WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling. First, U.S. Senator Joe Lieberman swayed Amazon's decision to stop hosting WikiLeaks. Then, Tableau Software removed graphs from th ...more
In this episode of Full Disclosure we are explaining the website attack known as Cross-Site Scripting (XSS). Cross-Site Scripting is a type of security vulnerability that affects web applications that do not sanitize user input properly. This kind of vulnerability allows an "a ...more
This Null Byte is a doozey. On Sunday, September 19th, an exploit for the latest Mac OS X 10.7 "Lion" was discovered by Patrick Dunstan. This exploit allows for an attacker, even remotely, to request to have the root user's password changed without knowing the password to the ...more
We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no ne ...more
We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no ne ...more
See how to make and receive video calls over a WiFi network when using an Apple iPhone 4G. Whether you're the proud owner of an Apple iPhone 4G or perhaps just considering picking one up, you're sure to benefit from this free video tutorial. For more information, including a d ...more
In this Computers & Programming video tutorial you will learn how to change the default Windows Remote Desktop port. It is actually a registry hack. You can check the IP address of our machine by typing ipconfig into the cmd prompt. For hacking into a machine, you should have ...more
The tutorial focuses on using Cheat Engine 5.5 to cheat (or hack) Epic Battle Fantasy 2, an online RPG game. The user will need to choose the "Epic Mode" under difficulty setting. The tutorial maker's mouse also shows where the user is clicking for the menu to come up. This tu ...more
This video teaches how to change/hack administrators Account/Password. Click START and find CMD. Type "net user" without the "". Now type "net user administrator" without the "". Scroll up the screen and find the administrator's name. Now go back down and type "net user admini ...more
When the New York Times paywall first went up, there was a whole lot of balking. The idea seemed egregious to most, and the digerati's overwhelming conclusion was that the system would fail. But interestingly enough, there is speculation that the NYT is actually experiencing a ...more
It's remarkable that a gaming device (from Microsoft, no less) designed for geeky gamers has incited broad innovation in medicine and robotics. But that Kinect has captured the imagination of hackers-with-MBAs-in-mind is downright amazing. Below, six videos demonstrating a va ...more
Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords. Visit us at bleedingedgesecurit ...more
In this video tutorial, viewers learn how to secure a home wireless network. There are 3 types of security protocols for connecting devices. The 3 types of security protocols are: OPEN, WEP and WPA. Users should use passwords that are secure but no so obscure that they are unu ...more
We're officially seeking Null Byters on a weekly basis who would enjoy taking their time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job ...more
Null Byte is looking for forum moderators! Last Friday's mission was to accomplish solving HackThisSite, basic mission 9. This mission delves a little further into Unix commands and remote directory traversal (which is just a fancy term for going through folders blindly). Th ...more
Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educate ...more
To the displeasure of many loyal Firefox users, Mozilla has been deploying what seems like a new marketing strategy to "catch up" to Google Chrome. I have no idea if this is because the version number is higher than theirs, but it is downright annoying. It's not all complaints ...more
Welcome to the second Goonight Byte! Our second coding session was kindly hosted by th3m, so props to him for letting this happen. Our task this time was to hack the bot that we made the week prior, which was only capable of connecting to the channel and then printing message ...more
It seems the French have carefully observed the hacking achievements of one super clever Carnegie Mellon grad, turning his hack into a modern iPad application-to-be. A couple years back, we told you about the fantastic Johnnie Chung Lee who used headtracking to create a three ...more
This past Sunday, a group called Gnosis launched a massive hacker attack on Gawker media, one of the web's most popular blog networks (Lifehacker, Gizmodo, Jezebel, io9, Jalopnik, Kotaku, Deadspin and Fleshbot). 1.3 million registered users' passwords were compromised, and 188 ...more
Clever little cinematography hack. Flickr user rtadlock mods an old kitchen timer into a panning timelapse motor controller. Explanation video below. Not bad for just $6.50! (Another video on Flickr made with the set up and GoPro camera).
Get a Mac Tip for your Mac computer! There's a million things you can do with your Apple computer, and this is just one of them. Watch this video tutorial to learn how to revert Safari 4 to the old tabs interface on a Mac computer. This technique allows a Mac user to use a ter ...more
Change the mood of any user on Facebook who has the Moods application installed... all you need is their user id and a few tools.
If there ever was a time for Null Byte to need people to contribute, it's now. Let's make Null Byte a place where anyone, from novice to master computer user, come and learn. It has been sometime since the last "Call to Arms" for Null Byte, and even longer since the last "Week ...more
Eventually, we plan on doing some root the box competitions here at Null Byte, but we're still looking for a server to play on. Anyone want to donate one? You won't regret it. Root the box is like 'king of the hill', except you have to hack a server and maintain access. Each s ...more
We'd like this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with (anyone want to donate one?), we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a ser ...more
We're aiming for this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with, we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain acces ...more
The community tore up the first realistic mission last week. You've applied the techniques learned in the basic missions to a real scenario, so I'm pretty content. The realistic missions are where the learning gets intense and where we can apply real knowledge to extremely rea ...more
Community byters, it's time to get serious. We are finally moving on to the realistic missions in HackThisSite. This is where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding ...more
We're officially seeking Null Byters interested in teaching others! Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowle ...more
9GAG's infographic teaches us all sorts of conveniences and short cuts to daily life, urawaza style. Some aren't complete revelations (the first hanger trick below), but others are pretty cool (if they work!). A few I wouldn't mind trying: free wifi at the airport ice cold dr ...more
Click the more info tab to see the instruction on how to get a bear on Mybrute.com. This is a tutorial on how to get a Bear on Mybrute.com, An Online RPG Game, It's a very popular game that a lot of people plays everyday, You don't need to do much action with your hands just s ...more
Learn how to build an environmentally friendly directional WiFi antenna with this simple video guide. To follow along at home, you'll need the following things: a copper wedge, an N-type connector, some screws, a clamp-on N plug, a pigtail, and a wireless card. You'll also nee ...more
The iPhone and iPod touch are nearly identical devices, especially now that Apple has added a front-facing camera to the iPod touch. All that's missing is the phone part. With the help of Lifehacker and apps like Skype and Line2, you can save some money by turning your iPod To ...more
Unlock your Galaxy's hidden potential by rooting it! Rooting your phone will enable you to do fun, against-the-rules things like running custom ROMs. Want to turn your Galaxy into a wireless hotspot with free WiFi tethering? You can do that too. Don't know how to root an Andr ...more
Unlock your HTC Tattoo's hidden potential by rooting it! Rooting your phone will enable you to do a great number of fun, against-the-rules things: Interested in running a custom ROM? It's easy. Want to turn your Milestone into a wireless hotspot with free WiFi tethering? Go ah ...more
Unlock your Motorola Milestone Google Android's hidden potential by rooting it! Rooting your phone will enable you to do fun, against-the-rules things. Interested in running a custom ROM? It's easy. Want to turn your Milestone into a wireless hotspot with free WiFi tethering? ...more
Though only just released, the official Skype client for Android has already been unlocked. Thanks to xeudoxus of DroidForums.net, American Android users may now do what their European counterparts have been able to do all along: make free Skype-to-Skype voice calls over 3G. ...more
Check out this amazing use of AR via Wired http://theleakinyourhometown.wordpress.com/ “the leak in your home town” is an iPhone app that lets users see the BP Deepwater Horizon oil spill whenever they see a BP logo. A user simply launches the app and aims their iPhone’s cam ...more
YouTube user Hacker of None teaches you how to hack Mushroom Madness using Cheat Engine. Start the game from Kongregate website and then run Cheat Engine. Search for your browser, which may be Firefox, Chrome or Internet Explorer, in the Process List and then click Open. Chang ...more
Do you own a hacked XBox 360? Do you want to burn some games for it? Well, in this video, the viewers will first be taught how to download games using peer-to-peer software, such as uTorrent. Then, with a combination of software, such as IMGBurn and abgx360, the viewers will l ...more
"Skimboarding in a Storm" displays some ultra cool camerawork, employing the relatively cheap and user friendly GoPro camera (also used in the clever Kitchen Timer Panning Time Lapse Hack). Says Gizmodo, "The idea is pretty simple: attach the rugged, waterproof Go Pro camera ...more
The big perk that comes along with purchasing a Nintendo DSi instead of a regular Nintendo DS is the Internet capability. With Nintendo's new DSi model you can go online and surf the web as well play other users over an Internet connection just like you would on an XBox or Nin ...more
This is a small tip for Farmtown users on Facebook on how to add trees and or flowers to the middle of your circle ponds. Have fun with it! Farm Town hacks, cheats, glitches. How to hack Farm Town. Description of the app on Facebook: In the world of Farm Town you and your fr ...more
Check out this hacking video tutorial to learn how to hack a cell phone with a magnet. You can easily hack Verizon's Motorola RAZR mobile phone to bypass the user password. Turn off the MOTORAZR phone and then turn it back on. After the red Verizon introduction screen comes o ...more
Null Byte is looking for forum moderators! Welcome to the ninth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone ...more
JavaScript is one of the main programming languages that the Web is built on. It talks directly to your browser and exchanges information with it in ways that HTML simply cannot. With JavaScript, you are able to access browser cookies, website preferences, real-time actions, s ...more
Anybody who spends most of their day on the internet should know all about lulz. Lulz are most often jokes made at the expense of web users, as popularized on 4Chan. Today, a consortium of hackers called LulzSec is attempting (and in some cases succeeding) in efforts to shut d ...more
This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last fo ...more
In this video tutorial, viewers learn how to create a Pandora battery for the fat PSP. A Pandora battery allows the user the process of using exploits and hacks to execute unsigned code on the PSP. Before beginning, users are advised to completely drain the battery. Begin by t ...more
Internet culture loves many things, but there are two web crazes in particular that always grab my attention: the notoriously addictive facebook game, Farmville, and the insane art of cake decorating. We've posted quite a few amazing cakes in the past - the ultra realistic ba ...more
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to get free ...more
Hacker Defender is one of the most widely deployed rootkits in the world. It is a user-mode rootkit that modifies several Windows and Native API functions, which allows it to hide information (files, processes, etc.) from other applications. In addition, Hacker Defender implem ...more
Last Friday's mission was to accomplish solving HackThisSite, realistic 4. The fourth in a series of realistic simulation missions was designed to be exactly like a situation you may encounter in the real world. This time, we are told "Fischer's Animal Products is a company th ...more
Do you need proxy access, but cannot have it for some reason? The most common perpetrator behind the issue is the network you're trying to access the pages from. Some networks will block websites, then go as far as filtering out all of the web queries for terms like "proxy" be ...more
Here's another Null Byte on hacking our Skyrim game saves. Some of the rarer items in Skyrim are really fun to play with. However, seeing as they are rare, you will probably not see all of the best weapons in the game. Null Byte doesn't take too kindly to games that don't give ...more
As many of you may have noticed, nearly every Google product (i.e. Gmail, Google search, etc.) has gone through a bit of a makeover since the release of Google+. Big blocky buttons and enormous font sizes are apparently the thing of the future, and with a cool JavaScript hack, ...more
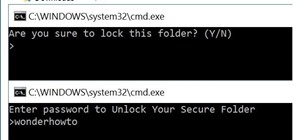
Security awareness seems to be a hot topic these days on the web, with developers making apps and devices that can hack networks and machines with just a few clicks. But these applications aren't only exploiting security flaws in systems and networks, they're being used by ama ...more
Attention all iPhone users. Engadget posts a helpful tip on possibly avoiding that painfully long iPhone 4 upgrade wait: "Apple and AT&T have worked to give folks a little leniency, with existing AT&T users able to upgrade to the iPhone 4 'up to six months early.' In other w ...more
In this video from rscp1050 we learn how to SSH into a jailbroken ipod touch or iphone. First go into Cydia and search for SSH. You need to download OpenSSH. Then also install Toggle SSH. After installed, restart the iphone. Now on your computer, download WinSCP. Once installe ...more