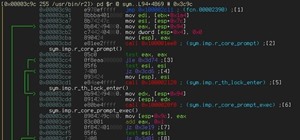
After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking t ...more
There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take c ...more
While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatic ...more
If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them ov ...more
Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer. This part is more involved, but the first ...more
A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us ...more
Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?" As the hacker is among the most skilled information technology disciplines, it requires a wide knowledge of IT technologies and techniques. To truly be a great h ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. More amazing community contributions this w ...more
This is a two-part series to locking down the computer to provide maximum protection. Even though this guide will sound intrusive, we are talking about reality here. Extreme measures must be taken to protect our computers, especially when we have confidential documentation or ...more
Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three! Each anonymity network is designed for a different specific purpose. One network al ...more
Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive. End ...more
A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, m ...more
What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, ...more
Gmail has been the email standard for quite some time now, and for good reason: it's a free service provided by one of the largest tech companies in the world that offers users an amazing feature set to manage, send, and keep track of all their important emails. However, all ...more
Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking. Before I begin, I want to re-emphasize to all of y ...more
If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for ...more
In most cases, when the free trial of software is over, that's it—you're left to either pay for it or find an alternative. But what happens if the trial wasn't long enough to sell you on the product? It'd be nice if there was a way to test it out again without having to whip o ...more
For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been ...more
Welcome back, my greenhorn hackers! As all you know by now, I'm loving this new show, Mr. Robot. Among the many things going for this innovative and captivating program is the realism of the hacking. I am using this series titled "The Hacks of Mr. Robot" to demonstrate the ha ...more
RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices. I initially covered RouterSploit on Kali Linux and macOS (OS X), but this tuto ...more
Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy. Many beginners come here looking t ...more
There are a bunch of new and interesting features packed inside of Windows 10, but one of the most exciting ones is the Microsoft Edge web browser, the long-awaited replacement of Internet Explorer. While the "e" icon that you know so well will remain the same, albeit with a ...more
Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to ...more
Apple's successor to the iPhone X is a beautifully made smartphone with much of the same characteristics, including a 5.8-inch OLED screen, two storage choices, and Face ID. But many features set the iPhone XS apart from its predecessor, as well as the other 2018 lineup of iPh ...more
Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target. Thanks to a pair of recon tools coded in Python, it takes just seconds to research how a website or server might be vulnerable. No matter what platform ...more
Welcome back, my aspiring hackers! Those of you who've been reading my tutorials for some time now know that I am adamant regarding the necessity of learning and using Linux to hack. There is no substitute, period. In this tutorial, though, we will be setting up a system to ...more
Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private ...more
An attacker can create three, five, or even ten new Netcat connections to a compromised MacBook with one command. Performing complex post-exploitation attacks might otherwise be difficult from a single shell without this essential trick. Why Create Multiple Netcat Threads? W ...more
Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn fro ...more
Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with. Wardriving has been around since the '90s and combines GPS data and Wi-Fi signal data to create accurate, in-depth maps of any nearby Wi-Fi networks ...more
Kali Linux has come a long way since its BackTrack days, and it's still widely considered the ultimate Linux distribution for penetration testing. The system has undergone quite the transformation since its old days and includes an updated look, improved performance, and some ...more
As we've seen with other tools and utilities, administrators typically use certain things to do their job more efficiently, and those things are often abused by attackers for exploitation. After all, hacking is just the process of getting a computer to do things in unexpected ...more
Signal is one of the best end-to-end encrypted messengers on the market. It offers robust security, keeps minimal information about its users, and is free to use. Switching to it as your main messenger can be a bit daunting, so to help, we created a guide to walk you through t ...more
If you have a PlayStation 5 and an Android phone running Android 12, you can stream and play your PS5 games right from your mobile device using PS Remote Play. While simply pairing your PS5's DualSense wireless controller with your phone will give you the basic controls to pla ...more
If you've spotted an unintended Ethernet connection and wondered what you could do with all of the information coursing through those wires, there's an easy way to hack into it and find out. Let's say there's a router that we need to know the password for, and we have physica ...more
In the 21st century, we're all looking for ways to stay private, especially on our electronic devices. We have big tech corporations, enemy countries, malicious hackers, and other prying eyes watching our every move, so it's only natural to want to limit what they can see. Mak ...more
Have you ever been locked out of your iPhone? Maybe you forgot your passcode. Or perhaps someone with access changed the passcode as a prank. Your iPhone's display could have even been damaged and unresponsive. Whatever the reason, there's an easy way to get back access to you ...more
Google's much anticipated eBook Store has finally opened. As of today, the digital bookselling enterprise is awaiting your needs, with over 3 million eBooks to read directly on the web or on other platforms, like Android, iPhone, iPad, Sony and Nook devices. And the best part ...more
For me, the idea of a smartphone with internet access was overkill for a cell phone. Wasn't that what my computer was for? Do I really need immediate access to the web? Must I update my Facebook every hour, from the palm of my hand? Do I need turn-by-turn directions from Googl ...more
This video tutorial demonstrates a mouse-hacking simple prank sure to annoy any friend or colleague. To replicate this hack, you'll need a mouse and a musical key chain. The steps are roughly as follows: First, open up the mouse. Looking inside, find and remove the scroll whee ...more
No website will be inaccessible and no web filter will deny you content once you learn the skills presented in this internet hacking video. In this tutorial you'll learn how to access blocked websites as well as to bypass web filters using URL scripting, HTTP proxies, and a w ...more
The Lesser Evils side quest is accessible immediately after completing the factory hostage mission at the start of Deus Ex: Human Revolution. This Giant Bomb tutorial will take you through the mission, which involves breaking into an apartment building complex and hacking into ...more
In this installment from the Unorthodox Hacking series of computer security videos, you will explore a few of the areas in Windows that most Sysadmins don’t even know exist. See how to become Local System through the Task Scheduler and abuse long filenames. Take a look at some ...more
With iTunes, you can listen to the radio over the internet and hear broadcasts from around the world. Make sure your computer is connected through the internet, then click "Radio" in the source list to see the internet radio stations available through iTunes.
WonderHowTo is a great place to find advice and learn things that you want to know, but can't find anywhere else. On this website, there are tons of people who make articles and videos to show you how to do stuff. In this tutorial, you will learn how to make your own WonderHow ...more
This video instructs the viewer about the basics of cloud computing, using more than one computer and managing your computing needs online. The instructor explains, "Cloud computing is a metaphor for using the Internet for your computing needs." A program called cloudo, allows ...more
If you have an Android-based cell phone and want to tether it to your MacBook, MacBook Pro, or other computer running Mac OS X software, the secret lies in a little application called PdaNet. Watch this video tutorial to see how to download PdaNet to both your Android phone a ...more
An explanation of how to get access to your Linux desktop from any other computer connected to the Internet.
In this tutorial, learn how to make a heart on your computer for such social Internet sites as MySpace and Facebook. It's very simple! Show your friends you care about them with this decorative love bonus!
My girlfriend was going away for a few weeks, but where she was going, there was no easily accessible Internet. She works mostly on the web, so it was imperative that she have a decent Internet connection during her travels. So, tethering her phone was the only real possibilit ...more
Anyone can set up their own wireless network. All you need is a little know-how. You will need a computer with wireless capability, a high-speed modem, a wireless router, and a broadband internet connection. Don't get tied to the wall; a wireless connection will allow you to m ...more
Palladium Pro is one of the newest rogues making it's way around the internet, posing as antivirus software and then infecting your computer with all sorts of nasty malware. This video will teach you three different ways of removing Palladium Pro from your PC completely and ge ...more
Here is a video tutorial showing how to take movies from your lap top or computer and play them on your HDTV using the internet.
Welcome to the information superhighway! In this BrainPOP movie, Tim and Moby will teach you all about the Internet and how it works—from what an ISP is to how emails get from one computer to another! Teach kids about the internet. Click through to watch this video on yahoo.com
The mouse is the primary tool most people use for accessing their computer and the vast stores of information on the Internet. Wouldn't it be funny if instead of allowing you to click icons on the computer screen, your mouse just lit up and made noises when you pressed it butt ...more
One of the cool things in Windows 7 is the new start menu. It is now possible to add an internet search area to your Start Menu. Instead of searching your computer, you can select a separate option called Search the Internet. This video shows you how to enable and operate thi ...more
What is DansGuardian? Schools, offices and universities often tend to use a software like DansGuardian to prevent people from accessing certain websites - websites like Youtube, Facebook, Myspace, and so on. However, if you ever find yourself in a situation where you need to ...more
Want to be able to print wirelessly without having to buy a pricey network printer? Now you can! All you need to do is follow these simple, quick, steps. What you need: At least two computers running Windows Normal non-network printer A network Once you have all of these th ...more
Looking a way to share a wired Internet connection? With an Apple computer, it's easy! So easy, in fact, that this home computing how-to from the folks at CNET TV can present a complete (and somewhat talky) overview of the process in just under a minute's time. For the specifi ...more
Interested in hacking the power button on your Windows PC to put your computer to sleep instead of shutting it down? This Windows 7 tutorial will show you how it's done! It's easy! So easy, in fact, that this home-computing how-to can present a complete overview of the process ...more