In a previous article, I demonstrated an Arc Welder made using parts from old microwave ovens. Video: . Here is part 1 of 2 on how that arc welding machine was made, and how you could make one too! This is the first of two parts on building it, focusing on the modification of ...more
Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn fro ...more
The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to ...more
After more than a year and a half of silence, the rumors have morphed into reality: Microsoft has finally released an update for the HoloLens. And with that update comes a collection of new features that hint at big plans for the HoloLens this year. For most HoloLens-focused ...more
Hello again, ***UPDATE: Adding links to the other Two articles**** I recently started working on creating evil twin ap's, after reading OTW's article. I wanted to find a way to automate this process as much as I could, so I started looking for sample bash scripts and found t ...more
Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! T ...more
Why I split it into two articles: I love images and I'm sure lots of us do. I decided to put in a lot of images as examples rather than have paragraph upon paragraph of boring text. Also, I don't think any of us like overly long articles; but if you think it's better to have i ...more
With T-Day on the horizon and approaching rapidly, you are probably in one of two camps. The one that is eagerly awaiting the holiday feast with barely-contained drool. Or the one that involves breathing heavily into a paper bag while worrying about your lack of oven and stove ...more
In my last article, I explained why text adventure games are some of the most Steampunk computer games out there. I even shared a free Steampunk text adventure game that I'd made myself! Now, I grew up playing text-based games (which are now known as interactive fiction) such ...more
Now that Android 7.1.1 has been released, several features that were previously exclusive to Google's new Pixel phones are now available on the Nexus 6P. However, Google seems to be holding back on the Pixel's best features, as things like the "Night Light" red screen filter, ...more
When you think of bivalves, such as manila clams and oysters, you tend to think of the meat as being nicely tucked in the shell. Anything else would be scary, right? Don't Miss: Would You Eat Fugu, AKA Poisonous Puffer Fish? Well, meet the geoduck, which is not only the weir ...more
In the last couple of days there's been a lot of speculation about the powers of Microsoft's HoloLens 2, but few have had a chance to get their hands on one to see if the company's claims live up to what HoloLens inventor Alex Kipman showed off on stage. Nevertheless, amid th ...more
Ever since the announcement of the Razer Phone, a wave of gaming smartphones started to hit the market. With ASUS being such a big name in gaming, it made sense for them to throw their hat in the ring. The result is the ROG Phone. And with this first try, ASUS has topped the r ...more
One could argue that, at least for the moment, software development is more important to the augmented reality experience than hardware. Since a viable augmented reality headset has yet to emerge for the broader, mainstream consumer market, currently, the same devices that mak ...more
The theme for 2017's World Malaria Day, which is today, April 25, is "End Malaria for Good." For many Americans, this might seem like an odd plea. Especially since Malaria is seemingly an obsolete problem here. However, on World Malaria Day, it's important to remember the dang ...more
First of all, I hope the title makes sense. :D Well, this is basically creating a program that can help with dictionary attacks. Generate possible passwords. It pretty much lies in you knowing the person you want to hack. Story Time I just like stories :D Well, I heard abou ...more
Whether it's the start, middle, or end of summer, it's prime-time grilling season. If you find yourself without a grill, however, it may seem as if half your summer plans of swimming by the pool while stuffing hot dogs in your face could be ruined. But have no fear as all is ...more
Catching up with Windows 8, Apple has finally included a way in Mac OS X to use two apps side by side in full screen view. In the 10.11 El Capitan update, it's called Split View, and it works fairly well for the most part. It's not quite as intuitive as it should be, but easy ...more
Everyone has the same five spirits in their bar: vodka, rum, whiskey, tequila, and gin. They're all great, but every so often the mood strikes to try a cocktail with a little something different. We'd like you to meet three spirits from South America that would make a welcome ...more
It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a so ...more
Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve ...more
Get Out absolutely tore up the record books this year. And the wildest thing about it? It did so with the most ordinary looking characters and props ever (hence the shoestring $4.5 million budget). Which makes it a godsend for the time- and cash-strapped come Halloween. With G ...more
Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associa ...more
Nothing gets me functioning in the morning better than strong coffee. And if I'm going to start my day with a dreaded workout, that steaming cup of caffeine is the exact motivation I need to get going. Although coffee might not seem like the best beverage to drink before hitti ...more
Many of us in the Steampunk community have pets that we love and cherish, myself included, and we want those pets to share our joy of Steampunk. In reality, they couldn't care less, but for some reason we still love to dress them up. Their reactions usually range from bemused ...more
You've probably already used a few Safari Extensions on your Mac, but if you haven't explored Safari's web extensions on your iPhone yet, you're missing out on some fantastic possibilities to increase productivity, make tasks easier, filter out noise, and bring more fun to you ...more
Group chats on WhatsApp are great for getting your friends all in one place, but the bigger the group, the more notifications you'll probably get. Needless to say, it can get annoying real quick. You can mute notifications for all your conversations, but that's not practical i ...more
T-Mobile is going for broke. The carrier recently announced it will be giving away free stuff to its customers every Tuesday through a new app called T-Mobile Tuesdays for Android and iOS, and that's in addition to one share of stock and free in-flight Wi-Fi. The app will give ...more
Classic party games like Spin the Bottle and Truth or Dare, immensely popular in the '80s and '90s, seem to have been long forgotten and abandoned by today's youth. Today, new forms of party games are all the rage, a prime example being Cards Against Humanity. Yes, CAH is hila ...more
Since picking up your first crayon, chances are you've had a favorite, or dominant, hand. That hand gets you through the day, taking care of everything from writing to eating. If you've ever been forced to rely on your "wrong hand", you know how uncomfortable and unwieldy it f ...more
Closing apps in iOS 6 was different that what is now in iOS 7. Shown in the video below is the old clumsy way of closing apps on the old iPads. Video: . Closing the apps prevents from taking up precious memory, resources and battery charge. Simply quit of the screen with the c ...more
One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sen ...more
The cord on your headphones is usually more enemy than friend. While they obviously need it to function, a tangled or unnecessarily long cord can wreak havoc on your sanity. Personally, I've broken at least two pairs of headphones by tripping over the cord and yanking the jack ...more
A couple of months ago at the Black Hat security conference, hacker Cody Brocious gave the hotel industry a nasty surprise when he figured out how to hack the locks made by Onity that are used in millions of hotels worldwide. The reason his hack is so impressive is because it ...more
Hello! Today I would like to introduce a simple tiny braid - so called the small wrap up. I recommend it to every person who wants to prevent the hair from falling onto the face. It is suitable especially for the people who have long or medium sized hair and very delicate skin ...more
Simple as the title, someone will particpate as a crash test dummy. The funny part of course the prank is the "particpate" will not know he is a crash test dummy. Its kinda like the prank that was pulled on Ryan Dunn in the addtional footage in the DVD of Jackass Number Two wh ...more
Reborning, the insanely creepy (!!) art of transforming vinyl dolls into strikingly realistic newborns, known as "living dolls" or "unliving dolls". The dolls are used for two purposes: first, simply as a collectors item for doll enthusiasts, and second (this one is a bit sca ...more
Ads aren't the only annoying part of navigating websites in Safari. Colorful banners, autoplaying videos, embedded objects, and other distracting elements can make it harder to read or watch what you want. Although ad blockers are one answer, they only get rid of advertisement ...more
You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information i ...more
The year 2018 was a rough one for Snap, the company behind the Snapchat app and the Spectacles wearable camera device. From executive departures to reports of slowed user growth, the company that once spurned Facebook's multibillion-dollar advances is now facing a moment of tr ...more
Next to map data overlays, one of the most often discussed concepts for apps that could propel augmented reality smartglasses into the mainstream is a real-time language translation app. Now, Netherlands-based startup Zoi Meet is promising to deliver just that with a new app ...more
While mobile gaming, in the 10 years since the App Store launched, has matured to console-level quality, premium augmented reality games built with ARKit (or ARCore) have been scarce. Immersive VR is looking to do its part reduce that deficit with the launch of The Ancients A ...more
Medical training technology company CAE Healthcare has given birth to the latest example of how augmented reality can help to build practical operating room skills for doctors and nurses. The company's newest product is called LucinaAR, which harnesses the power of the Microso ...more
Cycling accidents are more common than you think. In the past month, two men have been hit and killed while cycling in New York City. I even saw a cycling accident occur yesterday morning here in NYC. It's dangerous enough to be cycling in populated areas, it's made worse by p ...more
Texas has become only the latest state to face an unfortunate outbreak of mumps, but so far seems to be the hardest hit. On April 12, two days before the CDC's report was released, the Texas Department of State Health Services released a health advisory indicating this is the ...more
When you're on the road, the last thing you need to be doing is fumbling around with your phone. But with online radio services like Spotify and Google Play Music, you almost have to use your phone to play music through your stereo, because the in-dash head units on most cars ...more
Just last month, Microsoft announced plans to take away a huge chunk of storage from the free tier of their OneDrive cloud service, and users are understandably quite upset. At the same time, they reneged on an offer to give Office365 users unlimited OneDrive storage, and inst ...more
Ask around anywhere that Android users gather online, and you'll find that SwiftKey is almost unilaterally the most highly-recommended keyboard for our favorite mobile operating system. It's no surprise either—SwiftKey's combination of insanely accurate word predictions and ra ...more
Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history. Using a type of malware dubbed “KeyRaider,” hackers hav ...more
When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you h ...more
Getting things done isn't easy when you're bombarded with alert sounds and notifications all day long on your Mac. Here's how you can quickly remove those distractions with just a single click. Step 1: Download the Automator Apps This part is pretty easy. Just click here to ...more
In-N-Out Burgers on the West Coast is famous for their not-so-secret and secret menus, along with their cheap, no-fuss burgers. Pre-internet, you felt like you were actually part of a small, select club when you knew what secret menu items to order. But with the advent of the ...more
Whether it's because you travel quite often or have loved ones in another part of the country, Android makes it easy to place dual clocks on your home screen using a widget. While there are several other widgets you can use to tell the time, that's pretty much the only way you ...more
What is in store for the future? Flying cars? Maybe. Dinner in a pill? Perhaps. How about 4-legged army tank robot dogs? Hell ya! This delights both the Hummer loving He-men and the anti-war pacifists in us. Something that can kick ass and save lives! Perfect. BigDog is a me ...more
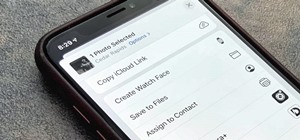
When you take a screenshot on your iPhone, it's automatically saved to your Photos app. You can ignore the screenshot thumbnail or swipe it away, but you shouldn't. If you open the screenshot editor instead, you'll gain access to your iPhone's most useful screen capture tool: ...more
The coronavirus continues to disrupt the tech industry, including the augmented reality segment, with Apple and the iPhone the latest to feel the impact. After the cancellation of Mobile World Congress due to the virus outbreak, HTC proceeded with its unveiling of HTC Vive pr ...more
While photography usually gets all the love, our phones have gotten really good at capturing video. Think about it — when was the last time you needed a camcorder for a vacation? With mobile cameras getting better each year, we're now at a point where smartphones can be used f ...more
After years of waiting, Microsoft has finally updated its industry-leading augmented reality device, the HoloLens. During a pre-show event at the Mobile World Congress in Barcelona, Spain, HoloLens inventor Alex Kipman, along with Microsoft CEO Satya Nadella and Julia White, ...more
With Pokémon GO as its cash cow and the forthcoming Harry Potter: Wizards Unite and Niantic Real World Platform promising future revenue streams, Niantic has convinced investors to bet on its flavor of augmented reality After reports surfaced in December that the developer wa ...more
Snapseed is an app that you should definitely be using not only if you're really serious about photography, but also if you want to ensure that your online work sets the standard for social media. It's a great companion app to Instagram and VSCO, and it will save your day many ...more