As a web developer, I often read articles about hackers (from the lowly to the knowledgeable) infiltrating websites via the dreaded 'SQL Injection' method and completely taking control, changing, gaining access, or destroying the owner's data. As a fellow web developer, I'm su ...more
Google is one of the most powerful forces on the Internet, and their technology can be the key to helping you find success in whatever your online endeavor might be, from web design to filmmaking. This video is a part of their Google Webmaster Series, offering help to webmaste ...more
The instructor, Diesel, teaches how to bypass blocked websites at school like MySpace and YouTube. He shows how to make a batch file which opens the command prompt. Next, he shows how to ping a website like MySpace and how to extract the ip address of the website from the comm ...more
SQL injection is a common web application attack that focuses on the database backend. WebGoat is a deliberately insecure J2EE web application maintained by OWASP designed to teach web application security lessons. I plan to use WebGoat for a few future videos. This first WebG ...more
Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webm ...more
Welcome back, my tenderfoot hackers! WordPress-based websites are among the most numerous on this planet (maybe other planets too, but I can't vouch for that). According to WordPress's own website, WordPress powers 23% of the top 10 million websites. That's approximately 2.3 ...more
While websites may run smoothly without any noticeable vulnerabilities, there's always the looming threat that any background weakness in the site can be exploited by hackers. Once a site is compromised, it can be difficult to get it fixed without the proper help. Google has r ...more
Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc. Any time someone's computer seems to act ...more
A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) to ...more
The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user i ...more
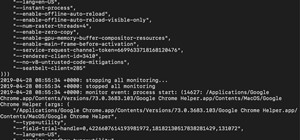
In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greetin ...more
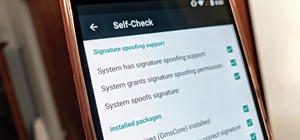
It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or ...more
Haven't you ever wanted to live in a futuristic home? I think that homes are headed towards an era where they will be controlled by our computers and smartphones. No longer will you have to find your keys to unlock your door, or wait until you get home to monitor your security ...more
Essential just dropped the Oreo Beta Program for their flagship PH-1 phone. Users have been eagerly awaiting this update as the early Nougat builds of the PH-1 software have suffered from numerous performance issues and lag. The good news is that you can grab the Oreo update t ...more
You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication b ...more
Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options; Use the meterpreter persistence command. Use the meterpreter metsvc command. Use netcat to listen on a port continuously. You have already tried option ...more
Earlier this year, we got our first taste of Android Pie in the form of Developer Preview 1. As with all past Android previews, DP1 was limited to Google devices — but at Google I/O 2018, Google announced that Developer Preview 2 would be accessible to other devices, including ...more
Like last year's beta release of Android Pie, Google has allowed the Android Q Developer Previews to support some non-Pixel devices. Announced at Google I/O 2019, there are 15 non-Pixel smartphones eligible for the Android 10 Beta, including 2017's Essential PH-1. With a few ...more
Rooting usually means sacrifice. With most root methods, you lose access to apps like Netflix and Android Pay when SafetyNet gets tripped. More importantly, you lose the ability to accept OTA updates, forcing you to manually flash new Android versions. But there's a way around ...more
Google released the first build of Android 12 almost exactly one year after dropping Android 11, which is remarkable in the midst of a global pandemic. But you can tell the Android engineers have been hard at work while quarantining, because the latest OS version is absolutely ...more
Many FarmVille farmers want money fast, or experience fast, or want to level up, or want to speed things up— make and earn things faster. No matter how long they play, they're not getting what they want, and that is to outshine everybody else. But you can't reach the top by si ...more
You know it's crazy out there when governments start blocking social websites like Facebook, Twitter and even YouTube. But that's what happened in Egypt, when tens of thousands of anti-government protesters took to the streets on Tuesday (January 25th) in hopes of ending Presi ...more
Thanks to online music services like eMusic and iTunes, compact discs are becoming a far distant memory, turning local music shops around the country into desolate wastelands. The once mighty movie rental store Blockbuster is now bankrupt because of online streaming services l ...more
Whether it's the new iPad Killer or not, one thing's for sure—the Motorola XOOM is hackable. Just hours after its release last week, Verizon's new Android-based tablet (running Honeycomb) was rooted by hacker Koushik Dutta, which seems easy enough. "Since it’s another Google ...more
With FarmVille being one of the hottest Facebook games on the market, it's no wonder it's the primary target for scams and virus downloads. Anyone playing FarmVille is at risk, but the primary targets are those looking to improve their gameplay and build their farms and neighb ...more
Social Profile Change the privacy settings on your social profile (Facebook, MySpace, Friendster, Twitter, etc.) so that the following information can't be found by a random person who you didn't accept you as a friend: Birthdate E-mail address Hometown Pictures A hacker ca ...more
Using a simple trace trick, you can easily look up the IP address and its location for any website. This method uses a command line command to first find the IP address of a given website, and then uses a free online tool to get that IP's location. Don't Miss: Tips & Tricks f ...more
No website will be inaccessible and no web filter will deny you content once you learn the skills presented in this internet hacking video. In this tutorial you'll learn how to access blocked websites as well as to bypass web filters using URL scripting, HTTP proxies, and a w ...more
In this tutorial, we learn how to use salty hashes to keep passwords secure. A hash is stored in a database that is hashed with an algorithm, so not everyone can see exactly what your password is. When you type your password into a website, it doesn't actually register as word ...more
Household Hacker brings you fun hack how to projects in a variety of areas: electronic hacks, computer hacks, pranks, etc. Search Household Hacker on WonderHowTo for more videos by this creator. In this video, learn how to make YouTube paper. Template: http://www.householdhac ...more
The video shows us how to use a proxy server with Firefox to hide your IP address. you can actually use this to avoid the hacking and various things that are blocking you from websites. Firefox is one of the easiest way to do this and for doing this you need to Google search t ...more
They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam si ...more
XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection betwe ...more
Have you ever wanted to make your own Minecraft server on Windows? This tutorial will teach you how, without having to download Hamachi. The whole process is a lot simpler than you might think, and it will only take a few minutes! You will need: Firefox web browser Computer ...more
Why a PDF Portfolio? If you've been wanting to create a PDF (portable document format) portfolio for your photos, art or design work, or wanted to create a PDF magazine that can be read by anyone on the net, then this article will show you how to go about it. I created my PD ...more
Illustrator's gradient mesh tool is a powerful one for vector artists... if you know how to use it. This tool can help create beautiful and vivid mesh-based vector portraits, as long as your skills are up to par. If not, try out some of the beginner tutorials on WonderHowTo fo ...more
This how-to video is about how to use command prompt to view the blocked websites at school. This step by step instruction will help one to open the blocked websites at school. First open a note pad and type "command" in it then choose the "file" option from the toolbar and c ...more
This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to rea ...more
We're aiming for this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with, we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain acces ...more
This video describes how to access websites that may be blocked by your school. To begin, on the desktop go to the Start menu and select Run. Type in "cmd" and hit okay to open the command prompt. If that doesn't work go to Start, My Computer, C drive, Documents and Settings, ...more
Last Friday's mission was to accomplish solving HackThisSite, realistic 4. The fourth in a series of realistic simulation missions was designed to be exactly like a situation you may encounter in the real world. This time, we are told "Fischer's Animal Products is a company th ...more
Do you need proxy access, but cannot have it for some reason? The most common perpetrator behind the issue is the network you're trying to access the pages from. Some networks will block websites, then go as far as filtering out all of the web queries for terms like "proxy" be ...more
Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords. Visit us at bleedingedgesecurit ...more
Last Friday's mission was to accomplish solving HackThisSite, realistic 3. The third mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend restore a defaced website about ...more
Having a secure password is essential in today's interconnected world. Hackers are just around the corner, and if you have an easy to guess or hack password that you use for all of your accounts, someone can login to all of your websites very easily. Look at this guide on how ...more
Google AdSense is a beautiful thing. They pay you for posting content online, whether it be through a third-party website like WonderHowTo or on your own website. WonderHowTo seems to be a good place to start from if you plan to make money with AdSense, but it's not the only p ...more
This episode of Full Disclosure demonstrates how to hack/crack MD5 password hashes. MD5 (Message-Digest algorithm 5) is a hash function commonly used by websites to encrypt passwords. MD5 is a one-way hash; therefore, to crack the password you most try every possible dictionar ...more
We're officially seeking Null Byters on a weekly basis who would enjoy taking their time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job ...more
We're officially seeking Null Byters interested in teaching others! Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowle ...more
Advancements in technology usually lead to the miniaturization of old technologies, and video games are no exception. Since at least 1990, game hardware manufacturers and enterprising DIY electronics enthusiasts have poured their efforts into making full-size video game consol ...more
Anonymous hacktivists announced via Twitter that they had successfully hacked the website of New York Iron Works, a police-equipment supplier, and replaced the homepage with a tribute of love to arrested hacker and Chicagoan Jeremy Hammond. Image by PictureDJ
Keep your Runescape account safe from hackers by following the instructions in this video. Don't get hacked by giving your password away or using unsafe websites. Watch this video and learn how to take precautions against hackers so you can enjoy Runescape worry free.
Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. A ...more
Want to be able to hack into a computer remotely? This method takes a little extra time and cunning to set up, since you will need to first install the ShowMyPc program on your target computer. Once you have installed this program, however, you will be able to go to the websit ...more
In this tutorial, Brian teaches us how to make your wireless network secure. First, go to the start menu, then go to run and type in "cmd", then type in "iconfig /all". Now a new window will pop up and you will look for the default gateway. Find the IP address to log onto the ...more
In this video tutorial, viewers learn how to find their I.P address in Windows 7 and Vista. Begin by clicking on the Start menu. Then type "cmd" into the search bar and press Enter. When the command prompt window opens, type in "ipconfig" and press the Enter button. Now search ...more
This video tutorial shows you how to jailbreak and unlock your iPhone 2G, iPhone 3G, and iPhone 3GS on firmware version 3.0.1 with Redsn0w and Ultrasn0w. Firmware 3.0.1 fixes the SMS hack/vulneravility Download Redsn0w v0.8: http://thebigboss.org/hostedfiles/red... Download ...more
Notice: This is probably not new to many people. This *IS* new for some people however, and meant for them! Post interesting cameras you find. Website at http://householdhacker.com Today we'll show you how to look through various security cameras using search engines. For t ...more
Friday's Community Byte was weird. The intent was to do a HackThisSite mission, but upon time to begin, everyone in there was programming without my assistance, with the help of Sol Gates. This is great! It's really awesome that everyone enjoys programming that much and will m ...more
You may have asked yourself, "How do hackers take my password, if the website owner can't?" The answer is simple. When a website stores your login password for the site, it is run through a cryptographic hash function before it enters the database (if the website isn't Sony). ...more