If you love the ocean and love swimming, it's time you step up to the next level… snorkeling. Snorkeling is one of the best ways to explore the underwater life, without fancy equipment or expensive training. And all you need is a snorkel. If you want a better look at what’s un ...more
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. For about the past month, the folks at Mojang have been leaking pre-releases of Minecraft 1.9 and they've added many exciting things. Additions to the game include: potions, new mob ...more
Dactyloscopy isn’t going anywhere. Forensic science has much relied on fingerprinting as a means of identification, largely because of the massive amount of fingerprints stored in the FBI’s biometric database (IAFIS), which houses over 150,000 million prints. And thanks to the ...more
How a Hovercraft can be build.Brittany is demonstrating how to make a Hovercraft. Since hovercraft needs a base she is using plywood for it. She takes square plywood of 48*48 and finds out its center to cut plywood in circle. Don’t forget to wear safety goggle while cutting th ...more
Make sure your next apartment rental goes smoothly by properly checking the property before signing a contract. This way you will avoid unexpected disappointments or problems that you were not aware off. Moving is hard enough, give yourself all the advantage you can by going i ...more
In this video series, learn from expert mechanic Nathan McCullough as he teaches and demonstrates how to tune-up a car and do a complete vehicle overhaul. Learn how to check your transmission fluid, air filter, power steering fluid, clutch fluid, brake fluid, radiator and cool ...more
Apple's unveiling of the iPhone 6S, iPhone 6S Plus, Apple TV, and iPad Pro dominated the news today, but at the end of their special September 9th event, they quietly released the final version of iOS 9 to developers, called the Gold Master (GM) build. Don't Miss: The Coolest ...more
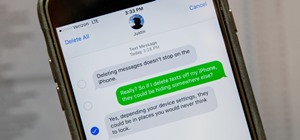
It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you. Today, we'll make a Wi-Fi probe logger with Probemon.py to track nearby devices ...more
While at work, you notice your gloves changing color, and you know immediately that you've come in contact with dangerous chemicals. Bandages on a patient signal the presence of unseen, drug-resistant microbes. These are ideas that might have once seemed futuristic but are bec ...more
A new leak from GSM Israel on March 6th shows some telling screenshots of the U.S. variant of the upcoming Samsung Galaxy S4, some of which confirm features seen in the leaked 4.2.1 ROM for the Galaxy S3. The New UI The NatureUX skin (TouchWiz) has been updated, but it's har ...more
Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In ...more
Apple released the iOS 8 Gold Master build to developers shortly after their WWDC event ended on Sept. 9th, which is jam-packed with tons of new features for iPad, iPhone, and iPod touch. The public version comes out on Sept. 17th, but if you can't wait to test out iOS 8, you ...more
Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful prac ...more
This year, like every year before it, Black Friday sales are starting earlier than ever. A lot of stores will be opening their doors as early as 5pm on Thanksgiving to get a head start on the madness (and it really is madness). As we've discussed in the past, one of the keys t ...more
Microbial cells can improve the functionality of clothes in creative and useful ways, including cooling us down during a workout or making clothing glow for better visibility. The innovative products were developed by a team of 14 researchers from MIT, in such broadly diverse ...more
The LED pollution dress: the ultimate tech + fashion + eco-friendly accessory. Danish design company Diffus recently introduced the Climate Dress, a garment with hundreds of LEDs that light up when air pollution is detected. Dvice explains how it works: "Hidden somewhere ab ...more
What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point. Don't Miss: ...more
Samsung unveiled their new flagship device, the Galaxy S4, at a live event in New York City today. Here's a quick rundown of the specs and all of the new features that you can expect when you finally get your hands on one (whenever that will be). The GS4's Specs 5" 1920x1080 ...more
Apple released the latest version of its iPhone OS, iOS 14.6, today, Monday, May 24. This latest update (build number 18F72) introduces new features like unlocking your iPhone with Voice Control after a restart, Apple Card Family support for up to five people, and subscription ...more
You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information i ...more
The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python to ...more
In a surprising twist of expectation management, Magic Leap managed to not only ship but deliver the Magic Leap One I ordered on Wednesday by 4 p.m. PT on the same day. After spending about an hour with the headset running through set up and poking around its UI and a couple ...more
The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll ...more
One of the worst-kept secrets in the tech world is Apple's plans for consumer-grade AR smartglasses, still unconfirmed publicly and only recently corroborated through a leaked account of an internal employee meeting. In addition to Apple's AR team, assembled through acquisiti ...more
The next-generation Audi A8 to launch in July is expected to be the world's first Level 3-capable production car to go on sale in retail channels. But aside from demo drives scheduled for journalists and analysts Audi plans to organize this month, the model's advanced driving ...more
Images of the newest Moto X flagship phones surfaced over the weekend, and it looks like Motorola has a cool new feature in store for the handsets, which are tentatively titled Vertex and Vector Thin. There are 12 dots near the bottom on the backs of each phone in the photos, ...more
If you have no desire to get a separate Mac desktop computer, but want to either supersize your laptop's screen for gaming or need to get additional screen real estate while you work, then connecting your MacBook, MacBook Air, or MacBook Pro to an external display is the right ...more
Per an anonymous leak yesterday and an official announcement today, the latest version of Android, KitKat (4.4), is rolling out right now for Sprint's variant of the Galaxy S4. This is the first KitKat update for US carriers on the Galaxy S4, showcasing Sprint's recent push t ...more
The final developer version of iOS 11 was leaked a few days ago, but Apple quickly stopped signing it so nobody else could install it. With Apple's Sept. 12 event now over, the Golden Master (GM) version of iOS 11, the same version that will be released to everyone around Sept ...more
A flat soda tastes awful. It's almost as bad as drinking a room temperature milkshake. Of course, you can always opt to buy single-serving cans or 20 ounce bottles, but that's always going to be more expensive than 2-liters. The problem with 2-liter bottles of coke is that th ...more
Nikola Tesla is one of the most tragic figures in the history of science, a history that is practically filled to the brim with tragic figures. Francis Bacon, a 16th century philosopher and scientist, caught pneumonia and died because he was trying to stuff snow into a dead ch ...more
Summer is here, and temperatures are rising. Instead of shelling out for an expensive new air conditioning unit, why not build one yourself with a few bucks worth of old computer parts? There's a number of ways you can go about doing this (and some really fun ways to make you ...more
If you've ever seen one of those Samsung commercials from about a year back, you know that the Galaxy S series of phones come with a feature that allows you to do certain things by making gestures in front of your screen. They call this feature Air Gesture, and it enables you ...more
Rising on the world stage, dengue fever is transmitted by mosquitoes — and apparently air travel too. In July 2017, the World Health Organization's official report tallied 80,732 cases of dengue fever in Sri Lanka, with 215 deaths so far in 2017. The announcement notes that i ...more
Peach trees and other related plants are susceptible to the devastation caused by fire blight, a contagious bacterial disease. Once contracted, infected trees have to be burned to contain the disease and prevent spread to nearby trees. Increasing resistance to antibiotic treat ...more
Add breathing in your house as another possible danger to your health. If your home is sick, it's possible you could get sick too. The term "sick building syndrome" hit the airwaves years ago as a one size fits all reference to homes and buildings that are just too efficient ...more
The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future. The main idea behind the Observa ...more
The Disney Research Lab is using projector-based illumination to paint actors' faces during live performances. You know what that means? Disney just took Halloween to a whole new level. Here's how they did it: The actors move on stage, sans makeup, while the AR light follows ...more
Under the rocket's red glare and the bombs bursting in air, the Statue of Liberty is swaying in celebration this Fourth of July thanks to Snapchat. On Thursday, Snapchat launched a new augmented reality experience to commemorate Independence Day for those at or in the vicinit ...more
While other devices are moving away from fingerprint scanners (cough, iPhone X), for many, a fingerprint scanner provides the best balance between security and speed. Typically, the rear fingerprint scanner on the LG V30 is quick and accurate, but every so often the phone will ...more
Flight disruptions can cost billions of dollars, but most modern commercial flights rely on air traffic control systems that harbor serious vulnerabilities. The Federal Aviation Administration uses an infrastructure called NextGen, which relies on Automatic Dependent Surveilla ...more
The hype is real surrounding the OnePlus 5. As of this post, over 300,000 people have registered for their chance to order the device next week. For everyone's sakes, I hope OnePlus has enough to meet demand. Whether or not you registered this week, there's a good chance you' ...more
The Android 4.4.2 KitKat update is available via firmware upgrade for the international GT-N7100 variant of the Samsung Galaxy Note 2, about a month after we saw its first leak. The update is available via Kies in France, with and OTA update soon to follow. Details courtesy of ...more
Confirming earlier leaks, today Samsung USA released an official a list of Galaxy devices that will receive an update to the latest version of Android, KitKat (Android 4.4). The official list of devices: Galaxy Note 3 Galaxy Note 2 Galaxy S4 Galaxy S4 Mini Galaxy S4 Active G ...more
Beta software can be exciting because you get to experience cool new features before most other people. But it can have unwanted consequences such as bugs, UI glitches, and horrible battery life that'll make you wish you never installed it. If that sounds like you with iOS 16 ...more
Working from home is going to be a reality for more people than ever. With Twitter CEO Jack Dorsey announcing that his employees will be working remotely for an extended period of time (and even permanently, in some cases), the workforce is rapidly changing. More companies are ...more
With iOS 12, iCloud Keychain has become a more useful password manager for your iPhone with strong password suggestions, password reuse auditing, and Siri support. However, before you jump ship from your current password manager, you should consider all the reasons why iCloud ...more
Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP ...more
Mobile World Congress 2018 is here, and with it, Samsung has officially announced the highly anticipated Galaxy S9 and S9+. While we already knew much about the new phones, Samsung's presentation officially filled us in on what to expect from the S9's cameras, including dual a ...more
On the surface, iOS 10.2 might look the same as iOS 10.3, but there's one big difference between the two versions: iOS 10.2 can now be jailbroken! Jailbreaking your iPhone means gaining access to thousands of tweaks and mods which greatly enhance the iOS experience, so this is ...more
The fatal crash of Air France Flight 447 is one of the most tragic accidents in avionic history — while it also serves as a stark reminder of what can go wrong when humans rely too much on driverless vehicles. The tragic 2009 plane crash off the coast of Brazil involved an Ai ...more
Foodborne infections often occur through the contamination of equipment, food-prep tools, and unsanitary surfaces. A recent report from the Centers for Disease Control and Prevention (CDC) reminds us that breast pump parts are part of the food-delivery chain — and they can bec ...more
Dengue fever is a danger to anyone living or visiting tropical or subtropical regions. It can be hard to detect the infection in its earliest and most treatable phase, especially in children. Luckily, new research highlights better techniques for triaging the disease in infect ...more
Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon. Typically, a careful internet user would always check the domain of any site ...more
We are living in a golden age of craft beers. Originally invented by the ancient Egyptians, every culture now has its own tastes regarding beer. The process of making beer is so multi-faceted, it's a miracle that any gets made at all. However, there are lots of steps along th ...more
When it comes to dictating what happens when the Galaxy Note 3's S Pen is detached, the stock settings that Samsung provides are severely lacking. There are only two measly options: launching Samsung's own Action Memo app, or displaying the Air Command menu. If you want to la ...more
No matter what the clean freaks out there try to tell me, I still drink my Los Angeles tap water without a care in the world. I figure that I've already consumed much more heinous things in my lifetime. Street vendor "steak" burritos comes to mind. However, if there's easy ac ...more
Many of us experience highly emotional "freakouts", so to speak, more often than we'd like. Weather you experience them personally, or via your loved ones, it can be very difficult to think rationally during an episode, and for some people it can take quite a while to calm dow ...more
A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials. ...more
Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely da ...more