Prepping fruits and vegetables ahead of time makes putting together the final dish a lot easier, but once you cut them up, they start to turn brown almost instantly. However, thanks to this quick and easy tip from America's Test Kitchen, you can keep them looking fresh for muc ...more
Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensi ...more
Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear ...more
Welcome back, my greenhorn hackers! In the first part of this series, I introduced you to the basics of networking including IP addresses, ports, NAT, and DHCP. In this lesson, I want to introduce you to the basics of TCP/IP, i.e., Transmission Control Protocol (TCP) and Inte ...more
cheatengine.org Farm Town hacks, cheats, glitches. How to hack Farm Town. Description of the app on Facebook: In the world of Farm Town you and your friends can have a great time! You can play games, design, grow and maintain your own farm and even send gifts to your friends ...more
Eggs are a staple food for most Americans, which is no surprise, considering how necessary they are in savory and sweet recipes alike. On their own, they're usually not too eggs-citing. However, these clever egg hacks will make your egg-making easier, more fun, and more intere ...more
Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know. Possibly the most popular and well-known reconnaissance tool currently ava ...more
Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful prac ...more
Who am I? First let me introduce myself. I am Th3skYf0x, an -well lets call it experienced- hacker and i recently found this site and right after that i found this Null Byte "world" soo i thought... Why not teaching instead of doing nothing with my knowledge. Let me get one ...more
OK, you've played through GTA IV many times and you're looking for a new kick. Check out this video and see what sweet mods you can apply to take this awesome PS3 game to a whole new level. From weapons, to vehicles, colors, characters, physics and more, these mods will let yo ...more
General Electric isn't known for their Christmas lights, but maybe they should be, because their GE Color Effects are pretty awesome. Especially the LED Color Effects G-35 String sets. And especially when someone named Darco hacks them. Darco, whose real name is Robert Sun Qu ...more
Welcome back, my aspiring hackers! One of the areas that often gives Linux newcomers problems are the environment variables. Although Windows systems have environment variables, most users, and for that matter, most administrators, never manage their environment variables. To ...more
RuneScape hacks, cheats, glitches. How to hack the flash game RuneScape. Watch this video tutorial to learn how to hack RuneScape with Cheat Engine (08/31/09). Description of the app on RuneScape: RuneScape is a massive 3d multiplayer adventure, with monsters to kill, quests ...more
The USB Rubber Ducky is a well-known hacking device in the cybersecurity industry, but it needs to be preprogrammed before it can be used. That means it's not easy to issue commands to a target computer since you can't interact with it from afar after plugging it in. And if yo ...more
How to hack games on a Mac using iHaxGamez. This is useful for any of the facebook/myspace games. How to hack flash games, using a Mac. Recently, Household hacker made a tutorial on how to do this for PC, I thought I'd show the world how to do it on a mac. iHaxGamez Commando ...more
You will need to have the most current version of Cheat Engine and Minecraft Alpha running on your computer. When you are running Minecraft, open up Cheat Engine and use the video to hack the game so you can duplicate as many inventory items as you would like.
The build.prop file in an Android device is home to many system-level values and settings. Everything from screen density to video recording quality is covered in this file, and people have been editing these entries to get new functionality and better performance since Androi ...more
This is the second episode of Full Disclosure by InfinityExists.com. This episode includes how to crack WEP encryption, and why it can be cracked so easily.
Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers w ...more
Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?) There is no better telltale sign of a script-kid ...more
Pop-Tarts are a pretty iconic breakfast food. And while I'm more of a bacon, eggs, and toast person myself... sometimes a sweet, gooey, artificially-flavored treat is just what you need in the morning. Yet, despite the fact that I do enjoy Pop-Tarts, I've always found them a l ...more
Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record. OTR does all the right things to make your instant messa ...more
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started. OVERVIEW: As you'll get further into the hacking community, and learn more about how it's all put together, you'll also realize very quick ...more
Anything free is cool, but getting a fully upgraded operating system for the great price of nothing is downright awesome. A recent exploit was uncovered that allows users to get a free copy of Windows 8 Pro directly from Microsoft's own website. Seriously. As I wrote in an ea ...more
Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private ...more
Last Friday's mission was to accomplish solving HackThisSite, realistic 1. This is the first in a series of realistic simulation missions designed to be exactly like situations you may encounter in the real world. This first mission, we are asked to help a friend manipulate th ...more
If you thought humans were reading your résumé, think again. Robots do, and their one solitary objective is to systematically crush the hopes and dreams of those who don't make the cut. Instead of paying a few humans to read thousands of résumés over a couple weeks, many compa ...more
Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner. The banner is simply the application advertisi ...more
Welcome back, my nascent hackers! One of the many reasons I write this blog is to help you keep the Internet free and open. Throughout human history, whenever a government or other powerful entity has wanted to subjugate a people or group, the first thing they do is isolate t ...more
XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection betwe ...more
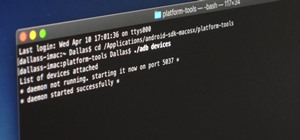
It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no mat ...more
Welcome back my fellow army of hackers! Today we'll be hacking a website. Hacking is technically not the right word used here. It should be defacing! So we are going to deface a website... What's Defacing? Website defacement is an attack on a website that changes the visual ...more
Welcome back, hacker novitiates! In the next few hacks, we will be breaking into Windows servers. In this installment, we will learn to add ourselves as a user to a Windows 2003 server. Of course, when we have added ourselves as a user, we can come back any time and simply log ...more
Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to hack Wizard101 money with Cheat Engine (09/27/09). 1. Log in to your account 2. Go to any shop 3. Open Cheat Engine 5.5, go to Wizard101 4. Put in the am ...more
This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the ser ...more
Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see wh ...more
The cell phone has come a long way. The very first "mobile devices" were made and used by the military in the late 1930s, with the first commercial mobile telephone service introduced by Bell in 1946. These devices were hardly what we'd call mobile today—some took up the whole ...more
It's a common misconception that iPhones are impervious to cyberattacks and "more secure" than Android. And when an iPhone does get hacked, it's nearly impossible to tell that it happened. Vulnerabilities in iOS are common, and Apple tries to tackle them with each security up ...more
Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or se ...more
Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity! Social Eng ...more
Bejeweled Blitz is a Facebook game. Learn how to hack Bejeweled Blitz with tricks, cheats, hacks. Watch this video tutorial to learn how to hack Bejeweled Blitz with Cheat Engine (07/25/09). Description of the app on Facebook: Bejeweled + Friends = Prizes! Play this special ...more
Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do t ...more
Can't seem to win at the craps tables? How about any other dice game? There are a ton of fun dice games out there, but rolling the number you need to win is pure luck, or is it? In craps, it good to roll a 7 each time, any you can roll 7 every time, but first you need to hac ...more
Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having ...more
Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc. Any time someone's computer seems to act ...more
If you've got an iPhone or iPod touch and are looking to hack Bluetooth, check out this video and see how it's done. You'll need your Apple devices to be jailbroken already so make sure you do that step first.
Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks. The goal of this project was to locate a known and easily detectable macOS payload, then ...more
Believe it or not, people are still using Friendster. Which is great news for all you hackers because that means there are accounts to hack! With this video you'll find out how to exploit a programming loop hole in order to hack into someone's Friendster account. We can't prom ...more
Just like Leslie Knope, I love waffles. Unlike that imaginary character, I don't require that my waffles come from JJ's Diner. I have a deep affinity for frozen waffles as well as the homemade ones. They're so convenient! A few moments in the toaster, and you have a great foun ...more
Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life. Imagine arriving home one night after work and there's a Post-it note on your apartment door with the website "your-name- ...more
This is a super easy hack that you can use to get as much money as you want when you're playing the hit indie game Plants vs Zombies. All you'll need for this hack to work is to make sure your computer has both the game and Cheat Engine installed.
This video tutorial is in the Computers & Programming category which will show you how to hack a wireless network with WEP encryption. This video is intended only as a means of testing the security of your own network. Go to Backtrack Linux, download the backtrack4 and burn it ...more
Last Friday's mission was to accomplish solving HackThisSite, realistic 3. The third mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend restore a defaced website about ...more
Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins. In this attack scenario, a malicious c ...more
Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, w ...more
Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elli ...more
Cooking spray is something of a gross necessity. The slimy, oddly-scented grease is perfect for keeping casserole dishes crust-free, but the oil splatter does a number on clean kitchen counters, and the lecithin ingredient can ruin nonstick cookware if not careful. Despite th ...more
Welcome back, my novice hackers! In my continuing effort to develop your Linux skills, I now offer you this eighth in my series for Linux Basics for the Aspiring Hacker. In this tutorial, we'll look at system processes and how to manage them. In Linux, a process is a program ...more
Hack Yoville with the coffee glitch (12/23/08). How to hack Yoville! Yoville cheats, tricks, hacks. Yoville is a game that can be played on Facebook or MySpace. In the words of Yoville's Facebook app, YoVille is a world where you can buy new clothes for your player, purchase ...more
This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with l ...more