In this video, we learn how to identify number types. You will need to figure out what numbers from a list is a rational numbers in your math equations. A natural number is a counting number (1,2,3). A whole number is a natural number and zero (0,1,2,3). An integer is a whole ...more
There are a number of diaper rashes that your baby can face. Sometimes a rash can be a great risk and hard to treat. You may need to take your baby to a doctor if you have tried treating their rash with different types of ointments/creams/medication and the rash has not gotten ...more
Pimples are definitely not a one size fits all condition. In this video, we'll look at the various forms of acne, from a basic blackhead to clusters of comedones. We'll also teach you the best skin care secrets to zap that zit! Health Guru is a site that produces videos which ...more
Seizures can take a variety of forms. Learn more in this video. Health Guru is a site that produces videos which provide medical advice in a number of areas: Pregnancy, Sex Health, and College Health. With the aid of Health Guru, you can understand your aches and pains, stay ...more
Heart disease affects more than 20 million Americans. Let's explore the various forms that heart disease can take. Health Guru is a site that produces videos which provide medical advice in a number of areas: Pregnancy, Sex Health, and College Health. With the aid of Health G ...more
There are two types of fly fishing flies, and they are distinguished as surface and sub-surface flies with the surface ones being called dry flies. This tutorial will teach you how to tell the difference, and what this means. Make sure you know what's what and make sure you ca ...more
Watch as a seasoned professional discusses various types of pet fish in this free online video about exotic pets. Part 1 of 24 - How to Identify types of fish. Identify types of fish - Part 2 of 24. Click through to watch this video on expertvillage.com Identify types of fish ...more
Don't know much about the dinner table? You know the basics: you eat from a plate, you use silverware to shovel it in and you drink from glassware. But what about if you're at a fancy dinner? Would you be able to distinguish a juice cup from a champagne glass? A white wine gla ...more
Phil Macdonald and Trent Munro discuss how you can identify wave types for surfing. There are two types of waves: rolling and clenching waves. Rolling waves break far from the shore while clenching waves are more dangerous.
Know the different types and varieties of mushrooms, what they taste like, and how to serve them to add an assortment of tastes, textures, colours and sizes to your meals. Profiles all Canadian grown mushrooms; white button, crimini, portabella, shiitake, oyster and enoki.
7-year old Chief Culinary Officer (CCO) of Lizzie Marie Cuisine presents kitchen safety tips. Watch this video tutorial to learn about knife safety and what those different knives do in the kitchen!
A banner alert for notifications is like the Robin to our iPhone's Batman—they're taken for granted and don't really get the recognition they deserve. Yes, they can be disruptive at times, but just like Robin, they can be necessary for getting things done. I can't count the m ...more
Check out this instructional home repair video to learn how to identify the model number on your washing machine and dryer. Knowing the model number can be essential in finding the right replacement parts. People make the mistake of assuming that the name and number on the fro ...more
Check out this instructional home repair video to learn how to identify and find your manufacturer's label and model number on your refrigerators and freezers. The model number is usually essential. People make the mistake of assuming that the name and number on the front pane ...more
If you're going to start a fire in the wild, you will need the right kind of rock. This great little video helps you identify the type of rock you'll need to light a fire in the wild successfully. You'll need some high-carbon steel for striking your sparking rock; then you'll ...more
Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a sin ...more
Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can e ...more
Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL in ...more
A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials. ...more
When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. Th ...more
With GPS chips and Wi-Fi positioning systems, a modern smartphone is capable of tracking its user's location with pinpoint accuracy. This being the case, it's strange that the most common text message sent today is still "Where are you?" So if you're ready to get out of the s ...more
You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discove ...more
There are times when physically interacting with your iPhone is less than ideal, like when you're cooking or driving. Fortunately, iOS 13 has you covered regardless of the circumstance you may find yourself in. With the new Voice Control feature, you can control pretty much ev ...more
Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the ...more
The community of bacteria that lives in our gut has a lot to tell us. It can give clues to what we eat, the environment we live in, and diseases and disorders we may have. Now, scientists have linked these bacterial species to how we feel. A new research study found an associa ...more
The number of households in the US that go hungry because they lack money for food hit a high of almost 15% in 2011. While that number continues to decline, nearly 13% of American households still go hungry. Malnutrition — either from not eating enough or not getting enough n ...more
The Centers for Disease Control and Prevention (CDC) just reported some upsettingly high numbers of human papillomavirus (HPV) in adults. In data retrieved from 2013–2014, 22.7% of US adults in the 18–59 range were found to have the types of high-risk genital HPV that cause ce ...more
Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem. ...more
The bacteria in our gut — a community called the gut microbiome — have been in the spotlight a lot lately. What we're learning about how our intestinal bacteria adapt and grow with our bodies could help athletes perform better, according to researchers starting a company focus ...more
Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve ...more
As fun as it is to see Fido's face light up when you feed him table scraps, American dogs are getting fat. The good news is that research is homing in on nutritional strategies to boost canine capabilities to maintain a healthy weight. In 2015, in a survey of 1,224 cats and d ...more
Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know. Possibly the most popular and well-known reconnaissance tool currently ava ...more
Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Althoug ...more
MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer neve ...more
Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private cha ...more
Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. ...more
International Pet Travel: Taking Your Pet Animal to a Foreign Country If you are taking a pet to another country (permanently or for a visit), contact that country's consulate or embassy for information about any requirements that you must meet. A list of consulates can be fo ...more
Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians acro ...more
Welcome back, my tenderfoot hackers! WordPress-based websites are among the most numerous on this planet (maybe other planets too, but I can't vouch for that). According to WordPress's own website, WordPress powers 23% of the top 10 million websites. That's approximately 2.3 ...more
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series. This tutorial is for those who already know how to program in C and have a basic understanding how networks w ...more
Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, i ...more
There are a ridiculous number of onion varieties, so choosing the right onion can make my head spin sometimes. With four distinct types of "green onions" that all look almost the same, I'm guessing you have the same issue—but not once you know the secrets to identifying and pr ...more
Tequila is a hard liquor that's often been misunderstood. Produced from the agave plant, this aged spirit has complex flavors that bloom the longer it's aged and can rival the finest scotch. Yet tequila has a terrible reputation for inducing hangovers, which is untrue, accord ...more
There have been mumps outbreaks in three different US colleges so far this year as instances of the illness are on the rise, according to the Centers for Disease Control and Prevention (CDC). Three students at Illinois State University and about 20 at Louisiana State Universi ...more
INTRODUCTION In this world of Internet era, almost everyone wants to create theirs own web presence by either hosting their own blog, articles, photos, videos, reviews, etc etc . But some people choose their own way and decide to have something bigger! What is it? Its a websi ...more
The Google Now on Tap feature puts the power of Google Search inside each and every application on your Marshmallow-powered device, allowing you to retrieve contextual results based on the content on your screen. Aside from results, Now on Tap can also perform certain actions ...more
Love is the spice of life — it is also the microbes that couples share through sickness and in health, through the bathroom and in a hallway. The skin is our largest body organ. Your skin is the most significant protective barrier between squishy, vulnerable innards and a pat ...more
Google just rolled out a revolutionary feature to its Pixel devices — Google Lens. Previously, Lens had only been available in the Photos app, but now, whenever you want to learn about something in the real world, you can just bring up Google Assistant, turn on the camera, the ...more
Devastating and deadly, land mines are a persistent threat in many areas of the world. Funding to clear regions of land mines has been decreasing, but new research may offer a less dangerous method of locating hidden, underground explosives by using glowing bacteria. There ar ...more
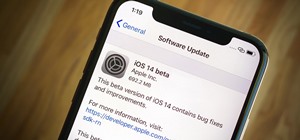
While iOS 11 is ready to take over your iPad, iPhone, and iPod touch, let's take a step back and check out all of the new features that iOS 10 brought to the public when it was released to everyone in Sept. 2016. Some of the updates from iOS 9 to iOS 10 were huge, as you'll s ...more
A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge. The goal in this article is to acquire a target's .plist file which contains the ...more
SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool c ...more
Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic An exploit is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability in order to cause unintended or unanticipated behavior to occur ...more
There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture hands ...more
Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to id ...more
Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target. Thanks to a pair of recon tools coded in Python, it takes just seconds to research how a website or server might be vulnerable. No matter what platform ...more
The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in r ...more
If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment. Using a directional Wi-Fi antenna and Wireshark, we can create a display filter to target any device in range to plot the signal strength on a gra ...more
If you've read or watched anything Harry Potter before, you know friendship and teamwork are huge parts of the story. The same goes for Harry Potter: Wizards Unite, with its "Wizarding Challenges." Here, you can tackle Fortresses full of Foes alone, but why do that when you ca ...more
Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scan ...more