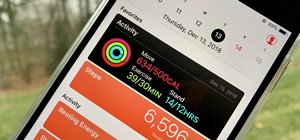
If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! mo ...more
In order to set up a secure wireless router, you will need to use the security that is available with your wireless routing. You will need to change the default ID names and password on your computer. Try to make sure that your passwords are difficult. Also, turn on the encryp ...more
Jim Reppond of Coldwell Banker Bain demonstrates the way of getting postlets into Facebook. He says that by adding the postlets in your Facebook page, one can click on the link and directly go the postlets page if they are interested. He asks you to then go to the postlets pag ...more
In this video, we learn how to upload Wordpress files using Filezilla. Before you get started, you will need to know the host, username, and password for your domain name. After this, click the quick connect button to connect to your server. The left hand side will show the lo ...more
Uh oh, you've forgotten your AT&T Online Account Management password! No worries, this simple guide shows you how to regain access to the site and reset a new password. Your AT&T Online Account Management portal is vital to keeping your information up to date, so make sure you ...more
AT&T Online Account Management portal for small business customers is a great place to manage a sea of information, BUT, it won't do you any good unless you know how to log in. This clear how-to shows you how to enter your AT&T username and password so you can manage your acco ...more
Remove the password on any iOS mobile device! This video will teach you everything you need to know to remove the log-in pass code from your iPhone, iPad or iPod Touch. For more information, including detailed, step-by-step instructions, and to try it out for yourself, watch t ...more
The world first knew it as Weave Sync, but Mozilla has moved Firefox's in-house synchronization project out of its Labs, giving it a new name. Check out how Firefox Sync, which will be included in Firefox 4, matches up your preferences, bookmarks, passwords, history, and open ...more
Looking for a quick guide on how to edit your account information when using Pandora Radio? This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get star ...more
Want to find out a forgotten password on a Windows PC? This clip will teach you everything you'll need to know. With MailPassview, it's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over ...more
Ever wanted to password protect a Firefox This clip will teach you everything you'll need to know. It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over two minutes. For more informatio ...more
Need some help figuring out how to put a password on your wireless router? This home-computing how-to from the folks at CNET TV will teach you everything you'll need to know to do just that. For detailed information, and to get started protecting your own wireless network help ...more
Picking a secure password is not only important for protecting your privacy, it's also very easy. Provided, that is, that you know how to go about it. This free video lesson from CNET TV will walk you through the process. For more information, and to get started creating and u ...more
Lifehacker posts an article on the art of cracking weak passwords, courtesy of Internet standards expert, CEO of web company iFusion Labs, and blogger John Pozadzides. Pozadzides certainly knows a thing or two about password logic. (Note: this information is not intended to ha ...more
You never know when you may lose your BlackBerry and expose all your personal information to whoever finds it. That's okay, protect private data on your mobile PDA by setting a password. Now you don't have to worry about strangers stealing your secrets anymore. Set a password ...more
Locked yourself out of your computer? The Virtual Frank teaches you how to log in to Windows XP using the administrator account that you may not have known existed.
Have you ever forgotten your password and didn't know how to get back on your computer? Or ever had an annoying roommate you wanted to play a trick on to teach them a lesson? Or perhaps overly religious parents who think the internet is of the devil and won't let you read onli ...more
Here's a nasty little Null Byte. An open redirect vulnerability was found in both Facebook and Google that could allow hackers to steal user credentials via phishing. This also potentially allows redirects to malicious sites that exploit other vulnerabilities in your OS or bro ...more
A few weeks ago I wrote about Atomic Web as the best web browser for iOS devices, and while I believe it is a superior option, Atomic Web is not the only alternative web browser you can use on your iOS device. There are three more—Dual Browser, iCabMobile, and iSwifter—that ar ...more
I'm not going to lie. I was Catholic. But one of my reasons for my faithful departure was having to tell my innermost secrets— my sins— to a silhouetted figure behind a latticed screen. With the creepy enclosed booth structure and separation of sinner and confessor, its anonym ...more
Go to http://yourguitarsage.com/ to find out how to order my ebook containing charts for over 170 tunes and constantly updating. This will ROCKET your productivity and fun on the guitar!!! Here is what I teach you! 1. How to play many of the open chords and inversions that y ...more
Note: The article assumes that the reader has a fundamental understanding of at least one other programming language and Perl. This is intended serve as a quick reference for Perl's input/output of data to databases. Once you've mastered the basics of Perl, you might want to ...more
Here at Null Byte, we try to inform and teach the community on ways to navigate the Internet in that special way, as well as staying safe along the trip. That being said, I need some help from all of you! There is a lot of information to cover and I know we have some smart use ...more
I'm sure everyone has heard about Google's changing privacy policy on March 1. It's scattered everywhere, with notification bubbles on Google Search, YouTube, and the rest of their products. Click here to see the new privacy policy that will take effect on March 1, 2012. What ...more
Hello everyone and welcome to Part II - The Ultimate Guide: Diagnosing & Fixing Connection Issues. In this tutorial we will discuss more advanced methods that I took in order to fix our home network. I have also attached a link to download the FREE eBook - so feel free to down ...more
What is Google Dorking? Well, simply put, "Google Dorking" is just an efficient way to utilise keywords in order to perform very specific searches on a given subject. In this case, one would look for websites/servers that are vulnerable to attacks or are configured improperly ...more
This is my attempt to show people some cool things we can do with programming, and to give a small incentive for people to join the weekly Community Bytes. I wanted to make a tutorial on how to use Twitter from the command line with Python. This would have been an easy project ...more
When you're out and about in the dangerous world of Wi-Fi, it's hard for the average computer user to stay protected, or even know what being protected entails. Little do most people know, Windows 7 has a built-in security that few people take advantage of: a VPN (Virtual Priv ...more
Movies like to show hackers breaking passwords with fancy software and ludicrous gadgets. The reality of busting passwords open is much more mundane. Simple as it may sound, most passwords are broken purely by guesswork. Check out this infographic from ZoneAlarm, as well as th ...more
If you're new to the Bluetooth hacking world, here's a little background on using Linux BackTrack to hack a Bluetooh device: Linux Backtrack is a Live DVD device that offers security tools - like password crackers - that allow you penetrate networks. Thus, you can penetrate e ...more
Facebook is an internet phenomenon which is quickly gaining popularity. For those who do not yet have a Facebook, this video will show you the basics of how to meet people and to connect with people online as well as how to set up your profile on the site. After creating an ac ...more
In this how-to video, you will learn how to change the password to your hotmail e-mail account. This will be useful if someone knows your password or it is not unique enough to be safe. First, go to your web browser and log in to your hotmail account. Once you are in, go to th ...more
This video shows how to hack the computer password for Vista. We can change the computer password without knowing the actual password. First go to Start menu. Type in the Search "cmd". Then right click on that folder and run as administrator. Then we get a pop up. Type in thei ...more
Be warned before hand that by making changes your router settings that you know nothing about can damage your router. Start off by opening your internet browser and then in the address bar either type 192. 168. 1. 1 or www.routerlogin.com. A prompt will come up in which you ha ...more
locker gnome teaches you how to unzip files online. The site you need to visit is WobZip. You can use a file from your own computer or one from the web. If the archive has a password, type that in the field. The formats supported are 7z, zip, gzip, bzip2, tar, rar, cab, ISO, a ...more
Start out by going to www.Facebook.com. From this page you will be able to create your own personal Facebook profile. Fill in your name, email, password, sex, and date of birth. Click 'Sign up' after you have filled in all of this information correctly. Facebook will send you ...more
This is a great tutorial on how to use Backtrack 2 to crack a local computer for access. You can either completely change the password or you can wipe it and restore the password so nobody knows you were there Part 1 of 3 - How to Crack local passwords for access to a computer ...more
For Infinity Exists Full Disclosure's first Website Hacking episode, we demonstrate how to exploit a security vulnerability occurring in a website's database to extract password hashes. Sql (Structured Query Language) is a computer language designed for the retrieval and manag ...more
Are you serious about becoming a bonafide hacker? Then you simply must learn how to hack SSL passwords using ARP poisoning. ARP poisoning, also known as ARP spoofing, involves attacking an ethernet wireless network by looking at the data frames on a LAN (local area network). R ...more
Back when I was a Windows user, I know I'm not the only one who has experienced password loss—that moment where you just can't remember your password. Sometimes it happens to the best of us. So, how can we get into the system without paying a local geek or geeksquad to do it? ...more
This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing p ...more
As hard as you try to protect your valuable information with strong passwords and anti-doxing measures, there's nothing you can really do when someone else gives up your goods. And that is the case with the recent Global Payments breach. Global Payments is just one of the mid ...more
This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to rea ...more
With the mass arrests of 25 anons in Europe and South America, and the rumors of an FBI sweep on the east coast of America floating around, times look dicey for hackers. Over the past few days, a lot of questions have been posed to me about removing sensitive data from hard dr ...more
By now, most of you have updated to the new Xbox look. Just as expected, it's got some great new features. The dashboard looks great and Bing integration is awesome, but I'm very unhappy about the new Netflix interface. It's awkward, slow, and half of the items don't even load ...more
I can't say it's absolutely true, but when it comes to mobile word gaming, there's Scrabble people and then there's Words with Friends people. It feels segregational. Rarely does one play both. At least, that's what I see when it comes to my family and friends. Everyone who l ...more
I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to rememb ...more
Spam is everywhere and Facebook is no exception. In fact, spammers are constantly stepping up their game by tricking unsuspecting Facebook users to participate in quizzes, games, apps, or "new features" that are actually dangerous computer viruses, spyware, or other trojan hor ...more
WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most ...more
A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc. Obviously, not all places use the same methods, and not all of the m ...more
Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying vario ...more
Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use y ...more
In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then a ...more
SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and e ...more
Have you ever been away from home or on holiday and noticed an open network connection? FREE INTERNET! But then you find out that every search or page redirects you to an "enter password" or "signup here" page. Well, there are ways around this. In this article, I'll show you ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. This week has been an exciting one. The com ...more
The purpose of this article is to discuss how you can change your Windows 7 logon screen. This post will explain how to require a user to enter a username and password by default like the classic version of Windows. I recommend advanced computer users carry out this task. It ...more
SSH is what is referred to as the Secure SHell protocol. SSH allows you to do a plethora of great things over a network, all while being heavily encrypted. You can make a remote accessible shell on your home computer that gives you access to all your files at home, and you can ...more
Web-spying technologies like FaceNiff, Firesheep and Newstweek are out there showing the world just how easy it is to see what you're doing online, but they're amateurish in comparison to what real hackers could do to you if they catch you browsing unsecured websites. Luckily ...more
While we're waiting for Google to sort out the mess over suspended Google+ accounts, it's a good reminder that you have the option to download much of your Google+ data with Google Takeout. Google Takeout, created by an internal Google engineering team marketed as the Data Lib ...more