Over the past few days, we've learned a lot about Samsung's upcoming Galaxy S9 and S9+ smartphones. In addition to a full list of hardware specs, we have complete renders direct from renowned leaker Evan Blass. Of course, Samsung always has a few surprises up their sleeve, and ...more
The new iPhone 8 and 8 Plus models come with a gorgeous Retina HD display with Apple's True Tone technology, which automatically adjusts the white balance on the screen to match the ambient light around you. The iPhone X also has True Tone built into its Super Retina HD displa ...more
In the "Do Not Disturb" menu in your iPhone's settings, you can choose to allow phone calls from everyone, your favorites, or specific groups. However, this does not apply to text messages, only phone calls, so there's no way to get vibration or sound alert for messages from s ...more
Samsung has some competition as LG may be incorporating OLED panels for their new flagship V30 launching later this year. Last month, it emerged that the "other" South Korean company would be preparing to mass produce curved OLED panels, which may be featured on the LG V30. L ...more
You know, I was actually starting to get comfortable with the idea of the iPhone 8 not showing up until next year. As an Apple fan, I made my peace with it. "There's a lot coming in this model," I told myself. "It does make sense that this many features could cause delays." I ...more
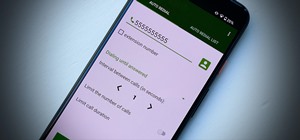
Whether you're a professional mechanic, a hobbyist, or someone who just wants to know why their check engine light came on, your Android device and an OBD-II adapter can provide insight as to what's going on with your car. Most adapters sell for less than $10, and once you plu ...more
The '90s were a great decade to be alive. Before the internet became a high-availability service, we were untethered from the bombardment of media present in today's culture. Children ran through the streets with levels of physical exertion beyond what's required to capture fi ...more
Halloween is this weekend, so if you're looking for a last-minute big batch cocktail that will keep your guests properly hydrated—and might turn them into mutants—look no further! (Note: This will not actually hydrate anyone, just so we're clear. Priorities, people!) Meet Zom ...more
Whatever you think of Google's new Pixel phones, the one thing we know for sure is that these are the most polarizing devices in recent memory. On the one hand, we've seen reviews in which longtime Android users say they'll be walking away from the OS all together thanks to Pi ...more
When a new version of iOS comes out, everybody gets caught up in the craze of finding features and playing around with new functionality. But this generally leads to a lack of coverage on the finer aspects of the update—things like bugs, minor tweaks, and pain points that user ...more
We're inching closer towards the singularity—that point where technology advances to the steepest slope of the logistic function S-curve and simply skyrockets at a rate we've never seen before. Somewhere along the way, the line between humans and the tech we rely on will becom ...more
When it comes to a perfect summertime dessert, lemon meringue pie is the ideal contender with its rich lemon filling and light-as-air meringue topping. In my humble opinion, the meringue is the true star of the dessert, instantly elevating what is simply a lemon pie to somethi ...more
Smartphones tend to struggle when it comes to recording video in low light situations. Danish phone manufacturer Lumigon included a good camera capable of shooting 4K video on its latest phone, The T3, but the real interest lies in the second camera, which is a dedicated night ...more
Researchers at MIT's Computer Science and Artificial Intelligence Laboratory have created Wi-Fi technology that identifies where you are, which may eliminate the need for passwords. Video: . The system, called Chronos, can determine where a user is with an accuracy of "tens of ...more
Apple unveiled a 9.7-inch iPad Pro at their keynote event today, filling their roster to four different iPads. The smaller iPad Pro has the same screen size as the iPad Air 2, but comes with significant improvements under the hood. Keynote speaker Phillip Schiller rolled into ...more
A few lines of code in the iOS 9.1 library cache found by Chase Fromm (@uloshe) indicate that Apple could be working on making iPhones that are Li-Fi compatible. Code in iOS 9.1 lists "LiFi Capability.". Li-Fi, which transmits data through light waves rather than radio waves, ...more
Apple revealed the new iPhone 6S and 6S Plus at their September 9th event, and there are two particularly awesome features built in just for selfie photogs. The first is 3D Touch, which gives you a quick shortcut to taking selfies just by pressing the screen in a certain way. ...more
Android's auto brightness feature was recently updated, and as of version 5.0, a new "Adaptive brightness" feature was added. This allows users to set a preferred overall brightness level, but still have the ambient light sensor adjust the backlight accordingly. For many folk ...more
The Nexus 6 has an AMOLED screen that uses virtually no power to display black pixels. To take advantage of this feature, Google included an Ambient Display notification system that shows a black and white version of your lock screen when you get a new message. As a result, th ...more
Carriers really suck, don't they? We constantly have to monitor our data usage, even though many of us are on "unlimited" plans, which, in reality, will just be throttled to a slower 2G or 3G connection when we hit a certain download threshold. Even when we're not actively us ...more
Toilet paper isn't the first thing that comes to mind when you want a hot meal, but when you're camping or out in the field (i.e. military training), a little TP is the difference between cold tuna and luxury. As redditor drdesparche points out, Israeli military forces are fe ...more
Cases and stickers are always great, but they aren't the only way to customize an iPhone. The software on your device is full of customization options, from a better-looking home screen and cooler lock screen wallpapers to app icon changes and a system-wide dark mode. There's ...more
If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them ov ...more
In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as ...more
When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving i ...more
Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands. RapidScan does an excellent job of automating the deployment of vulnerabili ...more
Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know. Possibly the most popular and well-known reconnaissance tool currently ava ...more
Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for expl ...more
Apple shipped their first batch of iPhone X's with an outdated and unpatched version of iOS. Be sure to check for updates and install iOS 11.1 first thing after you open your new iPhone or it'll be susceptible to the KRACK vulnerability for wireless connectivity. KRACK, or Ke ...more
If you've been looking for an alternative to Google Maps, look no further than Waze. In addition to benefits like crowd-sourced traffic data, police trap locations, and road work avoidance, the app even lets you personalize the voices used for navigation and directions. Best ...more
If you have movies and videos stored on Box, Google Drive, Dropbox, or OneDrive, you should definitely be using the VLC app for iPhone. After setting a few things up, VLC will let you stream videos directly from any of these services with a proper video player UI, complete wit ...more
As you all journey along with me on my challenge to become some sort of Instagram expert, let me share with you one hack that is currently helping me out a lot. If you've ever wanted to put a line break in your posts, then keep on reading. If you are in Android user, then you ...more
Google Home now helps users to discover new music with an added "Listen" tab in the app. The feature offers suggestions based on the Cast-enabled apps on a phone, while offering other apps to download if you'd like to broaden your musical horizons. The playlists are curated to ...more
One thing you have to love about Google is their sense of humor. From their annual April Fool's Day pranks to the hidden Flappy Bird mini-game in Android to tons of hidden commands in Hangouts, you can just tell that those smart guys in Mountain View still like to have a littl ...more
One more business has decided that rewarding hackers to find flaws in their computer systems is a wise investment! As you know, a number of software companies offer bug bounties, and some of these can be quite lucrative. Google, for instance, offers a bounty of $150,000 for an ...more
Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?" As the hacker is among the most skilled information technology disciplines, it requires a wide knowledge of IT technologies and techniques. To truly be a great h ...more
Holidays can be challenging, especially around Christmastime—but not if you invoke your inner MacGyver spirit. In my latest "life hacks" guide, I show you 10 amazing tips and tricks that'll hopefully make your holiday season a little more merry. Video: . If you're in need of s ...more
Remember the Power Pwn, the clever little hacking tool disguised as a power strip? It's great in theory, but with a $1,295 price tag, it definitely doesn't fit into most people's budgets. But what if you could make your own for a fraction of the cost? That's exactly what the ...more
(We did not know about these, either...until we discovered these videos.) The fixed gear bike, also called a fixie, was designed for track racing in the velodrome. Working bike messengers brought them to the NYC, Tokyo, SF, London streets on account the cycles gave them far m ...more
There's something extremely satisfying about hunting down your online adversaries and knocking them out with a well-placed shot, which probably explains why shooting games are still one some of the most popular time killers for iOS and Android. Shooting games for mobile come ...more
After months of waiting, it looks like HMD has finally answered the call. Nokia's parent company is finally releasing a true flagship phone — one that isn't just an enhanced version of a previous phone and actually brings something new to the table. That phone is the Nokia 9 P ...more
As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even a ...more
Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion ...more
Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exi ...more
RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices. I initially covered RouterSploit on Kali Linux and macOS (OS X), but this tuto ...more
The Galaxy S8 has finally touched down, and it's an absolutely gorgeous device. Samsung's brand new flagship comes jam-packed with new features — some refined, and some that aren't. Luckily, we've compiled some major features to help you get started as quickly as possible so y ...more
While the Apple Watch does have up to 18 hours of battery life each day on a full charge, your results will vary depending on how often you use it and what you're actually doing with it. If your Apple Watch isn't lasting all day long, we've got some battery-saving tips you ca ...more
Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire. Those packets can be examined for ...more
Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of th ...more
Welcome back my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on us all, all the time. Basically, the PRISM program simply look ...more
Have any Star Wars fanatics in your family? Well, here's a great Christmas gift idea for those Star Wars fans who think they have everything... a freaking LEVITATING DEATH STAR! Video: . Backwards Lamb Props created the above Death Star model by using one of those cheap magnet ...more
Need to be undercover? Well, make yourself impossible to photograph. Get some infrared LEDs. They're undetectable to the human eye, but that's not the case with cameras. Wire them to the brim of your hat and you've got instant invisibility to any camera -- paparazzi, Big Brot ...more
Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, w ...more
Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopp ...more
In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hea ...more
The Pixel is the phone to beat when it comes to cameras, and it's largely due to software. While its hardware is solid, Google's machine learning prowess and general coding wizardry are the biggest reasons the Pixel is so good with taking photos and recording video. What this ...more
Yelp reviews are great for getting a feel for how a business operates, but they can't always be trusted, and they don't always get to the point fast enough. That's where "Tips" come in, and you can view and make them whether you're on an iPhone or Android phone. No, I'm not t ...more
If you're not looking closely, it's easy to mistake last year's Galaxy S8 for the brand new Galaxy S9. Design, build materials, screen size, software — it's all virtually identical, save for a few exceptions. But those minor differences can add up. We made a chart highlightin ...more
Some phones have a feature that turns your screen white for a second when you're taking a selfie in dim lighting. This does a great job of illuminating your face in a pinch, but there are two problems with it: First, not all phones have the feature, and second, it doesn't work ...more
Essential recently launched their Android Oreo Beta Program, open to all owners of their PH-1 flagship. We detailed a quick and easy method for installing the beta on your device. With every beta program, there are bound to be plenty of new features and a few bugs, as we found ...more