The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already bu ...more
This is a how to to change any user password on a windows 7 computer. If you forgot your password you can change any account password even if you are locked out of your account. Warning I am not responsible for any damage done to any computer in the process of this hack or an ...more
This is how to hack a computer for educational purposes. First you need its IP address, radmin viewer 3.3 or later, and an open port scanner. Okay so first you need the IP and scan the IP address of the computer. Now find what open port it has. Ok then open up radmin viewer an ...more
Have you ever noticed that whenever you setup your voicemail account after getting a new cell phone number, it asks you to create a security pin to access your voicemail from other phone lines? When you call your home or cell number from another phone, after a few rings your ...more
Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scann ...more
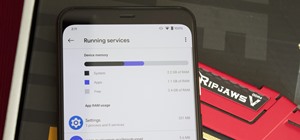
If you're looking to customize your Android beyond its stock options, things can get confusing quickly. One of the best places to get into developer mode is the XDA forums. XDA is home to hundreds of independent Android developers, all eager to showcase their wares. Everythin ...more
Hey guys I am starting this Series because I thought there was a lack of post about Hacking from Android. In This series I will tell you about That your Android can really be used for hacking just like your other systems. So in the first of the many posts I will be telling ho ...more
Whether you live in foggy California or icy Massachusetts, you've more than likely struggled with a cloudy, vision-impairing window that makes even the shortest commute impossible. While you can get rid of fogged up windows pretty easily using your vehicle's defogger system, ...more
Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote co ...more
Trying to focus on studying for your Stats final in the library but getting a serious ADD spell? Then make use of your time - while having a little fun with whoever else is in the library - by hacking into your computer's command prompt. The command prompt is the most basic o ...more
This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/ In this post we will explore more about finding hacked accounts online, w ...more
I'm a pretty nice person, so when someone asks me to take a group picture of their friends or family, I can't easily say "no," even if I have somewhere else to be. Even worse—sometimes I'm the one asking, fully knowing just how annoying it can be. Maybe you've been told "no" b ...more
Applying for jobs can be a truly miserable experience. Sending out endless résumés, filling out those janky online applications, and creating cover letters can really wear a person down. So, any suggestions that make that process easier are always welcome. If you suspect your ...more
Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!) In several episodes, Elliot was seen sending ...more
Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement t ...more
Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open ...more
The closest I've ever been to first class was when I was a young kid running up and down the aisles on a long international flight. I remember being in awe of how big the seats were and how much food was available. Ever since that moment, I've made it my life goal to earn enou ...more
Dispatch your enemies with a single sword strike. This cheater's guide will show you how to smite even the toughest of opponents with a single hit (and a few keystrokes in Cheat Engine 5.5). Hack Ninja Saga. The flash-based game Ninja Saga is role-playing game involving… you ...more
Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker c ...more
This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but ...more
Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend. ...more
In this episode of Hak5, Darren shows us a USB key, dubbed the USB Hacksaw, that instantly and silently installs on target Windows 2000 or higher computers with guest or higher privileges which will monitor USB ports for flash drives and automatically download their contents f ...more
Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms. First, I covered embedding a listener in ...more
After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even ...more
Now you can play old school Nintendo games on your Playstation 3! This tutorial shows you how to add an SNES emulator to your PS3 running 3.55 firmware. It's not difficult, but make sure you don't skip any of the steps.
In this four part video series, learn how to "hack" the LG Rumor/Rumour. In part one, learn the codes you can do, without using the USB cable. Part two and three goes over hooking the phone up to bitpim. Lastly, part four sums up what you will have learned. Again, by hacking y ...more
Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often ...more
If you're new to the Bluetooth hacking world, here's a little background on using Linux BackTrack to hack a Bluetooh device: Linux Backtrack is a Live DVD device that offers security tools - like password crackers - that allow you penetrate networks. Thus, you can penetrate e ...more
This video will teach you how to hack a WEP wifi network on a Mac. You'll need to follow the link, grab the prog and follow the steps. It's not too hard, so give it a try. Remember, stealing is illegal!
Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning ...more
While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Ra ...more
After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking t ...more
You can easily get to level 100 on Happy Aquarium with Cheat Engine. But hurry, before they patch the game. Hurry to level up! Watch this video tutorial to learn how to hack Happy Aquarium levels with Cheat Engine (10/09/09). For all of the details on this Happy Aquarium hack ...more
For Infinity Exists Full Disclosure's first Website Hacking episode, we demonstrate how to exploit a security vulnerability occurring in a website's database to extract password hashes. Sql (Structured Query Language) is a computer language designed for the retrieval and manag ...more
I rarely receive spam mail, but every now and then I’ll get an email from Cat Fancy Magazine. I’ve never read an issue of Cat Fancy Magazine or been to their website. Actually, I’m allergic to cats. So how did they manage to get my information? Well, anytime you register for ...more
Make sure you use FLASH Player 9 First: Deinstall Flash Player 10 -- http://kb2.adobe.com/cps/141/tn_14157.html Second: Install Flash Player 9 -- http://kb2.adobe.com/cps/142/tn_14266.html How to hack Coins & Gourmet points in Restaurant City? Step 1: Let all your employees be ...more
Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities app ...more
Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker. FileVault, created by Apple in 2003, is a hard ...more
Welcome back, my greenhorn hackers! In recent weeks, the Heartbleed vulnerability of OpenSSL has been dominating the information security headlines. This vulnerability enables an attacker to extract data from the server's memory that may contain authentication credentials, co ...more
We've told you how a rice cooker can work as a DIY sous vide machine and make amazing risotto the lazy way, but did you know that it can also make pancakes, bread, mashed potatoes, and poached fruit? Rice Cooker Pancakes Of course, when we say "pancake," it's more like a lit ...more
This video tutorial gives you a way to access websites that you can not normally access because of a web block or filter. What you need to do is click on the ‘Start’ button and then click on ‘Run’. In the small window, type in ‘cmd.exe’; this then opens a black window. Then ty ...more
The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be ...more
Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client. Although the most valuable information to the hacker ...more
There are a ton of cool features available on your Samsung Galaxy Note 2, but if you're a softModder, you can make your phone do just about anything. Therein lies the problem…what do you want from your Android device? When you first start tinkering around, it can be troubles ...more
There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distributi ...more
Welcome back, my greenhorn hackers! Congratulations on your successful hack that saved the world from nuclear annihilation from our little, bellicose, Twinkie-eating dictator. The rest of world may not know what you did, but I do. Good job! Now that we hacked into the malevol ...more
Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial ...more
Food can smell great before, during, and after cooking. A pot of stew simmering away on the stove will tantalize you all afternoon, and there's nothing better than the smell of fresh-baked cookies lingering in the house for hours. One place you don't want to smell food? On yo ...more
Every year I wait until the last minute to wrap Christmas presents. I always tell myself I'm going to get it done ahead of time, but it never happens. And the worst thing that can happen when you put it off is running out of Scotch tape. If you find yourself in this predicame ...more
Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, ...more
Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account ...more
Stuck in the middle of London with only 1p in your pocket? If you're hungry, have lost your "A to Z" and need to know how to get free goodies out of a British vending machine, check this out! In this video, you will learn how to take a 1 pence coin, wrap it in tin foil and tri ...more
How to hack Pet Society! Pet Society cheats, tricks, hacks. Watch this video tutorial to learn how to hack coins on Pet Society (09/23/09). Use Cheat Engine. Hex 1 : 89D068000000C1E9 Hex 2 : D06800000239850F Pet Society is a game that can be played on Facebook. Check Pet so ...more
Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different appro ...more
This how to will show you how to program a fairly simple Hacking bat file. First open notepad. Then copy the text into notpad: REM ============================================================ REM errorcode401.blogspot.in @echo off title Rar Password Cracker mode con: cols=47 ...more
Too little counter space has been the biggest annoyance in every kitchen of every apartment I've ever rented. They've all been either super small or awkwardly shaped, which means choosing between appliances and prep space. You either live with it or learn to adjust. There are ...more
Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can c ...more
With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer. In my last series, we used a Post-it note to trick a neighbor into visiting a website that we cont ...more
Play remotely with all your friends, stream videos and music from the Internet or even check your Facebook and email - all with your PSP. The PSP has Internet capability, but not every network will be available to you at all times. Here is how you can hack any wifi connection ...more