least one spar ...more
Wondering how to most effectively combine ice cubes and a simple USB-powered computer fan into a fully functioning air conditioning system? In this video tutorial, you'll learn how to hack a coffee can and USB-powered fan into a simple, but effective, air conditioning unit. Fo ...more
Screw the airplane man. Ticket prices are too high. Competitive consumer choices are pretty much nonexistent. And need I go into the pain of being crammed into those tiny seats, elbow-to-elbow, thigh-to-thigh with a perfect stranger? Even your average Richie Rich winces at the ...more
There are several different kinds of disc drives that come in different iterations of the XBox 360, and each one has to be hacked a little differently. This video will show you how to flash the ms28 drive used in some systems, the second part of the video will show you how to ...more
If you're tired of paying $60 for new XBox 360 games or waiting years for them to get cheaper, you should probably mod you system. This will allow you to play burned copies of games for free (no time to get into the moral implications here). The first step in that process is f ...more
Want to see whether your PC is being accessed by hackers? Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and W ...more
Now that you're officially allowed to do it, jailbreaking your iPhone, iPod Touch, or iPad is a better idea than ever before! This video will show you everything you need to jailbreak a wide variety of Apple devices, including the iPhone 3G and 3GS, the iPod Touch 2G and 3G, a ...more
Yes, the Droid X from Motorola can be rooted, and yes, you can do it at home. Just make sure you follow the directions precisely. If you succeed, you'll have a completely rooted smartphone. eFuse doesn't matter. If you want to expand your options on Verizon Wireless's Droid X, ...more
Many have tried to prove (or disprove) that tennis ball lock picking really works, but it still seems up for debate. Mythbusters have supposedly debunked this technique (watch the video). Someone over at the Auto Blog also has tested this car lock method with failed results (w ...more
Before, eReaders were only used to read eBooks. Not anymore. As tablet computers become more and more advanced, eReaders like Amazon's Kindle, Sony's Reader and Barnes & Noble's Nook are forced to expand their capabilities beyond the basic bibliophilic needs. And the first to ...more
Do you want to be able to play games for free on your XBox 360? If you have some time and patience, hacking the console is probably the next step for you, and the first step in that is flashing your disc drive. This will delete it's native firmware, which does not recognize bu ...more
Enjoying the many benefits of Facebook Places? But what if you want to check in somewhere you're not? Your smartphone can automatically detect your geographical location, preventing you from just checking in just anywhere, but like all technology… it's a long way from perfect, ...more
This video tutorial will teach you how to use the Nintendo Wii Shop Channel to download and play your favorite console games on your Nintendo Wii. To follow along, you'll need either a WiFi Internet connection or Wii Lan adapter. Instructions: 1. Click on the Wii Shop button ...more
The PSP has never had the software support that it needed to be a really commercially successful system. Since Sony blew it already, you may as well go the extra mile to make this expensive little thing you bought more useful right? This video will teach you how to hack a PSP ...more
Some people (including myself) are seeing a "Hold" button instead of the "FaceTime" button when calling people on our new iPhone 4. It turns out this problem comes from a bug where Apple disables FaceTime on the iPhone 4 if you restored from an iPhone 3G. To get your missing ...more
Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episod ...more
My girlfriend was going away for a few weeks, but where she was going, there was no easily accessible Internet. She works mostly on the web, so it was imperative that she have a decent Internet connection during her travels. So, tethering her phone was the only real possibilit ...more
Warnings i cant be held responsible for any illegal act done by anyone but myself and there are copyrights so notise that taken the trademarks or copyrights are strigtly prohibeted by law and will be punshied by law and i or my partners cant be held responsible for sudo camma ...more
In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack. Before we start hacking, let's familiarize ours ...more
If your computer is working slow--or not at all, there could be some unsavory programs running amok in your system. Trojans, malware, viruses, and hacks are dangerous to the health of your operating system. This video tutorial demonstrates the measures to take in order to rid ...more
NetBus—Swedish for NetPrank—is a Trojan horse application that will allow you to remotely control any Windows system that runs it (provided that system is not running anti-virus software). For more information, and to get started using the NetBus hacking tool for yourself, wat ...more
Did you know that your Nintendo Wii can go online? If you haven't been using the Internet with your Wii, you are missing out on some of the system's coolest features. With an Internet connection, your console can surf the web, watch movies from places like Netflix, or connect ...more
For Infinity Exists Full Disclosure's first Website Hacking episode, we demonstrate how to exploit a security vulnerability occurring in a website's database to extract password hashes. Sql (Structured Query Language) is a computer language designed for the retrieval and manag ...more
This Null Byte is a doozey. On Sunday, September 19th, an exploit for the latest Mac OS X 10.7 "Lion" was discovered by Patrick Dunstan. This exploit allows for an attacker, even remotely, to request to have the root user's password changed without knowing the password to the ...more
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to analyze p ...more