Long before Nvidia figured out how to embed neural networks in its graphics processor units (GPUs) for driverless vehicles, it and other chipmakers were already making the same kinds of devices for 3D games and other apps. GPU makers, including AMD, and to a lesser extent, In ...more
My Cuisinart ice cream maker was a wedding gift; it wasn't something on my list, but I jumped up and down with delight when I unwrapped it. I never would've purchased this appliance on my own because it didn't seem practical, yet I loved the idea of making homemade ice cream. ...more
With Gboard, Google created a keyboard with more functionality than just inputting words. The app includes features such as GIF search and live text translation, but it gets even better when you let it learn more about you. With this data, Gboard grows from a good keyboard to ...more
This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW. Hello script kiddies, Just running a script doesn't give you the understanding of what's going on under the hood. ...more
One of the only things I remember from watching Nickelodeon as a kid is the epic green slime. Looking back, I don't know what was so great about it, but every kid my age thought that being drenched in slime would be the coolest thing on earth. Of course, the first thing I did ...more
The transcribing app can be an invaluable tool, especially if you're a student or are in a profession that relies on audio journals or interviews. These apps can convert important recordings like lectures and meetings into text for you to carefully read through to better compr ...more
While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are al ...more
Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exi ...more
Marinades are among my all-time favorite tricks as a cook for several reasons. They're easy like Sunday morning, they let time do what it's supposed to, which is work for you, and you get a huge return for relatively little effort on your part. In a pinch, I've used store-bou ...more
There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distributi ...more
A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) to ...more
Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elli ...more
|Choose Your View: Quick Bullet Points | Detailed Descriptions Android's newest major update is a special one — it's the tenth full version of the world's most commonly used operating system. The latest release, dubbed simply Android 10 (codename Android Q), was first showcas ...more
It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to ...more
Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary fl ...more
Within the coming months, software startup Neurable plans to introduce the next paradigm in virtual and augmented reality: the brain–computer interface (BCI). A BCI interprets brain signals so that devices can understand user intention from predefined selections. Relying on s ...more
Sometimes you need a password to gain access to an older running Windows system. Maybe it's a machine in your basement you forgot about or a locked machine that belonged to a disgruntled employee. Maybe you just want to try out your pentesting skills. When you need to access ...more
When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a so ...more
A boring work meeting. A conversation with someone you don't like. A date that's going horribly. A run-in with an aggressive and intimidating stranger. These are all situations where you want to flee—and fast. The most common way to make your exit look more legit is with a ph ...more
3D printers allow hackers and makers alike to create something from nothing. They're an incredible technology that lets you build protective cases and covers for gear such as a wardriving phone and Raspberry Pi-Hole. 3D printers can even help you out in a bind when something b ...more
Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the ...more
Super Mario Run was released for iOS on December 15, 2016. Even though it debuted as a "free" app, almost all of the playable content was hidden behind a ridiculous $10 unlocking package. Despite coming with such a hefty price tag and receiving a two-star rating on the day of ...more
Hyundai Motor Company says it will launch its driverless tech ahead of schedule, but the Korean carmaker will remain behind mainstream rivals, including General Motors (GM), Nissan, and Honda. Speaking to the Korean IT news outlet the Electronic Times, Hyundai said it was lau ...more
Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, ...more
Finding the formula to the perfect cup of coffee for your taste can take a while. I finally got around to buying a French press a few weeks ago and I'm still tweaking the right ratio and brewing time to get it just right (though I am drinking it at the right times each day). ...more
lubuntu is a is a lightweight Linux/Ubuntu that makes it suitable to virtual environments, that you run with VirtualBox to add a secondary machine to your computer or laptop. With this program you can run a number of operating systems upon the same platform. But as we are all ...more
Who doesn't love a good prank? Taking advantage of unwilling and gullible bystanders is an obvious recipe for success—and some hilarious amusement. One of the best pranks I've seen in a long time was the Invisible Driver, which I featured last month. Created by magician and p ...more
Like with any shooting game, the gun can make all the difference in Zombies mode in Call of Duty: Black Ops 2. When fighting off a ton of zombies, walking around with a pistol or a shotgun that only holds two rounds can cause some serious issues. Since there are only a few wea ...more
With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassin ...more
Word games can expand your vocabulary skills in all sorts of exciting and creative ways. Because of this, both the iOS App Store and the Google Play Store are awash with word games, making it hard to differentiate between good and bad titles. This is especially troublesome if ...more
Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensiv ...more
Every time Donald Trump tweets about a stock you own, Trigger Finance, or just Trigger—the app founded on the "if this, then that" rule to track and invest in the stock market—alerts you with a notification for real-time analysis of financial data. Rachel Mayer, the CEO and c ...more
In this video I'm going to teach you 5 pranks you can get away with at school or at home On April 1st. Video: . Step 1: Dry Board Eraser Prank Lets start with one you can do on you teacher. Get to class early before your teacher and mess with their dry board eraser, heres how ...more
It's easy to grab a box of pre-prepared microwave popcorn at the grocery store. Yet with so much salt, butter, and other unpronounceable ingredients, microwave popcorn can go from a healthy snack to a complicated one. Even if you resolve to pop your own popcorn with the minds ...more
As a hacker or an aspiring one, You need to be careful and anonymous if your doing anything illegal. But you slipped up. Now someone is tracking you! Well luckily you read this post ahead of time and have a backup plan! The first step in remaining safe is to remain anonymous. ...more
We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm her ...more
Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, ...more
While our smartphones are many things, one of their primary functions is to make calls. Many of us try to avoid ever having to make calls, but there are situations when it's a must, such as wishing your grandma happy Birthday or calling 911 — and in those times you want stella ...more
Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a si ...more
This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/ In this post we will explore more about finding hacked accounts online, w ...more
As the demand for realistic volumetric video for AR experiences begins to grow (along with the available facilities and services for capturing it), researchers at Google have figured out how to improve upon the format. The team has devised a system, called "The Relightables," ...more
The iPhone X introduced the world to Face ID in 2017, and now, every new iPhone uses Apple's biometric security system instead of the old Touch ID. It's more secure than fingerprint scanners and it's even more user-friendly. True, it's not without its faults, but at least one ...more
Pokémon GO has become a cultural phenomenon. Finally, we can do what we always dreamed of back when we were kids—catch Pokémon in real life! But let's not forget that we're in adulthood now, and in adulthood, we can catch Pokémon by day and celebrate our successes at night. I ...more
Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post. Let me introduce myself first ! I am from Greece, I am working as a network engineer and I am into system and network administration but definitely ...more
NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!! Computer forensics ( Sometimes known as computer forensic science ) is a branch of digital forensic science pertaining to legal evidence found in computers ...more
What's the point of having a 1080p screen if you're not using it to get in some quality gaming time? Google Play is great for downloading games, but you probably already have an extensive library of games for your consoles, so use those! Emulators are a dime a dozen, but Retr ...more
You see it in the movies all the time. A character on the phone doesn't like what the other person is saying or telling them to do, or they just don't want to talk to them anymore, so they fake bad reception and cut the call off. In real life, it's pretty easy to tell when som ...more
Samsung's big reveal of the Galaxy S9 and S9+ at Mobile World Congress revolved around its "reimagined" camera and augmented reality capabilities. Between AR Emojis, Bixby, and ARCore, the Galaxy S9 and S9+ offer more native AR software features than any other device. AR is s ...more
The next-generation Audi A8 to launch in July is expected to be the world's first Level 3-capable production car to go on sale in retail channels. But aside from demo drives scheduled for journalists and analysts Audi plans to organize this month, the model's advanced driving ...more
The Snapdragon 820 and 821 were met with praise last year, receiving almost no complaints compared to their overheating predecessor, the Snapdragon 810. But now, all eyes are on Qualcomm to see what goodies they have in store for us this year, as their new SoC, the Snapdragon ...more
If you're here, you're probably one of the seven people dedicated to making Mac n' Cheetos a permanent part of the Burger King menu. For the rest of you that stumbled onto this page out of sheer curiosity, Burger King's Mac n' Cheetos were deep-fried, creamy macaroni and chee ...more
April Fools may be over, but any day is a good day to prank someone, and the best time to do it is when everyone's eyes are glued to the television. Turning off a TV during a climatic moment is the best way to prank a TV-obsessed sibling or friend, but it's even more hilariou ...more
Many of you are ready to capture the litany of 4th of July fireworks that will litter the night sky, but if you're using a phone to capture the burst of fire in midair, it can get a little tricky. Don't worry, though — you'll be fine if you use these tips. While pro and semi- ...more
If running out of battery while out and about weren't bad enough, the experience is a lot more painful if your iPhone has a semi-untethered jailbreak. With that kind of jailbreak, when the iPhone dies, all of the mods will be disabled after the device powers back up. Fortunate ...more
When rumors first emerged of Sony's Xperia XZ3, many of us wondered why. With the Xperia XZ2 just releasing in April of this year, why is Sony already releasing its successor? But now that it is officially announced, it makes a bit more sense, as what Sony is calling the XZ3 i ...more
The war on dehydration is a commercially burgeoning marketplace. An increasingly sophisticated consumer population hoping to conquer everything from 26-mile marathons to vodka shots is deconstructing every functional remedy in the fight to quell the effects of severe dehydrati ...more
User interfaces for computers have evolved over the years, from the introduction of the keyboard and mouse on the personal computer, to touchscreens on mobile devices, to natural voice recognition. However, the same cannot be said for robots or drones—until now. There are two ...more
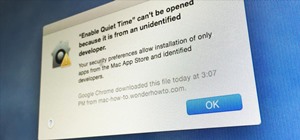
Now that we've learned about keeping all our data safe with encryption, it's time to continue progressing through getting your Mac set up for hacking. Just like most other people, we hackers have a lot of credentials to manage. We're also human, so we have a hard time creatin ...more
Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard. So in the last tutorial we did what we did without the use of our default gateway. To be honest, in really ...more
The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from eve ...more