This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing p ...more
It looks like Sony is adding some cool features to their upcoming portable game system called NGP (Next Generation Portable). It will have a front and rear camera & Six-axis motion sensing system (three-axis gyroscope, three-axis accelerometer), Three-axis electronic compass. ...more
Your BIOS, or Basic Input Output System, is the firmware on your motherboard responsible for initializing your computer's hardware when it is first powered on. It probes for video adapters, RAM, the whole works. The BIOS provides a small library of basic input/output functions ...more
Trying to focus on studying for your Stats final in the library but getting a serious ADD spell? Then make use of your time - while having a little fun with whoever else is in the library - by hacking into your computer's command prompt. The command prompt is the most basic o ...more
This tutorial will only work on a slim model PSP. If you have one, follow the steps outlined in this video to get a TV icon to show up on your Playstation Portable. It's super easy, and a fun way to hack your game system.
9GAG's infographic teaches us all sorts of conveniences and short cuts to daily life, urawaza style. Some aren't complete revelations (the first hanger trick below), but others are pretty cool (if they work!). A few I wouldn't mind trying: free wifi at the airport ice cold dr ...more
In this clip, you'll learn how to find and connect to WiFi networks on a desktop or laptop computer running the MS Windows Vista operating system. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-c ...more
Want to change your iPod background to something cool? This video shows you how to hack a click-wheel model to reset your iPod and gain access to the system center so you have the option to set a variety of different backgrounds and wallpapers for your iPod.
A great tool for any system administrators, the iPhone (or other Apple wifi device) app Ping a Majig allows you to enter in the IP addresses of websites. Then you can keep checking on them to make sure they are running smoothly and operating correctly. You can click on the web ...more
Windows 7 is awesome, and here are four super cool secret tips to make it look even better. Say hello to your new operating system! Learn how to use aero shake, jump lists, libraries, and more. Watch this video and learn how to use some of the new features on Windows 7.
http://www.texturemind.com/post463/ TypingRobot is an artificial intelligence studied to increase your points record with the Typing Maniac game on Facebook. It can recognize several labels because it uses a powerfull OCR system (tesseract) and some principle of word correcti ...more
Check out this cool hack from The Emo Lab. This video tutorial will show you how to boost performance in Window XP! First, learn how to create a restore point, then get down to business learning how to boost the performance of you Windows XP system. Here is the Emo Lab proje ...more
This is a really simple video guide on how to install Hackintosh OSx86 (Mac OS X) on a PC. OSx86 is a portmanteau of OS X and x86, a so-called collaborative hacking project to run Mac OS X computer operating system on a non-Apple brand personal computer, with x86 architecture ...more
This hacker's guide demonstrates a quick PHP script which may allow you to crawl through the operating system on your hosting provider. demonstrate the power of PHP on a Virtual Host, or vhost, if PHP is not correctly secured by your web hosting provider. For more information ...more
Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial pre ...more
Learn how to build an environmentally friendly directional WiFi antenna with this simple video guide. To follow along at home, you'll need the following things: a copper wedge, an N-type connector, some screws, a clamp-on N plug, a pigtail, and a wireless card. You'll also nee ...more
Blue tooth is slowly becoming more widely used for its hands off convenience. However, most people have a problem with the audio volume the bluetooth provides. Take a look at this instructional video and learn how to hack a bluetooth speakerphone mod for your cellphone. Speake ...more
Understandably, the tragedy in Japan has substantially risen the level of worldwide radiation-related hysteria. So much so, as an alternative to stampeding health food stores for iodine tablets, crafty individuals and organizations are hacking together personal radiation detec ...more
The iPhone and iPod touch are nearly identical devices, especially now that Apple has added a front-facing camera to the iPod touch. All that's missing is the phone part. With the help of Lifehacker and apps like Skype and Line2, you can save some money by turning your iPod To ...more
Unlock your Galaxy's hidden potential by rooting it! Rooting your phone will enable you to do fun, against-the-rules things like running custom ROMs. Want to turn your Galaxy into a wireless hotspot with free WiFi tethering? You can do that too. Don't know how to root an Andr ...more
Unlock your HTC Tattoo's hidden potential by rooting it! Rooting your phone will enable you to do a great number of fun, against-the-rules things: Interested in running a custom ROM? It's easy. Want to turn your Milestone into a wireless hotspot with free WiFi tethering? Go ah ...more
Unlock your Motorola Milestone Google Android's hidden potential by rooting it! Rooting your phone will enable you to do fun, against-the-rules things. Interested in running a custom ROM? It's easy. Want to turn your Milestone into a wireless hotspot with free WiFi tethering? ...more
There are so many hackers around these days, and they are becoming very smart. So smart that they have successfully taken down many government websites. The most recent attack was on the Department of Justice (DOJ). To read about the history of these hackers, check out Wikiped ...more
Since the day of the Xbox 360 release, storage space for the device has been overpriced beyond belief. OEM 250GB HDD models still cost $110 USD! A 250GB hard drive should not destroy my wallet, Microsoft. Storage space, especially on HDDs, is cheap. You can buy a removable 2TB ...more
Since the early genesis of the brilliant Microsoft Kinect hack, inventive applications have been popping up nonstop. One of the most fascinating projects to surface recently falls within the realm of 3D printing. "Fabricate Yourself"—a hack presented at the Tangible, Embedded ...more
When choosing a security system for the office, Billy Chasen decided to ditch the traditional lock & key barricade for something a little more 21st century. He hacked together a device that uses a web server, servo motor and some parts from Home Depot to enable locking & unloc ...more
Play all of your favorite Nintendo games on your Apple iPhone, iPad or iPod Touch! In this iPhone hacker's how-to, we learn how to use Cydia to download and install a Nintendo Entertainment System (NES) emulator on a jailbroken Apple mobile device. This hack works on the iPho ...more
Ah, Windows Vista. Amongst all the versions of Microsoft Windows, this particular operating system was designed far more for looks than actual function. Windows Vista offers limited ability for the users to customize programs and files. However, if you are having trouble boot ...more
Hallelujah, a miracle tool has been released to the world. This Windows/Mac tool is called Spirit and it enables you to jailbreak any iPhone, iPod Touch or iPad quite easily. And Gizmodo is all over it, with an in-depth guide on exactly how to do it. Some of you may be hackin ...more
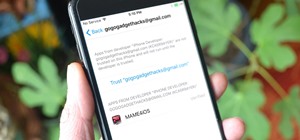
The Internet is full of crooks just waiting and waiting for the chance to steal your information. One way that people are getting into your system these days is with fake or rogue applications. These viruses sneak themselves onto your PC either through hacked websites or when ...more
In this Computers & Programming video tutorial you will learn how to change the default Windows Remote Desktop port. It is actually a registry hack. You can check the IP address of our machine by typing ipconfig into the cmd prompt. For hacking into a machine, you should have ...more
Do you own an iPhone or iTouch and are looking to learn how to SSH into your phone? You've come to the right place. Learn how to SSH into your Apple device with help from this video. In addition, you will learn how to open a virtual connection with your iPhone or iTouch & your ...more
This video shows you how to get every single Fallout 3 achievement, almost instantly, with no mods, or hacks. The steps performed are the following: Install Fallout 3 Sign into your account Press the ~ button to open the console (It's left of your 1 key and above the TAB butt ...more
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to get free ...more
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to program a ...more
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to secure re ...more
Hacking into computer systems to steal passwords could be a bit complicated for the average everyday joe, but for all of your tech illiterate folks out there, there's any easy way to get that password, and all it takes is a camera. Check out this con video tutorial to learn h ...more
This is a video walkthrough of the ultra violent and gory game MadWorld, exclusively for the Nintendo Wii. Mahalo has produced this full walkthrough for MadWorld, complete with high-quality videos. The guide explains everything from the point system and basic combat techniques ...more
This is a video walkthrough of the ultra violent and gory game MadWorld, exclusively for the Nintendo Wii. Mahalo has produced this full walkthrough for MadWorld, complete with high-quality videos. The guide explains everything from the point system and basic combat techniques ...more
These are video walkthroughs of the ultra violent and gory game MadWorld, exclusively for the Nintendo Wii. Mahalo has produced this full walkthrough for MadWorld, complete with high-quality videos. The guide explains everything from the point system and basic combat technique ...more
Find the ins and outs to UPS hacking in this video from Systm! And were not talking about the parcel service here—we're talking about your UPS system—your uninterruptible power supply, which can be pretty weak. That's why you should hack the tiny battery out of it and replace ...more
Are you a ... Windows Developer? Interested in ... testing the vulnerabilities inherent in your own operating system? If so, you're in luck. This video tutorial demonstrates a simple hack that will allow you to remove the Windows Genuine Advantage Validation software. For step ...more
The most successful video game packaged with almost all Windows PC's is probably Minesweeper, so it was just a matter of time before someone figured out how to beat the system and detect all of those mines without getting blown to smithereens. This video shows you the trick to ...more
As advanced gaming systems continue to evolve, older classics like the Nintendo Entertainment System (NES) are one step closer to extinction. They're rotting in the basements of gamers. They're gathering dust at the local pawn shop. Or worse... being thrown out in the trash li ...more
WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most ...more
Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and r ...more
Social engineering is described as the clever manipulation of the natural tendency of human trust. All of the passwords, locks, and encryption in the entire world are useless against a good social engineer who can charm or trick you into giving it up. But what once started as ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. This week has been an exciting one. The com ...more
Have you ever forgotten your password and didn't know how to get back on your computer? Or ever had an annoying roommate you wanted to play a trick on to teach them a lesson? Or perhaps overly religious parents who think the internet is of the devil and won't let you read onli ...more
Have you ever been away from home or on holiday and noticed an open network connection? FREE INTERNET! But then you find out that every search or page redirects you to an "enter password" or "signup here" page. Well, there are ways around this. In this article, I'll show you ...more
Thanks to Yifan Lu, it's been discovered that the operating system running on the Kindle Touch is written mostly in HTML5 and JavaScript, unlike the previous models which used Java. This is exciting, because when a device is hacked or rooted, that means homebrew programs can b ...more
Hello and welcome to yet another InfoSecurity World tutorial. This post is based on the Windows 7 'GodMode' panel. Windows 7 comes with many hacks, cheats and tweaks. This bonus lesson will teach you how to create Windows 7 GodMode. GodMode works a lot like the Windows Contro ...more
With a lot of Null Byters playing around with Linux because of its excessive use in the hacking world, some of you are bound to run into some trouble with the installation at some point or another. If you make a mistake, or you're intimidated by the wonky-looking installation ...more
Ever since kernel 2.6.xx in Linux, a lot of the internet kernel modules for wireless interfaces ended up becoming broken when trying to use monitor mode. What happens commonly (to myself included) is a forced channel that your card sits on. No good! For users of airodump and t ...more
This is the Windows OS counterpart to my tutorial on how to burn the new XDG3 formatted games on Xbox 360. Microsoft invented a new disc format system to trump piracy, it's called XDG3. XDG3's standard is to burn a whole extra gigabyte of data to the disc, to allow more conten ...more
When the New York Times paywall first went up, there was a whole lot of balking. The idea seemed egregious to most, and the digerati's overwhelming conclusion was that the system would fail. But interestingly enough, there is speculation that the NYT is actually experiencing a ...more
As a kid, my favorite thing to do at the Natural History museum was a midday stop, when my family strolled past an antiquated looking vending machine in the museum's musty basement. The Mold-A-Rama machine was oddly shaped, George Jetson-esque, and spewed out made-to-order, br ...more
Have an old-school tabula recta lying around? No? Then just print out the chart below. Nothing ensures better password security than this centuries-old cipher technique. Here's how it works, via Wikipedia: "Using a tabula recta, each alphabet is shifted one letter to the left ...more
Thanks to Microsoft’s XBOX 360 motion-detecting system, Kinect, the world is becoming a play place for sci-fi style virtual reality. One of the latest hacks demonstrates the next best thing to regular old air guitar... virtual reality air guitar: Artist Chris O'Shea explains h ...more
For the coffee addicts, Redditor therewillbesnacks shares a wealth of insider tips for cheating the Starbucks system. A dollar here, a dollar there- it all adds up. Below, a few highlights from the thorough posting: "If you and a friend are out and want a Frappuccino, ask for ...more