The Raspberry Pi loads an operating system from whatever SD card you insert, allowing you to keep different operating systems on separate SD cards depending on which OS you wish to run. A tool called BerryBoot cuts down on the number of SD cards needed by providing the ability ...more
Google's much anticipated eBook Store has finally opened. As of today, the digital bookselling enterprise is awaiting your needs, with over 3 million eBooks to read directly on the web or on other platforms, like Android, iPhone, iPad, Sony and Nook devices. And the best part ...more
Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker. FileVault, created by Apple in 2003, is a hard ...more
You may already know that you can build a functional circuit on a sheet of paper with the graphite from a pencil, but you'd probably never think of using it to fix an electronic device. This same principle can be used to bring back a bricked phone, but can also repair a damage ...more
These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred. We vigilantly remember to lo ...more
The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be ...more
There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distributi ...more
You can use the F1 key to notably dim your Mac's display, but sometimes that just isn't dark enough. If you're working in pitch black conditions, have a migraine or tired eyes, or just want a more comfortable environment, you might want your screen even darker—without making i ...more
Contrary to popular belief, augmented reality apps have been available for a while now. I remember using the Layar app (still available for iOS and Android) to explore nearby businesses and landmarks with varying success via an early-generation Android handset. It would be ha ...more
Yes, screen savers are fun to look at for a few seconds, but those animations actually used to serve a purpose beyond simple entertainment. In older CRT and plasma monitors, and even newer OLED ones, leaving a static image on the screen for an extended period of time could cr ...more
When you're stuck working or learning from home, video meetings can help you stay connected to employers, coworkers, schools, students, and more. And Zoom is the hottest video conferencing service at the moment. While Zoom is easy to use, it does have a fair share of sketchy f ...more
This is a video demonstration on how to tether your iPhone 3G to a Mac laptop to use the 3G network for surfing the web on the laptop. This is against AT&T's policy so try at your own risk. This is in place of the NetShare app that keeps getting removed by Apple or ATT. This l ...more
Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, ...more
The Snap feature in Windows has been tweaked many times since it debuted alongside Windows 7, with productive additions like Snap Assist brought in along the way. It only makes sense that Microsoft would put so much effort into developing this feature when you consider how use ...more
Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't en ...more
Got a dirty desktop computer or laptop screen? Mix together a solution of equal parts white vinegar and purified water and place solution in a spray bottle. Spray a clean cotton rag with the solution and gently wipe the screen for simple, streak-free cleaning. For a quick clea ...more
In an attempt to remain a mobile-exclusive app, Instagram doesn't let users upload photos or videos from their computer. On the Instagram web app, you can pretty much only like and comment on items in your feed, but what about all of those photos on your computer that scream # ...more
Defcon is the largest hacker conference with something for everyone, whether it be the talks, parties, villages, or any of the hundreds of events. In this guide, we'll take a holistic view at everything that goes into attending the con for the first time, from securing your el ...more
Apple unveiled the iPhone X-like redesign of its iPad Pro line Tuesday, Oct. 30. Among the many new changes to the company's famous tablet was a glimpse at its new wallpapers. These images, while clearly intended to take advantage of the new iPad's striking screen ratio, are c ...more
Paying for internet WiFi? That's SO 2010. If you have one internet connection on your iPhone 3G then you can share that connection with just about any other device, such as the iPad, iPhone, iPod, laptop, XBOX 360, and PS3. This method of tethering will only work if your iPho ...more
With the mass arrests of 25 anons in Europe and South America, and the rumors of an FBI sweep on the east coast of America floating around, times look dicey for hackers. Over the past few days, a lot of questions have been posed to me about removing sensitive data from hard dr ...more
With so much money on the line, it's no surprise that cryptocurrency exchanges are prime targets for cybercriminals. Because of this, the importance of keeping your personal account as secure as possible cannot be overstated. Binance is one step ahead in this regard, as it req ...more
Ever wonder how all of those tiny chips and components can fit inside your laptop or smartphone? If you tried to squeeze them in there yourself, your laptop would quickly become too heavy for your lap, and your mobile phone would need wheels to stay mobile. The secret to mini ...more
I regularly use iTunes on my home laptop and my work desktop forty-five traffic minutes away. I'm ashamed to admit it, but until recently, I'd been saving my iTunes library on a USB and transferring it back and forth, over and over again, between the two computers. Well, this ...more
Let's just say it's been a pretty bad year for spies and government agencies and an even worse one for the privacy of U.S. citizens. Edward Snowden blew the lid off the NSA's spy program, and the FBI was recently discovered to have the ability to access your webcam any time th ...more
See how to make a USB motion detector with KipKay and MAKE Magazine! Find out how to turn your PC into an ambush multimedia presenter! Kipkay loves his gadgets! This is combination of a motion detector, a USB interface cable, and a laptop computer.
Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we ...more
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, w ...more
MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the com ...more
Using a combination of my phone, laptop, and an arsenal of apps and plugins, I can send pretty much anything to my Chromecast. However, nothing is ever perfect, and the file type that was still giving me headaches were torrent and magnet files. Yes, I could download them to m ...more
If you're ever in a situation where you need to take a peek at the wireless spectrum, whether it's for Bluetooth or Wi-Fi devices, there's a fascinating Python 3-based tool called Sparrow-wifi you should check out. It's cross-platform, easy to use, and has an impressive GUI th ...more
Anyone who uses a computer on a regular basis probably knows how to access the task manager to check system resources and usage stats. However, on a Samsung Galaxy S3 or other Android device, it may not be so obvious. There's no equivalent to Control-Alt-Delete, but it's still ...more
The Microsoft Surface has been the go-to device for many professional artists since its initial release back in 2012. Since then, the Surface line has continued to offer customers a portable, high-powered machine that's a near perfect value for both casual and professional art ...more
The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practic ...more
Oh how we love open source software. If it wasn't for Open Office, we never would have been able to write that seven-page English paper while on our friend's Microsoft Office-lacking laptop during an impromptu road trip to Mexico. And Ubuntu, an open source secure operating sy ...more
It looks like there is a fatal flaw in the current macOS High Sierra 10.13.1, even straight from the login menu when you first start up the computer. This severe vulnerability lets hackers — or anyone with malicious intentions — do anything they want as root users as long as t ...more
Windows 10 and macOS have poor reputations when it comes to customer privacy and user policies. Our hacking Windows 10 and hacking macOS articles might make it seem like a reasonably secure operating system doesn't exist. But I'm here to tell you that there is a viable alterna ...more
Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a si ...more
Now that Samsung upgraded DeX in the Galaxy Note 10 and Note 10+, more users will be looking to use their phone as an "anywhere PC." With a simple USB-C to HDMI cable or adapter, you can turn your Note 10 into a desktop, complete with full access to your apps. But not all USB ...more
The iPhone 12, 12 mini, 12 Pro, and 12 Pro Max all have positive coverage surrounding their refreshed design, camera upgrades, and 5G connectivity. One piece of negative press you might've seen, however, is about the charger. Specifically, that there's a Lightning to USB-C cab ...more
Download the ISO and follow along with this video to learn how to install Android OS on a PC. Using Virtual Box, you can run Android directly on your desktop computer or laptop. Watch this video to see how it is done.
Recently, I decided to install Kali 2016 as dual boot on my laptop. Everything install perfectly up until the installer gave me the option to set up the package distribution mirror. No matter what setting I provided, no mirror would set up correctly. I was forced to continue t ...more
Cleanliness is next to godliness. My interpretation of that age-old adage means that keeping your house clean is just as un-fun and boring as being a goody two shoes. That's why they call things like laundry and doing dishes "chores," I assume. Yuck. Lucky for you, though, we ...more
I had my wallet stolen a few months ago, and I knew I would never see it again. My biggest gripe was not the credit cards in there, since they're easily cancelled, but the gift cards. I had some pretty good gift cards in there, and there's no way to get those back. Your walle ...more
lubuntu is a is a lightweight Linux/Ubuntu that makes it suitable to virtual environments, that you run with VirtualBox to add a secondary machine to your computer or laptop. With this program you can run a number of operating systems upon the same platform. But as we are all ...more
Like insurance, it's always better to have a computer mouse and not need it than to need it and not have it. Honestly, I don't want to carry around a clunky mouse with my laptop, so I don't. I do something else, something more convenient. I use my Nexus 7. If you want to give ...more
The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user i ...more
These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting. ...more
Everyone from first responders to hotel cleaning staff use radios operating in the sub-megahertz range to communicate, often without even encoding the transmission. While encoding and encryption are increasingly used in radio communication, an RTL-SDR adapter and smartphone ar ...more
Windows 10 has so many new features that we couldn't even cover them all with one article. From keyboard shortcuts to revamped search functions and all-new window gestures, Microsoft definitely piled on the fresh functionality in the latest version of their operating system. ...more
While certainly faster than writing by hand, manually typing passages from a book or document can be slow and frustrating. But thanks to Google Assistant, this is no longer the case. Whether you need to quote text for an essay or need to win an online argument, all you need to ...more
Before you pull out your phone book (okay, pull up your laptop and start up Google) to find a number for a handyman, why not attempt to fix your broken shower faucet yourself? Yeah, we know it's kind of annoying to find your tool box and remove your entire shower faucet unit, ...more
Oh, LifeHacker, we love you. You've brought us so many handy HowTo's: Hack Wireless Internet, Bypass Blocked Websites, Convert a Laptop Into a Projector, Watch TV & Movies on the Web For Free, 10 Must-Know Google Privacy Settings, and more. And now, another great one: LifeHac ...more
What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, ...more
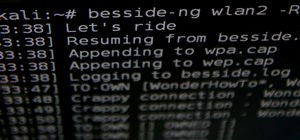
In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encrypti ...more
This year, like every year before it, Black Friday sales are starting earlier than ever. A lot of stores will be opening their doors as early as 5pm on Thanksgiving to get a head start on the madness (and it really is madness). As we've discussed in the past, one of the keys t ...more
Earlier this year, Apple announced Continuity, a feature for Yosemite and iOS 8 that lets you connect your iOS devices to your Mac in order to access apps, receive phone calls, send text messages, and more while seamlessly switching between the two. Within Continuity exists H ...more
With just two microcontrollers soldered together, you can inject keystrokes into a computer from a smartphone. After building and programming the device, you plug it into a desktop or laptop, access it over a smartphone, and inject keystrokes as you would with a USB Rubber Duc ...more
For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been ...more