For this week's review round-up, we bring you two games from opposite sides of the indie world. One is a free online hybrid shooter/platformer combining elements of Team Fortress 2 and Minecraft. The other involves driving jeeps around and shooting things as fast as possible. ...more
Everyone has used a ruler at some point in their life, whether for art sizing, blueprint plans, or sizing up your widescreen television on your living room wall. But there's a lot of little ticks on the ruler that you may not be aware of. Your ruler shouldn’t be used only to d ...more
One can easily get rid of acne scars without surgery by means of following steps. Identify the type of acne scars you have. See a dermatologist who can tell the difference between types of scars. For example, scars may be classified as ice pick, boxing, rolling or hypertrophy ...more
It’s a game, it involves numbers, it’s fun, it’s KenKen! Understanding the goals and rules of this fun, numbers puzzle will give you the skills you need to win. Have fun working your brain and passing the time with KenKen. KenKen can be a great way to challenge your puzzle-so ...more
Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. I ...more
In python, or any scripting language for that matter, there are certain things that you will carry with you throughout your entire scripting career. Some of the most basic things that you will keep with you are output, variables, and their value types. We'll start by going ove ...more
Google's new cross-platform video chat app, Duo, is finally making its debut today, following a long waiting period that began in late May. The app was heavily teased during the keynote speech at Google I/O, but was not made available for download until now, so any early hype ...more
Several recent research studies have pointed to the importance of the microbes that live in our gut to many aspects of our health. A recent finding shows how bacteria that penetrate the mucus lining of the colon could play a significant role in diabetes. The new study led by ...more
Google Lens is a fantastic addition to Google Photos for Android and iOS that allows your smartphone to identify a number of things in your pictures, like landmarks and contact info. Using this power, you can even find out how to buy almost any product you've taken a photo of ...more
When a dead body is discovered, finding out when the person died is just as important as finding out how the person died. Determining the time of death has always involved lots of complicated scientific detective work and less-than-reliable methods. However, a study by Nathan ...more
Learning to make giant bubbles for this video has been the most fun I've had with a project in a long time. It's addicting to try to get them to grow bigger and bigger than the ones before. Since filming this video, my skill has improved tremendously and the bubbles you're abo ...more
Just like Instagram, Photoshop Express for Android and iOS has its own set of filters you can quickly apply to any photo. It's simple, fast, and more customizable than using Instagram's pre-made filters. The options in Photoshop Express allow you to edit and change your filter ...more
The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you n ...more
Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often ...more
A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website d ...more
Hello! This post is not about craft, it's about cyber bullying. If you ever had such an experience, that an unknown hacker was bullying you for no reason at all, please follow my words. Thank you! Step 1: Let All the People You Know That Your Are Being Harassed. Hacking is th ...more
3D printers allow hackers and makers alike to create something from nothing. They're an incredible technology that lets you build protective cases and covers for gear such as a wardriving phone and Raspberry Pi-Hole. 3D printers can even help you out in a bind when something b ...more
This video will show you how to identify addons slowing down browser speed. If you have enabled a huge number of addons all of which is not necessary and consumes huge memory will slow down speed. Now you could identify which add-ons consume how much memory and are they necess ...more
It is finally happening. After not having a major update since August of 2016, HoloLens owners everywhere will soon get a number of new features added to their devices. At least if they are members of the Windows Insider program. Throughout 2017, the Mixed Reality Team at Mic ...more
A terrifying antibiotic-resistant superbug, one thought to only infect hospital patients, has made its debut in the real world. For the first time ever, the superbug carbapenem-resistant Enterobacteriaceae (CRE) infected six people who hadn't been in or around a hospital in at ...more
Recently, there have been some questions regarding networking popping up and we have decided to put together this series to try and cover this gap. In this guide, we will cover the basics of IP addresses, both internal and external, and begin to have a a look at how this wond ...more
Chrome, Firefox, and Safari all provide built-in features that allow you to save your username and password for your favorite sites, making the process for entering your credentials a breeze when you revisit them. While this automation does make your life a little easier, it ...more
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys! Reconnaissance is a big part in the hacking community. Penetration testing is most effective when you have a good grasp on the environment being tested. If you're an ...more
If you transition to an Apple Watch from another wearable like Fitbit, you might be a bit confused by the new calorie burn counter. Instead of ending your day with thousands of calories burned, your watch says you've burned just hundreds. Could it be you're less active with yo ...more
Augmented and mixed reality developer Arvizio is working on a suite of software solutions for enterprises that will extend HoloLens capabilities as a full-fledged collaboration and conferencing tool. The company will demonstrate its Mixed Reality Studio suite to attendees at t ...more
Over 1.2 million people in the US are infected with human immunodeficiency virus (HIV)—and one out of eight of them don't know it. Even after decades of intense research into the virus, there's still no cure for it. One of the big problems is that the virus hides out in certai ...more
Usually, we think of vaccines as preventative, a shot we get to prevent the flu or some childhood disease like measles or mumps. But there are vaccines for other purposes, such as the ones studied by researchers from the Netherlands. A report published in Current Opinion in V ...more
Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make wi ...more
Bed bugs are brown and creepy. Could you spot one in your hotel room? A new study reveals most people are freaked out by bed bugs, but only about 35% could identify one. In a new study published in American Entomologist, scientists from the University of Kentucky examined how ...more
Welcome back Java programmers! In this tutorial we'll being going over Variables/DataTypes and Type-casting So What Are Java DataTypes? Like in many other programming languages, you have variable types. Such as ints, doubles, chars, etc. They are used to instantiate the kind ...more
The Pixel 2 has a number of new unique features. One of the most interesting is the Now Playing option to identify songs you hear on a daily basis. Now Playing displays the artist and title of songs playing in the background of your day and shows this information on the lock s ...more
We use smartphones for just about everything, and while that may be beneficial to us in our day-to-day lives, it can also be used against us in the court of law. Law enforcement officials can seize smartphones and give warrants to Apple, Google, your cellular provider—whoever ...more
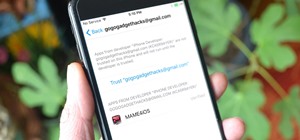
Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to f ...more
Hello there, people. Today, I am going to show you how to extract the essence from a useful plant, using either alcohol or olive oil. This is how you take a plant and turn it into a useful (and preservable) medicine. For those of you who know nothing about herbal medicine, let ...more
Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost! Everything is made up of bits in the computing world, like the atom makes up the basic building blocks of everyday materials such ...more
Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, onlin ...more
While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot ...more
There is a reason the Amanita phalloides mushroom is called the "Death Cap." It can kill you. Mushrooms are a type of fungi, an organism that produces thread-like mycelia that often produce spores. Spores allow the fungi to reproduce. Molds, lichens, and yeast are all fungi, ...more
There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you t ...more
Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes. Any self-respecting hacker must be ...more
While Snapchat is no stranger to location-based AR scavenger hunts, the app's new world-facing game adds some environmental understanding to the mix. This week, Snapchat launched a new Snappables game dubbed Scavenger Hunt. However, while most Snappables games use the front-f ...more
Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And ...more
In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, e ...more
Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available. Metasploit enables us to use pre-written exploits against known vulnerabil ...more
Welcome back, my greenhorn hackers! Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It ...more
With a predicated increase in the number of Lyme disease cases in the coming spring season, new research endorses the use of bait boxes to control ticks on the rodents that serve as their hosts. With cases spread across the country from coast to coast, Lyme disease is particu ...more
Whether scheduling meetings, events, tasks, or even keeping tabs on the weather, a good digital calendar can help you stay on top of your game in ways that a normal calendar could never do. Indeed, there are many calendars to choose from, but Google Calendar is one of the best ...more
In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the re ...more
Got a clogged kitchen sink? Before you reach for the plunger, see if you can fix the problem using Alka-Seltzer tablets and white vinegar. Simply drop four Alka-Seltzer tablets down the drain and follow that with 1 cup white vinegar. Let sit for 10 minutes before flushing the ...more
Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications ...more
The office of your physician, or your local hospital, is where you go when you need medical care. But it could also be where you could pick up a life-threatening infection. Most people understand that the use of antibiotics has led to the development of "superbugs," germs tha ...more
If there's an influential tweet, you can see what people are saying about it by reading its comment thread. But what about quote tweets, aka tweets someone posted on their own timeline that quote the initial tweet? These don't show up in comment threads, but there is a way to ...more
Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against t ...more
Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks fro ...more
In the last iteration of how to train your python, we covered if/else and conditional statements. We're going to diverge a little today and cover lists. Lists are simply that, lists. It is a set of values located under one variable. Now that we know the definition of a list, l ...more
We are in the midst of a mini-boom for communications tools designed for augmented reality headsets, with the introduction of Avatar Chat and Mimesys for Magic Leap One and Spatial for the HoloLens within the last few months. However, these apps have largely been siloed to on ...more
We know Android 9.0 will have the formal designation of Pie, following Google's age-old tradition of naming their OS after items you'd normally find on a dessert menu. And thanks to a slew of new features that centers around your overall security, P could also stand for Privac ...more
With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardri ...more
Apple is speeding things up in the iOS 11.4 development. The company released to developers the fifth beta for iOS 11.4 on Monday, May 15. Public beta testers got the update just hours later. The update comes just one week after the release of the fourth 11.4 beta, which intro ...more
Mushrooms are glorious: they're nutritional powerhouses, add meaty savor to just about any dish, and are cheap and plentiful (mostly). But just when you thought you knew best how to use edible fungi (in gravies, as portobello burgers, stewed and served over pasta, just to name ...more