People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want ...more
Given that megastar internet search engine Google became its own verb a few years ago, we've all come to acknowledge that the wide and ever-expanding engine is becoming more powerful than ever before. You can take a look at your own house from outer space via Google Earth, you ...more
Go to Google, type in this code and you can watch unsecured webcams. Hack a webcam via Google. Click through to watch this video on tricklife.com
Consider this reason 1,001 why we love the internet: Using Google, you can hack into almost any webcam or security cam, in any part of the world and even control the webcam to move around so you can get your full panoramic shot. Don't believe us? Then check out this video tuto ...more
Okay, net sleuths — this one's for you. If you've ever wanted to spy on other people on their computers, this video will show you how to use Google to hack unprotected webcams. All you have to do is enter the following into Google's search bar: /view/index.shtml And a list o ...more
John Park from Make Magazine hacks a Nintendo Wii controller and turns it into a personal flight recorder that can sense and measure the stomach-churning G forces of roller coasters and other high-speed, high-risk activities. This Maker Workshop episode will expand your uses ...more
Welcome back, my hacker novitiates! Like in my last article on remotely installing a keylogger onto somebody's computer, this guide will continue to display the abilities of Metasploit's powerful Meterpreter by hacking into the victim's webcam. This will allow us to control t ...more
Have you ever been in a situation when you needed to remember something real important, but you didn't have you didn't have your trusty cell phone or other electronic savior with you? Enter the Remember Pen! Kipkay shows you another glorious and simple hack, and with this on ...more
Let's just say it's been a pretty bad year for spies and government agencies and an even worse one for the privacy of U.S. citizens. Edward Snowden blew the lid off the NSA's spy program, and the FBI was recently discovered to have the ability to access your webcam any time th ...more
One of the best uses for an old Android device is to turn it into a security webcam that can be accessed over the internet. But most of the time, this is a rather difficult process, because existing apps usually require you to mess around with network settings and configure a ...more
Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to se ...more
A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data. The ...more
Now that most computers have internal webcams in them, what are you going to do with that external webcam eating up precious desktop space? Kipkay shows you the perfect hack— the "Super SpyScope". The first thing you'll need to do is disassemble the webcam. Remove the main bo ...more
This video in the Fitness category will show you how to do barbell hack squats. The video is from Livestrong. Michelle Trapp, a Certified Personal Trainer at Gold’s Gym will demonstrate this routine. Keep the bar low enough so that you can safely un-rack it. Stand next to the ...more
How many of you have or know people who have a smartphone? There's a lot of you, right? Well, depending on how most of you use those smartphones, there could be all kind of sensitive information stored on it, and that doesn't just mean sensitive personal information, but it co ...more
MAKE and Kipkay brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will. In this video tutorial episode of Weekend Projects with Kipkay, you'll learn how to build an ani ...more
Today, learn the basics of lock bumping. Lock bumping is a lock picking technique for opening a pin tumbler lock using a specially-crafted bump key. One bump key will work for all locks of the same type. This video tutorial will show you how to hack into locks with lock bumpi ...more
Tinkernut demonstrates how to crack a wifi connection, as well as how to better secure your own personal connection. Also included in the video gallery is Tinkernut's previous tutorial on the same subject. LifeHacker posted a great detailed text guide to accompany the second ...more
This video tutorial belongs to the Electronics category which is going to show you how to make a hack pack. This is basically turning a notebook in to something that you can take literally anywhere. Here you will learn how to create a video streaming hack pack to carry around ...more
Movies like to show hackers breaking passwords with fancy software and ludicrous gadgets. The reality of busting passwords open is much more mundane. Simple as it may sound, most passwords are broken purely by guesswork. Check out this infographic from ZoneAlarm, as well as th ...more
Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords. Visit us at bleedingedgesecurit ...more
Hack your webcam into a magnifier by adjusting the focus lens Turn your webcam into a magnifier. Click through to watch this video on tricklife.com
Looking for a cheap addition to your KGB-esque arsenal of spyware? Here's a hack using a webcam and a telephoto lens to record some far out sights. Build a $40 USB spy telescope.
Want to find out if your neighbors are talking about you? You could always hack their webcam or turn your iPhone into a secret spy camera, but unless you have a key to their house, that could be tricky to do without getting caught. With this DIY parabolic microphone (archived ...more
As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives ...more
Welcome back, my tenderfoot hackers! So many of you responded positively to my post about using the keylogger, as well as my post regarding turning on the webcam, that I decided that you might enjoy another similar hack. In this article, we will enable the audio recording cap ...more
Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeO ...more
Windows XP will always have a special place in my heart—it's the operating system I grew up on. It guided me through the glory days of AIM, Napster, and MySpace, but now it's dead. The OS that had been supported by Microsoft for twelve years officially lost its support on Apri ...more
While hackers adore the command line, working with the GUI (graphical user interface) of an operating system has some advantages. This is especially true when it comes to post-exploitation. When we can control the mouse and keyboard of a remote computer, we can truly say we ha ...more
Many people deal with motion sickness on a daily basis, and if you're reading this, chances are you're one of them. Kinetosis can make your stomach roll, your entire body sweat, and make you feel fatigued and dizzy at even the slightest movement, whether it's related to carsic ...more
WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the commu ...more
A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists righ ...more
While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on ...more
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life. Imagine arriving home one night after work and there's a Post-it note on your apartment door with the website "your-name- ...more
Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side sy ...more
In the recent hit movie Furious 7, the storyline revolves around the acquisition of a hacking system known as "God's Eye" that is capable of finding and tracking anyone in real time. Both the U.S. spy agencies and an adversarial spy agency (it's not clear who the adversary is, ...more
When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was ...more
The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data. Apple introduced so ...more
Garlic is a key ingredient in many delicious meals, and if you've been a fan of our site for even a short while, it's no secret that we love to share tricks and tips to make cooking with garlic even easier than you first assumed. Here are just 10 of the many ways to both prep ...more
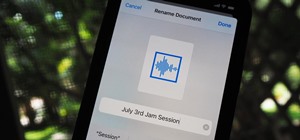
The sweet aroma of cooked fruit filling your kitchen is one of the trademark scents of summer. Yet attaining the perfect consistency for homemade jam can be difficult to master. Often it ends up a watery mess or over-solidifies into thick mystery goo that is destined for the t ...more
Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know ...more
Hello readers, and welcome to Null Byte. Before we start, for those of you who may not know me, my name is ghost_; I'm a relatively active member of our community and have been around for a while. During my time here, I've seen our community cultivate into the brilliant one ...more
A surefire way to delight this holiday season is with the latest tech. Gadgets today aren't cheap, but we've got you covered with some useful gear that's perfect for practically everyone — at a price that won't break the bank. If you need a last-minute present, check out the b ...more
Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, w ...more
You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and co ...more
Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat. Most Linux distributions are highly c ...more
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started. OVERVIEW: As you'll get further into the hacking community, and learn more about how it's all put together, you'll also realize very quick ...more
The new iPhone 5 was just revealed yesterday, and it's 18 percent thinner and just 1/5 the weight of its 4S predecessor. It's also taller with a larger screen, which gives you a fifth row for apps now. As far as speed is concerned, it has a speedy A6 chip and can tap into wire ...more
Learn how to hack Google with this amazing video. This video will teach you how to hack Google by using advanced search operators and esoteric search terms to find “hidden” files and mp3s quickly and easily; you'll also learn how to use Google to hack unprotected Internet-cont ...more
Identity theft is a huge problem and one of he fastest growing crimes in America. A number of credit card companies now issue credit cards with embedded RFIDs (radio frequency ID tags), with promises of enhanced security and speedy transactions. But, on today's episode of Bo ...more
WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling. First, U.S. Senator Joe Lieberman swayed Amazon's decision to stop hosting WikiLeaks. Then, Tableau Software removed graphs from th ...more
Social Profile Change the privacy settings on your social profile (Facebook, MySpace, Friendster, Twitter, etc.) so that the following information can't be found by a random person who you didn't accept you as a friend: Birthdate E-mail address Hometown Pictures A hacker ca ...more
According to Amazon.com, Kindle was their best-selling item this year, which means many, if not all of you are playing with a brand new Kindle on Christmas Day. Of all of Amazon's Kindle models, the Kindle 3 (6") will be the most common eReader in everyone's hands, either the ...more
Join the Pilot program and learn how to fly! But you're not going to be flying airplanes in this Pilot program, you'll be trying your hands at Google's first laptop computer. It's called the Cr-48, a black notebook wh ich runs an extraordinary operating system— Google Chrome. ...more
It's 1976. The hottest arcade game on the market is Blockade (or Blokade), an 8-bit maze game for 2 players. You and your opponent must move your characters around the screen in 90-degree angles, leaving a solid line behind them. Whoever runs into one of the solid lines first, ...more
This tutorial will let you hack into a wide selection of web cams and online security cameras. The hack is actually quite easy, and is best done with a browser like Mozilla Firefox. Navigate to Google in your browser, and then type in "inurl:viewerframe?mode+refresh". This pie ...more
Learn a harmless hack to access and control other peoples' webcams with a simple Google search. Access and control web cameras with Google. Click through to watch this video on tricklife.com
When the iPad 2 was released earlier this month, as to be expected there was a whole lotta buzz. And for good reason—while the the newest version shares the same price tag as the old, it boasts some significant new features. In case you missed it, here's a quick overview: Bet ...more
This is a really simple video guide on how to install Hackintosh OSx86 (Mac OS X) on a PC. OSx86 is a portmanteau of OS X and x86, a so-called collaborative hacking project to run Mac OS X computer operating system on a non-Apple brand personal computer, with x86 architecture ...more