You probably use your smartphone to mostly surf the web, play games, and communicate with others, but there's so much more it can do. Thanks to integrated features and third-party apps, you can seamlessly control things around your home, including your TV, tablet, Bluetooth sp ...more
One of the coolest features that Samsung built into the Galaxy S4 is the infrared (IR) blaster and WatchON software to control your television. I've been using my GS4 for the past few weeks to control my DirecTV setup and it works great. Smartphones are truly becoming all-in-o ...more
Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it. Even if you aren't a Windows user, it's good to know how command prompt works b ...more
Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, sk ...more
Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering. One such distribution is Pentoo, a Gentoo-b ...more
AppleScript is quite an easy scripting language to use. In this guide, I will be showing you several commands. Near the end, I will show how these can be used to create a fake virus that actually does no harm. Of course, this is only one way to use these commands—use your ima ...more
Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensi ...more
Sometimes windows will shutdown for "updates", which is great and all except when you had an unsaved project in the works or a huge file conversion that you expected to be completed when you wake up, only to find your computer rebooted. Check out the links below for instructi ...more
Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified. This attack assumes the Wi-Fi password to the ...more
Web browser extensions are one of the simplest ways to get starting using open-source intelligence tools because they're cross-platform. So anyone using Chrome on Linux, macOS, and Windows can use them all the same. The same goes for Firefox. One desktop browser add-on, in par ...more
As a hacker or an aspiring one, You need to be careful and anonymous if your doing anything illegal. But you slipped up. Now someone is tracking you! Well luckily you read this post ahead of time and have a backup plan! The first step in remaining safe is to remain anonymous. ...more
Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques i ...more
I'm not admitting to anything, but let's be honest, most of us download content on the Web from time to time. With copyright holders laying down the law more and more often, it can't hurt to do so with caution. And even if you aren't downloading copyrighted material, you still ...more
I still remember when I had to get up from my comfy spot on the couch to change the channel on my old television. So for me, the remote control may be one of the most underrated inventions of the last century. These days, remotes take on all sorts of shapes, not just the typic ...more
If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Obje ...more
Welcome back Hackers\Newbies! Hey guys first of all I would like to explain my absence here in NullByte. I got a little "occupied" with "other things". When I got back, I saw all these HowTo's, articles, Help Questions, I decided, I need to share more of what I have, to you g ...more
Hello Hackers/Viewers, It is a new day, and you might be thinking, It is so boring, why not try to be cool with computers in front of my friends? That is why, I have made this tutorial to make fake viruses using notepad to look cool! Step 1: Requirements for the Prank First ...more
Hi, often we do something wrong or accidentally delete software, drivers or files from our system. Then we want them back. But how? System restore is the way out. We are showing you how to do that in windows 7. Step 1: Go to Start Take your mouse pointer in START and click. ...more
Over the last few months I have been getting more and more into computers over the last few months, and I discovered my new favorite thing to do..... notepad stuff! I will teach you how to do a few basic things in notepad, notepad++, and how to use them to your advantage! Fi ...more
If you use Ubisoft's uPlay browser extension, you should probably get rid of it right now. An Information Security Engineer at Google discovered that the plugin has a hole in it that allows programs to be installed through uPlay, essentially letting anyone who feels so incline ...more
In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately ...more
If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed. Spooky Action at a Distance If you need to prove you've got remote ...more
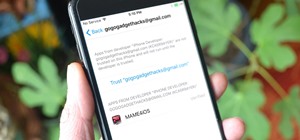
There have been hundreds of reports of Google Calendar users receiving notifications for events they didn't create. These "events" are actually spam ads and potential phishing threats. If this has happened to you, you're not alone — but luckily, there's a way to put an end to ...more
You've probably heard a lot about computer viruses — but how do you stop them? This home-computing how-to from the folks at CNET TV will teach you what you'll need to know. For detailed information, and to get started protecting your own Windows PC from malicious code, watch t ...more
Looking for a primer on how to protect your Mac OS X desktop computer or laptop from malicious software? This clip for Apple amateurs will show you precisely what to do. You'll find it's easy. So easy, in fact, that this home-computing how-to can present a complete overview of ...more
INTRODUCTION The everyday PC user doesn't think much about its PC and problems that can cause critical damage to their data or other stuffs stored on Hard drive and other electronic parts until the problem actually occurs. Once a failure happens, the repairs can be costly and ...more
Did you know Kali 1.0.8? You probably did, and you probably know about the EFI boot option that has been added. That's a very interesting new feature because it allows Kali to be easily booted on Mac too, and every EFI-supported device. First three preview lines gone? As alw ...more
If you're concerned that your computer has been infected by spyware and other malicious programs, watch this informational video and find out how to clean and restore your computer back to a normal bill of health. This informative tutorial shows various methods that can be use ...more
I explain how to view and control your computer from your iPhone/iPod Touch. This works over Edge and Wifi connection, but obviously the better your connection the faster it will go. If you are having problems connecting try going to control panel then security center then tur ...more
Antivirus programs usually aim to prevent malicious software from crashing your system, not ARE malicious software that crashes your system. Except, that was the case with AVG Anti-Virus yesterday when they released a software update that rendered 64-Bit Windows 7 systems usel ...more
If you've ever seen something called ThinkPoint Antivirus on your computer, you have gotten one ofhte most widespread and infectious fake antivirus malware programs out there. To get it off your PC, follow the instructions below, or watch this video for an alternate method if ...more
Paste this code: shutdown -s -t 10 -c "Your Message Here" One of our viewers brought up that -s would simply shut down your PC, and not keep restarting it. To do so, substitute -s for -r and you should be set! Youtuber ricsto also commented that holding shift after the start ...more
How to use uTorrent First of all we need to understand what uTorrent is. uTorrent is a file or a Micro-Torrent that helps you, the user, download stuff like documents, pictures, videos, or e-books. uTorrent is very, very, useful when you know how to do it. so hope fully this ...more
The executable file association virus deletes the "Regkey" that associates ".exe" files with the proper Windows execution. The virus can be contracted while browsing the web, from an infected file, or even from pictures and documents. Once the damage is done, Windows will show ...more
This video tutorial from ballader1 shows how to remove viruses, trojans, adware, spyware from your computer. To do that you need to download Malwarebytes application from malwarebytes.org. Open your internet browser and enter malwarebytes.org URL address. Make sure you down ...more
A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc. Obviously, not all places use the same methods, and not all of the m ...more
In this video we learn how find out IP addresses of websites and shut down the computers with those IP addresses. To do this click "start", then "run" then type command prompt. In the command prompt type "tracert website" (example tracrt Google.com) then hit enter. Various IP ...more
Suspect something's amiss with your desktop computer? Has your Microsoft Windows PC felt slow and sluggish as late? Don't take any chances: check your computer for spyware, trojan viruses and other forms of malware. This free video tech tutorial will walk you through the process.
In a boring lull after getting home from summer school and need some random play to perk your day up? Watch this video to learn how to quickly shut down someone else's computer from your own. The method doesn't require ip addresses and won't spawn noxious viruses so you won't ...more
If your computer is working slow--or not at all, there could be some unsavory programs running amok in your system. Trojans, malware, viruses, and hacks are dangerous to the health of your operating system. This video tutorial demonstrates the measures to take in order to rid ...more
In this tutorial, we learn how to protect a Windows PC from spyware & malicious software with Dave. You can get spyware from downloading random things, so a great way to make sure you don't download these things, is to use Firefox and search your items before you download them ...more
In this video tutorial, viewers learn how to reformat an Acer computer hard drive. Begin by clicking on the "Empowering Technology" logo on the top of the screen and select Recovery Management. Then click on the Restore button and click on Restore system to factory default. En ...more
There are 10 major ways to protect your PC. Disable Autorun, in Windows. Make sure that your system is up to date, by setting automatic updates. Always use a log on for your computer that does not have administrative privileges. Use different passwords, and change your passwor ...more
A quick tutorial on how to effectively removed corrupted files from your USB pen drive Insert USB drive into computer. Click on "My computer". Right click on your USB drive (e.g., Removable Disk Drive E: )Go to "Properties" and select "Tools". Under "Error Checking" select "Ch ...more
Is your PC too slow? Want your PC performance to increase without paying any money? Well, in this video the viewers will be taught how to speed up their PC and internet speed without spending a dime. First of all, the video goes through some of the potential applications that ...more
This is a tutorial that shows you how to view and control your computer screen from your iPhone/iPod Touch. But this method is for people who have a jailbroken iPhone/iPod Touch. This works on Edge and Wifi. If you are having problems connecting try going to control panel then ...more
This video demonstrates how to set your Mac up to accept VNC connections.First we open up the "system preferences". Double click on Sharing and then go down to remote management and check this. We can see some options . Check the options Open and quit the application, Change s ...more
Watch out Macs. Flashback is back. Variations of the trojan have reportedly infected 600,000 Mac computers around the globe, with about 57 percent in the U.S. and another 20 percent in Canada. Dr. Web, who discovered the spreading Flashback, said that these trojans install t ...more
With the computer's rapid increases in power and efficiency, computer virtualization has taken the scene by storm. With virtualization software, and powerful enough computer hardware, your computer can run a virtual computer within itself. This effectively gives you multiple O ...more
Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic functio ...more
Sometimes it's necessary to format your memory card in your mobile phone or digital camera, just like you need to format a hard drive, because of virus problems or slower speeds. This video will show you the steps to formatting (or reformatting) the SD memory card for a cell p ...more
First of all you have to go to Photobucket. In the search option you have to type in '3d gif''. Now click 'search'. You shall get a number of photos and you can select the image that has red color moving screen. It is better to get image this way without a virus. Now you have ...more
There are times when you must start up your Windows XP computer system in Safe Mode, for example if you need to remove certain viruses, key loggers, adware, etc. that cannot be removed while in standard mode. If you want to learn how to boot in safe mode in Windows XP, you sho ...more
In this Know Your PC video the instructors show how to perform a recovery on your computer by demonstrating it on the HP TouchSmart PC. This recovery process will work on any HP desktops, HP Pavilions, Compaq Presarios. Your PC might get corrupted if you recently made any chan ...more
Looking for a guide on how to protect a Microsoft Windows desktop computer or laptop from viruses, spamware and other malicious software? This clip provides a very good starting point. For complete details, and to et started protecting your own Windows PC from viruses, watch t ...more
Computers are vulnerable to all kinds of viruses, hacks and other attacks that can do serious damage and cost you money. Make sure your version of Windows is the real deal and protect it from counterfeiters by making it genuine. This video will show you how to make Windows XP ...more
Don't just click X when closing pop-ups! You might be installing malware. This internet tutorial video will show you how to close pop-ups safely without installing spyware, malware, or viruses on your computer.
Prank your friends' computers by making a fake trojan virus that shuts their system down. Make a prank trojan virus in 3 minutes. Click through to watch this video on tricklife.com
This video helps you to protect your computer against viruses and spyware often contracted when using peer to peer (p2p) networks like limewire, kazaa and emule.
Private browsing is all the rage with browsers these days. Once you go into private browsing mode, you can traverse the internet without leaving a trail. Your history? Deleted. Your cookies? Destroyed. Your bookmarks and non-private history? Preserved for when you come back to ...more