Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems ...more
Have you ever seen those super-expensive universal remote controls like the Logitech Harmony and thought to yourself, "Man, I really want one of those, but that's just too much money"? You're not alone. Luckily, if you're an owner of an Android device with an infrared (IR) bl ...more
Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of ...more
So, you want to become anonymous? well let me give you everything I know (or at least most of it) to you. Introduction Part: So this is a serious only about being anonymous on the internet and while hacking. This series will cover: (further steps might be added if I decide ...more
Instead of wasting time asking where your friends and family are at a given moment, then having them waste time by describing their location, there are several Android apps you can use that will automate this whole process. To top it off, it doesn't have to be about invading p ...more
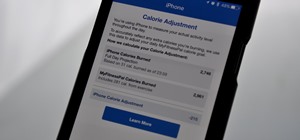
There is much to be learned about Apple Music and the revamped Music application introduced in iOS 8.4. Throwing their hat into an already competitive field with other companies like Spotify, Tidal, or Rdio, this is a bold move on Apple's part. So, before you consider signing ...more
Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it. And this tutorial is going to explain the same. #1 Protection, PC Security: I will tell you how to add another level of security to your PC, instead of j ...more
Whether it's terrorism or brain-hungry zombies you're neutralizing, first-person shooters are an awesome way to immerse yourself within a new world and kill some time with your iPad or iPhone. And with so many games available in this genre, we wanted to show off ten of our abs ...more
Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it i ...more
We always want to find more ways to help brilliantly lazy cooks make great-tasting food and save money and time in the process. Luckily, our Facebook fans are invaluable sources of information when it comes to getting cool tips, behind-the-scenes info, and more. We've already ...more
Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to c ...more
If you struggle with deciding which wine you should buy for an intimate dinner, or the type of beer with the highest alcohol content that doesn't taste like tree bark, then check out some of these great alcohol-friendly apps to make better booze decisions. There are a lot of ...more
When you're actively using your phone, a certain amount of battery drain is to be expected. But, if your device is just sitting in your pocket draining its battery, that's when you need to take action. Among the biggest screen-off battery draws are the various connections tha ...more
Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different. In many restaurants, hote ...more
Welcome back, my budding hackers! One of the keys to being successful as a hacker, pentester, or cyber warrior is the ability to find vulnerabilities or flaws in the target system, which are what we exploit when we hack. We have looked at several ways to do that including var ...more
Arcades have long faded away from popularity, but their legacy is being kept alive thanks to emulators and the avid fans who grew up loading quarters into all of those coin-op games. Although nothing beats an actual arcade environment, my favorite emulator from the early 2000s ...more
Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requi ...more
Android uses a set of permissions that apps can request to perform certain actions, and you're notified of these permissions each time you install an app. The problem here is the fact that you aren't given any built-in way to deny apps these permissions (although Danny just sh ...more
Welcome back, my novice hackers! In a recent tutorial, I showed you how to use shikata_ga_nai to change the signature of a payload to evade detection by security devices (firewalls, IDS, etc.) and AV software. Shikata_ga_nai is an encoding module in Metasploit that XORs the ...more
When OS X Yosemite was first announced, there were a number of features that struck my attention, but one in particular that stood out above them all was the ability to make and receive texts and phone calls from your Mac, which Apple calls Continuity. I probably use iMessage ...more
Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal. This ...more
Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a ...more
Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensi ...more
Smartphone users these days can get bombarded with texts and emails every hour. Online retailers sending you coupons to get you to buy stuff. Girlfriends asking where you are. Service providers reminding you to pay your bills on time. You probably don't need to read or respon ...more
Considering that the average movie ticket these days is $8.38, it's not much of a surprise that Netflix is kicking ass. The same amount will get you a full month of unlimited streaming, and you don't even have to leave your couch. While no one's arguing that it isn't a great d ...more
Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities an ...more
While the PlayStation 3 is an awesome gaming console and the iPhone is an awesome smartphone, Apple and Sony have made two devices (that could be perfect for each other) nearly incompatible. Truth be told, this is more Apple's fault than Sony's, but we'll get into that later. ...more
Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft ...more
Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be. NOTE ...more
An average of 140,000 hard drives crash in the United States each week, according to online backup service Mozy. Additionally, 70 percent of Americans have lost a laptop, smartphone, or tablet, and the average person now loses 1.24 devices each year—less than half of which are ...more
PRL, or Preferred Roaming List, basically tells your phone which towers to connect to first. Changing PRLs can improve reception and data speeds, and in some cases even give you access to corporate/test towers. Because PRLs only operate on CDMA networks, this method only appl ...more
Changing the carrier name from an unlocked iPhone's status bar has been possible to do ever since Cydia released Zeppelin earlier this year. The application comes with preset logos you can use such as Pac-Man, Space Invaders, the Assassin insignia of the Assassin Order from As ...more
If you have an iPhone running iOS 15 that's connected to Google Fi or another mobile virtual network operator, you may not be getting any photos or videos in Messages. That may be because you recently installed a software update, and you'll have to restore your cellular data n ...more
You're in a Zoom meeting, and you're click-clacking away at your keyboard, typing important notes from the call. More realistically, you're doing something unrelated to the meeting, such as browsing the web, playing a game, or messaging friends. Whatever it is you're typing, i ...more
TikTok has grown to be one of the most popular social media platforms in the world. The video-sharing app is a driving force for viral content, spurring various popular movements in dance, pranks, comedy, and more. And as one might assume, videos on TikTok don't stay on TikTok ...more
A side effect of the COVID-19 pandemic is that small businesses are suffering from forced closures and social distancing, but game developer Niantic has a solution. In addition to donating proceeds from Pokémon GO Fest ticket sales (at least $5 million) to fund projects from ...more
We all know Google keeps a history of everything we do on our phones unless we say otherwise. However, you might not realize just how detailed it is until you check it for yourself — even the actions you do in each app are tracked by default. Even if you aren't trying to hide ...more
These days, you can FaceTime with family and friends whether you're at home connected to Wi-Fi or on-the-go with mobile data. You may have noticed, however, that your iPhone will sometimes drop Wi-Fi and rely on cellular instead — whether you're placing or receiving a FaceTime ...more
One of the coolest things about Android is the ability to tweak things to your liking. When it comes to Galaxy phones, Samsung is no stranger to adding extra customizations. Want to add an equalizer to your volume panel? Samsung has an app specifically for that — no joke. Ope ...more
While mobile data caps are larger than they used to be, many of us still have limits to contend with. If you find yourself up against that ceiling month after month, your iPhone itself might be to blame. Luckily, there's an easy fix to stop your iOS device from burning through ...more
When you look at the top corner of your phone, what do you see? Upon upgrading to Android 11 or iOS 14, you'll see either "5G," "5G+," or "5G E" if you're connected to the right network. But what exactly do these symbols mean? They indicate not only if you're using 5G, but als ...more
Before you go out to protest, understand what you are facing. Sometimes these demonstrations become infected with looters and rioters, which could mean interaction with law enforcement and potentially arrest. And if your phone is on you, it can be used as a tool against you. ...more
Undo. Redo. These two actions are forever intertwined, but they're missing from the standard keyboard on Android. Accidentally delete a word, and there is no Ctrl + Z to undo this mistake. But there is finally a solution available on Samsung Galaxy phones. Now, if you acciden ...more
Google's G Suite collection of premium cloud services and apps have become popular with business customers, with more than six million subscribers now. For those who use Google accounts for business and personal use, this can create some workflow issues. For instance, while G ...more
An unfortunate byproduct of Samsung's One UI version of Android is redundancy, where you have the Google/AOSP way of doing things mixed with Samsung's methods at the same time. One example comes in taking screenshots, where Samsung has added its own take on editing and sharin ...more
If you have a OnePlus phone with an in-display fingerprint scanner like the 6T or 7 Pro, the "Quick launch" feature can put a variety of app shortcuts right on your lock screen for easy access. For example, you could use the "My apps" shortcut for the Play Store to check for y ...more
Several popular custom ROMs and root mods let you double tap the status bar at the top of your screen to put the phone to sleep. It pairs perfectly with the double tap to wake gesture you'll find on pretty much any Android phone. But if you're not rooted, you'll be glad to kno ...more
It's nice having a dark theme on Android 10 and One UI 2, but setting it on a schedule takes it a step further. Imagine the light theme turning on every morning, and the dark theme taking over after sunset — all automatically. It sounds pretty simple, but it's one of those thi ...more
As long as you have the meeting ID, you can join and interrupt virtually any video call on Zoom. And that's how we get terms such as "Zoom-bombing," where someone jumps into a chat to say or visually show vulgar and inappropriate things to the other participants. However, host ...more
Since Stadia is an early access game streaming platform, Google is still working on bringing big things to the table. You can expect wireless Stadia controller support for many more devices, high-quality 4K gaming on all Chrome web browsers, and more Google Assistant features. ...more
The coronavirus pandemic has ushered in an unprecedented time in modern history where terms like "social distancing" and "self-quarantine" have pushed their way into the zeitgeist. One of the most popular (and likely most effective) ways that employers have done their part in ...more
Recovery mode and download mode are useful for modding and they can come in handy in a pinch. Booting into recovery mode to do a factory reset or wipe cache fan save your Galaxy S20 from a soft brick, and entering download mode lets you install firmware with utilities like Odi ...more
When Apple removed the Home button from iPhone, it introduced a new way to install apps that caused confusion over what to "double click." Like most iOS changes, it didn't take long to get used to double-clicking the Side button. But for some, performing a double-click on the ...more
Google has always experimented with Chrome's UI, but when they make more drastic changes, they start by hiding them in the feature flags menu. One of the latest designs makes Chrome more accessible in a world of big and tall phones. "Duet" is an optional redesign that takes C ...more
As helpful as it is, Google Maps isn't the only mapping app with augmented reality walking navigation anymore. This week, Israel-based startup Moovit introduced a new AR navigation feature called Way Finder for its eponymous navigation app for public transit and ridesharing s ...more
Like other popular social media apps, TikTok features a tagging system — dubbed TikCode — to follow people in your immediate vicinity. Instead of searching for their username, you can scan their TikCode, and TikTok will launch their page immediately. Of course, you have a TikC ...more
Group chats in Facebook Messenger can devolve into outright noise pollution as people chit chat randomly and bombard you with distracting notifications. Unfortunately, leaving the group outright alerts everyone inside, so if you want to get out of the thread unnoticed, what ex ...more
Back in the earlier days of Android, you were able to connect your phone to a computer, and it would mount automatically. This meant once the USB connection was made, your internal storage would pop up on the computer and you could go about your business. But recent versions o ...more
Two minutes on TikTok is all it takes to learn that Renegade is a huge deal. The song and the dance combined are a viral trend that shows no sign of stopping. Feeling left out? Let's change that. You can learn the entire dance in just 20 seconds. First, what is the Renegade c ...more
One of Android's biggest strengths relative to iOS is how simple it is to sideload apps that aren't on the official app store. Rather than having to sign IPA files or tell your phone you trust a developer every two weeks, you can just enable a setting and be done with it. Jum ...more