This educational safety video is geared toward public and private utility workers and linemen who need to remove pole tops while dealing with high-voltage electrical cables and electrical insulators. It discusses the proper pole topping removal procedure and demonstrates effec ...more
In 1999, Robin Williams starred in Bicentennial Man, a movie in which Williams played a robot named Andrew Martin, taking care of a family as a their nanny and personal assistant. For almost 15 years, I have waited for my Andrew Martin, but until now, I have been disappointed. ...more
No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from ...more
In Photoshop-speak, we call them faux-tographs. Michael Shermer presents this lesson in falsehoods as a children's craft project. Just tie up some kitchenware to an old fishing pole, flash the photo and ta-da! There's your err... evidence! Believer or not, there's a remarkab ...more
The two-handed sixteenth note drum beats featured in this lesson are a little different than anything covered in previous lessons. Unlike the regular sixteenth note beats, these patterns have the hands alternating between the hi-hats and snare for the entire measure.
Fourth of July is coming up this weekend, and if you consider yourself any kind of patriot (and also happen to love crafting) then you're no doubt going to be honoring the all-American holiday with crafts festooned with vestiges of red, white and blue. Finish up a knitted Ame ...more
This video shows how to start a continual round in single crochet, half-double crochet and double crochet. The photography on this video allows you to see the motion of the crochet hook and the thread and really see observe the techniques as they are explained. Techniques are ...more
Levon Helm... The longtime drummer for The Band , Levon Helm wore many musical hats throughout his long career, including multi-instrumentalist, songwriter, singer, impressario, studio ...more
Emily and Martha carve a pumpkin flower vase. Pumpkins wear many hats this time of year, appearing in pies and soups as well as in centerpieces. Here's another use: Transform one into a colorful homemade vase. Make a pumpkin flower vase. Click through to watch this video on ma ...more
In this video series, our expert Patrick Sapia will show you how to set up a drum set or drum kit. Mr. Sapia will show you how so set up a bass drum, a bass drum pedal, the tom tom stands, the cymbal stands, and the hi hat stand. He will then teach you how to mount the cymbals ...more
Summer is just around the corner, and though many of us are going to dash out of our schools in relief and joy and then head straight out the pool in our skimpy bikinis, we should be covering up with sunblock and hats to prevent noxious nasties like cancer. Wrap your child's ...more
This is one of my previous posts that was initially rejected by WHT. So I'll post it here: Okay Flyers fans, it been way too long since the Flyers have won the coveted Stanley Cup. The cup belonging in Philadelphia is long overdue since its visit in the 73-74 and 74-75 season ...more
This video explains how to keep a dog calm and to be less reactive to objects that it is not used to including baby strollers, hats, canes, and a few other items. Starting with a few tips on how to get a dog used to the item in question such as keeping a leash on the dog and f ...more
French berets are here! Instead of just one winner for the poetry contest there will be two winners. The first place contestant will receive a brand new Khaki Kangol Wool Beret Hat! The Second place winner will receive a Brand New J Hats Black Beret Hat! Make sure to submi ...more
General Tips for Exercising in the Heat -Schedule workouts for the cooler times of the day. -Allow overweight, out of shape or unacclimated kids time to acclimate to the heat. -Schedule timed water and rest breaks every 30 minutes during activities. During these breaks, do ...more
These amazing reworking of the tron and tron legacy posters are the creations of this design master. Hats of for the great work, keep it up and please post your future creations here.
So the Big Surprise News of today is that The King's Speech is Kicking Major Nomination Ass with twelve count-em 12 nominations, just brutalizing stuff like The Social Network (eight - nice try), The Fighter (seven - really? seven? that's the best you can do idiot movie?) and ...more
When a migraine strikes, it can be crippling. Intense and sharp pain not only at the temples, but radiating throughout the entire head; feelings of nausea and digestive discontent; an unbearable aversion to light, sound, and even the smallest of movements. Instead of succumbi ...more
Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat. Most Linux distributions are highly c ...more
Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions. Second i want to say sorry for the series i left in stand by m ...more
International, T-Mobile, and Verizon customers all share something in common—their carriers provide unlocked Wi-Fi tethering for free. Of course, you still pay for the data used, but they don't charge you extra simply for using your Samsung Galaxy S4 as a wireless hotspot. Ho ...more
Thrift stores! As a Steampunk, they can be your best friend, but it's easy to make a tragic mistake. This hands-on guide will help you navigate the murky waters of successful thrifting in order to find the hidden gems that will make your Steampunk outfit complete! Thrift Stor ...more
Your iPhone goes with you pretty much everywhere you go, and unless you have unlimited data on your cellular plan, you've probably connected to dozens of Wi-Fi hotspots over the years. Wi-Fi passwords are saved to your iPhone so you can auto-connect to the router or personal h ...more
JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicio ...more
As 2009 comes to a close, the Telegraph presents a compilation of this past year's wackiest inventions. As always, here at WonderHowTo, we are inspired and impressed by ingenuity. The contraptions below range from utter silliness (engagement ring bra) to downright amazing (see ...more
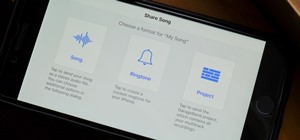
The next big iOS version for iPad, iPhone, and iPod touch was revealed by Apple at WWDC 2018 and dropped for everyone on Sept. 17, 2018, less than a week after Apple revealed the new iPhone lineup. We've rounded up all the big picture items and secret features and changes we c ...more
It used to be that you only had to worry about maids rummaging through your belongings in your locked hotel room. But now anyone with 50 bucks of hardware and some programming skills can hack their way in—as long as it's locked by keycard. At the Black Hat security conference ...more
Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial. THC Hydra is very prominent online brute-force tool and ...more
Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called ...more
Greetings my fellow hackers. As you may have noticed by my lack of posts, I've been away for a while working on a big project with a team (which won't be finished anytime soon), and I have also been putting together a small side project for Null-Byte that I will be announcing ...more
Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network. Whe ...more
Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System ...more
A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data. The ...more
We've talked about the deep web before, but we never really covered the details of what's out there. It occurred to me that a nice list of resources would be very helpful to all of you anons out there. Think of this like a helpful brochure to the hidden web. However, I should ...more
Apple's Siri is well-versed in the spells of the Wizarding World of Harry Potter, but it's not like Android users are Muggles. Google Assistant, Android's virtual concierge, can cast a few spells out of the box, and it can learn the spells it doesn't know quicker than a year o ...more
There's only three weeks left until the spookiest holiday of the year, which means stores and costume shops everywhere are bringing out their Halloween inventory full force. So now's a good time to start prepping your Halloween costume—because you really don't want to do it la ...more
Aside from the second-generation iPhone SE, all new iPhone models since the iPhone X have had Face ID instead of Touch ID as the biometric authentication technology. While Touch ID can be touchy, Face ID is not without its own issues. If you can't get Face ID on your iPhone to ...more
If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs ...more
For your next dinner party, impress your guests with some intricate-looking, but actually super-easy, napkin origami when you're setting up the table. The rosette fold is ridiculously easy and would probably work well for a Mother's Day brunch or an outdoor garden party. Simp ...more
Do you have a beanie and just can't figure out how to wear it? Then this video is the right one for you! With this, we learn how to wear a beanie 18 different ways! The first way is to wear it flat on your head. Or you can wear it as a fedora. A girl can wear it with her bangs ...more
It's that time a year when winter storms begin causing havoc across the United States, and when "rotating outages" are common to help sustain the electrical grid during intense cold periods. That means pretty much anybody with snow and ice in their backyard can succumb to powe ...more
As strange as it may seem, the Hustle "Wobble" is actually a form of line dancing. But rather than tossing your cowboy hat on and your boots for an old West rendition of the Cowboy Boogie, the Hustle Wobble is more about shakin' what your mama gave you and getting down with yo ...more
Google has added some fun Easter eggs to Hangouts that'll give you a few more ways to procrastinate throughout your day. All of them (except for one) work on the web browser version, the Chrome app, and the mobile apps for Android and iOS, and are activated by sending a specif ...more
Hello, fellow grey hat hackers and aspiring coders. I'm back again with another python tutorial. Just that this one is gonna be a lot cooler ;-). We gonna make an encryption program, that well you know encrypts all the files on your pendrive or hdd or whatever you want....Also ...more
Snapchat popularized personalized stickers for social media and messaging with Bitmoji, followed by walled-garden versions from Apple with Memojis and Samsung with AR Emojis. Even Google has gotten into the game, integrating an emoji generator for Gboard. Finally, Facebook ha ...more
The art of disguise is a very important skill to master, no matter if you're a hounded celebrity trying to ditch the paparazzi or just someone who'd like to step out of the house without being recognized. If you think simply throwing on sunglasses and a hat is a good disguise, ...more
A couple of months ago at the Black Hat security conference, hacker Cody Brocious gave the hotel industry a nasty surprise when he figured out how to hack the locks made by Onity that are used in millions of hotels worldwide. The reason his hack is so impressive is because it ...more
Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks. Sparta, authored ...more
Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam wi ...more
Hello, multicolored-hat hackers! Today I am going to show you how to use the wordlists that come preinstalled with Kali Linux to crack those annoying hashes that contain our passwords. I'm sure that at some point in all of your lives, you have attempted to crack a password by ...more
In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and m ...more
Solar panels are an amazing invention. Catching energy from the Sun before it even enters Earth's food chain, photovoltaics are like an all-natural nuclear power plant. Unfortunately, the constituted parts of a solar panel are rare, valuable, and subject to the coercive forces ...more
Snowman Construction parts for FarmVille! In FarmVille you can now build a snowman! To get the pieces you need you'll have to ask for a few from your friends. You can ask once/ day and the friends are supposed to reset each day. Mine didn't thus far, so I'm providing the link ...more
After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even ...more
Now that we've talked about encryption and managing your passwords, let's continue this series on getting your Mac ready for hacking by turning our attention to the terminal. The terminal is a key component of any pentester's setup. We're going to be spending a lot of time wo ...more
Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities app ...more
With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassin ...more
Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, ...more
Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic An exploit is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability in order to cause unintended or unanticipated behavior to occur ...more
Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't en ...more