We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no ne ...more
We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no ne ...more
Thank you to everyone who entered Phone Snap! and MacPhun's contest for the International iPhoneography Exhibition. There were a lot of impressive entries, and I'm very excited to announce the three photos that will be shown at the exhibition December 18th through the 22nd at ...more
Encryped traffic and tunneling is a must when away from home to keep you and your information safe. SSH tunnels can be slow, and are heavily encrypted. VPNs are an all port solution, and proxies are just not what we need in most cases. Then, there is Tor. Tor runs your traffi ...more
You've seen the felt mouse, which made computer clicking comfortable and chic, now brace yourself for something a little more interactive—DataBot. DataBot hails from the clever minds of Jan Barth and Roman Grasy, two Interaction Design students based in Germany who wanted to ...more
Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills. Submit your best shot to our weekly competition for a chance to win an awes ...more
Nintendo's Wii Remote came close, but never has a video game peripheral garnered such adoration from the hacker community than the Kinect. Since the release of Microsoft's controller-free gaming device last November, there has literally been thousands of fun and useful projec ...more
It's remarkable that a gaming device (from Microsoft, no less) designed for geeky gamers has incited broad innovation in medicine and robotics. But that Kinect has captured the imagination of hackers-with-MBAs-in-mind is downright amazing. Below, six videos demonstrating a va ...more
It's gigantic! It can handle over 100 simultaneous touch points! It has a curvature of 135 degrees! And best of all, it is not the newest, insanely expensive gadget to hit the market. Instead, this touchscreen was hacked together with a bunch of PCs, video cameras, projectors ...more
Think beautiful bokeh photography + just a hint of TRON sensuality and you have photographer Audrey Penven's lovely series entitled "Dancing with Invisible Light: A series of interactions with Kinect's infrared structured light". Penven's process is quite interesting: "With ...more
In 1782, an English plumber named William Watts came up with a clever method for making shotgun ammo. Watts constructed a six story "shot tower", consisting of a series of perfectly lined up holes, drilled into all six floors of the structure. Watts then poured molten lead thr ...more
Tricycle + simple plow blade = true yankee ingenuity. (Who needs a pricey snow plow vehicle?) Craig Smith recently submitted his custom contraption to MAKE: "The custom 3-wheel bike with sidecar was made years ago, a replica of a bike my childhood friend had. Last winter I a ...more
As Theo Gray of Gray Matter demonstrates below, contrary to what the ads may say, diamonds CAN expire. Especially when attacked with a blow torch and liquid nitrogen. Gray says: "Diamonds are neither rare nor intrinsically valuable nor uniquely romantic. Those are ideas inven ...more
China's latest futuristic project is a massive "3D Express Coach", a clever project proposed by Shenzhen Hashi Future Parking Equipment Co. as a solution to traffic in the extremely overpopulated country. The gigantic bus will allow cars less than 2 meters high to travel unde ...more
Get rid of all your preppy shirts by morphing them into something spectacular. This is chic simplicity. A smart and casual princess cut button-up shirt that will never go out of style. See how to turn a preppy shirt into a cute princess top in this video from GiannyL. This DI ...more
Iowa firefighter Pete Lilja has modded the software of a Canon powershot to record images of Earth, from as high as 85,000 feet! Lilja's hack requires the following: 1 basic point-and-shoot consumer camera attach camera to a GPS transmitter (+ a phone number just in case the ...more
Take a break from the city and treat your friends and family to some good old-fashioned fun. You Will Need * A route through fields and woods * A pickup truck, or tractor with trailer * Firewood * Marshmallows * Hot dogs * 1 to 2 dozen bales of hay * A clear night * Friends an ...more
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a m ...more
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hide secr ...more
So, your children have the same old boring Fisher-Price Power Wheels that all the other kids on the block have. Do you really want your child to be like all of the rest? No, I didn't think so. Turn those miniature Power Wheels, Dumar or Peg Perego vehicles into a little bit of ...more
The DIY industry is booming, despite the desperate blackmailing of society by finance capitalists. Companies like Adafruit and Makerbot are grossing well over a million dollars a year, and Evil Mad Science Laboratories just recently dedicated themselves to running a full-time ...more
WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. This week: A nostalgia-themed cell phone photo ...more
Home chemistry is great, but what happens when you forget to label your chemicals? How do you know if you turned a clear glass of ammonia into a clear glass of unobtainium? Chemists have a tool for just that. Litmus paper are small bits of filter paper saturated with a reacti ...more
Shortening URLs has become a necessity in this age of Twitter and limited-character status updates. It not only allows us to cram more words into our oh-so-important Twitter statuses, but it also helps us with a few other things. Some Benefits of URL Shorteners We can create ...more
Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their c ...more
When the iPad 2 was released earlier this month, as to be expected there was a whole lotta buzz. And for good reason—while the the newest version shares the same price tag as the old, it boasts some significant new features. In case you missed it, here's a quick overview: Bet ...more
Body hacks. So simple, so ingenious. They're the shortcuts in life. We love them, the internet loves them. Back in 2008, somebody named Alicia Goh wrote a friendster blog post that has been passed along far and wide. Her tricks of the body include quick solutions for an itchy ...more
Click the more info tab to see the instruction on how to get a bear on Mybrute.com. This is a tutorial on how to get a Bear on Mybrute.com, An Online RPG Game, It's a very popular game that a lot of people plays everyday, You don't need to do much action with your hands just s ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. Thanks to all of our active moderators and ...more
Anonymity is very important to many internet users. By having your "e-identity" exposed online, you can be stuck with a number of unwanted issues, such as: Privacy invasion. Internet tracking. Exposure to being hacked. However, what if we wanted to spend money anonymously? T ...more
Bokeh (which translates to "blur" in Japanese) is a photography technique referring to the blurred areas of a photograph. Basic bokeh photographs often have one point of focus, while the background falls away into a dreamy, blurred haze. The technique can be taken even furthe ...more
The UK print media has been yellower than the middle traffic light for a long time now. The News of the World scandal has cast that into particularly sharp relief of late. The Sun, one of the biggest newspapers in the United Kingdom, demonstrated it again last week when they r ...more
Always falling asleep behind the wheel? The National Highway Traffic Safety Administration (NHTSA) estimates that there are over 56,000 sleep-related accidents each year, resulting in 40,000 injuries and 1,550 deaths annually in the United States. Don't want to be a statistic? ...more
Nobody could predict the success of Microsoft's Kinect, not even Microsoft themselves. So, it was quite a surprise when it ended up earning a Guinness World Record for fastest-selling consumer electronics device, and an even bigger surprise to see people buying one that didn't ...more
This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to rea ...more
In this article, I'll show you how to build a simplistic circuit to generate negative ions. Negative ions have been known to contribute to fresher air, happier mood, and general health benefits. However, they also look amazing in the dark (check out the photos below, purple pl ...more
Formerly ipchains, iptables is a script-based firewall that's included with both Mac and Linux operating systems. In my opinion, it's the best firewall in existence. The only downfall is that it's complicated for some people to use due to its script-based nature. But this shou ...more
In 1988, John Langley created COPS for the fledgling FOX network. 23 years later, the show is still running. It is the Energizer bunny of prime time television. Since John has followed more police officers and witnessed more crime than any human being on earth (absolutely no q ...more
Final Fantasy 14 the MMO is now live. The special edition priced at $75 enables people to play eight days earlier than people getting the regular edition, which comes out on September 30th. Mine arrived yesterday and here are some pictures of what's inside the special edition ...more
The Holy Grail of chicken has just been found by an unsuspecting reporter of the Chicago Tribune. Yes, that's right: The secret 11 herbs and spices in Colonel Sanders' Original Recipe chicken has finally been revealed, and it looks legit as hell. While a copy of the Original ...more
On a Wednesday evening when friends are going to a movie or out to dinner, you’re at the dojo training. On a Sunday night when your show or the game is on the television you’re not home to watch it, you’re at the dojo training. On a Friday night when the town is full of exci ...more
Since the invention of the mechanical clock, enclosure of the commons, and proletarianization of labor, the alarm clock has been the bane of our existence. While not actually evil, it does represent the constant and uncompromising glare of our owners shaking a patronizing fing ...more
In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the ...more
In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts. In the last Hacker Fundamentals, we talked about the OSI model as well as a little on TCP/IP and the protocols that make ...more
The community here on Null Byte has always been great and helpful in sharing their know-how, even before I took up admin duties in this World. I jumped at the chance of leading Null Byte because I enjoy teaching and informing people on all of the important need-to-know things ...more
Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use y ...more
Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three! Each anonymity network is designed for a different specific purpose. One network al ...more
Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. A ...more
If you’ve never heard of the term search engine optimization or SEO, then your website probably isn’t optimized for search engines and it’s hindering your site’s ability to get all of the traffic that it should. Read on for an explanation of what this entails and how it can he ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. Thanks to all of our active moderators and ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. More amazing community contributions this w ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. This week has been an exciting one. The com ...more
When you first become interested in learning how to program, it can be difficult to find a place to start. A lot of questions come up, especially if you're new to the idea of programming entirely. After you pick which language you want to learn, you have to worry about how you ...more
+Nik Cubrilovic discovered last week that Facebook could track your web activities even after you logged out of your Facebook account. After some blatant denials from Facebook spokespeople, Facebook decided to fix the logout issue, but not before +Michael Arrington, on his new ...more
By Ethical Traveler As the world becomes ever more interconnected, being an ethical traveler becomes both easier and more urgent. Travelers today have access to far more information than we did even 10 years ago. We can observe–almost in real time–the impact that smart or sel ...more
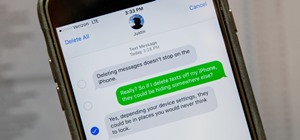
Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called ...more
See how to hack a two "D" cell Maglite to make it much brighter. This is a cheap but very power light of 700-800+ lumens, brighter than other hacks.
Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global finan ...more
Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my b ...more
Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different. In many restaurants, hote ...more