Most people have had the unfortunate experience of not having a washer and dryer at some point. Apartments in my area tend to charge at least one hundred dollars extra for the units with washer and dryer hookups, and even more if you want a unit with an actual washer and dryer ...more
Here at WonderHowTo, we appreciate the fine art of photography (including its extensively vast bag of mind boggling tricks). We also enjoy playing with fire. Sorry, most of us are little boys at heart, and we can't get enough tutorials that fall within the playing-with-matches ...more
A press release should be about news. It should have a sense of urgency about it and grab the reader’s attention from the outset. A good press release must quickly answer the journalist’s immediate questions: Who? What? When? Where? Why? How? The release should ideally conta ...more
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. While it may first appear complex, the Multi-Channel music sequencer made famous by User FVDisco is rather simple in principle. It relies on proper combination of timing and tone to ...more
The whole world seems better when you’ve had a full night’s sleep, and if you don’t believe me, you’re JUST FRIGGIN’ WRONG. Studies show that getting enough sleep during nighttime hours can make you less irritable, help you lose weight, and reduce your risk of cancer and other ...more
A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc. Obviously, not all places use the same methods, and not all of the m ...more
WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most ...more
WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most ...more
No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the In ...more
Social engineering is described as the clever manipulation of the natural tendency of human trust. All of the passwords, locks, and encryption in the entire world are useless against a good social engineer who can charm or trick you into giving it up. But what once started as ...more
In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then a ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. Thanks to all of our active moderators and ...more
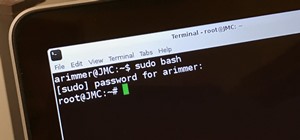
Have you ever forgotten your password and didn't know how to get back on your computer? Or ever had an annoying roommate you wanted to play a trick on to teach them a lesson? Or perhaps overly religious parents who think the internet is of the devil and won't let you read onli ...more
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. While mining is a basic aspect of Minecraft, it is often overlooked. Every adventure requires iron and diamonds and other ore and if you're playing in hardcore mode then you need al ...more
Like theme music, I always feel that I need more fog in my life. Fog can be useful for many reasons—warding off smaller siblings from your bedroom, keeping curious hands out of your cupboard, and tricking your friends into thinking there's something horribly wrong with their v ...more
These are some tricks for advanced computer use. These are PC only and meant for use on Windows XP machines. Part 1 of 14 - How to Learn advanced computer skills for PC. Learn advanced computer skills for PC - Part 2 of 14. Click through to watch this video on expertvillage.co ...more
Last week, I updated VirtualBox on my computer since I had skipped a few versions, then I could no longer copy text or paste text from my Kali virtual machine to my host OS and vice versa. Installing the Guest Additions didn't seem to do anything, and the bidirectional shared ...more
This video will guide you 5 useful tricks and tips for Google search engine. These tips include search operators, search in a single site, get definition, calculation and currency conversion, fast essential information etc. So please watch the video and follow all the steps to ...more
A potentially groundbreaking new app targeting retail financial services hopes to bring augmented reality to your local bank and credit union. Last week, Kony, an enterprise applications developer based in Austin, Texas, introduced its Digital Banking Platform. The software ...more
Windows XP will always have a special place in my heart—it's the operating system I grew up on. It guided me through the glory days of AIM, Napster, and MySpace, but now it's dead. The OS that had been supported by Microsoft for twelve years officially lost its support on Apri ...more
Marinades are among my all-time favorite tricks as a cook for several reasons. They're easy like Sunday morning, they let time do what it's supposed to, which is work for you, and you get a huge return for relatively little effort on your part. In a pinch, I've used store-bou ...more
First off, I would like to say two things. One, this is not for beginners; if you don't feel that you understand this how-to at all, do not try it. Second, never ever install random software or change settings if you do not trust the source. If I haven't scared you yet, here ...more
In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenari ...more
In my last quick clip, I demonstrated how to take a bottle of soda and freeze it on command. I received many requests for a more detailed article on this, so here we go. This "super cool" trick works with cans of soda too, not just bottles! Video: . This project was inspired b ...more
Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. ...more
Wet shoes are uncomfortable, no one can deny that. Just think about walking around with soaking wet footwear ... and each squishy step you take. Makes you cringe, doesn't it? It can happen in heavy rain, at the beach, or from an unforeseen puddle on the street. And while you c ...more
Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life. Imagine arriving home one night after work and there's a Post-it note on your apartment door with the website "your-name- ...more
The microwave oven is a monumental technological achievement that's saved college students and single people from starvation for decades. Almost 97% of all American households have one, which makes it the most-owned kitchen appliance in US homes right after the refrigerator. ...more
YouTube illusionist Brusspup has used everything from mirrors to fire to create his optical illusions, but his latest trick is a little more 2D. Using a printer, a transparency sheet and a piece of regular paper, he made several illusions that trick your brain into thinking th ...more
When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a littl ...more
What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, ...more
In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greetin ...more
The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack usi ...more
Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in ...more
There are two types of bad USBs out there. One lets you trick the computer into thinking it's a keyboard or other USB device, and the other goes straight over malicious into computer killing territory. Last year, Russian security researcher Dark Purple designed a USB stick th ...more
Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now. From what I can tell, it's a very safe a secure method keeping passwords, links, and personal stuff encrypted and online. TURTL https://turtl.it Turtl is ...more
When I first moved to Los Angeles, I rented a bed in a tiny studio. I was too broke to afford my own place, so all I had was a mattress in someone else's apartment. Unfortunately, this person had no interest in cooking, and therefore no kitchen equipment whatsoever. To make ma ...more
Finding the formula to the perfect cup of coffee for your taste can take a while. I finally got around to buying a French press a few weeks ago and I'm still tweaking the right ratio and brewing time to get it just right (though I am drinking it at the right times each day). ...more
C.R.E.A.M., aka Cash Rules Everything Around Me. There have never been truer words spoken in real life, or even in a video game. After playing BioShock: Infinite for a few days know, I wish I came across this little glitch a little earlier. The lifeblood of your BioShock char ...more
Convenience is a big deal these days. You can buy single-serving or single-use sizes of just about anything, from fruits and vegetables to sanitizing wipes, and, apparently, even bananas. Uhh, it already has a wrapper... Admittedly, we do have one of those espresso machines h ...more
Linux is generally a pretty stable OS, but occasionally things happen. However, as long as your keyboard has a SysRq key, you'll never need to worry about freezes again. The SysRq key functions allow you to perform various low level commands, even when your system is unrespon ...more
Black Mirror, Netflix's technology-horror anthology, never fails to provide thought-provoking entertainment centered around emerging and futuristic technologies, and the third season's second episode, "Playtest," delves deep into the worlds of mixed, augmented, and virtual rea ...more
Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you ...more
Contrary to popular belief, augmented reality apps have been available for a while now. I remember using the Layar app (still available for iOS and Android) to explore nearby businesses and landmarks with varying success via an early-generation Android handset. It would be ha ...more
Mobile augmented reality developer Blippar's mission is to construct a computer vision map the world, with visual recognition of thousands of notable buildings, bridges, castles, holy places. A major step toward that goal has been taken by the company this month with the annou ...more
Last year, Motorola released their Moto G5 Plus, a fantastic mid-tier machine that earned praise from both reviewers and consumers. Starting at $229, it was well-built and inexpensive considering everything Motorola managed to jam into it. This year, Motorola is looking to rep ...more
Google, the company that rules the internet, is now testing a method to leverage its machine learning with its ubiquitous presence on mobile devices. The new model they're employing is called Federated Learning, and it hopes to apply artificial intelligence to Google's service ...more
Mirror, mirror on the wall, who's the smartest of them all? Since Max Braun's Medium post went viral back in January of 2016, smart mirrors have been appearing on tech blogs in all shapes and sizes. Some are technically sound, some incredibly easy, but all are visually compel ...more
Hi, I am Robel, I am here to let you know about how to hack windows admin password with out Sam files, this requires physical access and any boot operating system...I used Kali 1.8 , if it doesn't work make sure you have shuted it down properlyor use backtrack. I have tested ...more
For the past three or four months, Microsoft has been pushing advertisements onto the lock screens of some Windows 10 users as part of its "Windows Spotlight" feature. This feature normally shows you scenic photographs and gives you the option to learn more about them by launc ...more
Hello you sexy, savage, surreptitiously tech-savvy penetrators (Pun intended)! Today I'm going to show you two really quick tricks that allows you to find someones saved passwords on their browser. To use these tricks you must have access to their browser, which means you are ...more
At first glance, the Big Green Egg looks like it was created by Dr. Seuss or some other whimsy-driven being, like Zooey Deschanel. And while this earthenware cooker may look cute, it produces serious results that can rival the best barbecue or grill. In fact, it's got quite a ...more
Get some tinfoil hats and make a time machine because we are about to go back to the 90s and learn about some phreaking. Step 1: What Is Phreaking? Phreaking is the action of hacking into telecommunications systems, especially to obtain free calls. Phreaking was big in the 9 ...more
Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world! Advanced Per ...more
Need to add some spooky ambient fog to your super-scary Halloween party? Rather than shelling out money for a fog machine you'll probably only use once a year, make a trip to the nearest drug store and pick up a bottle of glycerin, a gallon of distilled water, a 2-liter bottle ...more
Sometimes you just want to grill. It doesn't matter where you are, what you have, or whom you're with—you just want a delicious burger and you don't care what it takes. If you don't have a home grill or you're out camping in the wild, then it's the perfect time for your MacGy ...more
Mountain Lion (OS X 10.8) is out today, available in the Mac App Store for just $20. Unfortunately, installing Mountain Lion requires that you already have a Mac running Snow Leopard (OS X 10.6) or Lion (OS X 10.7). If you're currently running a Leopard system, you're out of l ...more
Users are often the weakest link when probing for vulnerabilities, and it's no surprise they can be easily fooled. One way to do this is called clickjacking. This type of attack tricks the victim into clicking something they didn't mean to click, something under the attacker's ...more
Hackers are always seeking zero-day exploits that can successfully bypass Windows 10's security features. There has been extensive research into creating undetectable malware and entire GitHub projects dedicated to automating the creation of undetectable payloads such as WinPa ...more
Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about. Sometimes, if yo ...more