This how to will show you how to program a fairly simple Hacking bat file. First open notepad. Then copy the text into notpad: REM ============================================================ REM errorcode401.blogspot.in @echo off title Rar Password Cracker mode con: cols=47 ...more
Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers). Flash ...more
Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By ex ...more
Many FarmVille farmers want money fast, or experience fast, or want to level up, or want to speed things up— make and earn things faster. No matter how long they play, they're not getting what they want, and that is to outshine everybody else. But you can't reach the top by si ...more
Yes, the Droid X from Motorola can be rooted, and yes, you can do it at home. Just make sure you follow the directions precisely. If you succeed, you'll have a completely rooted smartphone. eFuse doesn't matter. If you want to expand your options on Verizon Wireless's Droid X, ...more
So, a lot of people seem to be having trouble rooting their Motorola Droid X smartphone from Verizon Wireless using ADB (Android Debug Bridge). Well, there is an alternative for those having problems with the ADB version. You will need to have a Wi-Fi or Bluetooth widget handy ...more
Instructions: http://www.4shared.com/file/83381263/7178ff05/instructions.html Cheat Engine: http://rapidshare.com/files/185190575/CheatEngine54_By_DeX.rar Flash Player V9: http://rapidshare.com/files/182661767/Flash_Player_9_ByDexter.rar Safari: http://rapidshare.com/files/ ...more
This is a tutorial showing you how to easily hack flash (.swf) games! You only need two things: A flash game (in .swf format) and Flasm (an amazing flash disassembler). Getting Flasm Download Flasm Flasm can be downloaded from the no|wrap.de website. Save & Extract Save ...more
With FarmVille being one of the hottest Facebook games on the market, it's no wonder it's the primary target for scams and virus downloads. Anyone playing FarmVille is at risk, but the primary targets are those looking to improve their gameplay and build their farms and neighb ...more
Computer forensics expert Steve Burgess gives a highly informative tutorial on how to recover deleted emails in Outlook and Eudora. The most critical factor affecting the recoverability of deleted web-based emails, according to Steve, is whether the PST file, which stores all ...more
Thanks to Yifan Lu, it's been discovered that the operating system running on the Kindle Touch is written mostly in HTML5 and JavaScript, unlike the previous models which used Java. This is exciting, because when a device is hacked or rooted, that means homebrew programs can b ...more
Take a look at this instructional video and learn how to install the Twilight hack for you Wii. The twilight hack is an exploit that reads a elf file off the root of your secure digital (SD) card. To start up this hack, you'll need to load the Zelda: Twilight Princess game bef ...more
This Null Byte is a doozey. On Sunday, September 19th, an exploit for the latest Mac OS X 10.7 "Lion" was discovered by Patrick Dunstan. This exploit allows for an attacker, even remotely, to request to have the root user's password changed without knowing the password to the ...more
iPodTouchedMaster shows how one can easily SSH into their iPod Touch with all firmware! To SSH is the ability to hack into your iPod Touch's file system. First, your iPod Touch must be jailbroken. Next, you'll have to open Cydia. Click "Featured Packages" or search for the ter ...more
Don't be too disappointed if you don't have the spiffy new Kindle Touch, there is an up side. The benefit to owning the older (duller) models is that the firmware remains the same throughought generations, so the hacks retain their usefulness. This has given the modding commun ...more
It won't be much trouble getting a decent police sketch if Andrew Salomone decides to knock off a liquor store. Salomone used the Brother knitting machine hack shown below: "The balaclava is knit from cotton yarn and the design is from a bitmap file, in which pictures of my ...more
This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to rea ...more
Since the day of the Xbox 360 release, storage space for the device has been overpriced beyond belief. OEM 250GB HDD models still cost $110 USD! A 250GB hard drive should not destroy my wallet, Microsoft. Storage space, especially on HDDs, is cheap. You can buy a removable 2TB ...more
Gamers like myself who have switched back and forth between Skyrim on PC and Xbox lack the ability to share game saves. This really sucks. I love playing Skyrim on a console. It's a very comfortable, easy and relaxed gaming experience. You don't have to worry about your frame ...more
Welcome to the 10th Community Byte session for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers ...more
Want to control a friend's cell phone remotely and make "free" calls from it? In this hack how-to video, you'll learn how to hack Bluetooth-enabled cell phones with your Sony Ericsson or Nokia phone and the Super Bluetooth Hack—or "BT Info"—, a free program easily found throug ...more
In this video, we learn how to hack your iPhone 3G. To do this, you will need: iPhone 3G, Firmware 3.0 or 3.1 file, charger cable, and the Redsn0w program. First, connect your phone to the computer and then start up the Redsn0w program on your computer. Turn the phone off, the ...more
Though only just released, the official Skype client for Android has already been unlocked. Thanks to xeudoxus of DroidForums.net, American Android users may now do what their European counterparts have been able to do all along: make free Skype-to-Skype voice calls over 3G. ...more
Check out this cool hack from The Emo Lab. This video tutorial will show you how to do a few Windows registry hacks! Here is the file you'll need to start hacking the Windows registry. Before you download this file, read all of the "read me" files contained first in this down ...more
Warnings i cant be held responsible for any illegal act done by anyone but myself and there are copyrights so notise that taken the trademarks or copyrights are strigtly prohibeted by law and will be punshied by law and i or my partners cant be held responsible for sudo camma ...more
Do you want to use Apple iPhone's Video Recorder for free, without paying to release the filming length restriction? Well, check out his video tutorial to see how to hack the iPhone Video Recorder version 1.2.4 for non-stop movie recording. Make sure the iPhone Video Recorder ...more
To the displeasure of many loyal Firefox users, Mozilla has been deploying what seems like a new marketing strategy to "catch up" to Google Chrome. I have no idea if this is because the version number is higher than theirs, but it is downright annoying. It's not all complaints ...more
Since the early genesis of the brilliant Microsoft Kinect hack, inventive applications have been popping up nonstop. One of the most fascinating projects to surface recently falls within the realm of 3D printing. "Fabricate Yourself"—a hack presented at the Tangible, Embedded ...more
This video tutorial shows you how to jailbreak and unlock your iPhone 2G, iPhone 3G, and iPhone 3GS on firmware version 3.0.1 with Redsn0w and Ultrasn0w. Firmware 3.0.1 fixes the SMS hack/vulneravility Download Redsn0w v0.8: http://thebigboss.org/hostedfiles/red... Download ...more
Hey, hackers! Now that you've hacked/owned your first "box" in my last article, let's look a little closer at another great feature of Metasploit, the Meterpreter, and then let’s move on to hacking a Linux system and using the Meterpreter to control and own it. Why Meterprete ...more
Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying vario ...more
Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an imag ...more
Welcome back, my hacker apprentices! A you know, Mr. Robot is my favorite TV show this year, and not just for the realistic hacking. Rami Malek, the actor who plays Elliot, is incomparable in his depiction of a young man with social anxiety who is alienated from a superficial ...more
Welcome back, my aspiring hackers! As you have probably discovered by now, the file system in Linux is structured differently from Windows. There are no physical drives—just a logical file system tree with root at the top (yes, I know, roots should be at the bottom, but this ...more
Windows XP will always have a special place in my heart—it's the operating system I grew up on. It guided me through the glory days of AIM, Napster, and MySpace, but now it's dead. The OS that had been supported by Microsoft for twelve years officially lost its support on Apri ...more
The Xposed Framework offers many great customization options for your Galaxy S5. S Health, with its ability to read your heart rate through a built-in monitor, is one of the main selling points of the GS5. Trouble is, the two don't seem to play nice together. Many users (myse ...more
hello hackers,newbies and followers of this great community, after some research here in our community, I noticed that there is not even one tutorial that teach Web Development. We have a lot of tutorials on how to hack web site but many do not know exactly how a web site is c ...more
It used to be easy to hack tethering—root your device and install a third-party or modded tethering app. But snuck in amongst the changes in Android 4.3, a new data-monitoring service of sorts made its debut. There used to be a time when your data connection was yours. You pai ...more
Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, ...more
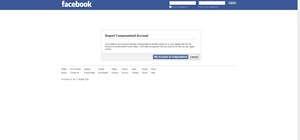
Facebook is a black hole. The constant stream of baby photos, #hashtags, BuzzFeed quiz results, and unintelligible status updates is mind-numbing. I know too much about too many people I hardly know. Posts like this turn my soul into dark matter.. No matter what web browser yo ...more
Privacy and security go hand in hand, especially for smartphones. When it comes to privacy, you decide what personal information about yourself is out there to discover. Security, on the other hand, is all about enforcing those privacy decisions. Sometimes privacy and securit ...more
Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method. Note: This method only works if the website has the vulner ...more
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started. OVERVIEW: As you'll get further into the hacking community, and learn more about how it's all put together, you'll also realize very quick ...more
File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target. To demonstrate these vulnerabilities, we'll be practicing PHP file inclusion using the Damn Vulnerable Web App. We'll ...more
Transparent status bars and new lock screens weren't the only new additions that came with the Galaxy S3 KitKat update. Along with better battery life and a smoother user experience, we got a new toggles design and recent apps menu. Of course, Samsung's infinite wisdom left th ...more
It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or ...more
One of the best things about the Samsung Galaxy S3 is the ability to modify the device in countless ways, as with any other Android device. A recent guide on adding softkeys to the GS3 from mod Faisal inspired me to share some information on how to edit build.prop, which is y ...more
You can easily lock any folder on your Windows computer with a simple Notepad hack. By creating a batch file, you can hide a folder and require a password be entered before it becomes visible and accessible. This is a great tool for locking sensitive information, like pictures ...more
The Samsung Galaxy S III is undoubtedly a great phone, but still has some minor issues to work out. One involves buggy Wi-Fi roaming, where the Galaxy S3's Wi-Fi signal strength will increase when getting closer to a Wi-Fi access point, but then completely disappears when att ...more
Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype. What we are going to do today? 1 - get the IP from h ...more
Samsung bucked the trend and threw hard keys onto the Galaxy S3 while most manufacturers are going the soft key route. This hack will add on-screen buttons to your TouchWiz-based ROM. You'll need a root file manager with a system writable text editor—I recommend ES File Explor ...more
Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, ...more
In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greetin ...more
Hello my fellow hackers, it's been a while since my last post, I can't get the time now-a-days for the posts but can manage to tend to comments. Welcome to my 9th post, this tutorial will explain how to extract and decrypt WhatsApp database from the Victim's android system. ...more
The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data. Apple introduced so ...more
Welcome back, my neophyte hackers! Several of you have written me asking how to crack passwords. The answer, in part, depends upon whether you have physical access to the computer, what operating system you are running, and how strong the passwords are. In this first install ...more
This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the ser ...more
Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use ...more
In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the ...more
Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next ti ...more