Six months ago, 1.3 million registered users of Gawker Media had their passwords compromised when the site was hacked by Gnosis. The passwords were encrypted, but 188,279 of them were decoded and made publicly available for all to see. Just three weeks ago, Sony Pictures was h ...more
Having a secure password is essential in today's interconnected world. Hackers are just around the corner, and if you have an easy to guess or hack password that you use for all of your accounts, someone can login to all of your websites very easily. Look at this guide on how ...more
About two months ago, the massive Gawker Media hack was a wake up call for many web denizens on the importance of proper password security. Data analyzed by the Wall Street Journal revealed the three most popular passwords recovered from the hack were downright idiotic—123456, ...more
This video teaches how to change/hack administrators Account/Password. Click START and find CMD. Type "net user" without the "". Now type "net user administrator" without the "". Scroll up the screen and find the administrator's name. Now go back down and type "net user admini ...more
In this video tutorial, you'll find a step-by-step guide to how a n00b hacker (like you?) can get usernames and passwords easily through one of the security flaws of the Ethernet ADSL router. More than half of Internet users never change their default password which makes this ...more
Friday's Community Byte was weird. The intent was to do a HackThisSite mission, but upon time to begin, everyone in there was programming without my assistance, with the help of Sol Gates. This is great! It's really awesome that everyone enjoys programming that much and will m ...more
Various ways to password protect a file or folder using Microsoft Vista are shown in this video. The first step is to choose a file you want to add a password to. After you decide on the file you wish to protect you must right click and select add to archive using Win Rar. Aft ...more
World of Warcraft is a super fun game, but as anyone who's ruling the game at level 80 (the level cap at the moment) will tell you, getting to 80 is a long and sometimes tedious journey. So why drudge along fighting bosses and other supernatural phenomenon for eighty levels w ...more
Have you ever forgotten your password and didn't know how to get back on your computer? Or ever had an annoying roommate you wanted to play a trick on to teach them a lesson? Or perhaps overly religious parents who think the internet is of the devil and won't let you read onli ...more
Check out this hacking video tutorial to learn how to hack a cell phone with a magnet. You can easily hack Verizon's Motorola RAZR mobile phone to bypass the user password. Turn off the MOTORAZR phone and then turn it back on. After the red Verizon introduction screen comes o ...more
As the image above suggests, it takes expertise (and perhaps sleuth) to actually hack into somebody's facebook account. But to steal a friend's password? If you're lucky, a simple mind game will do the trick. Read and learn: Image credit.
JavaScript is one of the main programming languages that the Web is built on. It talks directly to your browser and exchanges information with it in ways that HTML simply cannot. With JavaScript, you are able to access browser cookies, website preferences, real-time actions, s ...more
Hello and welcome to another InfoSecurity World tutorial. The intent of this article is to teach one how to encrypt sensitive files. When set up correctly with a strong password, it would be almost impossible to hack. Even the FBI have had issues decrypting this software. I'm ...more
How to get pet society money cheat in a easy way. auto clicker: http://rapidshare.com/files/40560577/Autoclicker_V3.exe.html http://rapidshare.com/files/40560796/123.rar.html Working on 14 april 2009. How to hack Pet Society! Pet Society cheats, tricks, hacks. Pet Society ...more
If you have a group of large files that need to be sent to a client, you might want to compress it into one single file for easy access or even protect its content from outsiders with a password. This video will teach you how to create password-protected zip files with WinRAR. ...more
Movies like to show hackers breaking passwords with fancy software and ludicrous gadgets. The reality of busting passwords open is much more mundane. Simple as it may sound, most passwords are broken purely by guesswork. Check out this infographic from ZoneAlarm, as well as th ...more
If you're new to the Bluetooth hacking world, here's a little background on using Linux BackTrack to hack a Bluetooh device: Linux Backtrack is a Live DVD device that offers security tools - like password crackers - that allow you penetrate networks. Thus, you can penetrate e ...more
Nothing on the internet is ever truly private and this hack proves it! Learn how to use PhotoFucket to hack into Photobucket with this video. You'll be able to access Photobucket without a password and view private photos from users. Be careful what you leak though...you might ...more
Welcome to the 10th Community Byte session for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers ...more
If you're trying to hack someone's wifi, a useful bit of software you may want to try is called Wireshark. Wireshark is a wifi packet sniffer, which is an essential step in actually breaking into someone's wireless system. Of course, this is illegal, so make sure you're only d ...more
locker gnome teaches you how to unzip files online. The site you need to visit is WobZip. You can use a file from your own computer or one from the web. If the archive has a password, type that in the field. The formats supported are 7z, zip, gzip, bzip2, tar, rar, cab, ISO, a ...more
Have an old-school tabula recta lying around? No? Then just print out the chart below. Nothing ensures better password security than this centuries-old cipher technique. Here's how it works, via Wikipedia: "Using a tabula recta, each alphabet is shifted one letter to the left ...more
Archiving and compression is a great way to store and prepare files for sending. You can reduce the size of a file, turn a group of files into a single file, and even encrypt and password the contents! Just take a look at this image to see how much it compressed a 28GB text fi ...more
"Facebook is a social utility that connects people with friends and others who work, study and live around them. People use Facebook to keep up with friends, to share links, to share photos and videos of themselves and their friends, and to learn more about the people they mee ...more
In this clip, you'll learn how to use the Backtrack 3 Linux distro and Aircrack-ng WiFi security app to crack the password to a WEP-protected wireless network. The process is simple. For more information, including step-by-step instructions, and to get started testing the secu ...more
For Infinity Exists Full Disclosure's first Website Hacking episode, we demonstrate how to exploit a security vulnerability occurring in a website's database to extract password hashes. Sql (Structured Query Language) is a computer language designed for the retrieval and manag ...more
Cheers to another completed Community Byte project! Things went well regarding timeliness and being friendly to the other coders and students. If you've got ideas for our next mission, or an idea for a tutorial, submit them to me. Friday, our mission was to take out HackThisSi ...more
This video tutorial shows you how to jailbreak and unlock your iPhone 2G, iPhone 3G, and iPhone 3GS on firmware version 3.0.1 with Redsn0w and Ultrasn0w. Firmware 3.0.1 fixes the SMS hack/vulneravility Download Redsn0w v0.8: http://thebigboss.org/hostedfiles/red... Download ...more
This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to rea ...more
People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people ar ...more
The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user i ...more
Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next ti ...more
Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless ...more
If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a pro ...more
Even though we all know it's a bad idea, a lot of people still use their browser's store password function to keep up with all their accounts. While convenient, this shortcut also makes their passwords very easy to find if you have access to the computer they're stored on. He ...more
While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of i ...more
Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily act ...more
Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, ...more
Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending ...more
Step 1: Introduction: Hello! Hackers In this tutorial I will tell you how to hack windows 7 administrator password. However you already know (I think) Specifically, it is used in school, computer labs or other workplaces, where, administrator is locked with a password, while ...more
Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app. In addition, this hack worked 86% of the ...more
Everybody knows not to store sensitive information in unencrypted files, right? PDFs and ZIP files can often contain a treasure trove of information, such as network diagrams, IP addresses, and login credentials. Sometimes, even certain files that are encrypted aren't safe fro ...more
While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot ...more
Unless you have unlimited cellular data, you probably connect your iPhone to every Wi-Fi network you come across. It could be a local coffee shop, public library, or just a friend's place. Wherever it is, you'll need to ask for the access point's password if it's a secured net ...more
Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/W ...more
With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device. UserLAnd, created by UserLAnd Technologies, is a completely free Android app that makes installing ...more
People have asked: "Here is an IP address. Can you hack this? Can you hack me right now?" Hacking takes time and skill. You can't just get an IP or an email and hack it in ten minutes unless the password is 1234. I say, "No. I can't really do what you want me to do like this ...more
While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatic ...more
Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making cus ...more
I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords. Usually, the ...more
A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials. ...more
Steganography is the art of hiding information in plain sight, and in this tutorial, I'll show you how to use Steghide — a very simple command line tool to do just that. In addition, I'll go over a bit of conceptual background to help you understand what's going on behind the ...more
If you read my previous post, "How to Hack into a Mac Without the Password", you know that it is very easy to break into someone's Mac if you have physical access to the computer. Now the question that lies is, how do we protect ourselves from this happening to us? Well, here ...more
JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicio ...more
The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in r ...more
Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get ...more
It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the ...more
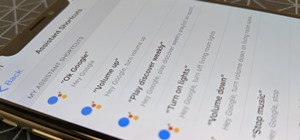
Finding the motivation to make a change can be tricky. It's difficult to resist the urge to procrastinate, or even give up when goals seem distant and difficult. If you wish you could stick to your New Year's resolutions, or maybe even just commit to pursuing smaller goals, yo ...more
Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacki ...more
Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can c ...more