I was getting kind of sick of ordering delivery pizza (this happens at least 2-3 times a month). It was time to put a spin on gourmet pizza, but I just didn't know what it would be. Without pizza dough or an oven that is capable of creating the perfect pizza crust (I don't hav ...more
Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat. Most Linux distributions are highly c ...more
If your PC setup includes a mouse and keyboard, you'll be happy to know that most of the touchscreen-first features of Windows 8 have gone by the wayside in Windows 10. Where it once required awkward gestures to access key features, Windows now recognizes when you're using a t ...more
If you need to do some hardcore multitasking on your Windows PC, a second monitor can go a long way towards getting things done. If you opt to "extend" your Windows desktop across a dual monitor setup, it's as if you have two computers side by side, with each display getting i ...more
OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers, Welcome to my 5th Post, In this tutorial I am going to show you how to make the backdoor we created in my guide here a persistent one. I finally found out a way to do this, as I was/am very ...more
Mouth burning with pain from eating too much hot sauce or some seriously "spicy" food? Well, ignore your first instinct and steer clear of that cup of cold water — it won't help. Instead, reach for a glass of milk, a lemon slice, a spoonful of sugar, or some starchy bread to d ...more
Before many games make it to the US-based iOS App Store, they get "soft launched" in a smaller country to get real-world testing for bugs. It's a pilot program, so to speak, as countries like Vietnam or the Philippines have far fewer iPhone users than the US, thus offer a more ...more
If you've ever owned an HTC device or anything in the Nexus line, odds are, you have typed the word "fastboot" into your command line at one time or another. That said, odds are, you have only just barely scratched the surface of what this handy little Android tool can do. Let ...more
UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/ Hi guys, I'm here again with my second tutorial, as I promised. Metas ...more
Forum member Luciano posted a terrific guide on adding hacks to our phone by editing build.prop. The article was great, but one of best things I saw in it was the "What You'll Need" section: A current nandroid/backup of your device. Having current and complete backups of you ...more
The new Jelly Bean is out in the wild, but if you've installed Android 4.3 from stock, you'll notice rooting is now not possible. If you miss the ad-blocking capabilities of AdBlock Plus, how Seeder made apps snappier, or the convenience of backing up with Titanium Backup, you ...more
A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc. Obviously, not all places use the same methods, and not all of the m ...more
When you take a screenshot on your iPhone, it's automatically saved to your Photos app. You can ignore the screenshot thumbnail or swipe it away, but you shouldn't. If you open the screenshot editor instead, you'll gain access to your iPhone's most useful screen capture tool: ...more
Welcome back, my neophyte hackers! As part of my series on Wi-Fi hacking, I want to next look at denial-of-service (DoS) attacks, and DoSing a wireless access point (AP). There are a variety of ways to do this, but in this tutorial we'll be sending repeated deauthentication f ...more
Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks. For those of you who are new here, a denial of service is basica ...more
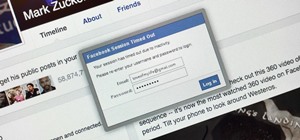
Since the release of Windows 8, Microsoft has been heavily encouraging users to use Windows with a Microsoft account. According to Microsoft, the main benefit of using a Microsoft account is the ability to sign in and sync your information across various Microsoft devices and ...more
If I were to lose access to the entire internet for the rest of my life, one of the websites I would miss the most would have to be Wikipedia. Wikipedia has ended countless arguments, informed me of how old and single some of my favorite actresses are, and helped me brush up o ...more
Hello! This is my first post on this awesome website! I know that Windows exploits are less common than the more advanced hacks, but I found something I deem pretty cool and figured why not share it with you all. Alright, enough about me, lets begin. Warning: This resets your ...more
If hearing the names of classic PC games like Commander Keen, Fallout, Master of Orion, and Wolfenstein 3D send you into a fit of nostalgia, then DosBox Turbo is the perfect app for your Android device. DosBox Turbo is a highly optimized and feature-enhanced Android port of D ...more
While still extremely awesome, the Samsung Galaxy Gear smartwatch is limited as to what you can download on to it, especially apps. It also doesn't have its own internet access (only Bluetooth), so apps like Instagram, Facebook, and Vine have yet to make their way to the Gear ...more
When you're sitting at your desk trying to get some work done, your Android device can be a big distraction. If a text comes in, you have to pick up your phone, unlock it, then respond with the clumsy touch screen keyboard—and by then, you've probably forgotten what you were d ...more
Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ...more
Dancing! Apparently, it can be done anywhere! That's the impression one gets when looking at Jordan Matter's captivating photo series, Dancers Among Us, anyway. Who knew! What's the oddest place you've danced? Weigh in below!
Apple's already gone through iOS 13.0, 13.1, 13.2, 13.3, 13.4, and 13.5 betas, and now it's time for iOS 13.6. If you want to try out new features on your iPhone before the masses, install either the developer or public beta. The iOS 13.6 beta first appeared as an iOS 13.5.5 ...more
There are loads of reasons for somebody to want to recover a Windows password, and there are lots of different ways of doing it. My favorite of all of these ways is to use a piece of software called Ophcrack because: The free tables are suitable for almost all uses (I've neve ...more
NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of ...more
Anyone who has rooted their Android device has likely used a tool called Android Debug Bridge, better known as ADB, at some point during the process. For most, that is their only interaction with the ADB, but to be a true Android power user, you need to really know the tools a ...more
I was in college, and my 15-inch Sony Vaio laptop was my prized possession. It was my first PC and probably the most important thing I brought with me to my dorm — it was both how I completed my assignments and my primary source of entertainment. How could it turn its back on ...more
If you're a self-described multitasker, Samsung has a feature that's perfect for you called Multi-Window, which lets you display two apps on your Galaxy S4's screen simultaneously. You can browse the day's news while doing a sudoku, take notes while watching a YouTube video, ...more
When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a littl ...more
Your freezer is no one-trick pony. While it does excel at keeping your food fresh for as long as possible, it has a few secret talents it doesn't want you to know about. Like making soda slushies and pyro-friendly smoke mix, as well as reviving dead hard drives. Even better—it ...more
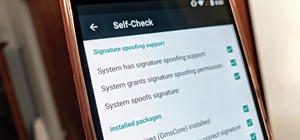
It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for ...more
Whisking liquids seems somehow quaint, especially since there are good, cheap devices out there like immersion blenders and hand mixers that can whip cream, turn egg whites into meringue, and mix batters for you. However, I still love my whisk and use it often, and here's why ...more
Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester. On the other hand, there are many here who come to Nu ...more
Android Marshmallow introduced a pair of new battery-saving features called Doze and App Standby, and according to the general consensus, both features are a rousing success. Average battery life has increased dramatically for virtually every phone or tablet running Android 6. ...more
Want to adjust the Windows Firewall to permit µTorrent? This clip will show you how it's done. It's easy! So easy, that this video tutorial can present a complete, step-by-step overview of the process in about two minutes. For more information, including detailed, step-by-step ...more
No one likes it when random people wander into your home and mess things up, which is why it behooves you to hide your things from even the most prying eyes with builds like this totally invisible, 2x2, piston-operated door with no visible redstone either inside or outside. Th ...more
Battery management is a never-ending struggle. To be on the safe side, you likely won't want to leave your home with less than 100% battery, but continually checking your charging iPhone is a hassle. Instead of continuously monitoring your battery's power level, have your iPho ...more
Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a smal ...more
Have you ever forgotten your password and didn't know how to get back on your computer? Or ever had an annoying roommate you wanted to play a trick on to teach them a lesson? Or perhaps overly religious parents who think the internet is of the devil and won't let you read onli ...more
Apple's latest mobile operating system for iPhones, iOS 12, was released to everyone Monday, Sept. 17, and it's the same exact build that developers and public beta testers received as the "golden master" on Sept. 12, the day of Apple's 2018 special event. Install it to start ...more
The act of liking someone's really old Instagram post is called "deep-liking," which is pretty apt if you think about it. While going "deep" into older posts on the feed of your ex or crush or whoever, your finger may slip accidentally and double-tap on a photo or video that y ...more
Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. ...more
Apple officially unveiled iOS 14 on June 22 at its first all-virtual WWDC. After months of beta testing, iOS 14 hit iPhones on Sept. 16, but that doesn't mean that Apple is done beta testing iOS 14. There will be new features to try out right up until iOS 15 comes out next yea ...more
There are a few ways to make trapdoors, but out of all of them, this one is my favorite. It's fast, completely hidden, and both opens and closes. This particular trapdoor can be used for a variety of purposes, such as hiding your valuable possessions, having a secret entrance ...more
The Pixel 2 has finally arrived. Google unveiled their newest flagship phones on October 4th, and there's quite a few changes in store. For one thing, most of Google's official renders have already showed us something new: The Pixel 2 and Pixel 2 XL will have a Google Search b ...more
While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show y ...more
All day I dream of eggs: scrambled, poached, over easy, hard-boiled, fried, baked, raw... Okay, the last one is a joke (unless you're Gaston, which means that you eat five dozen of them and you're roughly the size of a barge). But eggs are freaking good in just about any cooki ...more
This video will show you how-to hack Bluetooth on your iPhone with an app called BlueSn0W. You'll need a jailbroken Apple device to begin with, so make sure that step is done first. After that you'll be able to hop on someone else's signal.
For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in Vir ...more
For people that like to get things done, Android's home screen widgets are almost indispensable. Rather than packing your launcher with a bunch of icons, you can utilize widgets to get quick information in a beautiful package or provide one-tap access to a particular functiona ...more
Scanning important paperwork on smartphones is a tedious process, often relying on either external scanners or third-party apps that had to be either purchased or were loaded with annoying ads just to get the job done. Thankfully, iOS 11 now lets you easily scan documents usin ...more
With the amount of time we spend glued to our smartphones, they could be considered a second job (if only we got paid). I spend a large part of my day scrolling through Reddit, Facebook, Instagram, and countless other apps, and burn through hours and hours without even noticin ...more
Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access ...more
It may sound irrational, but I bet a lot of you actually avoid doing any work at work—but not on purpose. You might be simply struggling with motivation, or you might just be overdosing on the caffeine. Whatever the issue, getting focused takes lots of time and effort. But we ...more
The Jitterbug is a popular swing dance, also known as the Lindy Hop and East Coast swing. This how to video demonstrates a series of 6-count Jitterbug steps. These steps are quick and easy to learn. Watch this dance tutorial and you will be doing the Jitterbug in no time.
In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003. Although these operating systems were first released, in some cases, almost 10 years ago, the ...more
Apple's goal with iOS 12 is to smooth out the problems with its famously flawed predecessor. Of course, change isn't for everyone, and by iOS 11.4.1, Apple had a pretty stable thing going. If you're not digging all the bugs and new features included in iOS 12, here's how to do ...more
By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet mani ...more
Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the ...more