In the latest example of life imitating art, IBM has applied for a patent for a video censoring system that looks a lot like the "Arkangel" child monitoring system from the latest collection of modern sci-fi fables from Black Mirror on Netflix. For those who haven't seen the ...more
A testament of man vs. machine will air on February 14th, 15th, and 16th when IBM's supercomputer "Watson" is pitted against the world's fiercest Jeopardy players, Ken Jennings and Brad Rutter, for a chance to win a cool $1 million. It took researchers four years to build Wats ...more
This month, the power of artificial intelligence will be coming to more augmented reality developers as a leader in the game and 3D software development space and a major force behind the current school of cloud-based AI have officially announced a new partnership. In a post ...more
Accidents will happen. This brief how-to will guide you through the process of disassembling, cleaning and reassembling an IBM 5100 series mobile smartphone quickly and efficiently without damaging any of the components, the first necessary step of any successful repair or res ...more
The PowerForce G3 ZIF (Zero Insertion Force) is the super-fast, yet economical CPU upgrade for your "Beige" Power Mac G3 desktop or minitower, "G3 All-in-One" educational model, Blue and White Power Macintosh G3's and the Power Macintosh G4 "Yikes." This video tutorial will wa ...more
The number of passwords I have for different websites and emails is easily in the triple digits. And if I had to actually remember all of those individual passwords, I would be locked out of accounts on a daily basis. That's why I use the "remember my password" feature whenev ...more
During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform O ...more
Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be a ...more
Remember what life was like before your iPhone? Before there were palm-sized smartphones with seemingly endless features, there were phones like Motorola's RAZR that peaked with its embedded camera. Before that, there were simple flip phones with texting capabilities, bulky tw ...more
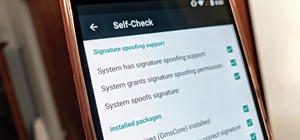
Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack. That's because the database—alm ...more
If you thought humans were reading your résumé, think again. Robots do, and their one solitary objective is to systematically crush the hopes and dreams of those who don't make the cut. Instead of paying a few humans to read thousands of résumés over a couple weeks, many compa ...more
Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers beca ...more
Not all weather sources are equal. When you're looking at the forecast, you hope that it's at least semi-accurate so you can plan the week and days ahead, but many sources are unreliable. And with the famous Dark Sky API shutting down on March 31, 2023, you'll need an alternat ...more
Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal. This ...more
It's 1976. The hottest arcade game on the market is Blockade (or Blokade), an 8-bit maze game for 2 players. You and your opponent must move your characters around the screen in 90-degree angles, leaving a solid line behind them. Whoever runs into one of the solid lines first, ...more
Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positi ...more
Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way ...more
If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?" Many of the top names in the industry from the 2018 edition remain the same, but their positions have shuffled. The p ...more
Windows users have been getting a lot of bad news about their security lately. First, we found out that passwords in Windows 7 and 8 can easily be exploited if password hints are enabled, and now, Russian password-cracking software developer Elcomsoft has found another huge vu ...more
Back in 1982, the Commodore 64 home computer was released by Commodore International for $595 (which would now be close to $1,300). It featured an 8-bit microprocessor, 16-color video microchip, awesome sound chip, parallel and serial capabilities, and a whopping 64 kilobytes ...more
As practically the entire Steampunk world knows by now, IBM has predicted that Steampunk will be the big new trend from 2013 to 2015. They based this prediction on their computers, which sift through broad swathes of the internet in order to see patterns that may help commerci ...more
Need some IBM Lotus Notes help? Well, check out this video tutorial to learn how to connect to a Lotus Domino Server from Lotus Notes. This is a very quick connection to the Lotus Domino Server from Lotus Notes. Easy to follow.
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to break dow ...more
Augmented reality is expected to eventually change everything, and the prevailing view is that those changes will be for the better. The converse view, however, is that the technology will further erode privacy. A new Netflix film called Anon, starring Clive Owen and Amanda S ...more
WonderHowTo welcomes guest contributor, +Ryan Crowe - formerly the man behind GPlusTips. Crowe will be providing tips and tricks on how to use Google+ in interesting and innovative ways, and the self-proclaimed Google+ User Experience Enthusiast is nearly ready to launch a web ...more
One tweet can get your fired from your job. At least, in the cases of Gilbert Gottfried, Rashard Mendenhall, Ozzie Guillen, and Mike Bacsik, who were all either fired or forced to resign from their jobs after posting regrettable tweets online. An ex-GOP aide for Jeb Bush was ...more
How did we get to the age of smartphones, ereaders, laptops, and crazy touchscreen displays? Gizmodo covers Steve Wozniak's recent presentation of nine key gadgets that have deeply influenced the tech God's work. A few highlights below; click through for the full survey. Stibi ...more
If there is a major blind spot in the AR space in 2019, it's the impact that blockchain technology will eventually have on the software distributed in AR clouds. For the uninitiated, the quickest way to describe blockchain technology is as a method of assigning unique attribu ...more
Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use ...more
The world of investment and finance can be labyrinthine in its very nature — and even more complicated in regards to augmented and mixed reality. While these new emergent technologies are teeming with explosive levels of unrealized potential, there's still a big layer of uncer ...more
Back to the Future Part II missed wildly on many technological advances for the year 2015, such as flying cars and rehydration ovens. However, it connected on several predictions, such as video calling and biometric security, and it was in the ballpark (pun intended) on others ...more
In the past 25 years, there have been five generations of home video games systems. Since Nintendo changed the world by releasing the NES in 1987, there has always been at least two consoles competing for dominance in the wild west of the games industry. This competition— coup ...more
With give or take 250 million cars in America, odds are most city dwellers waste time hunting for parking spots. And while a smartphone app can't make free parking spots magically appear, it can aid in the searching process. The Parker app isn't new to the iPhone, but its fou ...more
Thanks to the expanding universe of augmented reality tools being made available, increasingly, anybody can liven up sleepy office meetings with immersive computing. Now, a new 3D presentation-sharing service for the Magic Leap One has PowerPoint is in its crosshairs (someone ...more
If you're looking into buying shoes from DSW on Black Friday, then you can save an extra 20% — but only if you smile more. An augmented reality mobile web ad campaign created for the retailer by PadSquad asks customers to smile for the camera. According to a PadSquad spokespe ...more
With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years h ...more
Greg French talks to us about the different ways to reboot a computer to resolve issues in the computer. The first way is by pressing F8 key while startup after rebooting the system. When you insert a wrong driver for video card or something, sometimes when you boot the comput ...more
While many of you were off surfing and lounging on some sandy beach or trying to figure out how to balance work with sky-high summer temperatures, I've been talking to all the companies that make augmented reality what it is today. My best opportunity came during the recent A ...more
The US Department of Education has put together a competition called the EdSim Challenge with a $680,000 purse to facilitate next-gen education. The event calls upon augmented and virtual reality, as well as video game developers, to bring immersive simulation concepts to prep ...more
In this Tuesday's Brief Reality report, there's a trio of stories from the healthcare world where augmented reality is helping out with surgical microscopes, asthma treatment, and other diagnostic and treatment tools. There's also something for all of you AR/VR storytellers ou ...more
The Washington Post believes augmented reality adds an extra layer to stories, and they're doubling down on that belief by adding in new AR features into their already popular "rainbow" news (iOS and Android) and Classic (iOS and Android) news apps. Last year the media compan ...more
While the world is only recently becoming aware of its existence, augmented reality has been around in some form or another since the '90s. In the last decade, with the advancement and miniaturization of computer technology — specifically smartphones and tablets — AR has becom ...more
Apple computers have long been maligned as the computer for Starbucks aficionados and graphic artists. "Dude, have you used Excel on a Mac? It's terrible," says everyone that owns a Dell. The whole PC versus Mac battle was encapsulated in what I think to be the greatest ad cam ...more
NTFS? What is it? It stands for New Technology File System, but what does that mean? Well, it's the standard system for filing in Windows NT, including all later versions, up to the current Windows 7, but Mac users can take advantage of this file system, too. If you’re confuse ...more
Apple has billed ARKit as a means to turn millions of iPhones and iPads into augmented reality devices. The refrain is similar for Kaon Interactive, a developer of product catalog apps for businesses. Kaon's High Velocity Marketing Platform powers product catalog apps for com ...more
The future of augmented reality isn't on your smartphone or face, it's in the everyday items all around us. At least that's the belief of Gordon Meyer, the vice president of marketing at New York-based startup Lampix. Meyer joined me recently in New York to talk about why he ...more
A week after the L.E.A.P. Conference, our cup of Magic Leap news continues to floweth over, with the company's content chief giving us some insight into the company's strategy, and Twilio sharing what its virtual chat app looks like. Elsewhere, the demand for AR among busines ...more
Need some IBM Lotus Notes help? Well, check out this video tutorial to learn how to have Lotus Notes remember the sorting of emails. This is a very quick and easy way of getting Lotus Notes to remember the sorting of emails. Easy to follow.
As someone who grew up adamantly complaining every time my parents dared to turn on talk radio in the car, I can admit it's a bit weird that I have a love affair with podcasts. I can't help it! Even though podcasts are essentially the modern-day customizable talk radio, I choo ...more
Since its release in 1991, Python has become one of the world's most popular general-purpose programming languages. From data mining and web programming to cybersecurity and game design, Python can be used for virtually everything online. When it comes to coding languages, Py ...more
Amazon Web Services (AWS) is the premier on-demand cloud computing platform. Offering a wide range of APIs to companies, governments, and individuals on a pay-as-you-go basis, this Amazon subsidiary pulled in over $35 billion in revenue in 2019 alone. Opportunities for workin ...more
What is Technology? Technology is all around us. Some technology we take for granted while other technology we allow ourselves to be amazed and baffled by. Technology is more than modern technology companies like Cisco Systems, IBM, and Google. Technology exists in our every ...more