Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft ...more
Welcome back, my greenhorn hackers! Congratulations on your successful hack that saved the world from nuclear annihilation from our little, bellicose, Twinkie-eating dictator. The rest of world may not know what you did, but I do. Good job! Now that we hacked into the malevol ...more
For years, Skype has been synonymous with video calling and messaging. However, as the industry moved toward encryption and privacy, Skype usage was discouraged by experts due to its murky encryption. To combat this, Skype has introduced true end-to-end encryption. While Skyp ...more
Research group OpenAI, a research institute co-founded by Tesla CEO Elon Musk, says it is possible to trick driverless cars' neural networks into mistaking images for something else. In a blog post published on OpenAI's website, Anish Athalye, an undergraduate studying comput ...more
When Facebook purchased WhatsApp for $19.3 billion back in 2014, we all knew this was coming—it just took longer than we thought. But starting today, the data mining became official, and now, information from your favorite messaging app is no longer out of reach for the world' ...more
The notification light on phones and tablets is slowly disappearing. The once staple feature is now only found on a few devices, and a bevy of other notification systems have sought to fill the gap. The most popular of these systems is Ambient Display, which has grown in popul ...more
Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids to ...more
iOS 12 has a feature that lets you instantly share saved Wi-Fi passwords with other iPhone users, but it can be finicky when you're sharing with multiple people. Then there's an even more pressing question: How do you share your password with Android users? Thankfully, there's ...more
The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data. Apple introduced so ...more
Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a b ...more
On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated ...more
If you're watching videos over Wi-Fi on your iPad, iPhone, or iPod touch, iOS 10 lets you adjust the quality for when you want to save data or need help watching a movie or TV show on a poor connection. To do so, open up the Settings app and scroll down to Videos, then select ...more
Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expa ...more
Sometimes you might find that a certain app keeps sending you notifications. What are you to do? There are plenty of useful apps that might send one too many push notifications, but that doesn't mean you should dump them. Luckily, Android gives you complete control over how ea ...more
For many, the stock version of Android is often considered the epitome of what the operating system should look and feel like by default. It's clean and clear of unwanted extra apps that come pre-installed with the system, provides a fluid and fast user experience, and runs on ...more
Hot on the heels of all the talk about Google's newest Android Q update, known as Android 10, there's a new beta to check out. OnePlus is one of the many partners that can now offer its users a chance to test the latest version early. That means you can install the newest Andr ...more
When flashing files through TWRP, ADB, or Fastboot, there's a slight chance for things to go wrong. Whether it's user error related or something else entirely, it's always good to have a backup plan. In most cases, you'll be dealing with a semi-brick or soft-brick, which can u ...more
Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods. A bootloader is a program that starts up on a device that states what operating system it ...more
Battery drain is a major pain point for Android users, though that promises to change thanks to Android Pie's new Adaptive Battery feature. But Google hasn't said much about the inner workings of this feature, only publicly stating that it uses AI to boost battery life. So we ...more
Although the Essential PH-1 got off to a rocky start, thanks to steady updates, it has slowly become one of the best Android phones to come out in recent years. For $499, the Essential Phone is a cheaper Pixel, receiving updates almost as soon as the Pixel lineup does. What's ...more
These days, it seems new phones get announced every other week. We've grown accustomed to glossing over the specs, looking at some press renders, then moving on to check out the next phone. If you had done this in September 2008, you might have overlooked what would become one ...more
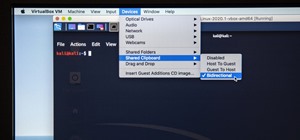
Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listenin ...more
The OnePlus 5 had been in the hands of the public for a meager twenty hours before developers on XDA released a custom recovery image for it, and the 5T had a similar trajectory. The installation process is simple enough, but it can be somewhat confusing if you're new to moddi ...more
The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB ...more
Apple just pushed out the iOS 10.3 update to everyone on March 27, so if you haven't installed it yet, make sure to do so by going to Settings -> General -> Software Update. Trust us, you'll want to. iOS 10.3 is a fairly major update, and will succeed iOS 10.2.1 on your iPad, ...more
In the recent hit movie Furious 7, the storyline revolves around the acquisition of a hacking system known as "God's Eye" that is capable of finding and tracking anyone in real time. Both the U.S. spy agencies and an adversarial spy agency (it's not clear who the adversary is, ...more
Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associa ...more
Google has finally released the next version of the world's leading operating system—Android 6.0 Marshmallow. This latest iteration isn't as much of a visual overhaul as Lollipop was, but it packs in more new functionality than almost any update before it. Awesome features lik ...more
Hello my fellow hackers, it's been a while since my last post, I can't get the time now-a-days for the posts but can manage to tend to comments. Welcome to my 9th post, this tutorial will explain how to extract and decrypt WhatsApp database from the Victim's android system. ...more
Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that ru ...more
Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?" In this tutoria ...more
While photography usually gets all the love, our phones have gotten really good at capturing video. Think about it — when was the last time you needed a camcorder for a vacation? With mobile cameras getting better each year, we're now at a point where smartphones can be used f ...more
Gboard has come a long way from its roots as the "Google Keyboard" in the earlier days of Android. It's now the most popular, feature-rich, and useful keyboard app on the market. Google even includes quite a few themes right out of the box for Gboard — but what if you could ha ...more
With the rise of OLED displays, Android users have been begging Google for a true system-wide dark mode for years. While a system-wide solution is still somewhat unlikely, Google has given in by providing a dark mode for certain apps, including Contacts. With most phones rock ...more
Samsung makes more than just the Galaxy S and Note series. With a large portion of the world not able to afford phones with flagship specs, Samsung makes several different series that focus on price. The latest is the Galaxy A6, a budget option with a flagship feature. The Ga ...more
I don't know about you, but nothing is more annoying than when my phone hits 15% and I'm nowhere near a charger. Not just because I know my phone will die soon, but until I reach a charger, I have to deal with the annoying low battery notification and LED light. Well, with And ...more
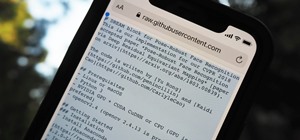
A massive leak appeared the web today, and it's got some huge security implications for every iPhone on the market. On the plus side, it also has some potential for enabling deep-level modifications and jailbreak tweaks. GitHub user ZioShiba posted the iBoot source code for i ...more
One major iOS 11 improvement that Apple skimped out on during its WWDC presentation was the redesigned storage management system, which makes it easy to view storage consumption in greater detail on your iPhone — and even easier to free up storage space with surgical precision ...more
It's always nice getting paid to do something you love. That's why Nintendo is offering all Nintendo Switch owners a chance to find vulnerabilities before another hacker beats them to it first. Depending on the vulnerability you find, Nintendo is willing to shell out rewards s ...more
When Google added new security measures to Android Marshmallow, it had a lasting impact on the entire process of rooting. These measures prevent the the Superuser daemon (the process that handles requests for root access) from getting the permissions it needs to do its job at ...more
The first public beta of Android O, (most likely to be called "Android 8.0 Oreo") was released on May 17, bringing tons of new features and goodies for Android enthusiasts with supported devices. However, not all of Android O's features were available to try out right off the ...more
ViPER4Android is a revolutionary audio equalizer for Android, something that I personally can't live without. That's the reason why porting V4A to the LG V20 was the first thing I did when I got the phone. There are two variants of ViPER4Android: FX and XHiFi. XHiFi is an olde ...more
The LG V20 went on sale on September 29, 2016, and is the second flagship phone in the V series to be released by LG. Both the V20 and its predecessor, the V10, have been audio-oriented phones from the start, but the V20 has a much nicer Hi-Fi Quad 32-Bit DAC, which makes the ...more
The widget system on iOS leaves a lot to be desired when compared to Android's offering, but that's not really Apple's fault. The system is there, we just need some good widgets to really get the most out of it, so it's up to developers to create some awesome apps that work wi ...more
Let's say you gave your Wi-Fi password to your neighbor a while back, under the assumption that they'd only use it while they were at your house sharing stuff via Chromecast. But now, your connection is slower than it normally should be, and you have this sneaking suspicion th ...more
A custom recovery is a very powerful tool. You can flash ZIPs that modify your Android device in ways that not even root can accomplish, and of course you can use it to install custom ROMs. But when you're applying all of these cool mods, there's always a chance that something ...more
There's one thing that I've always liked about iPhones, and that's their centered digital clock in the status bar at the top of the screen. On Android, it's always on the right side by default, and there's no easy setting that lets you just change it to the center position. Bu ...more
One of Android's biggest strengths relative to iOS is the fact that you can use any app to open compatible links, not just the stock ones that come preloaded on your device. When you tap a link that two or more of your apps are capable of opening, you'll see a message asking w ...more
Traditional root ad-blockers like AdAway and AdBlock Plus have no effect on YouTube anymore. Until now, if you wanted to get rid of the commercials that play before your favorite videos, there have only been two ways—either by paying for a YouTube Red subscription, or by using ...more
Imagine if you combined Tasker with your favorite live wallpaper—that's roughly the gist of a new app from developer feedK. With this one installed, your home screen background will finally be aware of its surroundings. Don't Miss: Top 8 Free Wallpaper Apps for Android Afte ...more
Back in iOS 8.4, Apple introduce a new "heart" icon in their Music app, which works in direct correlation with their Apple Music service that was released at the same time. By hearting a song, you're telling Apple that you love that song, and they can make better suggestions f ...more
Apple has stepped up its emoji game lately, and as a result, there are several iPhone emojis that don't show up on Android devices running older firmware. However, Google responded by adding a next-gen set of Unicode 9.0 emojis to its Android Nougat preview build, meaning that ...more
Android 6.0 Marshmallow added a new permissions system that can make your digital life much more secure. Unlike previous versions, apps now have to ask for your consent before they can access certain data, which puts you firmly in the driver's seat. As if that weren't enough, ...more
Android has a built-in browser called WebView that any app can use, which makes it easy for developers to display webpages without actually having to build an internet browser into their apps. But WebView is a stripped-down, bare bones browser with no ties to Android's default ...more
When someone asks me why they should root their phone, one of the top reasons I always give is that it enables you to install the Xposed Framework. Created by developer Rovo89, Xposed basically hooks into the Android system, then allows users to simply install mini-apps called ...more
Everyone's favorite Android modding tool is finally available for the Galaxy S6 and S6 Edge. Thanks to some hard work by Wanam and a few other developers, we can now install the Xposed Framework on Samsung's latest mid-sized flagship phones. But there are a few stipulations—m ...more
Performance boosters generally get a bad rap, but that doesn't mean they should all be dismissed—particularly when they're as well thought out as the latest work from developer Danijel Markov. After recognizing a few inefficiencies in the way Android handles memory management ...more
Carriers like to distinguish their Android phones from the competition by making small changes to the interface here and there. This practice is so common that Android now has a built-in system for managing these small tweaks. A series of XML files known as CSC (customer soft ...more
When it comes to app permissions, Android takes an "all or nothing" approach. You have no granular control over what data apps can access, so the only way to prevent an app from seeing your location or starting up on boot, for instance, is to not install the app in the first p ...more
Welcome back, my aspiring hackers! In this series on Linux for aspiring hackers, I'm trying to provide you with the basic skills needed to be capable in Linux as a hacker. One area that's critical that we haven't covered yet is building and managing an Apache web server. Apac ...more