Android's flexible operating system allows for lots of customization, and one of the most common ways to add personal flair to your smartphone is to set your own ringtones and notification sounds. On Android this feature is no only supported, but it's actually very simple. Ch ...more
Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do t ...more
Live wallpapers have dipped in popularity lately, with many users favoring a single, static image as their home screen background. But this is generally due to still photos offering a more sophisticated look, while traditional live wallpapers can sometimes seem a little less a ...more
Although lots of the bigger hotel chains are lessening the restrictions they put on their room TVs, some smaller ones are still taking measures to prevent you from plugging in computers or streaming devices into an HDMI port. However, there are a few steps you can take to bypa ...more
Cellular carriers like to nickel-and-dime us out of every bit of money they can feasibly justify, so as consumers, we owe it to ourselves to make sure that we're getting our money's worth. There are several under-advertised freebies and discounts that come included with a con ...more
When you click a link from Google search, the link itself turns purple to let you know you've already visited this page. But let's say you're searching for something similar a few weeks from now and you see one of these purple links—you'll probably think to yourself, "What was ...more
Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow. Scenario Let's say, that we have done all the recon(both passive and active) and we have scanned the web serve ...more
OS X is built upon a UNIX foundation, which grants you access to the benefits that UNIX offers, including the standard toolkit (make, gcc, clang, git, perl, svn, size, strings, id, and a lot more) via the command line developer tools, which are an essential if you're a develop ...more
There's no iMessage app on Android, so unlike the folks who own both an iPhone and a Mac, we have to rely on third-party solutions to send and receive SMS messages from our computers. But on the bright side, this means we don't have to buy an exorbitantly expensive desktop or ...more
Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, ...more
Hello there Nullbyte users! This will be my first article here. Feel free to give feedback in the comments! Today I'll be introducing the UNIX text editor VIM. VIM is a text editor that is completely controlled from the keyboard. An experienced VIM user is A LOT faster than ...more
Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic An exploit is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability in order to cause unintended or unanticipated behavior to occur ...more
You've probably heard the old joke about how Ford is an acronym for "Found on Road Dead." Well, the Detroit automaker on Monday announced a new and much better way to help you find your parked vehicle, as well as a whole host of other features—just use your smartphone. Ford mo ...more
Before you sell or give away an old iPhone, Find My iPhone, which works in conjunction with Activation Lock (Apple's anti-theft system) needs to be deactivated from your iCloud account. This also applies if you've lost your passcode and are locked out of the device, if you're ...more
First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell). We will be using Kali version 1 as the attacker machine and Windows 8 ...more
The competition between iOS and Android is fierce. Each operating system offers unique and powerful features, so it can be hard to choose which one you want. However, for iPhone users, a little tweaking and some themes can give your iPhone some of the key features and aestheti ...more
Google Play Music has been my go-to music service ever since its release. The free cloud storage for 50,000 songs and full access to Songza-powered radio stations make it a great music app, even without the $10/month streaming service. The only downside is that the desktop ex ...more
A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you ha ...more
When someone asks me why they should root their phone, one of the top reasons I always give is that it enables you to install the Xposed Framework. Created by developer Rovo89, Xposed basically hooks into the Android system, then allows users to simply install mini-apps called ...more
With a slab-style touchscreen device, butt dialing is always going to be a problem. While you're moving about, your phone can unlock itself and give your most recent contact a ring, leading to an awkward one-sided conversation where the other person gets to eavesdrop on everyt ...more
Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels. "Why would I do that?" One might ask. Good question m ...more
You'll have to forgive me if I sound a little overexcited about this, but in my opinion, Google's "Now on Tap" is one of the most innovative™ smartphone features that I've seen in years. Sure, Microsoft heard about the feature being in the works and rushed out a similar Androi ...more
Android has a brand new mobile payments system, and it's rolling out to most devices as we speak. Android Pay, as it's called, will replace the existing Google Wallet app as an update, and it brings some awesome new functionality such as tokenization and the ability to tap-and ...more
Uninstalling programs in Windows is not the nicest procedure. Some programs bundle a nice uninstaller with them which helps to ease the process. Other programs, mainly those that utilize the Windows Installer technology, begin the uninstall process right away. This can potenti ...more
Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of ...more
Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my ...more
Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I ...more
Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record. OTR does all the right things to make your instant messa ...more
Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes. But while Tor is great for desktop users, since they can simply install a Tor browser or plugin, it's a bit more c ...more
All of those keys on your keyboard can do much more than just help to update your Facebook status or fire off a scathing tweet. By learning all of the keyboard shortcuts for apps on your Mac, you can cut back on mouse or trackpad usage to perform actions faster and more effici ...more
In the past, updating a rooted Samsung Galaxy device has always involved the complicated process of downloading the proper firmware for your variant, installing device drivers, then sideloading the update with Odin. Luckily, though, with the release of the Galaxy S6, Samsung ...more
When setting up a new Mac, there can be a bunch of settings that need to be changed in order to get the system running the way you like it. That usually involves going through tons of System Preferences panes and app settings—but it doesn't have to. If you'd rather get everyt ...more
The next time you're out camping, whether it's outdoors in the wilderness or right outside in your own backyard, try this hack out for an effortless campfire all night long. While there is definitely some prep work involved, it's well worth it if you don't need a huge bonfire, ...more
Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial. THC Hydra is very prominent online brute-force tool and ...more
While a mobile game developer may have built something unique, they still have to go through an arduous process of fixing bugs, smoothing out gameplay, making sure it works on different screen sizes, and following Apple's rules before they can submit their game to the iOS App ...more
There are several reasons that you might want to restore the factory firmware on your device—maybe you need to send your phone back for warranty purposes, or perhaps you're getting ready to accept an over-the-air update and need to unroot first. In some cases, reverting to the ...more
While its hardware may already be a little outdated compared to newer flagship phones, the OnePlus One is still a great value thanks to the dedicated community that continues to develop ROMs for it. Cyanogen 12 and Oxygen OS are the two most popular ones, but neither offers th ...more
I'm an Android fan through and through, but occasionally, I see a feature or two on iOS that makes me a bit jealous. This was the case when I first discovered the useful functionality that lets you scroll to the top of a page by simply tapping the status bar on an iPhone. But ...more
Make no bones about it—Google is an advertisement company first and foremost. Nearly everything they do is geared towards targeting the right people with the right ads. In this vein, they've released an app that will actually give you real money to spend in the Google Play St ...more
Samsung is known for its added features, but occasionally, these can cross the line between functionality and bloat. For many users, this is the case with the "S Finder" and "Quick connect" buttons that are hard-coded into the notification tray on most Galaxy S6 and S6 Edge va ...more
With our internet-connected devices growing in number by the year, it would be nice if they could somehow all be interconnected. This is becoming commonplace for our tablets, smartphones, and laptops, but our media streaming boxes still seem to be isolated in their own little ...more
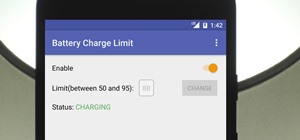
Ever feel like you're receiving notifications way too late on your Android device? Many Android apps use Google's Cloud Messaging service to send and receive notifications, including Hangouts, Gmail, Pushbullet, Facebook, and even WhatsApp to an extent. To ensure that your ph ...more
Believe it or not, there was a time when smartphones weren't the primary tool for taking photos. People actually walked around with bulky film-based cameras on their necks, and some even used cheap disposables. While photography wasn't introduced to the world when smartphones ...more
After several weeks of testing out the public beta, Apple has finally released iOS 8.3 to the general public. The latest iteration of iOS for iPad, iPhone, and iPod touch serves mostly as an update to fix many of the bugs that plagued earlier versions, but there are still a co ...more
Reddit is one of the internet's greatest sources of funny and interesting videos. Its user base is extremely active, and a system of upvotes and downvotes ensures that the best content always rises to the top. With Android TV's casting abilities, you might think that the best ...more
Instagram recently rolled out their new Layout app that helps users build photo collages more easily, and it's quick and easy to use with great results. Unfortunately, only those with an iOS device can enjoy Layout at the moment, with the Android version slated for release "in ...more
As an Android user, there aren't many elements of my friend's iPhone that I find myself envious of, because anything he can do on iOS, I can surely find a way to do on Android...often better. That being said, I have to admit that one feature I do like is the minimal style and ...more
With floating song lyrics displayed over the screen, apps like musiXmatch and Floating Lyrics are perfect for people who want to go beyond just the tunes and delve into a song's message and meaning. And while these floating windows can be convenient, they're not always necessa ...more
The bulk of my mobile gaming is done in instances of boredom, like sitting in a waiting room or watching bad TV. So when I heard about a new trivia game that pits every user against each other just once a day, I was immediately intrigued; it's a new spin on a very popular plat ...more
If Detective Alonzo Harris from Training Day taught me anything, it's that "It's not what you know, it's what you can prove." So when items mysteriously go missing from my room or my section of the fridge, it's up to me to figure out and prove which roommate took them. I don' ...more
Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resourc ...more
Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method. Note: This method only works if the website has the vulner ...more
In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new us ...more
You wouldn't send your GPS coordinates to a completely random stranger just because he or she asked you for it, right? So why are you constantly sharing your location (and other data) to apps on a daily basis? While there are many apps that need your location in order to func ...more
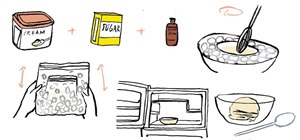
We're a little butter-obsessed here, and that includes topics on why butter should always be browned, the rationale behind clarifying butter, and even how to make a DIY butter candle. And while some may consider the problem strictly one for the first world, we're always very i ...more
Most diehard Mac users have used TinkerTool at some time or another, and if you haven't, it's time to start. Whether it's to change your system's font or to disable UI animations, it seems like anything you could ever think about tweaking in Mac OS X is doable through TinkerTo ...more
The "Smart Keyboard" on the LG G3 has received a lot of praise for its ability to adequately analyze user keystrokes, provide adjustable sizes, and customize key placements, among other things. These features, combined with predictive text, swipe gestures, and autocorrect make ...more
It's a shame that one of the world's tastiest foods can be such a pain to prep. Most cooks are familiar with this conundrum: chopping or crushing garlic releases a pungent liquid that causes bits of garlic to stick your knife and hands, creating a messy affair. So what is goin ...more
Apple has a built-in way to protect you from opening up potentially malicious apps on your computer in Mac OS X Lion, Mountain Lion, Mavericks, Yosemite, El Capitan, and macOS Sierra. This setting, named Gatekeeper, will never stop you from installing apps from the Mac App Sto ...more
Unless you're waiting in line for your iPhone 6 or iPhone 6 Plus, it's a sure bet that you'll be sitting by at home for your new device to get delivered today. Preorders were record breaking for this year's iPhones, but there's a good chance you won't be getting yours deliver ...more