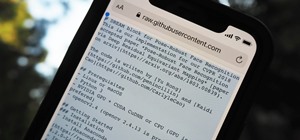
With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device. UserLAnd, created by UserLAnd Technologies, is a completely free Android app that makes installing ...more
Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and ...more
Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/ne ...more
Mobile phones are not only essential for work and communication, they're quickly becoming an integral asset to our health. Your iPhone can store valuable data about fitness, nutrition, heart health, and so much more. And since iOS 11.3, your iPhone can even import a list of al ...more
Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by d ...more
Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get ...more
OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers, Welcome to my 5th Post, In this tutorial I am going to show you how to make the backdoor we created in my guide here a persistent one. I finally found out a way to do this, as I was/am very ...more
Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement t ...more
Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all o ...more
Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features. In my first Metasploit installme ...more
Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly al ...more
Whether you want to edit photos, compress files, play games, or DJ your next party, there's a free Mac app that can help you out. But things can get annoying real fast if you download a lot of free apps from the Mac App Store, since you have to type in your Apple ID password e ...more
Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this in ...more
Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password ...more
Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly d ...more
As the industry has shifted toward OLED (including Google's own Pixel lineup), the outcry for dark mode has been louder than ever. Google heard the cries and has been working toward a real system-wide dark mode. To lay the groundwork, they are adding the feature to all their a ...more
Apple just released the second public beta for iOS 12.3 today, Tuesday, April 9, one day after the release of the iOS 12.3 developer beta 2. This update introduces new Japanese "Date & Time" updates as well as changes to Wallet transactions. Overall, iOS 12.3 includes Apple TV ...more
Apple just released iOS 12.3 dev beta 2 today, Monday, April 8, which follows the first iOS 12.3 beta by twelve days. This update introduces new Japanese Date & Time features as well as updates to Wallet transactions. As a whole, iOS 12.3 introduces Apple's previously announce ...more
In Android 10, Google is letting you adjust the accent colors to give your phone a bit of flair. When combined with the new system-wide dark mode, you are looking at eight different color combinations. That is seven more than we had in the previous version and seven additional ...more
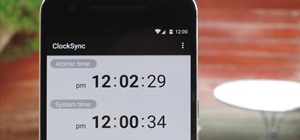
For most Android phones, the system clock is set using a protocol called NITZ, which relies on a connection with your carrier to ensure that the time stays in sync. The trouble here is that this feature won't work when you're outside of cellular range, and a lot of times, the ...more
Android 6.0 Marshmallow is bringing in lots of changes to our favorite smartphone operating system, ranging from battery-saving tweaks like Doze to a Now on Tap feature that essentially bakes Google right into every app on your phone. But for folks that like to tweak the inter ...more
Apple's latest round of devices—including the MacBook Pro, Apple Watch, and the iPhone 6S—use a new touch input method that can detect when you've applied a bit more force than usual. Dubbed "Force Touch" ("3D Touch" on the new iPhones), this gesture simulates a long-press or ...more
Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you ...more
Welcome back, my greenhorn hackers! This tutorial will be the fourtenth in the Linux for hackers series and will focus on the MySQL database. Although this is not strictly a Linux tutorial, MySQL is the database of choice on most Linux distributions. In addition, it is the mo ...more
Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all beca ...more
With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassin ...more
Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacki ...more
Apple's MacBook line of laptops is quite famous for their extensive battery life, thanks to various technologies that Apple has utilized. However, all things must pass, and over time your MacBook's battery will degrade. Certain use scenarios can accelerate the degradation of t ...more
Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems ...more
Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now. Mr. Robot is about a young man with ...more
Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal. This ...more
Welcome back, my aspiring hackers! One of the areas that often gives Linux newcomers problems are the environment variables. Although Windows systems have environment variables, most users, and for that matter, most administrators, never manage their environment variables. To ...more
Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. ...more
Welcome back, hacker novitiates! In the next few hacks, we will be breaking into Windows servers. In this installment, we will learn to add ourselves as a user to a Windows 2003 server. Of course, when we have added ourselves as a user, we can come back any time and simply log ...more
Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands. RapidScan does an excellent job of automating the deployment of vulnerabili ...more
Apple's iOS is a great operating system, but it's not without its faults. Minor quirks have plagued the Apple community for years, such as a general lack of customization, a poor notification system, and some interesting UI choices like the intrusive volume popup. With iOS 11 ...more
Everyone loves emojis, but some folks aren't quite happy with the way the little yellow guys look on their particular phone. In order to replace them, however, your device needs to be rooted, and you'll usually need to perform some complicated procedure that ends up making you ...more
Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this t ...more
I've done numerous tutorials in Null Byte demonstrating the power of Metasploit's meterpreter. With the meterpreter on the target system, you have nearly total command of the victim. As a result, several of you have asked me for a complete list of commands available for the m ...more
10 Life Hacks: 1.Wifi Booster 2.Spray Bottle 3.Mosquito repellent 4.Untie Plastic Bag Knot 5.Tootpaste Hole cover 6.Remote Control fix 7.Vibrating Toothbrush 8.Shoe Reminder 9.Zip Bag Protector 10.Colored Keys Video: .
Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on. ...more
A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, m ...more
Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering. One such distribution is Pentoo, a Gentoo-b ...more
With the same starting price as its predecessor and a nice list of improvements, the OnePlus 6T is a great buy for a number of reasons. But for many Android users, the main selling point for the latest OnePlus flagship is how easy it will be to root and mod the device. We jus ...more
There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your comput ...more
Tesla founder and CEO Elon Musk offered some insight into how hackers might seek to turn driverless cars into zombie fleets, but remained upbeat about what can be done about it. Speaking at the National Governors Association this weekend, Musk covered a lot of ground when ask ...more
No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks. Most iPhone and Android phones run on a Broadcom Wi- ...more
Verizon Wireless executives recently cooked up a plan so devious that it could have only come from one of the four major US carriers. Apparently, they aren't satisfied with simply loading every Android device they sell with their own bloatware, so now they're reaching out to b ...more
Wi-Fi signals have limited range, so if you live in a two-story house or work in a larger office, you may have set up multiple routers or repeaters to ensure full wireless coverage. Sadly, Android handles the transition between networks pretty poorly. The main issue here is t ...more
When was the last time you restarted or shutdown your Mac? In the post-iPhone era, most devices are now powered on almost constantly. For better or for worse, the computing landscape has accommodated this "always on" trend, but you still need to periodically restart your devic ...more
This is a how to to change any user password on a windows 7 computer. If you forgot your password you can change any account password even if you are locked out of your account. Warning I am not responsible for any damage done to any computer in the process of this hack or an ...more
Android's Quick Settings menu is quite handy—just swipe down with two fingers from the top of your screen and you're ready to toggle several different system settings on or off. It got even better with Android 6.0 Marshmallow, since you can even use the hidden System UI Tuner ...more
Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc. Any time someone's computer seems to act ...more
Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them. In each ...more
Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 month ...more
Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to ge ...more
If you thought humans were reading your résumé, think again. Robots do, and their one solitary objective is to systematically crush the hopes and dreams of those who don't make the cut. Instead of paying a few humans to read thousands of résumés over a couple weeks, many compa ...more
Welcome back, my hacker novitiates! Like in my last article on remotely installing a keylogger onto somebody's computer, this guide will continue to display the abilities of Metasploit's powerful Meterpreter by hacking into the victim's webcam. This will allow us to control t ...more
Spam calls are one of the most annoying things to happen in the world of smartphones for more than one reason. Not only are they bothersome, but they can also be dangerous to people who don't know any better. Google has come up with a crafty solution known as "Call Screen" to ...more
As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing ma ...more