With the nation facing a shortage of ventilators for COVID-19 patients and no apparent ramp-up in the production of new ones, engineers, medical resistents, and do-it-yourselfers are sharing plans for homemade versions. But before you go online to start ordering parts for any ...more
In order for this tutorial to work, you will need a jailbroken iPhone or iPod Touch. Once you have this, download the OpenSSH protocol from Cydia and then download WinSCP onto your PC. Once you've hooked everything up and logged in, navigate through your Applications directory ...more
In this tutorial, learn how to hack a can of Monster - or any large soda can - to stash a bottle. This is great if you are drinking a beer in public when you aren't allowed or if you'd just rather no one knew what kind of embarrassing beverage you are actually consuming. Follo ...more
This is a hack to create a Roomba covered in LEDs that will munch your dust. See how to do this cool mod for the Roomba, the robotic vacuum cleaner made by iRobot.
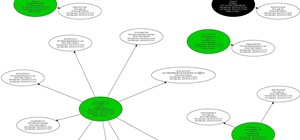
Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator. In earlier posts in this series, we examined registry fi ...more
So 2000 was a wash for an election year; we put up with W for four years, then what happened? 2004! Lost again!!! Diebold you just can't seem to fade. Don't believe the elections were a fraud -- try out the legitimacy of the elections yourself. Princeton students present the ...more
Sometimes, in the course of playing virtual aquarium games, it becomes necessary to break the rules. Learn how with this cheater's guide, which demonstrates how to hack Happy Aquarium with the Charles Web Debugging Proxy tool. Watch this video tutorial and learn how to hack H ...more
Raw onions are commonly associated with bad breath, but when it comes to wet paint, instead of creating toxic smells they help remove them. If you just painted inside your home, slice a few raw onions in half and place them alongside the walls to absorb noxious fumes. Just mak ...more
Ever been warned that sitting too close to the TV might damage your eyesight? It won't. That probably won't stop this electronic View-Master from giving your poor mother a heart attack, however. Tuttle of Hacker Consortium writes, "[The toy has] 2 Colby 1.5 inch digital key ...more
Would you exercise more if you were constantly running from zombies in a post-apocalyptic world where hundreds of people are depending on you to not get eaten? If your answer is yes, then you really need to snap out of your sedentary lifestyle ASAP and install the Zombies, Run ...more
At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher. Previously: How to Create a ...more
Build your own cheap taser with an old camera and some plastic. These guys even show you the final product's effects on each other.
Considering that nearly half a million brand new apps were published to the Google Play Store in 2015, you can definitely call it a banner year for Android development. In fact, it's getting to the point where we're a bit spoiled as end users, since we've grown to expect somet ...more
Holidays can be challenging, especially around Christmastime—but not if you invoke your inner MacGyver spirit. In my latest "life hacks" guide, I show you 10 amazing tips and tricks that'll hopefully make your holiday season a little more merry. Video: . If you're in need of s ...more
Looking for a way to game your Bejeweled score? Check out this video tutorial to learn how to hack Bejeweled Blitz (01/27/10) with a Mozilla Firefox extension. Cheat info: 1-7 turn gem under cursor into a gem of the respective color F turn gem under cursor into a flame gem S ...more
When performing this iPod hack, make sure to turn off your iTunes and keep it from popping up after you've plugged in your iPod via USB. Take a look at this tutorial and learn how to hack into you iPod on your Mac with the program Alterpod. With luck, no error log will pop up ...more
Farm Town hacks, cheats, glitches. How to hack Farm Town. Watch this video tutorial to learn how to Hack Farm Town with Cheat Engine (09/16/09). You'll need Cheat Engine 5.5. Description of the app on Facebook: In the world of Farm Town you and your friends can have a great ...more
This how-to video shows a powerful and effective hack to turn any dust vacuum into a water vacuum. You will need a rubber band, tissue paper, a set of four straws, a pen knife, a soft drink bottle, and a vacuum cleaner. Watch this video tutorial and learn how to modify a regul ...more
Farm Town hacks, cheats, glitches. How to hack Farm Town. Description of the app on Facebook: In the world of Farm Town you and your friends can have a great time! You can play games, design, grow and maintain your own farm and even send gifts to your friends. Play now and sh ...more
Watch this instructional cinematography video to learn a cheap and easy method of creating your own time-lapse footage with a motor controlled hacked clock. This is an excellent way to generate fast forward effects in film (think of the famous scene in Garden State). This is a ...more
Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world! Advanced Per ...more
Making yogurt at home doesn't sound like an easy task at first. We initially saw it as detailed, hands-on, and precise—a process that required special equipment, specialized (and expensive) live-culture bacteria, and loads of yogurt knowledge. But, lo and behold, we discovere ...more
Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer. This part is more involved, but the first ...more
Since its inception in 2007, the Pwn2Own computer hacking contest has been challenging the vulnerability of mobile phones and web-related software. In 2010, the fruit of two full days of hacking came down to the exploitation of the following web browsers: Safari 4 on Mac OS X, ...more
Country Story hacks, cheats, glitches. How to hack Country Story. Watch this video tutorial to learn how to cheat Country Story: dog hack (09/26/09). Needed: Adobe Flash Player 9 Cheat Engine 5.5 Mozilla Firefox Instructions: 1: Open/Accept the "Man's Best Friend" quest 2: S ...more
In this video, we learn how to hack your iPhone 3G. To do this, you will need: iPhone 3G, Firmware 3.0 or 3.1 file, charger cable, and the Redsn0w program. First, connect your phone to the computer and then start up the Redsn0w program on your computer. Turn the phone off, the ...more
As many of you may have noticed, nearly every Google product (i.e. Gmail, Google search, etc.) has gone through a bit of a makeover since the release of Google+. Big blocky buttons and enormous font sizes are apparently the thing of the future, and with a cool JavaScript hack, ...more
Cheat your way to success by using Cheat Engine on Fish World. Nobody makes it in life without a little cheating! Facebook Fish World cheat! In this Fish World video tutorial, see the steps on how to cheat Fish World: Coin and EXP hack (10/29/09). Download Cheat Engine 5.5 ma ...more
Todbot offers instructions for making your own Arduino shifty-googly Halloween eyeballs. Perfect to pop inside a pumpkin or skull. All you need is "3 servo motors, some scary eyes, a few Popsicle sticks and an Arduino". Click through for a detailed How-To, as well as a video ...more
Chrome, Firefox, and Safari all provide built-in features that allow you to save your username and password for your favorite sites, making the process for entering your credentials a breeze when you revisit them. While this automation does make your life a little easier, it ...more
INVedit is an inventory modification program that you can use to hack into your character's inventory when playing Minecraft. Give yourself more items of one time, unlimited resources or whatever else you feel like. Fill a whole island with diamonds or TNT!
For about a buck, you can make a fun Mini-Pinball machine out of a VHS, just follow the steps in this how-to video. This is a great toy for kids, or anyone that wants to make a cheap version of the arcade favorite. Bring the VHS pinball machine into the car to stay entertained ...more
The mighty toaster oven may be the most useful small appliance ever, whether you're a college student who needs to heat up your Bagel Bites or a professional looking for a quick way to warm up a frozen pizza after a long day. But that toaster oven is no one-hit wonder. With th ...more
A little-known setting on your iPhone gives you the power to change the color of certain contact names and email addresses when drafting an email. Customizing the color works well for visually separating contacts at a glance, and it can even help you from sending an email to t ...more
Nintendo's Wii Remote came close, but never has a video game peripheral garnered such adoration from the hacker community than the Kinect. Since the release of Microsoft's controller-free gaming device last November, there has literally been thousands of fun and useful projec ...more
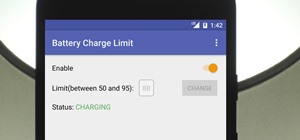
The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac ...more
Friday's Community Byte was weird. The intent was to do a HackThisSite mission, but upon time to begin, everyone in there was programming without my assistance, with the help of Sol Gates. This is great! It's really awesome that everyone enjoys programming that much and will m ...more
Welcome back, my budding hackers! Digital forensics is one of IT's most rapid-growing disciplines. All hackers should be familiar with digital forensics if for no other reason than to protect themselves. More than one hacker has been apprehended because they were unaware of t ...more
Toothpicks can be surprisingly handy when it comes to woodworking and fixing small household problems like stripped screw holes and scratched furniture. They can also be used as a quick fix for a hard-to-close door that has to be forced or slammed shut. Most of the time, a st ...more
This is the Double Pointer Coin Hack for RC. The tools you need for this hack are Cheat Engine 5.5, Adobe Flash Player 9 or 10, Mozilla Firefox or Flock, and Mouse Recorder. Watch this video tutorial to learn how to cheat Restaurant City: Double pointer coin hack (12/12/09). ...more
This musical instrument, coke can ocarina hack is fun & creative (but doesn't really make a nice sounding instrument). Follow these instructions to learn how to make your own coke can ocarina - who knows maybe you can mod this hack into a better sounding instrument. Good luck! ...more
Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information y ...more
In the second part of this tutorial, we are going to crack the hashes that we've captured previously. I'm going to explain how to do it with the powerful John the Ripper. It comes with Kali by default, so no need to install! Using John the Ripper If you don't know nothing ab ...more
Do you own a hacked XBox 360? Do you want to burn some games for it? Well, in this video, the viewers will first be taught how to download games using peer-to-peer software, such as uTorrent. Then, with a combination of software, such as IMGBurn and abgx360, the viewers will l ...more
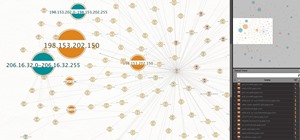
Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we ...more
Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely ...more
Hello! This post is not about craft, it's about cyber bullying. If you ever had such an experience, that an unknown hacker was bullying you for no reason at all, please follow my words. Thank you! Step 1: Let All the People You Know That Your Are Being Harassed. Hacking is th ...more
In this video, we learn how to hack school filters to get on Facebook with Tracert. First, go to the start menu and then type in "cmd" into where it says run. After this, type in "tracert" and then the website name. Wait for all of the information to fill in in the black scree ...more
Want to add a dislike button to your page? Or want to make an update about what you did last night, but don't want your grandmother to read it? This video shows you ten ways you can hack your Facebook page. You can also pre-schedule certain status updates, set your Facebook la ...more
UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, exa ...more
Want to mod your HTC HD2 Microsoft Windows smartphone to use wireless charging—without breaking your warantee in the process? It can be done! And quite easily at that. For complete details, and to get started modding your own HD2 phone to work with wireless chargers, watch thi ...more
Yep, it's that easy. From Re-Nest: "To quiet the sound of a leaky faucet, simply tie a string around the neck of the faucet and allow it to catch the drips on the way down. This will allow your pipes to continue to flow freely and give the water something to cling to. Think ...more
Ikea Hacker features a nice Ikea mod: Romain turns the Ivar side unit into a camera dolly. "A few days ago, I found out that the Ivar 'wooden ladder' was perfect to use it as rails for my cinema dolly! I can now make some nice sequence shots with this 18€ accessory from Ikea. ...more
Corporation, Inc., is a fun game you can get from Armor Games. Like most CEOs, you'll want to be as cutthroat and ruthless in pursuit of profits, and that sometimes means cheating. This tutorial shows you how to hack the game using Cheat Engine.
This is a little xp password cracker I'm going to show you how to get and use. Hack Windows XP passwords with a password cracker. Click through to watch this video on tricklife.com
If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a pro ...more
Hi! In case you missed it, on Reddit is pretty good article about attack on E Corp in pilot episode. Hacking sequence explained : MrRobot.
Learn how to hack your 1.1.2 and 1.1.3 iPhone with Ziphone (zibri) software for Mac or Windows. No technical skills required!
Cheers to another completed Community Byte project! Things went well regarding timeliness and being friendly to the other coders and students. If you've got ideas for our next mission, or an idea for a tutorial, submit them to me. Friday, our mission was to take out HackThisSi ...more
It's a given that if you're driving, you or someone you know has Waze as a go-to on their smartphone. The Google-owned crowdsourced navigation app is one of the best for avoiding traffic, roadblocks, and even cops. But a new academic study and report from Fusion suggest that ...more