Let's face it, finding your remote, let alone finding something to watch, can take more time out of our days than we'd care to admit. There are remote locators and channel guides out there, but why use those when you have a perfectly good remote always on you—your HTC One. HTC ...more
I love my status bar. Not only does it tell what time it is and how much battery juice is left, but it gives me cellular connection info, text alerts, and app update notifications. However, one thing is does not give me is customization. Since you're looking at it all the damn ...more
Samsung's exclusive music streaming service, Milk Music, has been making waves across the web thanks to its peculiar name and ad-free stations. Only problem is, not everyone has a Samsung device. If you want to get in on the action, we've got a way to get Milk Radio on your r ...more
Windows 8's interface was met with criticism when it was released, mainly directed at the tiled Start screen, a departure from Windows versions of old. Many felt that this new home screen style was better suited for mobile devices like Microsoft's Surface tablets and Windows P ...more
I have Verizon, America's largest 4G LTE network, as my cell service provider, but there are times when I find myself with a pretty shitty signal, rendering my upload and download speeds substantially slower than usual. One of those times are when I'm in my bedroom, and altho ...more
With a 5-inch screen, it's possible that the Samsung Galaxy S4 can be a bit large for our hands. While my grubby hands let me navigate the phone pretty easily, the same can't be said for everyone. A lot of us use two hands to type on the phone, play games, and perform tap or s ...more
Many of us were left scratching our heads when the iOS 7 update removed the Twitter and Facebook options from the Notification Center. Allowing you to quickly tweet and post Facebook updates, these were features used, and missed, by many—including me. Fortunately, if you have ...more
Rounded rectangle icons are so 2007. Sure iOS 7 tweaked them a bit, but with the clean new approach to design that software is taking today, they're starting to look dated. Today I'm going to show you how to go full circle with your iPhone's icons, and the results are actually ...more
Gmail is a free, advertising-supported email service provided by Google. Users may access Gmail as secure webmail, as well as via POP3 or IMAP4 protocols. Gmail initially started as an invitation-only beta release on April 1, 2004 and it became available to the general public ...more
I know it's a very first-world problem, but I really can't stand it. Email was invented to speed up communications between people across the world, even just across the office, yet when I'm on my super awesome iPhone running iOS 7, I have to go back and forth between my galler ...more
Welcome back, my aspiring hackers! In this series on Linux for aspiring hackers, I'm trying to provide you with the basic skills needed to be capable in Linux as a hacker. One area that's critical that we haven't covered yet is building and managing an Apache web server. Apac ...more
Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, ...more
There are many impressive features on a Samsung Galaxy Note 2, but just like any other smartphone on the market, the most used one is the camera. How many times did you take a picture today? Or admire all the selfies in your gallery? Or upload a video to Instagram, Vine, or Sn ...more
Next time you go to the beach, stash a bottle of baby powder in your beach tote—even if you're not planning on changing any diapers. Before you head back home, dust your hands and feet with baby powder to remove sand particles quickly and easily, so you don't track any into yo ...more
There are a ton of cool features available on your Samsung Galaxy Note 2, but if you're a softModder, you can make your phone do just about anything. Therein lies the problem…what do you want from your Android device? When you first start tinkering around, it can be troubles ...more
Traveling can be pretty expensive, but your meals don't have to be. Though hot dogs made in the cheap coffeemaker of your hotel room probably won't be the best dinner ever, you can bet that it'll be oodles cheaper than ordering room service or going to a fancy restaurant. If ...more
With the majority of smartphone carriers no longer offering unlimited data plans for the iPhone, monitoring how much mobile data you use is a key element to saving money on your phone bill. Android has been integrating data monitoring into its OS for quite a while now, and wi ...more
Ditching Sense (HTC's stock Android Launcher) is a great way to breathe new stock-like life into your HTC One smartphone without rooting, but even that has its limitations. If you really want the full Google experience, albeit with some extras, CyanogenMod has always been the ...more
We've all been there. Your phone's either dead or barely hanging on with a few minutes of life left, and you only have a small window of time to charge it before you need to head out. Sure, you can charge it for the few minutes you have, but what's the point if your device is ...more
While websites may run smoothly without any noticeable vulnerabilities, there's always the looming threat that any background weakness in the site can be exploited by hackers. Once a site is compromised, it can be difficult to get it fixed without the proper help. Google has r ...more
Security is always a top priority for our smartphones. Leaving your phone at the bar or even at a friend's house can leave you open to hacks and lead to the loss of sensitive information. Beyond the lock screen, passwords don't always do enough to protect the information stor ...more
I used to have nightmares when I watched Terminator 2. I mean, I didn't step on a playground for a least two months after I saw that movie. There was something terrifying about computers having so much intelligence. Video: . But that was then and this is now. Terminator was wa ...more
Samsung bucked the trend and threw hard keys onto the Galaxy S3 while most manufacturers are going the soft key route. This hack will add on-screen buttons to your TouchWiz-based ROM. You'll need a root file manager with a system writable text editor—I recommend ES File Explor ...more
I can't say that I'm a huge Tweeter, but I'm definitely a good follower. Having the ability to follow comedians, brands, and athletes helps me stay up to date on the things I'm interested in, and I appreciate being thrown a good joke every now and then. Also, it's nice to see ...more
Going out on New Year's Eve is not for the faint of heart, especially if you live in a big city. Follow the New Year's Eve survival guide below to make sure you are prepared for worst-case scenarios that can range from losing your phone to figuring out how to quickly remove a ...more
Free trials are a great way to test out products before a purchase, or simply for the exploitation of free stuff for that limited amount of time. Some trials last a few days and some last even a month or two, but no matter what—these trials will always expire. But like most th ...more
The Samsung Galaxy S III is undoubtedly a great phone, but still has some minor issues to work out. One involves buggy Wi-Fi roaming, where the Galaxy S3's Wi-Fi signal strength will increase when getting closer to a Wi-Fi access point, but then completely disappears when att ...more
Most of us have some sort of malware scanner or antivirus program on our computers, but what about our smartphones? A lot of people don't realize that computers aren't the only devices that are susceptible to malicious software and apps—they can follow you on your smartphone o ...more
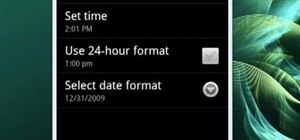
The cell phone may have replaced the pocket watch, but thanks to some clever mods and hacks, "old-fashioned" time telling is making a comeback. Smart watches that connect to your mobile device cannot only tell you what time it is, but also change the song you're listening to a ...more
With the Samsung Galaxy S III being a hot commodity, it's no surprise that your friends might try unlocking your fancy password-protected phone. While some friends have good intentions when using your phone, there are those certain friends who get into the phone to do this... ...more
The newest firmware update for Android, Jelly Bean 4.1.1, has been out for a while now, but not every device has gotten it yet (some never will). One popular device that has recently gotten it is the Samsung Galaxy S III, only they'll be pushing the update out overseas during ...more
All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system. As I have mentioned nu ...more
In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003. Although these operating systems were first released, in some cases, almost 10 years ago, the ...more
If you bought the new iPhone 5 or upgraded your old one to iOS 6, you may be having issues when you try to upload photos to Facebook. After updating, the first time you try to share an image from the Facebook app, it will ask you to allow access to your Camera Roll. If you're ...more
Getting a new phone is like getting a pair of new socks—you can't wait to try them on and when you do, they feel totally awesome. Maybe that's just me, but for many customers that have already received their highly anticipated iPhone 5 in the mail, awesome is definitely not th ...more
Several people have been reporting Wi-Fi problems after updating to iOS 6 on both iPads and iPhones. The connection might work sometimes, but it usually cuts out or takes forever to connect to anything, only to time out shortly after. It turns out this isn't so much a bug in ...more
How do you make a 1950 Studebaker even cooler? By installing an iPod Nano in the dashboard, of course! The folks over at MAYA Design hacked their way to a touch-controlled sound system with this project they've dubbed the "Nano-Baker" (or "Stude-iPod") using a pair of Apple ea ...more
Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security ...more
If you are like me and you have a old iPhone and you don't want to buy a new one, you can fake your ios version by fallowing this tutorial. Just to be safe i am not responsible for what you do with this or if you mess up and wreck your phone. Plus ios and iPhone all belong to ...more
The big question this week would be the controversial Obamacare mandate. And heres the answer: Yes. Obamacare passes Congress' filters and is now an official OK. Texas college hacks drone in front of DHS — RT. There are a lot of cool things you can do with $1,000, but scientis ...more
What's the first thing you would do once you realized you were lost in, say, a desert? If you're like me, you would immediately pull out your cell phone and start dialing every number. But what if you have no service? What if your battery is dead? If you make this survival so ...more
Apple AirTags are super helpful for keeping track of your keys, backpack, and other frequently misplaced items, but there are some pretty clever things you can do with them beyond finding regularly used stuff. Apple sells its smart trackers — small, circular white discs 1.26 ...more
Believe it or not, there are legitimate iOS apps beyond the App Store that you can install on your iPhone. Some of them even work for iPad, Apple TV, and Mac, and there are also benefits to using them over apps found in the App Store. Not all of you will want to try these app ...more
Losing pictures is a uniquely frustrating experience. You take pictures to remember something, to capture a moment so you can look at it again later. So when you lose the thing that's supposed to be what's keeping your memories safe, it's unfortunate and infuriating. Photo Bac ...more
Numerous potential exploits are found for every operating system each month, and Android is no exception. Trouble is, lots of Android devices don't receive timely updates — but many are now getting regular monthly security patches to at least shore up these vulnerabilities. I ...more
The memories on your devices are precious, even if you don't often get a chance to revisit them. The worst thing in the world is when something happens to your computer or phone, and you end up losing some of those memories because your files weren't backed up or your microSD ...more
Cybersecurity is an industry that isn't going anywhere. After the mass move to online work, the need for more cybersecurity professionals skyrocketed. That demand isn't going away because more and more industries are keeping online and cloud services going for their workers. ...more
When an iPhone is lost or stolen, it's imperative to start tracking it via Find My as soon as possible, whether that's from a computer, tablet, or someone else's phone. However, if it's stolen, there's a good chance the thief or robber turns on Airplane Mode, blocking all comm ...more
Never being contacted for a job you're interested in interviewing for is a terrible feeling. It might make you feel inadequate as if your qualifications aren't up to par, but the problem might be that your resume isn't even getting read in the first place. Most recruiters and ...more
Although it's always been important to safeguard your data and private information in the digital age, privacy has recently taken on an entirely new meaning. With more and more people working from home and using unsecured networks as a result of the coronavirus outbreak, hack ...more
At $349, you won't find many smartphones that provide a better deal than the Google Pixel 4a. It has flagship-level performance, a headphone jack, and one of the best smartphone cameras on the market, all for less than $400. But if you act now, you can save even more. At Best ...more
With thousands of people across the country protesting, you might be thinking about joining the march. But as is too often the case, law enforcement has been called to oversee the protests, and interactions aren't always peaceful or lawful. One of the most effective preventat ...more
If you've tossed around the idea of turning your interest in white hat hacking into a career in cybersecurity or IT, now's as good as time as ever to invest some time and energy into improving your skill set. Companies of all sizes hire IT specialists who can install servers, ...more
In the last decade, the number of people working remotely in the US has increased dramatically, and so has their need for technology and software to supplement that remote work. Whether you work from home or a coworking office space, the requirement for highly compatible and h ...more
Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By ex ...more
Thanks to numerous smartwatch deals this holiday season, many people are receiving their first one. But what exactly can they do? In regards to fitness, quite a lot. With a growing list of sensors and software updates, these small devices can be the very thing you need to ulti ...more
The year 2019 was filled with all the normal peaks and valleys of the tech business cycle, but this year was particularly important in a space as relatively young as the augmented reality industry. What once seemed like a vast fertile bed of mobile AR apps, powered by Apple's ...more
Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a ...more
So you've been playing Call of Duty Mobile for some time but can't seem to get MVP at the end of the battle. Well, since the game is a competition of players and bots, you're in an uphill battle. But you don't have to languish at the bottom. With the help of these tips, you mi ...more
Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate c ...more