Remember the good ol' days when you actually had to swipe your credit or debit card to make a payment at the store? Now all it takes is a flick of the wrist to purchase goods with your card, thanks to RFID (radio-frequency identification) technology from Chase (blink), Visa (p ...more
The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an ent ...more
This is a Tutorial for those who want to hack their level in Pet Society. Hex Code: 840FFF85C12A0FF2 How to hack Pet Society! Pet Society cheats, tricks, hacks. Pet Society is a game that can be played on Facebook. Check Pet society's Facebook app page here. In the words of ...more
Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this in ...more
Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbl ...more
Summer is right around the corner, which means it's time to switch from perfect hot coffee to perfect cold coffee. A nice icy glass of cold coffee is wildly refreshing and just plain delicious. In my opinion, it's the key to enjoying any sunny day (warning: if you don't alread ...more
To decrease the possibility of breaking your glass dinner plates while moving into a new home, stack them vertically inside a box like vinyl records instead of horizontally like a stack of pancakes. If you're an office supplies nerd, here's the perfect excuse to buy different ...more
Have a need for speed? And high scores? Look no further than this cheater's guide, which demonstrates a method for hacking Crazy Cabbie for high speeds and maximum points. Learn how to hack Crazy Cabbie on Facebook! This video tutorial shows you how to hack Crazy Cabbie (01/0 ...more
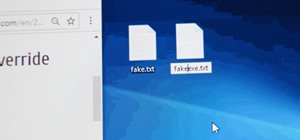
With the macOS stager created and the attacker's system hosting the Empire listener, the malicious AppleScript can be designed and disguised to appear as a legitimate PDF using a few Unicode and icon manipulation tricks. A real PDF is required for the attack to work. Files ov ...more
Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listenin ...more
Samsung and Microsoft do it out of the box, Google does it with a little tweaking, and they all do it well—multitasking. While we can hope for better (or simply any) multitasking integration for the next iteration of the iPad and iPad mini, a new jailbreak tweak eliminates the ...more
Do you have one of those jobs where the minutes seems to stretch by like hours? Then shaving off an extra twelve might make all the difference. All you need is cunning (to kidnap the workplace clock for the night) and hacking skills (not to worry, creator Randy Sarafan will he ...more
The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely. The sheer volume of Windows computers currently in operation around the world ...more
First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the ...more
Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will. Torrent clients like uTorre ...more
Club Penguin is a flash-based website with an a virtual world of online games for kids to play. Learn how to hack Club Penguin with tricks and cheats. Watch this video tutorial to learn how to hack Club Penguin with Cheat Engine (09/14/09). This uses Cheat Engine 5.3. Club Pe ...more
Many of us experience highly emotional "freakouts", so to speak, more often than we'd like. Weather you experience them personally, or via your loved ones, it can be very difficult to think rationally during an episode, and for some people it can take quite a while to calm dow ...more
Christian Cantrell, Adobe's Air Product Manager and Evangelist, has released a video to demo websites that take advantage of the motion sensors in a mobile phone, tablet, or laptop via JavaScript. Now, let's take a look through the code and break down the core pieces that you' ...more
This video shows you a variety of hacks and mods for your Xbox 360, AppleTV and how to boost your wifi. You're shown how to make an antenna booster for your router, stream content to your Apple TV and upgrade the hard drive.
Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method. Note: This method only works if the website has the vulner ...more
Battery life is often a big problem with new smart phones. In this tutorial, learn how to change the settings on your brand new HTC EVO 4G so that the battery lives longer on the 4G network. Don't get stuck with a dead phone- check out this clip and keep it alive!
Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems ...more
In this tutorial, you'll learn how to exploit weak security questions to take control of a given Yahoo! Mail account in much the same way Sarah Palin's Yahoo! account was recently "hacked." (To access Sarah Palin's account you will need, in addition to the tutorial, some manne ...more
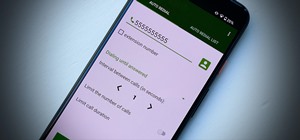
Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with ...more
The interwebs is a great source of information, but sometimes said information is not always legit. That can be frustrating when it comes to making fun food, costumes, and arts and crafts for Halloween, like this bowl of "bloody" gummy worms. There are certain tricks you need ...more
Flash games are addicting, especially Bouncing Balls. But can you actually beat all of those high scores you see? Probably not, but you can if you use Cheat Engine. Watch this video tutorial to learn how to hack points in Bouncing Balls (10/11/09). Download Cheat Engine 5.5 i ...more
When it comes to earning high scores in a web game like Crazy Taxi or Crazy Cabbie, sure, you could, like, actually play it — but where's the fun in that? Cheat your way to the top with this hacker's how-to. Learn how to hack Crazy Cabbie on Facebook! This video tutorial show ...more
Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely da ...more
If you are a photographer and are handy with a screwdriver and electrical tape, this is a really cool project to do. Basically, you "Frankenstein" a camera, taking a camera apart and rebuilding it with different lenses and the like, which makes for really cool photo effects.
When the much buzzed Facebook profile page redesign was released back in December, French artist and co-director of ad agency La Bande Originale Alexandre Oudin came up with an innovative way to maximize the visual possibilities of the page. His clever "hack" created a ripple ...more
Microsoft's built-in antimalware solution does its best to prevent common attacks. Unfortunately for Windows 10 users, evading detection requires almost no effort at all. An attacker armed with this knowledge will easily bypass security software using any number of tools. As ...more
In this eight minute video the host of the video conveys the methods and techniques that can be used for hacking the "Urban Rivals" video game. By use of Microsoft Word, the host types out the methods that are being used. This typing makes for a clear and easy to understand co ...more
Kipkay never fails to impress, and this so-called "condom hack pack" is no exception. Who knew there were so many useful uses for a condom besides the obvious! In this Kipkay two-part video, learn how to hack condoms for nine different uses. One condom hack is the "condom fir ...more
Turn a 'toy' radar gun into the real thing! Cops don't even have one like this! While this is a completely new and different design, the inspiration for this video is from an article by Ken Delahoussaye in MAKE Magazine. Just watch this video tutorial on how to hack a toy rada ...more
Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers). Flash ...more
We've always loved a good summertime hot dog, placed lovingly in a soft simple bun with ample ketchup and mustard. But after eating hot dogs this way and this way alone for the majority of our lives, we grew tired of the same old thing. Enter: The search for the 10 best hot d ...more
Thanks to Yifan Lu, it's been discovered that the operating system running on the Kindle Touch is written mostly in HTML5 and JavaScript, unlike the previous models which used Java. This is exciting, because when a device is hacked or rooted, that means homebrew programs can b ...more
Welcome back, my novice hackers! It has become clear from some of your questions that quite a few of you are unfamiliar with the hexadecimal system, or simply, hex. The hexadecimal system is used throughout computing and if you have never studied this Base16 numering system, ...more
So, how does someone keep their hacking life completely secret? What This Is: I'd like to know how hackers keep their hacking life secret. So with a bit of experience and knowledge obtained from elsewhere I want to share what I know, and also ask a few questions to become ev ...more
Welcome back, my hacker novitiates! Now, and more so in the future, wars will be fought hacker v. hacker. The number of soldiers, guns, tanks, and ships will be less important in your success in warfare than the number of well-trained hackers you have. Every nation and every ...more
Get more money, deliver one hit kills, increase your experienc points... you can do all of these when playing Ninja Saga, all you need is the free game hacking program Cheat Engine. Here's how to use it to get what you want.
What if you could have a secret hard drive connected to your computer that only you could activate? You can! Samimy shows you how to hack a remote controlled toy car and make a super secret hard disk drive in your computer, accessed via a secret activation key. This hidden eme ...more
Hi there, Crackers, Welcome to my 7th post (Part-1), this tutorial will explain about the basics of Batch Scripting. Why Batch? Batch is a really easy and interesting scripting language, it is used for malicious purposes, i.e. how can you exploit the victim's PC/life, furthe ...more
What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl. A user with the handle @blanket found out the hard way that Twitter's security is atrocious when his a ...more
Tired of touch-tone hell? Get human with our cool phone hacks and cheats with the tips from this how-to video. Become a life hacker - we'll show you how to find phone numbers, cheat the computer and hack the call center system with our hacking tools. Watch this video tutorial ...more
You must have read news about hackers dumping the data online, recent one was Ashely Madison. It's only the big companies' data, which gets noticed once it is out. There are many other small leaks which don't even get a mention. So this article is the first one of my series wh ...more
Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an imag ...more
Today, learn the basics of lock bumping. Lock bumping is a lock picking technique for opening a pin tumbler lock using a specially-crafted bump key. One bump key will work for all locks of the same type. This video tutorial will show you how to hack into locks with lock bumpi ...more
If I could survive on one food for the rest of my life, it would be pizza. The irresistible smell of baking pizza instantly makes me feel both comforted... and hungry! While frozen pizza can satisfy your cravings, using fresh dough to make your own pizza is definitely much mo ...more
Welcome back, my aspiring hackers! As you have probably discovered by now, the file system in Linux is structured differently from Windows. There are no physical drives—just a logical file system tree with root at the top (yes, I know, roots should be at the bottom, but this ...more
Google Play has no shortage of Nintendo emulators: SuperGNES (Super Nintendo) Gameboy Color A.D. (Game Boy Color) My Boy! (Game Boy Advance) nds4droid (Nintendo DS) DroidEmu (SNES, NES, GBA, GBC, etc.) Those are just a few of what's available out there. The only problem with ...more
If you need to relieve an itch in your throat, you can try getting rid of it by scratching your ear. Or if you accidentally give yourself brain freeze while eating ice cream, you can press your tongue against the roof of your mouth and cover as much as surface area as possible ...more
Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV so ...more
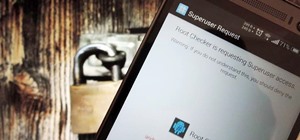
Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of ...more
To hack into Google images follow the following steps. You will first need to open a new internet browser window and go to Google, then load their images website. Next type into the search bar your image query and press search. Once you have gotten your search results paste th ...more
I don't like paying for repairs, and I don't like purchasing extended warranties. When one of my gadgets break, I perform emergency surgery and try and fix it myself. It doesn't always go well, but I've managed to resuscitate a few iPhones, an HDTV, an Android tablet, multiple ...more
In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greetin ...more
Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?" In this tutoria ...more
Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this ...more
The cold time of Christmas is upon us, and Icy Town is a winter-ific game you can play… and hack. With Cheat Engine and a little patience, you can hack and unlock floors in the game easily. This wintery video tutorial teaches you how to hack Icy Tower floors with Cheat Engine ...more