On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated ...more
In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hea ...more
What if you could have a secret hard drive connected to your computer that only you could activate? You can! Samimy shows you how to hack a remote controlled toy car and make a super secret hard disk drive in your computer, accessed via a secret activation key. This hidden eme ...more
Hardware hacks are something I feel we don't get enough of at Null Byte, so today I figured I would introduce a fun one. I've always been a curious hardware hacker. Taking things apart and learning how their internals work has always been a part of my nature. Quite some years ...more
Normally, when standing outside your local regional airport, you'd need a special radio or scanner to pick up the transmissions coming from that Air Traffic Control tower. Well, not anymore. Kip Kay from Make Magazine will show you how to take an old vintage AM/FM transistor ...more
In this clip, you'll learn how to create a WiFi radio with an Asus WL-520GU and a WL-520GU-ASUS wireless router. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch t ...more
An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manuf ...more
The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, ...more
Flight disruptions can cost billions of dollars, but most modern commercial flights rely on air traffic control systems that harbor serious vulnerabilities. The Federal Aviation Administration uses an infrastructure called NextGen, which relies on Automatic Dependent Surveilla ...more
It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement. Whether you are a journalist, a protestor, or a hi ...more
Want to boost your WiFi reception? Have an extra wok or parabolic collander? This video tutorial demonstrates a simple hack that will allow you to build an effective radio antenna that will significantly increase the gain of your WiFi signal. To replicate this hack at home, yo ...more
Watch this amazing USB Bluetooth adapter hack from Kipkay. It's easy and effective, plus it will work with other wireless devices, too. Bluetooth works on a 2.4GHz short wavelength radio frequency, but it's only effective over short distances. Well, Kipkay's going to show you ...more
This video demonstrates a very simple way to broadcast your voice on the same frequencies that a drive-thru restaurant uses, enabling you to mess with the customers and employees. This hack will work on just about any fast food drive thru. If you like the drive-thru pranks on ...more
Are you tired of keeping all the music on your mp3 player to yourself? Share it with the world by hooking your mp3 player up to a radio and using the speakers for output. This simple radio hack of connecting a capacitor to the potensiometer will bring you endless hours of musi ...more
In this video tutorial, learn how to open & take the back off the iPhone 2G. This shows how to crack open the iPhone 2G case, specifically to hardware flash the radio by shorting the test point. This was considered the first hack freeing the iPhone 2G from its simlock. Warnin ...more
It won't be much trouble getting a decent police sketch if Andrew Salomone decides to knock off a liquor store. Salomone used the Brother knitting machine hack shown below: "The balaclava is knit from cotton yarn and the design is from a bitmap file, in which pictures of my ...more
Got a knack for speeding? Like running red lights? Believe or not, the police have better things to be doing than pulling you over, like catching real criminals. That's why more and more cameras are popping up at known speeding zones and on street corners—so the cops can clean ...more
Turn a 'toy' radar gun into the real thing! Cops don't even have one like this! While this is a completely new and different design, the inspiration for this video is from an article by Ken Delahoussaye in MAKE Magazine. Just watch this video tutorial on how to hack a toy rada ...more
Superman is one of the greatest and most known superheroes out there. Developed by DC Comics, Superman has seen the world… as in comics, television, newspaper strips, video games, movies, radio serials, etc. See how to make a Superman costume in this video from GiannyL. This ...more
Want to build your own DIY solar panels on the cheap? This video demonstrates how to make solar panels to power devices. The video explains how a solar panel works and how to connect it to a radio in order to power it. For more on this hack, including step-by-step instructions ...more
Step 1. Have the victims of the prank just engaging in a normal everyday activity such as going out to eat at a restraunt or whatever. Step 2. Stage a police situation in view of the prank victim but dont make it a spectacle. (traffic stop) whatever Step 3. When you arrive t ...more
You can use Twitter to print Instagram photos, track news and weather events, or even remotely shut down your computer, and if you're familiar with IFTTT, there's no shortage of ways your account can help automate your life. Or, if you just want to build something cool (pract ...more
Our good friend Kipkay is at it again! He has earned six figures from videos like HowTo Unlock Handcuffs and HowTo Make a Stink Pen Here he teams up with Howcast to deliver the ultimate treasure hunter's secret weapon: a metal detector. This homebrew hack combines the AM freq ...more
Admittedly, we've been quite hot on Kipkay lately, but can you blame us? This guy just keeps rolling out the wild inventions and bold pranks! A motion triggered spy cam is high level 007 stuff. Here's the scenario. You suspect your new roommate is eating your food, but you n ...more
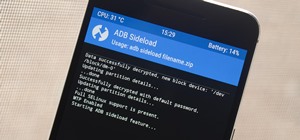
Malevolent hackers can divert your incoming calls and texts to any number they want, and they don't need to be a criminal mastermind to do it. Even friends and family members can reroute your incoming calls and messages so that they know exactly who's trying to reach you, and ...more
Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is ...more
Everyone from first responders to hotel cleaning staff use radios operating in the sub-megahertz range to communicate, often without even encoding the transmission. While encoding and encryption are increasingly used in radio communication, an RTL-SDR adapter and smartphone ar ...more
Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc. You can also use this technique to hack/spoof messengers like Facebook or WhatsApp etc. Step 1: Fire-Up Kali: I hope you know how to hack android and gain access t ...more
Samsung's exclusive music streaming service, Milk Music, has been making waves across the web thanks to its peculiar name and ad-free stations. Only problem is, not everyone has a Samsung device. If you want to get in on the action, we've got a way to get Milk Radio on your r ...more
Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa d ...more
The biggest pet peeve of many Google Now users has always been the fact that you can't toggle basic system functions with voice commands. In fact, this was such an annoyance that folks even went so far as to apply root mods to get the functionality. Well, we're happy to repor ...more
Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I ...more
Most new stereos come with an auxiliary port built in, but if you drive an older car, you're usually stuck with the radio or CD player, and we all know both of those options suck. So, rather than paying the $95 fee the dealership wanted to charge, or replacing the stereo alto ...more
Pokémon GO, the global augmented reality game that's brought fans out of their homes to catch Pokémon across the planet, has brought about plenty of real-world positives. Unfortunately, when players get power hungry and start taking game hacks too far, we all get a little scre ...more
Back in March, Samsung partnered with Slacker Radio to create a streaming service called Milk Music. For those of us who don't own a Galaxy device, this news was a non-starter, as it was exclusive to Samsung's flagship line of phones and tablets. Since then, mods have made Mi ...more
Cell phone jammers, a DIY endeavor for the darker crowd. I'm pretty sure we've all considered having one at some point: whether the obnoxiously loud woman next to you is announcing private bedroom stories to a crowd on the subway, or your kids are grounded from using the phone ...more
The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centere ...more
A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts f ...more
Prank Calls, Masked NumbersWho is calling your phone or your child's? Pranksters use a lot of tricks to make sure they can get on your nerves. Being able to trace prank calls is important because you're not going to learn much from your Caller ID, since most prank callers use ...more
Whether it's the new iPad Killer or not, one thing's for sure—the Motorola XOOM is hackable. Just hours after its release last week, Verizon's new Android-based tablet (running Honeycomb) was rooted by hacker Koushik Dutta, which seems easy enough. "Since it’s another Google ...more
Identity theft is a huge problem and one of he fastest growing crimes in America. A number of credit card companies now issue credit cards with embedded RFIDs (radio frequency ID tags), with promises of enhanced security and speedy transactions. But, on today's episode of Bo ...more
If you want to enter the police station armory in Detroit while playing Deus Ex: Human Revolution, you either need to have enough credits to afford it, or you need a high hacking skill. This video from Game Front will allow you to skip both of those requirements by giving you ...more
General Electric isn't known for their Christmas lights, but maybe they should be, because their GE Color Effects are pretty awesome. Especially the LED Color Effects G-35 String sets. And especially when someone named Darco hacks them. Darco, whose real name is Robert Sun Qu ...more
Android smartphones have all sorts of connectivity chips built in, including Bluetooth, Wi-Fi, GPS, NFC, and mobile data. But what about AM or FM radio, two of the most common methods of wireless communication? The truth is, it really depends on your device. Some phones come ...more
By now, many of you may have heard about iPhone tracking and recording your location data, but is there anything else being extracted from cell phones without our knowledge? If you're a Michigan state resident, the answer is an alarming "maybe". Michigan's police department h ...more
In a riveting interview on TruNews Radio, Wednesday, private investigator Doug Hagmann said high-level, reliable sources told him the U.S. Department of Homeland Security (DHS) is preparing for “massive civil war” in America. “We have problems . . . The federal government is ...more
Anonymous hacktivists announced via Twitter that they had successfully hacked the website of New York Iron Works, a police-equipment supplier, and replaced the homepage with a tribute of love to arrested hacker and Chicagoan Jeremy Hammond. Image by PictureDJ
Collapse At Hand Ever since the beginning of the financial crisis and quantitative easing, the question has been before us: How can the Federal Reserve maintain zero interest rates for banks and negative real interest rates for savers and bond holders when the US government i ...more
“Bad Burrito” Summary: this is basically a prank within a prank. The person (who does not know it’s a prank within a prank) will go to a Mexican restaurant (or any place that serves spicy burritos). It must have an out door seating area, like a sidewalk. He sits down and star ...more
MAKE and Collin Cunningham brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will. In this Make Presents video tutorial, you'll see how to create your own diode, along ...more
Check out this tutorial and hide your goodies inside a seemingly ordinary house candle. The candle will still burn once you've hacked it, but be careful not to burn it all the way down! You don't want your stash to be revealed! So, the next time you have something you need to ...more
The biggest struggle with flashing DVD drives on Xbox 360s has been the price tag of the probe to extract keys on some drives. The probe and kit is required to extract the DVD key, which is needed to perform a drive repair, flash, or backup of any kind. Who wants to pay big bu ...more
Every day of the week, WonderHowTo curators are hard at work, scouring the web for the greatest and most inspiring how-to videos. Every Friday, we'll highlight our favorite finds. Make your own police taser Remember that great scene in the movie The Hangover with the police ...more
Remember the good ol' days when you actually had to swipe your credit or debit card to make a payment at the store? Now all it takes is a flick of the wrist to purchase goods with your card, thanks to RFID (radio-frequency identification) technology from Chase (blink), Visa (p ...more
Want all of the GTAIV cheats? This is a Grand Theft Auto hack like you'd never believe. Get the cheat codes for every glitch and cheat in the game. Full health and armor Dial "3625550100" on the cell phone. If you enter this code while in a vehicle, it will also repair it. No ...more
So, you scratched up your $500 Adobe CD and now it's unreadable. You could go buy a new one, but you already purchased it! Searching The Pirate Bay and downloading some Adobe software can usually be easy enough, but what should you watch out for? And what about your movies? W ...more
It's been a great year for video games, kind of. Sure, the AAA release lineup has been a trainwreck and hacking has been a bigger problem than ever. But two things have happened involving the federal government that have made video games more legitimate in the United States th ...more
Law enforcement can make a lot of folks cringe. Too often do we hear on the news, and even experience in our own lives, the unjust way that an unacceptable portion of law enforcement treat the very citizens they are supposed to protect. People's rights are violate each and eve ...more
In 1988, John Langley created COPS for the fledgling FOX network. 23 years later, the show is still running. It is the Energizer bunny of prime time television. Since John has followed more police officers and witnessed more crime than any human being on earth (absolutely no q ...more
Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use y ...more