Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the prev ...more
On Thursday morning, May 28th, Google announced an upcoming version of Android—and within a few hours, a preview build of this so-called "Android M" release was made available to select Nexus devices. If you're one who likes to stay on the cutting edge, this build offers lots ...more
For anyone interested in using cheap, Wi-Fi-connected microcontrollers like the ESP8266, the Arduino programming language can be a barrier to entry. Based on C++, Arduino requires knowledge of more computer science than languages like Python. Fortunately for beginners, setting ...more
A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starrin ...more
Nearly ten years since the first Galaxy Note and yet the Galaxy Note 20 still hasn't solved one of its biggest problems: bloatware. There are still over 20 redundant or unnecessary apps that are on this $1,000+ phone. But while it does require some advanced tools, it's still p ...more
ProtonMail has long been the favorite of journalists and security-conscious professionals, with Edward Snowden the most famous example. But these days, everyone cares about anonymity, so it's no surprise that ProtonMail currently has over 2 million users. And now the service i ...more
WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most ...more
Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In ...more
Aircraft equipped with ADS-B are constantly shouting their location into the radio void, along with other useful unauthenticated and unencrypted data. In this guide, we will make an ADS-B receiver using a Raspberry Pi with a software-defined radio (SDR) dongle, which we can us ...more
Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, ...more
SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and e ...more
Thousands of emoji are available on iPhone, iPad, and Mac, and you can use these in many of the apps you have installed on your Apple devices. But there's one emoji you'll likely never see on any of Apple's official emoji keyboards, and its absence may surprise you at first, c ...more
Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scan ...more
If you're getting into automation, Bash scripting is usually the way to go. However, there are a couple of limitations, and one of them is logging into another device like a Raspberry Pi and running a script automatically. To help in those situations, we're going to automate d ...more
A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later. We're going to explore how it works by creating a single line that downloads and runs potentially infinite ...more
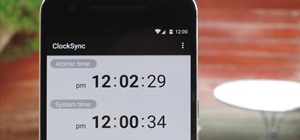
A core concept that has resonated through societies of the world over the course the last few hundred years is "knowledge is power." And understanding that concept gives us the drive to push further forward and learn as much as we can on a subject. At the moment, that subject ...more
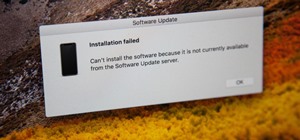
Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does ma ...more
I have an absolutely wonderful time making projects and writing articles for all of you mad scientists! Today, I will bring you behind the scenes for a look at the workbench, tools, and software that make the Mad Science World possible. Above is my beautiful workbench! My who ...more
Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic ana ...more
When it comes to modding an Android device, a custom kernel can take you farther than almost anything else. Most offer the ability to overclock your processor for performance gains, change your CPU governor, or even under-volt to increase battery life, among other features. O ...more
Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start som ...more
Thanks in large part to our phones, many of us don't get the recommended eight hours of sleep. In Android Pie, Google introduced a feature called "Wind Down" that aims to help combat this. However, thanks to a creative app developer, we don't need to wait for Android 9.0 to en ...more
Welcome back my precious hackerians. Today i would like to promote an OS which i have been using for the past couple months. I'm not talking about Backtrack 5 or Kali Linux. Something even more promising: Bugtraq 2 Black Widow I'm not going to show you how to install it beca ...more
A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, m ...more
Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. ...more
Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed ove ...more
We go to such great lengths to secure our smartphones. We put passwords on our lock screens, encrypt our data, and install anti-theft programs, but it's never enough—someone, somewhere, will find a way around any protective measure you use, no matter how sophisticated. Unfort ...more
Without an available browser, it is challenging to enjoy media on your Nvidia Shield outside of the apps on the Play Store. It is because of this limitation that file transferring is vital, as only then can you enjoy your movies and music. Initially, we set out to showcase al ...more
I've previously mentioned how saving browser passwords is a bad idea, but I never went into much detail as to why. Passwords that are saved in your browser can be carved out and stolen very easily. In fact, even passwords you save for instant messaging and Wi-Fi are vulnerable ...more
Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there ...more
It's here... Update: May 1, 2014 We got word of an imminent update yesterday, and it's here today! Our 2012 flagships should be seeing over the air updates starting today, and the Android 4.4 build has been officially confirmed by Sprint. While a staged rollout will eventual ...more
Native screen recording was initially introduced on Android 4.4 KitKat and, although useful, was primarily utilized by developers to showcase their apps. It required either a rooted device and an app or a non-rooted device with some ADB commands, which, while totally doable, w ...more
This is a collection of various guides and tools available on the internet. Instead of searching for 1 you can easily find whaht your looking for here. LAST UPDATED : Monday, 08/06/2015 Hello, This is my first post so please bear with me if anyone else had already posted so ...more
Another week has passed on the online battlefield as the CISPA legislation continues to grind away at our freedom. Here at Null Byte, we try to keep our community informed and knowledgeable at the same time—and that means creating content for them to learn from. After last we ...more
Deep down, Android is a fork of Linux, which is a desktop operating system that started out as entirely command prompt-based. For that reason, many system-level tasks can still be executed within a terminal emulator app. But visually speaking, the terminal apps that have been ...more
With over 60 commercials, chances are you've seen one of the Get a Mac spots run by Apple, which brands Mac as intuitive and hip, compared to their boring and clunky PC counterpart. You also probably saw Microsoft's response in their I'm a PC campaign. But who are Mac and PC u ...more
Android 7.0 Nougat has finally arrived—well, technically, it's in the process of arriving on Nexus devices across the globe. Google uses a staged rollout system to prevent excessive server load when issuing Android updates, which means even though Nougat has made its official ...more
For those who doesn't want their root password on Kali Linux live USB persistent login to be reset to the default 'toor', Step 1: Easy Once you have changed your password using passwd root command, edit /lib/live/config/0031-root-password and comment out the line before: us ...more
Tab previews—you can do it on an iPhone or an Android device, so why not on your Mac or PC? It's about time you take your browsing game to the next level and learn how to toggle between previews of your tabbed webpages. This guide will run you through enabling secret settings ...more
Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact. For example, Android encryption still lags b ...more
In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately ...more
This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to ...more
While installing the new Android 9.0 Developer Preview is fairly easy if you're using a Windows machine, it's a little trickier if you want to use macOS instead. To help you get the latest Android OS on your Google Pixel phone, we'll break down the whole process so using your ...more
Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn ...more
Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Dis ...more
If you're like me, you spend a lot of time on your computer, which can be damaging to your eyes in the long run. Studies have shown that staring at a computer screen or television up close for extended periods of time can have harmful effects on your vision. An application ca ...more
With so many cloud storage services out there, many people are starting to keep their important documents online, especially when they know they'll need to view them when they're away from their computer. That's all well and good, but I'm still human, and I forget things. Som ...more
Back in 1982, the Commodore 64 home computer was released by Commodore International for $595 (which would now be close to $1,300). It featured an 8-bit microprocessor, 16-color video microchip, awesome sound chip, parallel and serial capabilities, and a whopping 64 kilobytes ...more
TCP/IP Client / Server Application Hello! Today's blog post will be about coding a very rudimentary Client and Server application duo, which will communicate by using TCP Sockets. It is, as illustrated, in principle, just two cans and a string that ties them together. The se ...more
The Galaxy S8's AMOLED display is prone to screen burn-in, particularly with the navigation and status bars. But hiding these bars would make it hard to navigate your phone — that's where Pie Controls come into play. By enabling full-time Immersive Mode, you can hide the on-s ...more
Ever since kernel 2.6.xx in Linux, a lot of the internet kernel modules for wireless interfaces ended up becoming broken when trying to use monitor mode. What happens commonly (to myself included) is a forced channel that your card sits on. No good! For users of airodump and t ...more
Need a way to convert your scanned documents back into text files? Check out this video tutorial on how to convert scanned documents (JPG, PDF) to text. Free-OCR.com is a free online OCR (Optical Character Recognition) tool. You can use this to perform OCR on any image you su ...more
The already robust and ingenious Nmap tool has received a whole slew of new scanning scripts that can be used to do all sorts of naughty endeavors. Notably, the SQLi module, since it is a necessary evil that we must cover here at Null Byte. This major update is going to fuel t ...more
A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fort ...more
Hi, I am Robel, I am here to let you know about how to hack windows admin password with out Sam files, this requires physical access and any boot operating system...I used Kali 1.8 , if it doesn't work make sure you have shuted it down properlyor use backtrack. I have tested ...more
Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock: Level 7 this level says: This time Network Security sam has saved the unencrypted level7 password in an obscurely named file saved in this very di ...more
Think back to when you last wanted to transfer some music or videos to your friend's smartphone and how difficult and slow it was. As powerful as our phones are, the default file sharing options are limited. There are, fortunately, some better options which make moving files e ...more
Brutus, first made available in 1998, is one of the fastest, most flexible remote brute-force password crackers you can get your hands on - it's also free. It is available for Windows 9x, NT and 2000. In this video tutorial, you'll learn how to use Brutus to crack a Linux box ...more
Over the years, I have enjoyed playing with Asterisk. I have found Asterisk to be extremely powerful and fun to play with. There are several books and many scattered how to articles out there, but most are outdated and the information required to build Asterisk from beginning ...more
Two computers, two displays...one keyboard and mouse. Molly Wood from CNET shows you how a free software app (Synergy) can make beautiful music between PCs, Macs, and even Linux.