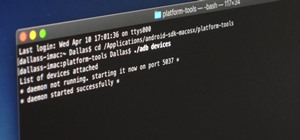
Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigator ...more
If you have never heard of a Virtual Machine (VM) before you might think it to be some new kind of gamers virtual reality system, and that would be incorrect. A virtual machine is a Virtually a real computer that exists inside of your own computer. You can run Kali inside of a ...more
We recently showed you 8 menu bar apps that ever Mac power user should have, covering apps that allow you to control iTunes, eject drives, organize screenshots, and more—all from that tiny strip at the top of your screen. But when it comes to the menu bar, we only began to sc ...more
Welcome back, my apprentice hackers! As many of you know, I have been hesitant to adopt the new Kali hacking system from Offensive Security. This hesitancy has been based upon a number of bugs in the original release back in March of 2013 and my belief that BackTrack was easi ...more
For those needing to replace old controller hardware on cutting mills, those into native retro gaming, or for those who want to see what all the fuss was about in the 1980's, or for those who just want a play with old but great technology, this tutorial shows you step-by-step ...more
If you have a broken laptop computer, but the hard drive still works, this video will show you how to access and remove your old photos, pictures and files. Video: .
Led infinity mirror that I make with some materials like mirror from old hard drive,leds,plastic mirror sheet and battery holder. Video: . Make sure you subscribe for more awesome videos from the macobt projects! Subscribe to my YOUTUBE channel:http://www.youtube.com/subscrip ...more
Converting Movies To Psp Format. Hey again, this is a real quick guide for anyone interested to get a movie onto there PSP without all the fluff i have seen elsewhere. I just watched Africa the Serengeti on my PSP and heres is the lowdown. Movie - approx 40 minutes - dvd Sav ...more
If you have a Mac, you've probably been anticipating the release of OS X Mountain Lion. If you have multiple Macs, you've probably been dreading the long process of downloading and installing it on all of them. Here's how to create a bootable backup disk and save yourself some ...more
Microsoft's first venture into the tablet market, the Surface RT, combines many of the capabilities of a normal Windows 8 laptop into a super compact tablet, whose super-thin touch cover and kickstand can transform it into a functional mini-laptop, small and light enough to go ...more
Windows 10 and macOS have poor reputations when it comes to customer privacy and user policies. Our hacking Windows 10 and hacking macOS articles might make it seem like a reasonably secure operating system doesn't exist. But I'm here to tell you that there is a viable alterna ...more
While still extremely awesome, the Samsung Galaxy Gear smartwatch is limited as to what you can download on to it, especially apps. It also doesn't have its own internet access (only Bluetooth), so apps like Instagram, Facebook, and Vine have yet to make their way to the Gear ...more
If you're an Android user, Google probably has almost your entire digital life stored on its servers. Family pictures are backed up on Google Photos, your e-book library resides with Google Play Books, videos are on YouTube, chat logs in Gmail and Hangouts, starred places and ...more
Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, ...more
The Files app received a big update in iOS 13. Before, it was limited to local and cloud-based files, but now you can access data from external storage devices, including SD cards and USB drives. But before you try to connect your favorite card or drive to your iPhone, there a ...more
The new iOS 10 won't be released to the public until September 13 via an OTA update, but the Gold Master edition is available right now. Essentially, it's the same version that Apple will release on the 13th, but only for developers so they can get their apps up to snuff befor ...more
Finally! A media box that gives you everything you want, in one tiny package. The EzeeCube will allow you to view your pictures and videos while staying organized at the same time. Video: . You can add more storage by simply stacking another EzeeCube hard drive on top. Need a ...more
Welcome back, my budding hackers! In my continuing series on Linux basics for aspiring hackers, I now want to address Loadable kernel modules (LKMs), which are key to the Linux administrator because they provide us the capability to add functionality to the kernel without hav ...more
Like a computer, your brain can store and process large amounts of information. It can remember names, solve math problems, and save tips that you might need at a later time. Unlike a brain, though, computers tend to collect information that might not be important. Not only t ...more
It might be time to move those Instagram photos to another service. It seems that Instagram has never heard of the phrase, "If it ain't broke, don't fix it." In a very big WTF moment, the extremely popular photo sharing and editing app decided that it has the right to sell its ...more
When you don't have a steady cellular signal or immediate Wi-Fi access but need to communicate with others around you, you can set up an off-the-grid voice communications network using a Raspberry Pi and an Android app. There are apps such as Bridgefy that will create a mesh ...more
Greetings my fellow aspiring hackers, Its been a long time and I have to confess I would not be around for long as I am not free yet. I just have some few hours to spare and decided to help out. I learnt OccupyTheWeb won't be around to help out anymore which is like a slap in ...more
Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here. As the Archwiki states: Systemd is a system and service manager for Linux, compatible with SysV and LSB init scripts. systemd ...more
While Windows 10 is still a few weeks away from a public release, that doesn't mean you can't enjoy its brand new features right now. Anyone with an Insider Preview account can install Windows 10 on their computer. And that doesn't just go for those that own a Windows PC—Mac u ...more
Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available. Metasploit enables us to use pre-written exploits against known vulnerabil ...more
In this Windows 8 Tutorial you will learn how to disable automatic maintenance. Their are really two situations I can think of when you would want to disable automatic maintenance in Windows 8. The first being if your Windows 8 computer came with a Solid State Disk then you wi ...more
Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you. Rooting allows you to remove barriers and open Android to a level of unprecedented contro ...more
At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher. Previously: How to Create a ...more
Have a PC but hate Windows? Maybe you've just heard a ton about the new Mountain Lion OS X and want to see if it lives up to expectations. Either way, you can install Mountain Lion on your Intel-based PC in a few easy steps. All you need is a copy of the OS X and an 8 GB USB f ...more
Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary fl ...more
Having a flash drive is more or less a must, but the biggest downside is that they often get stolen, and it's not hard to figure out why. They're small, so they easily fit into pockets, and a lot of people store valuable information on them. Want to pretty much guarantee no on ...more
Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exi ...more
Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks. The goal of this project was to locate a known and easily detectable macOS payload, then ...more
For modders, there are few tools more important than TWRP. TeamWin's custom recovery makes flashing mods like Magisk, Xposed, and custom ROMs incredibly easy, and it lets you root your phone at the press of a button. On top of that, it can make complete backups of your phone i ...more
A.E Hi again this is my second post on nullbyte. The first one was on how to make a remote screenshot captor, now I will give you a presentation for a project of mine(I have named It Antisocial Engine) that It is not something extraordinary but will help many guys. It is a g ...more
It sounded great on the surface when Microsoft announced that existing Windows 7 or 8 users would be able to upgrade to Windows 10 for free, but the execution so far has left a lot to be desired. Upgrading from an existing installation is relatively easy, but when you start wi ...more
Google makes backing up your contacts, messages, and Wi-Fi passwords extremely easy, but leaves you out in the cold when it comes the data on your internal storage. With most Android devices now lacking SD card support, when you unlock your bootloader or do a factory reset, yo ...more
Most of us have traded our desktop systems for laptops, tablets, and mobile devices, meaning there's a lot of outdated hardware sitting in attics. Want to give your old computer a new purpose? Matthew Chappee turned his iMac G4 into an HDTV using the guide by Dremel Junkie. On ...more
A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts f ...more
It seems like every cloud service out there is offering tons of upgrade options and free promotions to give people as much space as they need to store their files online. I personally have over 100GB of Google Drive space which is shared between multiple computers, phones, and ...more
I love my MacBook Air, but the fact that it runs on only 128 GB of flash storage causes me to move most of my files to the cloud. I don't mind having to be connected to the internet in order to access my files, but it's definitely a hassle trying to figure out which files I sh ...more
With an Android device left at its default settings, your location history is automatically recorded. You can view and manage this data, but the simple interface of points plotted on a map leaves a lot to be desired. Developer Theo Patt realized this, and created a tool that ...more
The National Transportation Safety Board (NTSB) said it is still investigating the circumstances of a fatal Tesla crash last year to determine if the car or Tesla's Autopilot driverless system was at fault, but revealed more details about the circumstances of the crash. The m ...more
So yeah. Its AugustFackYou and I felt like posting today and being an active member of the community. After reading this please tell me if you have any comments on what I can do better or if this method is bad. Anyway today I will be showing you how to get root on a mac. I man ...more
Sideloading apps on Android is incredibly easy—you just have to enable "Unknown sources" in your device's Security settings, then you're free to run an APK installer file to get the app installed. As simple as that sounds, the trouble comes when you're trying to find an APK t ...more
Converting files from one format to another can be a pain. Sometimes you have to download software that you'll only end up using once. Other times you have to use a shady third-party conversion site that's riddled with ads. Not to mention that after a while, unless you're extr ...more
Getting things done isn't easy when you're bombarded with alert sounds and notifications all day long on your Mac. Here's how you can quickly remove those distractions with just a single click. Step 1: Download the Automator Apps This part is pretty easy. Just click here to ...more
Automator takes the work out of common repetitive tasks in Mac OS X. One of my least favorites is resizing images for the web, so I created a drag and drop action to quickly do it for me. Step 1: Download the Automator App This part is pretty easy. Just click here to downloa ...more
Hello everyone. The red ring of death of Xbox 360 has been a huge problem since the beginning of Xbox 360. Many gamers like me have faced this problem and the red ring of death (RROD) is one of the biggest reason behind all the rant on Xbox 360 gaming console. Now, I cannot h ...more
Popcorn Time is an app that streams movies directly from torrents on to your computer, and it's seen its fair share of publicity, being lauded as a free Netflix alternative and chastised as an illegal file-sharing network. After a brief legal scuffle influenced the original d ...more
Fingers are very useful for many things in life—but fingers get dirty. With most smartphone and tablets using touchscreen technology, our fingers have become our greatest technological asset. But if you want to keep your phone or tablet from looking like this: Then you can try ...more
If you use Ubisoft's uPlay browser extension, you should probably get rid of it right now. An Information Security Engineer at Google discovered that the plugin has a hole in it that allows programs to be installed through uPlay, essentially letting anyone who feels so incline ...more
There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distributi ...more
If you read my previous post, "How to Hack into a Mac Without the Password", you know that it is very easy to break into someone's Mac if you have physical access to the computer. Now the question that lies is, how do we protect ourselves from this happening to us? Well, here ...more
Welcome back, my novice hackers! In a recent tutorial, I showed you how to use shikata_ga_nai to change the signature of a payload to evade detection by security devices (firewalls, IDS, etc.) and AV software. Shikata_ga_nai is an encoding module in Metasploit that XORs the ...more
Windows 10 is due to be released on July 29th, and the majority of existing Windows users should be eligible to upgrade to the newer version for free. But there's been a lot of confusion about which older versions of Windows will be eligible for the free update, and some unce ...more
It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge. Continuing with our situational awareness attacks, we'll be further orie ...more
While photography usually gets all the love, our phones have gotten really good at capturing video. Think about it — when was the last time you needed a camcorder for a vacation? With mobile cameras getting better each year, we're now at a point where smartphones can be used f ...more
In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that A ...more
Piracy, it can be argued, is the scourge of the internet. But when it comes to music, sometimes it's best to give a listen to a track or album before deciding to spend your hard-earned money on fully supporting it. Unfortunately, there are few good ways to do this without exp ...more