Welcome back my friends !! Today we'll go through the second part of this C# series Let's start!! Last time we left off with Console.WriteLine and Console.ReadKey now we'll combine these with some variables and comments. Comments are useful for multiple reasons: for exemple ...more
Hello Java-ers, In the previous two tutorials, we learned about installing the JDK, Installing/CreatingAProject in Eclipse IDE, and data types in Java. In this tutorial, we will be learning about if/else statements. -------------------------------------- In Java, an if sta ...more
UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/ Hi guys, I'm here again with my second tutorial, as I promised. Metas ...more
Hello Null-Byte community. First off: this my first post here on Null-Byte. Some of you may have already seen me in the comment section, to all others: Hi, I'm the new guy. Secondly, a standardized text to wash my hands in innocence: I have used the search function with diffe ...more
Video: . I made this Tesla Coil using the myRIO and LabVIEW. It uses electricity to play the music, which can be Star Wars, Harry Potter or even Hunger Games! The music is played by the spark heating the surrounding air (causing it to expand) then the spark turning off (causin ...more
The cell phone has come a long way. The very first "mobile devices" were made and used by the military in the late 1930s, with the first commercial mobile telephone service introduced by Bell in 1946. These devices were hardly what we'd call mobile today—some took up the whole ...more
There's nothing worse than when you come up with a brilliant idea while you're busy with other things and then promptly forget it. Whether it's the perfect ending for your novel or a comeback you should've said during that argument with your roommate last week, it's always ann ...more
You can use Twitter to print Instagram photos, track news and weather events, or even remotely shut down your computer, and if you're familiar with IFTTT, there's no shortage of ways your account can help automate your life. Or, if you just want to build something cool (pract ...more
The worst part of moving into a new place is, well...moving. It's tedious, a lot of hard labor, and it can take forever, and don't even get me started on all those labels. It's also one of the only times in your life when everything you own can be stolen at once, since it's si ...more
Apple has a few exciting surprises for you in its latest iOS 16 and iPadOS 16 software updates. Released on Thursday, May 18, version 16.5 includes new features, bug fixes, and security patches, and there are even hints of some big things coming in future software updates for ...more
It's Black Friday time, and in 2020, that means a lot of online deals to make up for more stores closing on Thanksgiving, as well as everyone avoiding in-person shopping because of the coronavirus. But while you may wish to grab a better 65-inch 4K TV, the new PlayStation 5, o ...more
Knowing just one or two programming languages is no longer sufficient if you want to make serious money in the lucrative world of web design and development. But the good news is that you don't need to spend an excessive amount of time or money on a traditional coding educatio ...more
Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, ...more
There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer. It's puzzling to imagine about 100,000 .onion websites in existence. Readers who ...more
A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simpl ...more
Augmented reality software maker Upskill has released the latest version of their Skylight platform, adding a number of new tools to ease implementation and improve functionality for enterprises, including a new application builder. Paired with AR smart glasses from Google or ...more
Aircraft equipped with ADS-B are constantly shouting their location into the radio void, along with other useful unauthenticated and unencrypted data. In this guide, we will make an ADS-B receiver using a Raspberry Pi with a software-defined radio (SDR) dongle, which we can us ...more
Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians acro ...more
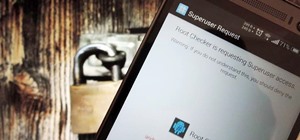
It used to be that you only had to worry about maids rummaging through your belongings in your locked hotel room. But now anyone with 50 bucks of hardware and some programming skills can hack their way in—as long as it's locked by keycard. At the Black Hat security conference ...more
If you want to try out one of Apple's beta programs on your iPhone — whether that's by becoming a developer, joining the public beta, or using an IPSW of an available beta update — there's always a possibility that you'll want to go back to the stable iOS version you were usin ...more
There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're conc ...more
Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pen ...more
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up ...more
Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily act ...more
Those of us who've taken the time to learn how to code are relatively well-suited for shakeups in the economy. Despite the recent and notable disruptions caused by the COVID-19 outbreak, demand for talented and trained programmers and developers is still high, and it will like ...more
There are countless ways in which you can turn your love of tech and coding into a full-fledged career — from developing apps and websites as a freelancer to working in the IT departments of small startups or major tech companies. But one of the best ways that you can put your ...more
After dipping its toes into the AR cloud arena last year, Ubiquity6 is now jumping in with both feet this year. Late last year, the startup launched Display.land, a social network for sharing and editing 3D digital scans of real-world locations. Now, the company is expanding ...more
While Magic Leap World gets its share of fun apps for playing with Porgs, watching TV, and exploring the ocean's depths, developers are making a strong business case for the Magic Leap One as well. Cue BadVR, a Los Angeles-based startup that was recently highlighted as one of ...more
In recent years, augmented reality has increasingly helped to take art off museum walls and bring it (virtually) into people's homes and communities, offering new perspectives on classic pieces and modern creations alike. On Tuesday, Apple announced [AR]T, a new project desig ...more
For Snapchat users wondering if that selfie is ready to send to their crush, independent Lens Studio creator Andrew Mendez created a handy tool called the Smile Rater. The lens is simple yet effective. A white bar floats over the user's head, showing a rating of one through 1 ...more
Two years ago, Facebook founder and CEO Mark Zuckerberg kicked off the F8 Developers Conference keynote with augmented reality and the introduction of Facebook's AR camera platform, now known as Spark AR. Since then, Facebook has faced an avalanche of controversy on its appro ...more
New documents reveal that electric car company Tesla has filed a surprising new patent that has nothing to do with batteries or autonomous driving and everything to do with augmented reality. Last week, the company's US Patent and Trademark Office patent application, titled " ...more
Our national month-long celebration of all things creepy and crawly comes to a climax on Wednesday with Halloween and will end with Día de Muertos on Friday, so now is the ideal time for the The New York Times to publish a mildly chilling augmented reality story for children. ...more
Facing mixed reviews for the Magic Leap One, Magic Leap has already returned to the lab to improve on the device's successor. On Monday, in a bid to facilitate further innovation and spread its physical footprint, Magic Leap revealed a new Center of Excellence in Lausanne, Sw ...more
Amazon Web Service's do-it-yourself tool for building augmented reality experiences and VR has graduated from beta and is now available to all interested users. Unveiled at the AWS re:Invent developer conference last year, Amazon Sumerian is billed as software that lets anyon ...more
Instagram is no stranger to stealing features from Snapchat. Stories, originally a Snapchat invention, feels more at home with Instagram today. Now, Instagram is attempting to repeat this feat with nametags, a way to quickly add new friends akin to Snapchat's Snapcodes. If yo ...more
The augmented reality and VR arm of Verizon, Envrmnt, wants to make it really easy for anyone to create AR apps. AR Designer is a web-based tool with a drag-and-drop interface that enables non-developers to import 3D assets, build ARKit and ARCore apps, and publish them to th ...more
One of the most overlooked components of talking about augmented reality and virtual reality is getting people to actually use the hardware and software associated with these platforms. We're so early in the development of immersive computing that we're still dealing with a f ...more
The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix ...more
Outside of early military applications, augmented reality is a relatively new technology. It stands to reason that the next company to make a splash in AR would be a startup, and Techstars wants to help. Nonetheless, there are also more established companies working in AR, an ...more
The fourth and final beta version of Android O just made its debut, and the biggest change is what appears to be a new code name. When you access Android 8.0's version number Easter egg, you'll be greeted by ... a cartoon octopus. Octopus starts with the letter "O," and Googl ...more
Bixby — Samsung's voice-activated digital assistant — has been delayed again because the software still can't recognize English. Although Samsung claims Bixby can execute 15,000 tasks, it appears it's inability to master English is a major obstacle that's preventing its full r ...more
In the nascent AR/VR race, any release news is big news. For augmented reality, those invested in the new technology eagerly await the release of Microsoft's Hololens and any inkling of information that comes with it. If you're one of those folks, you're in luck, as new inform ...more
This morning, in an early morning session at GDC 2017, Brandon Bray, a senior program manager lead at Microsoft, revealed a mixed reality headset made in collaboration with Acer—a different headset than the one we saw from Acer at CES 2017 earlier this year. Also at the event, ...more
Verizon Wireless executives recently cooked up a plan so devious that it could have only come from one of the four major US carriers. Apparently, they aren't satisfied with simply loading every Android device they sell with their own bloatware, so now they're reaching out to b ...more
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series. This tutorial is for those who already know how to program in C and have a basic understanding how networks w ...more
A little less than a year after announcing "Project Astoria," Microsoft announced Thursday, February 25th, that it will end the "Bridge," which would have brought Android apps to the Windows Store. Microsoft's Android Bridge (aka Project Astoria) is no more.. Microsoft also an ...more
Sup? Today, we'll be learning about for loops in Java: What they are, how they work, and how to create them. Lets begin In Java, like many other programming languages, we have Loops, which are functions that repeat the statement(s) within their brackets until something withi ...more
Hello there Nullbyte users! This will be my first article here. Feel free to give feedback in the comments! Today I'll be introducing the UNIX text editor VIM. VIM is a text editor that is completely controlled from the keyboard. An experienced VIM user is A LOT faster than ...more
OK, In my last Tutorial we made a Server for sending Instructions to a Client. This time we will build the Client. Fire up your favourite Python environment and get the Code here. The Server Code ---Imports--- -socket is again for the connection -time is for pausing the Clie ...more
Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start ...more
What's up guys! It's time to discuss strings in more detail. Review Just a revision in case you have forgotten about what buffers (arrays) are. A buffer is a container to hold data which are adjacent to each other in memory (we have seen this in the previous tutorial on memo ...more
Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effor ...more
If you've switched ROMs before or flashed quick mods on your Android device, you've probably used TWRP or another custom recovery to install them. But another great purpose for flashing through a recovery is to install your own custom .zip file filled with everything a fresh R ...more
Disclaimer: All information in this tutorial is for entertainment and educational purposes ONLY. You pesky teenagers. In my previous tutorial, I covered how to make a backdoor in an OSX system. I also covered some fun commands to try whilst the backdoor connection is in tact. ...more
Social media is where we post our thoughts for the world to see, but sometimes a little more exclusivity is needed. And that's where Scrambls comes in. Scrambls if a free extension for Chrome, Firefox, Safari, and Internet Explorer that scrambles your messages for super cool ...more
The beauty of free apps is that, well, they're free. But as we all know, there is no such thing as a free lunch. Sometimes these "free" applications are only feature-limited mini versions, or they're so littered with ads that opting to pay for it is the only way to actually en ...more
Robert Templeman from the Naval Surface Warfare Center in Crane, Indiana and several of his friends from Indiana University recently developed an Android application that is capable of gathering pictures and videos from mobile devices in order to reconstruct a user's environme ...more
UPDATE: A patch to fix the exploit has been released. Download it here. A new vulnerability in Java 7 has been added to the BlackHole exploit kit and Metasploit that allows malicious software to be installed on Windows, Mac OS X, and Linux computers. So far, it has only been ...more
If you use Ubisoft's uPlay browser extension, you should probably get rid of it right now. An Information Security Engineer at Google discovered that the plugin has a hole in it that allows programs to be installed through uPlay, essentially letting anyone who feels so incline ...more