This paper airplane has got to be one of the best airplanes of all time. It's called the Nakamura Knot for theknot in the center of the plane that keeps the airplane well-balanced. However, these airplanes take a couple good trials to get right. Once you've constructed it corr ...more
Don't buy those $100+ laser pointers. Watch this video, and for under $50 you can make your own that is capable of burning, popping balloons, and cutting things! Casing/Lens (650nm 10mw 12mm X 30mm case): http://mfgcn.com/_wsn/page2.html Do not make the mistake I did the fi ...more
Our expert, Laura Nessen, shows you how to create a holding tank for your hamster. Learn the right kind of hamster bedding to buy. Also, Laura gives you tips for finding accessories and toys for your hamster. So, take some time, and learn how to make your hamster as comfortabl ...more
Tired of the same old boring things on the internet. Learn how to fool everyone and fake your own death. Through careful planning you too can join the likes of Elvis, Bigfoot, and Nessie the Lockness Monster. Fake your death online and have a grand ole time fooling all of the ...more
This video demonstrates how to do a close-grip lat. pull-down. This primarily works the upper back and upper latisimus dorsi and secondarily works the biceps. Don't jerk the bar down using momentum in an attempt to complete the repetition, control the weight at all times. Do c ...more
This video demonstrates how to do a preacher curl with a dumbbell. you hold a dumbbell in your right hand so that the edge of the bench is under your armpit and your arm is fully extended over the bench surface. Raise the weight towards your chin, keeping your wrist locked at ...more
Blake Whitaker has been playing dominoes for a long time and now he's here to teach you how to play. In this series, he goes over what you'll need, how to play, how to score, and some demonstrations. Part 1 of 6 - How to Play dominoes. Play dominoes - Part 2 of 6. Click throug ...more
Materials Needed: Panda Costume, Robot Costume, Burrito (unwrapped)Okay, to tell the truth, i am not 18 or older, i am a 15 and a half year old teenager who has admired you guys for years and has been dying to meet you all. my idea (my best friend Steven Vaughan also helped wi ...more
This series goes over setting up and playing roll playing games like Dungeons and Dragons. It even tells you how to start writing your own games. Part 1 of 9 - How to Play role playing games. Play role playing games - Part 2 of 9. Click through to watch this video on expertvil ...more
The title of this prank doesn't really tell everything about it. So here it is. Imagine Johnny Knoxville walking down the road among dozens of other pedestrains. Have police sirens blaring in the backround. Have a white van speeding hen come to a screeching halt. Have Bam marg ...more
This prank has to be where people walk all the time.... You start off by putting portable or wireless speakers that would play a playback of car tires skidding on the ground, in cylinder shaped trash cans right by a busy street full of cars and where a lot of spectators would ...more
alright so my dumb friends and I were sitting just bullshitting and came up with an idea for a gnar prank. if ya got balls though, this shit might get your ass killed. we want you guys to skydive down and land in a state correctional facilities' outdoor recreational area, and ...more
so victim gets in the shower. person locks/blocks them in the shower. victim does not know they are locked in. let victim get all wet and fill the shower up with a bit of water. (before victim gets in shower) hook up a stun gun, or some other low voltage torture machine to the ...more
It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something. Our rush to the future is too fast to keep up with. Denying technology is ignorance, isolat ...more
Who pays for live TV anymore? Better question, who watches live TV anymore? With a ton of streaming services available, there's no room in our lives for things like schedules, commercials, or going weeks between episodes. (What is this, 2010?) But streaming services think peo ...more
Trendy restaurants are fun, but waiting in line isn't. Too often, we arrive at a location to find a queue between us and our dinner. If only we could know when wait times were down so we could go out at the optimal time. Well, Google wants to help you out with that. A new fea ...more
As augmented reality becomes more and more integrated into the mainstream, people have been wondering the future of AR is going to look like. Jay Samit has a pretty clear idea. Samit is an expert in digital media innovation. He has been called a leader in digital "disruption" ...more
No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly! I hope you had a good Christmas and happy new year! Update1: Added the section "weaponizing your Android" where I talk about apps and fundamental Kali ...more
Believe it or not, yes, Youtube is getting ready for high definition. But, because (me thinks) of the cost structure involved, they ain't advertising the hell out of this feature, yet. This tutorial from a soft spoken asian accented man tells you how to download and view a vi ...more
While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are al ...more
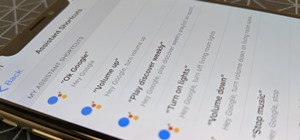
Despite a rocky start with plenty of feature disparity, the Google Assistant now provides a pretty consistent experience regardless of what device you're using it on. Be it Android, iPhone, or Google Home, the AI behind the Assistant is virtually identical — including its quir ...more
A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physi ...more
While The New York Times' augmented reality section has largely been dormant in 2019 (so far), USA Today has continued to crank out AR news stories. On Monday, the news outlet published a feature story about the world's tallest buildings (and the recent lack of new skyscraper ...more
There's nothing worse than driving up to your destination only to discover that there isn't a parking spot in sight — but thankfully, Google Maps will soon have you covered. Android Police reports that the latest beta version of Maps V9.5 will incorporate a number of handy to ...more
Facebook Messenger has now incorporated a live location sharing feature, one week after Google Maps revealed its own real-time location tool. On Monday, the social media giant announced the new feature, which will allow users to share their live whereabouts with friends at the ...more
What you probably don't know is when you remove a file on your system, it is actually still saved, and not entirely removed. Let me tell you how to get rid of it completely. Overview: When you delete a file it is not removed entirely from your drive and can be recovered. No ...more
Yes, screen savers are fun to look at for a few seconds, but those animations actually used to serve a purpose beyond simple entertainment. In older CRT and plasma monitors, and even newer OLED ones, leaving a static image on the screen for an extended period of time could cr ...more
Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then. The idea is to write simple scripts ...more
Getting those perfectly winged eyeliner can be such a trouble at times. Especially for those with shaky hands, or less stretched out eyes, this can be really difficult and a very time consuming process. Video: . Products used: Sugar Eye Told You SO Waterproof Eyeliner Twist a ...more
All of Apple's products are praised for being extremely easy to use. So much so, that your grandma can pick one up and be a "pro" within a few hours. However, this isn't necessarily a good thing for us real power users who want more granular control of our devices. Luckily, M ...more
bObsweep robotic vacuums automatically clean whenever instructed to do so by an owner or because of a pre-programmed schedule. The first step to making a schedule is telling Bob the time and date, so your vacuum can correctly follow your settings. Video: . Set the Date and Ti ...more
Earlier this month, John Oliver spent a segment on Last Week Tonight explaining native advertising, a practice followed by many online media outlets such as BuzzFeed, The New York Times, and VICE, which combines editorial content along with sponsored advertisements. Video: . W ...more
If you have a lot of friends on Facebook, chances are that every day is at least one of their birthdays. If you took the time to individually post a message every time, you'd spend ALL of your time on Facebook, but you don't want to be a bad friend either. Let's face it, some ...more
Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you alre ...more
The older I get, the more my Friday nights involve watching Netflix at home with a bottle of Maker's Mark and a box of Oreos. Netflix is a big part of my life, and I'm not alone. YouTube and Netflix make up over 50% of all activity on the Internet, so it might be worth your ti ...more
There's a tool on your iPhone that can help you with your overall emotional well-being, one that can help you be more aware of your emotions throughout the day and build resilience against the stressors in your life. This State of Mind feature is found in the Health app and i ...more
In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied togethe ...more
Uber resumed its pilot program for driverless cars after one of its autonomous vehicles crashed in Tempe, Arizona last weekend. The program was grounded in Arizona, Pittsburgh, and San Francisco after the incident on Friday, when a Volvo self-driving SUV collided with another ...more
Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, sk ...more
Hello everyone on null byte this is my first tutorial This Tutorial Is on Useful Lesser Known Commands on Linux STAT COMMAND: The stat command displays the status of a file.The information is much more when compared to ls -l. It also includes the absolute path,Number of blo ...more
Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house. Probably, you already know what SSH means, but for ...more
Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what appli ...more
In the Western world, the only time you'd associate food with cockroaches is health code violations. And while other cultures and countries are more open to cooking with and eating these and other little buggers, insects are probably not a food trend that will be adopted by th ...more
Android's personal assistant is more than just a sassy backtalker—it's a full-on suite of all the information you could need at a given time. Google Now, as it's called, uses data from various sources to predict what you'll want to know before you even search for it, and it's ...more
Cable TV providers were dealt a pretty significant blow on Thursday, February 18th, 2016, when the Federal Communications Commission decided that customers should have a choice in what type of device they use to watch cable, instead of being forced to rent a set-top box. This ...more
Sometimes our information important. So important that we have to encode it to keep it away from criminals. What better way to encode information than to make our own encoder with Python? In this tutorial, we will cover the basics of cryptography in hopes to make a "gibberish ...more
Samsung catches a lot of flak for all of the "bloatware" it preinstalls on its Galaxy line of devices. Many users complain that "TouchWiz," Samsung's custom Android skin, causes lag with its overabundance of features. But some of these features can actually be pretty handy, li ...more
This time last year, we got our first taste of what mobile app developers could do in augmented reality with Apple's ARKit. Most people had never heard of Animojis. Google's AR platform was still Tango. Snapchat introduced its World Lens AR experiences. Most mobile AR experien ...more
It's that time of year when high school students say goodbye the their past four years of coddling, ready to enter the "real world" and the next chapter of their lives—college. It's a time of growth, change, and new friends, along with all the timeless memories that go with t ...more
On July 3, Apple pushed out iOS 13 developer beta 3 for iPhone, and there's a lot found hidden within. A new FaceTime setting, more Arcade details, full-page scrolling screenshots everywhere, a noise cancellation option in the Control Center, and a new markup tool — and that's ...more
Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to ...more
On March 13, President Trump announced during a briefing in the Rose Garden that Google was building a COVID-19 screening website to help Americans understand if they might have the new coronavirus. If likely infected, the site would also include the location of a local drive- ...more
While there were a ton of features added in iOS 12, one that Apple had been bragging about since June was nowhere to be seen. Until now. With the iOS 12.1 update, your iPhone gets a huge feature, as well as a few smaller ones to boot. The iOS 12.1 update was released on Oct. ...more
Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of sk ...more
Technology ages rapidly. We're conditioned to refresh our iPhones every one or two years, and why wouldn't we? New iPhones are fast, and our old ones inevitably slow down, sometimes to an unusable degree. However, it turns out, there's something we can do about that, and it do ...more
Andre was enjoying the carefree life of a 12-year-old with his friends, riding his bike and playing sports, like all kids that age. Schoolwork wasn't hard for him, and his grades showed that. Then, the headaches began. He lost vision in one eye, symptoms that drove his famil ...more
Sometimes you need a password to gain access to an older running Windows system. Maybe it's a machine in your basement you forgot about or a locked machine that belonged to a disgruntled employee. Maybe you just want to try out your pentesting skills. When you need to access ...more
Researchers at MIT's Computer Science and Artificial Intelligence Laboratory have created Wi-Fi technology that identifies where you are, which may eliminate the need for passwords. Video: . The system, called Chronos, can determine where a user is with an accuracy of "tens of ...more
After a long time I succeed to reconnect to victim's system without a touch(the victim did not click the app again) note:my big problem is the AVG sometimes the AVG does not discover it but sometimes does..... first of all i hacked his pc with Veil-Evasion by sending him the ...more
Fugu - a simple virus in bash. I once told a friend of mine I'd written a virus in bash and he scoffed - "You can't write a virus in bash!" - he sniggered, like an ignorant idiot. Take my script, read and run it I told him. He declined. I still have that script so thought I ...more