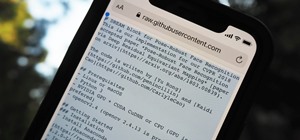
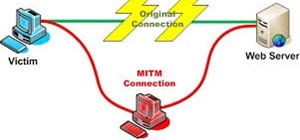
Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on. Those are just the big ones that get reported in the news. Millions ...more
It's been a while, since I have just started High School. I have put a hiatus to my pentesting for a few weeks, and now, I am making a return. I have taken time to read about code, (even did a research article analysis on how humans can write "beautiful" code and something li ...more
A vulnerability in the design of LiDAR components in driverless cars is far worse than anything we've seen yet outside of the CAN bus sphere — with a potentially deadly consequence if exploited. The hack is also going to be hard to fix, researchers Hocheol Shin, Dohyun Kim, Y ...more
Airports are terrible germ-infested purgatories where people sit around for hours without Wi-Fi while they anxiously await to get wherever they really want to go. Unfortunately, there isn't much we can do about waiting, but this little Wi-Fi hack could help make the waiting a ...more
Welcome back my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on us all, all the time. Basically, the PRISM program simply look ...more
You can make Siri do all kinds of things it was never designed to do. From installing it on older jailbroken iDevices to using it to bypass an iPhone's lock screen, people have managed to come up with some interesting hacks—and that's only the beginning. Raspberry Pi Forums m ...more
Privacy and security go hand in hand, especially for smartphones. When it comes to privacy, you decide what personal information about yourself is out there to discover. Security, on the other hand, is all about enforcing those privacy decisions. Sometimes privacy and securit ...more
Since most devices these days are mobile and wireless, a lot of people have a bunch of old hardware from a decade or two ago sitting around unused, just wasting away in dusty boxes. Look familiar? If you have an old mouse (or several) lying around, you can turn it into a wire ...more
While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one ...more
Black Mirror, Netflix's technology-horror anthology, never fails to provide thought-provoking entertainment centered around emerging and futuristic technologies, and the third season's second episode, "Playtest," delves deep into the worlds of mixed, augmented, and virtual rea ...more
T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the ...more
Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app. In addition, this hack worked 86% of the ...more
Even though we all know it's a bad idea, a lot of people still use their browser's store password function to keep up with all their accounts. While convenient, this shortcut also makes their passwords very easy to find if you have access to the computer they're stored on. He ...more
Rumor has it that a gang of hackers—or possibly, one lonesome individual—holds the power to remotely wipe millions of iPhones and iCloud accounts, unless Apple coughs up some ransom money by April 7. The gang calls themselves the "Turkish Crime Family," and they're demanding ...more
So, how does someone keep their hacking life completely secret? What This Is: I'd like to know how hackers keep their hacking life secret. So with a bit of experience and knowledge obtained from elsewhere I want to share what I know, and also ask a few questions to become ev ...more
Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc. Any time someone's computer seems to act ...more
The closest I've ever been to first class was when I was a young kid running up and down the aisles on a long international flight. I remember being in awe of how big the seats were and how much food was available. Ever since that moment, I've made it my life goal to earn enou ...more
Great ideas often strike at random times, but messaging friends and loved ones at an inopportune hour not only risks their wrath, but also increases the chances of your message not being paid proper attention to. Thankfully, there's an app that lets you create and post WhatsAp ...more
Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for s ...more
A trip to any grocery store's produce section will quickly reveal that bananas are often picked from the tree well before their prime—which is necessary for them to arrive at our local store without going bad. In fact, bananas are refrigerated en route to our supermarkets in o ...more
If you're one of the lucky people who received the gift of terrible eyesight from your parents at a young age, chances are you ate an awful lot of carrots growing up. Though carrots are one of the top vision-boosting foods, they don't offer fast results. Rather than risk turn ...more
Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client. Although the most valuable information to the hacker ...more
Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending ...more
A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fort ...more
An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manuf ...more
Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer. This part is more involved, but the first ...more
hello hackers,newbies and followers of this great community, after some research here in our community, I noticed that there is not even one tutorial that teach Web Development. We have a lot of tutorials on how to hack web site but many do not know exactly how a web site is c ...more
Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us. In this episode, Elliot is being blackmailed by the ru ...more
Just because a problem is small or superficial doesn't mean it can't annoy the living crap out of you. Others may think you're overreacting, or even have the audacity to roll their eyes, but you're in your own personal hell. First-world problems, white whines—call it whatever ...more
There's only one thing keeping hackers, thieves, law enforcement agencies, and maybe even the people you thought you could trust from breaking into your iPhone should they ever get possession of the device. Their odds of bypassing that thing are pretty good, but there's an eas ...more
In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greetin ...more
I'm constantly searching for a homemade pizza dough that tastes good but isn't too challenging to execute. In other words, a recipe that doesn't require any arcane "dough whispering" skills. However, my hunt may be coming to an end thanks to one celebrity chef's concept. Maki ...more
Prank Calls, Masked NumbersWho is calling your phone or your child's? Pranksters use a lot of tricks to make sure they can get on your nerves. Being able to trace prank calls is important because you're not going to learn much from your Caller ID, since most prank callers use ...more
It's that time of year again when pizza boxes line the room and buffalo wings stain the couch. When cases of beer sit in the cooler and the big screen TVs are fired up and properly calibrated. When two of the best football teams vie for the championship title and the Vince Lom ...more
With FarmVille being one of the hottest Facebook games on the market, it's no wonder it's the primary target for scams and virus downloads. Anyone playing FarmVille is at risk, but the primary targets are those looking to improve their gameplay and build their farms and neighb ...more
Firesheep is a packet sniffing browser exploit that can access the exposed accounts of people on Facebook and Twitter while they use public Wi-Fi connections. This video shows what steps can be taken to protect yourself against someone accessing your Facebook account. Links: ...more
iChat is gaining steam as a mainstream online chat program. Fortunately for you, you little prankster, it is exceptionally easy to change someone else's iChat away message to whatever hilarious thing you want from your computer! This video will show you exactly how to do it, w ...more
When you sign up with Gmail, Google gives you both an "@gmail.com" address and an "@googlemail.com" address. You can take advantage of this fact to reduce the amount of spam you receive. And this video tutorial from the people at CNET TV will show you how. Regain control of yo ...more
Social Profile Change the privacy settings on your social profile (Facebook, MySpace, Friendster, Twitter, etc.) so that the following information can't be found by a random person who you didn't accept you as a friend: Birthdate E-mail address Hometown Pictures A hacker ca ...more
In this Electronics video tutorial you will learn how to use Bluetooth connectivity to share cell phone files. You are not hacking in to other people's phones as you need their permission to access their phones. You can change ringtones and pictures or share them with your fri ...more
If you still own and use an original XBox console, good for you! You've got a little piece of history right there that most people just tossed or sold to a game store for $10. This video will show you how to replace the paltry 8gb hard drive that the console came with with a b ...more
Having trouble with people snatching your stuff? Did someone take your lunch from the company fridge? Here is an inexpensive, sneaky gizmo you can make to keep those sticky fingers away. This is a junk drawer hack from Make Magazine's Kipkay. It's activated when an item is mov ...more
So, a lot of people seem to be having trouble rooting their Motorola Droid X smartphone from Verizon Wireless using ADB (Android Debug Bridge). Well, there is an alternative for those having problems with the ADB version. You will need to have a Wi-Fi or Bluetooth widget handy ...more
They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam si ...more
This is a very lengthy explanation on BTD playing. There's a lot to actually know about the strategy of Bloons Tower Defense. This video tutorial will show you how to place towers in Bloons Tower Defense (10/08/09). Many people will tell you that you should place your towers ...more
This is a tutorial showing you how to easily hack flash (.swf) games! You only need two things: A flash game (in .swf format) and Flasm (an amazing flash disassembler). Getting Flasm Download Flasm Flasm can be downloaded from the no|wrap.de website. Save & Extract Save ...more
General Electric isn't known for their Christmas lights, but maybe they should be, because their GE Color Effects are pretty awesome. Especially the LED Color Effects G-35 String sets. And especially when someone named Darco hacks them. Darco, whose real name is Robert Sun Qu ...more
WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling. First, U.S. Senator Joe Lieberman swayed Amazon's decision to stop hosting WikiLeaks. Then, Tableau Software removed graphs from th ...more
Eventually, we plan on doing some root the box competitions here at Null Byte, but we're still looking for a server to play on. Anyone want to donate one? You won't regret it. Root the box is like 'king of the hill', except you have to hack a server and maintain access. Each s ...more
Welcome to another Community Byte announcement! For the past few Community Bytes, we coded an IRC bot, and hacked it. Then, we created a web-based login bruteforcer! This week we are going to start something a bit different. We are going to start going through the missions at ...more
Here's something fun for the Null Byte community to do—a coding competition! This week, I wanted to get everyone involved by offering you all a nice library of possible program types to choose from and try to code. At the end of this competition, all of the submitted programs ...more
Last Friday's mission was to accomplish solving HackThisSite, Realistic 5, the fifth and last in my series of realistic hacking simulation missions. This time, telemarketers are invading people's privacy, and it was up to us to stop them! The job was to get root on the site an ...more
Meet Newstweek, a hidden device engineered to hack news items being read at public WiFi hotspots (cafes, libraries, airports, etc.). Both nefarious and tech-saavy, the ingenious mechanism wasn't fathered by a group of web hackers, but rather a pair of Berlin artists, Julian Ol ...more
Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information y ...more
Ivy League schools aren't just places for people to row and sip their drinks out of glasses normal people would never use (i.e. snifters). They also the place for trolling on a grand scale. Just take a look at these Trolls de la Resistance! Yale's Trolling This little ditty ...more
Null Byte is looking for forum moderators! Last Friday's mission was to accomplish solving HackThisSite, basic mission 9. This mission delves a little further into Unix commands and remote directory traversal (which is just a fancy term for going through folders blindly). Th ...more
Welcome to another Community Byte announcement from Null Byte! The goal of the Community Bytes is to teach people in a co-operative, hands-on manner. Learning from experience and immersing yourself in a subject is the best way to learn something foreign to you, so that is exac ...more
With the rather large success of the Community Byte activities, both programming and HackThisSite, I have decided to continue to do both activities every session! With that said, when programming sessions occur, they will be lead by Sol Gates in Gobby. Also, the programming mi ...more
Welcome to another Community Byte announcement! In the past two sessions, we have coded an IRC bot in Python capable of issuing commands. Since it can issue commands and most of you are new to programming, that project will stay idle for a while. Other commands such as voice a ...more
Learn a harmless hack to access and control other peoples' webcams with a simple Google search. Access and control web cameras with Google. Click through to watch this video on tricklife.com