Firesheep caused quite a stir when it was released last October, giving both hackers and non-hackers instant access to people's account information when on a public Wi-Fi connection. When logged into an insecure website on the same network as someone with Firesheep, you're giv ...more
Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords. Visit us at bleedingedgesecurit ...more
Last Friday's mission was to accomplish solving HackThisSite, realistic 3. The third mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend restore a defaced website about ...more
Leaving your wireless router at its default settings is a bad idea. The sad thing is, most people still do it. Once they've penetrated your network, hackers will change your router settings so they'll have an easy way back in. This allows them to change your network into a she ...more
Having a secure password is essential in today's interconnected world. Hackers are just around the corner, and if you have an easy to guess or hack password that you use for all of your accounts, someone can login to all of your websites very easily. Look at this guide on how ...more
Six months ago, 1.3 million registered users of Gawker Media had their passwords compromised when the site was hacked by Gnosis. The passwords were encrypted, but 188,279 of them were decoded and made publicly available for all to see. Just three weeks ago, Sony Pictures was h ...more
Google AdSense is a beautiful thing. They pay you for posting content online, whether it be through a third-party website like WonderHowTo or on your own website. WonderHowTo seems to be a good place to start from if you plan to make money with AdSense, but it's not the only p ...more
Want to find every instance of a person's name on a particular website? This Googler's guide from the folks at Mahalo will teach you how to do just that. For all of the relevant details, and to get started using this handy Google hack yourself, watch this video tutorial.
This episode of Full Disclosure demonstrates how to hack/crack MD5 password hashes. MD5 (Message-Digest algorithm 5) is a hash function commonly used by websites to encrypt passwords. MD5 is a one-way hash; therefore, to crack the password you most try every possible dictionar ...more
Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educate ...more
We're officially seeking Null Byters on a weekly basis who would enjoy taking their time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job ...more
We're officially seeking Null Byters interested in teaching others! Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowle ...more
Advancements in technology usually lead to the miniaturization of old technologies, and video games are no exception. Since at least 1990, game hardware manufacturers and enterprising DIY electronics enthusiasts have poured their efforts into making full-size video game consol ...more
Keep your Runescape account safe from hackers by following the instructions in this video. Don't get hacked by giving your password away or using unsafe websites. Watch this video and learn how to take precautions against hackers so you can enjoy Runescape worry free.
Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. A ...more
Want to be able to hack into a computer remotely? This method takes a little extra time and cunning to set up, since you will need to first install the ShowMyPc program on your target computer. Once you have installed this program, however, you will be able to go to the websit ...more
In this tutorial, we learn how to use the notepad to get by school internet blocks. First, open up Notepad on your computer, then type in "<html>" "<body>", "iframe src=http://www.youtube.com", then "height=100%", then "width =100%". To finishe, type in "<iframe>>/body><html>" ...more
YouTube user Hacker of None teaches you how to hack Mushroom Madness using Cheat Engine. Start the game from Kongregate website and then run Cheat Engine. Search for your browser, which may be Firefox, Chrome or Internet Explorer, in the Process List and then click Open. Chang ...more
You start the game from the Kongregate website and then run Cheat Engine. Look for your browser in the Process list. It could be Firefox, Chrome or Internet Explorer. Set the value type to Array of bytes. Then check the Hex box above and use the values from the description to ...more
Want Gary the Gadget Guy's background for Club Penguin? Well, there are just a few simple steps to getting the background on CP. Watch this video tutorial to learn how to hack backgrounds in Club Penguin (10/29/09). It works only if the item is available. He is only available ...more
This video tutorial shows you how to jailbreak and unlock your iPhone 2G, iPhone 3G, and iPhone 3GS on firmware version 3.0.1 with Redsn0w and Ultrasn0w. Firmware 3.0.1 fixes the SMS hack/vulneravility Download Redsn0w v0.8: http://thebigboss.org/hostedfiles/red... Download ...more
Club Penguin is a flash-based website with an a virtual world of online games for kids to play. Learn how to hack Club Penguin with tricks and cheats. Watch this video tutorial to learn how to wear member clothes as a non-member in Club Penguin (09/23/09). Download CP Trainer ...more
Club Penguin is a flash-based website with an a virtual world of online games for kids to play. Learn how to hack Club Penguin with tricks and cheats. Watch this video tutorial to learn how to hack Club Penguin with Cheat Engine (09/14/09). This uses Cheat Engine 5.3. Club Pe ...more
Got 3D glasses leftover from the Superbowl? Time to break them out! You will need cheap 3D glasses from television promotions or you can grab them off eBay for this demonstration. Or you can simply make your own 3D glasses red and blue or yellow and blue cellophane. NOTE: Get ...more
Notice: This is probably not new to many people. This *IS* new for some people however, and meant for them! Post interesting cameras you find. Website at http://householdhacker.com Today we'll show you how to look through various security cameras using search engines. For t ...more
Friday's Community Byte was weird. The intent was to do a HackThisSite mission, but upon time to begin, everyone in there was programming without my assistance, with the help of Sol Gates. This is great! It's really awesome that everyone enjoys programming that much and will m ...more
You may have asked yourself, "How do hackers take my password, if the website owner can't?" The answer is simple. When a website stores your login password for the site, it is run through a cryptographic hash function before it enters the database (if the website isn't Sony). ...more
JavaScript is one of the main programming languages that the Web is built on. It talks directly to your browser and exchanges information with it in ways that HTML simply cannot. With JavaScript, you are able to access browser cookies, website preferences, real-time actions, s ...more
This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last fo ...more
The Internet is full of crooks just waiting and waiting for the chance to steal your information. One way that people are getting into your system these days is with fake or rogue applications. These viruses sneak themselves onto your PC either through hacked websites or when ...more
The idea is to buy a few items from IKEA and use them to make a back garden BBQ smoker. The concept is also know as IKEA hacking and the principles are simple, re-engineer IKEA products to make a entirely different item. This video will take you step by step through the buying ...more
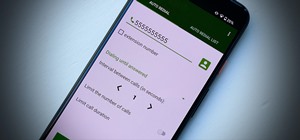
In this article, I'll show you how to easily "hack" Facebook, Twitter, YouTube, and any number of similar account types with an Android app called FaceNiff. FaceNiff allows you to sniff and intercept web session profiles over the Wi-Fi that your mobile device is connected to. ...more
As many of you may have noticed, nearly every Google product (i.e. Gmail, Google search, etc.) has gone through a bit of a makeover since the release of Google+. Big blocky buttons and enormous font sizes are apparently the thing of the future, and with a cool JavaScript hack, ...more
Big Block Games has a pretty good indie track record. They've spent years developing their fun free-roving space game, Black Market, which is still in Beta. And they've spent just as much time with their much simpler, but fully completed physics platformer, Super Goblin War Ma ...more
As advanced gaming systems continue to evolve, older classics like the Nintendo Entertainment System (NES) are one step closer to extinction. They're rotting in the basements of gamers. They're gathering dust at the local pawn shop. Or worse... being thrown out in the trash li ...more
Hacking can't be that hard, can it? At least, that's what it seems like thanks to movies like Hackers, The Net and that last Die Hard flick. Even the Jurassic Park girl's got some game. They all look like they're typing 20wpm, yet can generate a screen full of code in the blin ...more
When the much buzzed Facebook profile page redesign was released back in December, French artist and co-director of ad agency La Bande Originale Alexandre Oudin came up with an innovative way to maximize the visual possibilities of the page. His clever "hack" created a ripple ...more
To hack into Google images follow the following steps. You will first need to open a new internet browser window and go to Google, then load their images website. Next type into the search bar your image query and press search. Once you have gotten your search results paste th ...more
Nowadays many schools and colleges have blocked the social community sites from accessing them through school computers. The video shows how one can access to these sites using a command prompt. Follow these steps and access the blocked sites: 1. Go to the start menu and ope ...more
There's a great new web game called Epic Duel out on the internet, and everybody's playing it, but not everybody's hacking it, except you! Outshine them all with this EpicDuel cheat with Cheat Engine 5.5. Learn from this video cheat: how to hack EpicDuel for money (12/31/09). ...more
Are your fish starving? If they are, you need to do something about it, and quick. Well, there's no quicker solution to feeding your fish than hacking Happy Aquarium with Cheat Engine. Watch this video tutorial to learn how to hack unlimited food in Happy Aquarium (10/29/09). ...more
Hacking seems like the only solution to today's flash-based games, like Club Penguin. If you can't do it yourself, let a cheating program do it for you. That's the new fad. Cheat Engine. That's all you need to hack online games. Watch this video tutorial to learn how to cheat ...more
This is Cheat Engine hacking for Club Penguin. If you want more coins, you have to hack your way to them. And to hack your way to more coins, you're going to need Cheat Engine. Watch this video tutorial to learn how to earn Club Penguin coins with Cheat Engine (10/23/09). Dow ...more
If you have any problems you can email me or visit my website at www.gapto.webs.com!!! This video shows you how to hack into Restaurant City using Cheat Engine and Restaurant Tools v5. Restaurant City is a Facebook game that allows you to create your own restaurant. Descrip ...more
I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to rememb ...more
There are a lot of things on your computer that can reveal information about you when you are surfing the Internet. If you are like me, then you will do anything to maintain your privacy and prevent those little leaks of information from happening. Here's a list of a few of th ...more
Welcome to another Community Byte announcement! For the past few Community Bytes, we coded an IRC bot, and hacked it. Then, we created a web-based login bruteforcer! This week we are going to start something a bit different. We are going to start going through the missions at ...more
JavaScript is the language of the internet. It is what allows us to create dynamic, interesting webpages that are fast, web-based applications and so much more. The primary use of JavaScript is to write functions that are embedded in or included from HTML pages and that intera ...more
eBooks are an amazing thing, especially with Amazon's Kindle. What's irrtating about eBooks as that you have an infinite selection of books at your fingertips, but they all cost so much! Well, as always, Null Byte has a trick up our sleeves for nabbing free ebooks from Google. ...more
Got a knack for speeding? Like running red lights? Believe or not, the police have better things to be doing than pulling you over, like catching real criminals. That's why more and more cameras are popping up at known speeding zones and on street corners—so the cops can clean ...more
For most thrill-seekers, skydiving alone is an adrenaline rush worth experiencing only once, but for the death-defying, elite skydiver, the wingsuit is the next step in daring midair adventures. But thankfully, we people who like our feet planted on the ground can enjoy the th ...more
By now, many of you may have heard about iPhone tracking and recording your location data, but is there anything else being extracted from cell phones without our knowledge? If you're a Michigan state resident, the answer is an alarming "maybe". Michigan's police department h ...more
Understandably, the tragedy in Japan has substantially risen the level of worldwide radiation-related hysteria. So much so, as an alternative to stampeding health food stores for iodine tablets, crafty individuals and organizations are hacking together personal radiation detec ...more
This past Sunday, a group called Gnosis launched a massive hacker attack on Gawker media, one of the web's most popular blog networks (Lifehacker, Gizmodo, Jezebel, io9, Jalopnik, Kotaku, Deadspin and Fleshbot). 1.3 million registered users' passwords were compromised, and 188 ...more
Cheating ruins everything. Cheating makes game play unfair for others who may be truly competitive and strategic. Cheating makes others disrespect and un-friend you. There can be unforeseen consequences, like getting viruses, trojans or your account hacked from downloading a c ...more
Flash video. It's what all smartphone users have been waiting for. Why has it taken sooo long? And why is Apple still resistant? Here's the scoop, via Wired: "Adobe is releasing Flash Player 10.1 for mobile phones and desktops today. And it is piggy-backing on Google’s fast ...more
Have you ever noticed that whenever you setup your voicemail account after getting a new cell phone number, it asks you to create a security pin to access your voicemail from other phone lines? When you call your home or cell number from another phone, after a few rings your ...more
Here's something fun for the Null Byte community to do—a coding competition! This week, I wanted to get everyone involved by offering you all a nice library of possible program types to choose from and try to code. At the end of this competition, all of the submitted programs ...more
Last Friday's mission was to accomplish solving HackThisSite, realistic 2. This second mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend take down a racist hate-group ...more
The community tore up the first realistic mission last week. You've applied the techniques learned in the basic missions to a real scenario, so I'm pretty content. The realistic missions are where the learning gets intense and where we can apply real knowledge to extremely rea ...more